350-901 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 350-901 certification exam? Kickstart your success with our 350-901 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 350-901 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 350-901 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Which scenario is an example of the pseudonymization of sensitive data that meets GDPR requirements?
A. implementing X-Forwarded-For at the frontend of a web app to enable the source IP addresses of headers to change
B. separating the sensitive data into its own dedicated, secured data store and using tokens in its place.
C. encrypting sensitive data at rest by using native cloud services and data in transit by using SSL/TLS transport.
D. leveraging an application load balancer at the frontend of a web app for SSL/TLS decryption to inspect data in transit.
What is a benefit of running multiple instances of a back-end service and using load balancing to distribute the communication between the front-end and back-end services?
A. High availability is provided for the back-end services.
B. Scaling horizontally is automated out of the box.
C. The total load on the database servers decreases.
D. The consistency of data for stateful services increases.
What are two benefits of using a centralized logging service? (Choose two.)
A. reduces the time required to query log data across multiple hosts
B. reduces the loss of logs after a single disk failure
C. improves application performance by reducing CPU usage
D. improves application performance by reducing memory usage
E. provides compression and layout of log data
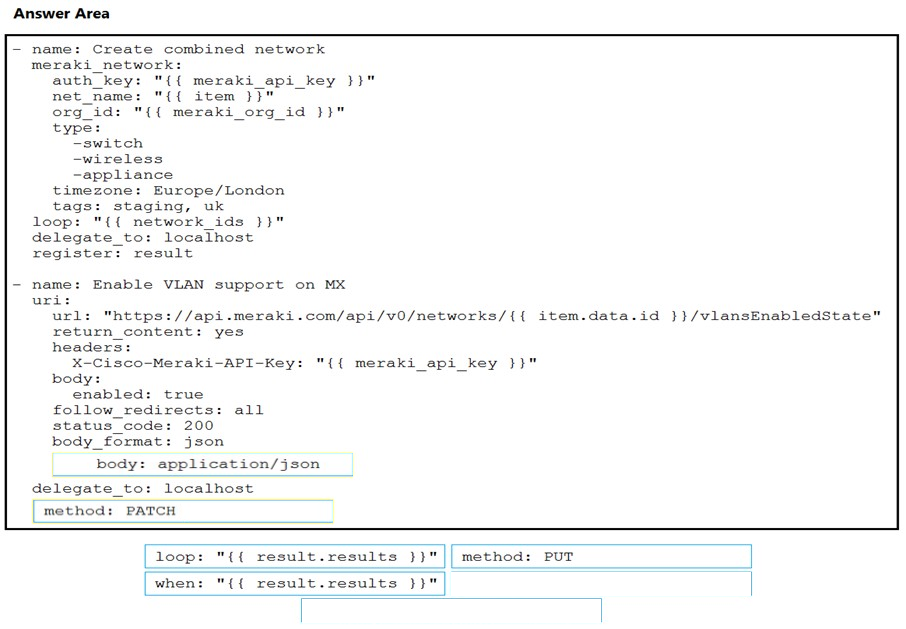
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX device. Not all options are used. Select and Place:
A developer in a team of distributed authors is working on code in an isolated Git branch named 'update1a2b3456789'. The developer attempts to merge the new code with a branch named 'dvcapp9a8b7654321' however the merge operation encounters a conflict error during the process. Which Git command must the developer use to exit from the merge process and return the branch to the previous state?
A. git abort –status
B. git abort –merge
C. git merge –exit
D. git merge –abort
A software developer is designing a new application to collect data from the network and feed the data into a custom dashboard. The application must be easy to troubleshoot and scale. What are two reasons the developer must use modularity in the design for maintainability instead of a single code base that involves dependencies? (Choose two.)
A. makes the application operate faster
B. application becomes more flexible and extendable
C. code reusability increases
D. better integration with public cloud services
E. software configuration management is easier
DRAG DROP - A developer must package an application for Kubernetes to integrate into a prebuilt CD environment. The application utilizes a Docker image from Cisco DevNet public repository and is accessible from a specific port of the container. Drag and drop the code from the bottom onto the box where the code is missing in the Kubernetes YAML configuration file. Not all options are used.
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to write a module that will do the following: • examine an HTTP response status for the "Too Many Requests" error and the HTTP Retry-After header • enter the sleep() function • wake from the sleep() function and retry the POST request Not all options are used.
An engineer oversees the development of an application that is hosted in the Python Django framework. Containerized microservices are used for the application logic. A remote database for state deposition is used. Which two monitoring solutions provide the application observability to assist with troubleshooting and debugging? (Choose two.)
A. integrated configuration environment
B. continuous deployment pipeline
C. security information and event management
D. resource utilization monitor
E. Cisco Intersight view
How is client code that consumes gRPC telemetry implemented, assuming that the preferred language is able to be chosen?
A. Leverage a Thrift code generator to parse a Thrift IDL.
B. Compile the protocol buffers IDL.
C. Review the Swagger API documentation to build client code.
D. Parse the OpenAPI spec model.
DRAG DROP - Drag and drop the expressions from below onto the code to implement error handling. Not all options are used. Select and Place:
Refer to the exhibit. A developer created a Python script to retrieve information about Meraki devices in a local network deployment. After requesting a security review of the code, the security analyst has observed poor secret storage practices. What is the appropriate secret storage approach?
A. Set an OS environment variable for MER_API_KEY to the API key before running the code and no longer set MER_API_KEY within the code.
B. Leverage an external secret vault to retrieve MER_API_KEY and set the vault key as an OS environment variable before running the code.
C. Set the Base64 encoded version of the API key as MER_API_KEY in the code and Base64 decode before using in the header.
D. Leverage an external secret vault to retrieve MER_API_KEY and embed the vault key as a new variable before running the code.
How is AppDynamics used to instrument an application?
A. Enables instrumenting a backend web server for packet installation by using an AppDynamics agent.
B. Retrieves a significant amount of information from the perspective of the database server by using application monitoring.
C. Provides visibility into the transaction logs that can be correlated to specific business transaction requests.
D. Monitors traffic flows by using an AppDynamics agent installed on a network infrastructure device.
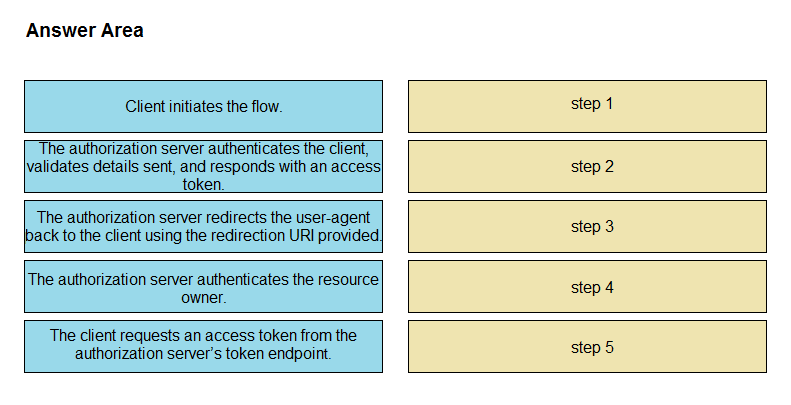
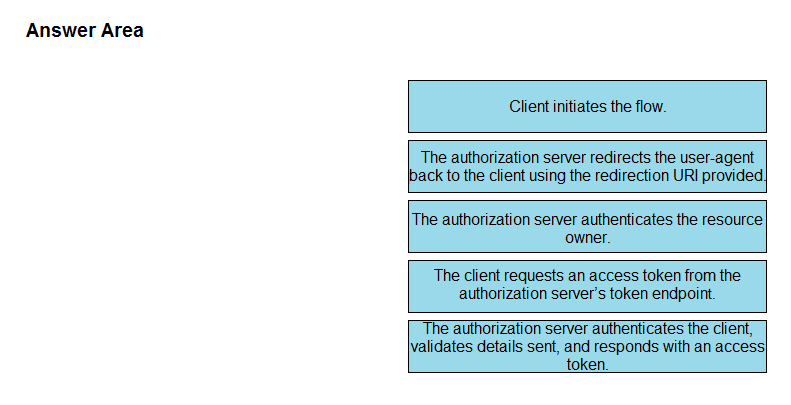
DRAG DROP -Refer to the exhibit. Drag and drop the steps from the left into the correct order of operation on the right for a successful OAuth2 three-legged authorization code grant flow. Select and Place:
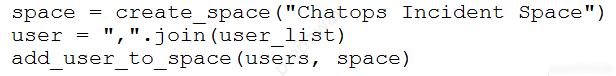
Refer to the exhibit. Which snippet creates a Webex space and adds the users in the variable user_list to that space? A.
B.
C.
D.
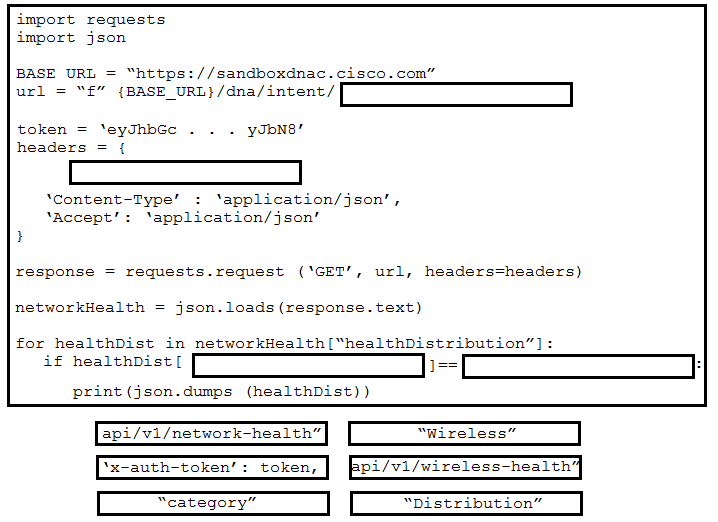
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to retrieve and display wireless network health information. The wireless network devices are being managed by Cisco DNA Center and are compatible with REST API. Not all options are used. Select and Place:
DRAG DROP - Drag and drop the components from the left into the order on the right to create the flow of the three-legged OAuth2.
Refer to the exhibit. This cURL POST request creates an OAuth access token for authentication with FDM API requests. What is the purpose of the file `@token_data` that cURL is handling?
A. This file is given as input to store the access token received from FDM.
B. This file is used to send authentication-related headers.
C. This file contains raw data that is needed for token authentication.
D. This file is a container to log possible error responses in the request.
A development team is looking for a tool to automate configurations across the infrastructure. The tool must have these characteristics: • written in Python • define playbooks for intent • stateless • imperative Which tool meets these requirements?
A. Ansible
B. Netmiko
C. NCM
D. Puppet
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to construct a contact tracing application that dynamically returns all the Bluetooth clients on a given Meraki network. Not all options are used.
Which two encryption principles should be applied to secure APIs? (Choose two.)
A. Use temporary files as part of the encryption and decryption process.
B. Use encrypted connections to protect data in transit.
C. Reuse source code that contain existing UUIDs.
D. Embed keys in code to simplify the decryption process.
E. Transmit authorization information by using digitally signed payloads.
A developer is deploying an application to automate the configuration and management of Cisco network switches and routers. The application must use REST API interface to achieve programmability. The security team mandates that the network must be protected against DDoS attacks. What mitigates the attack without impacting genuine requests?
A. IP address filtering at the application layer
B. traffic routing on the network perimeter
C. API rate limiting at the application layer
D. firewall on the network perimeter
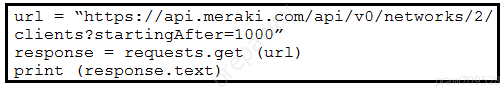
Refer to the exhibit. A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2. The number of client entries per returned page is restricted to 1,000 according to the API specification. Network 2 has 2,500 clients. What must be added where the code is missing to print the content of each response? A.
B.
C.
D.
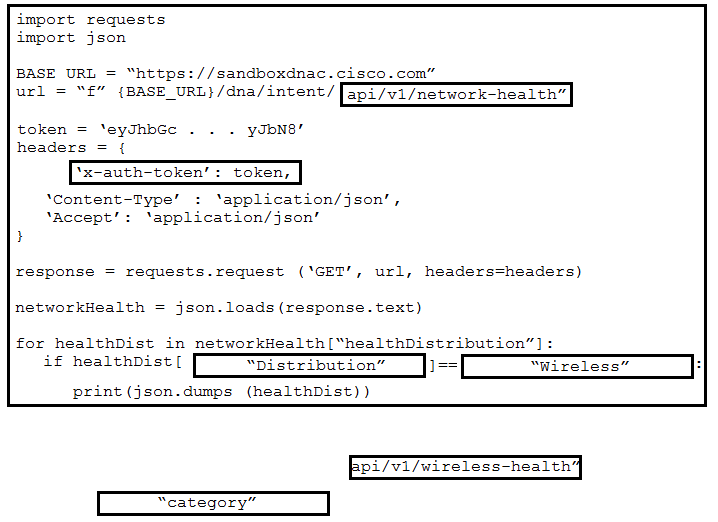
DRAG DROP -Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to construct a Python script that prints a message if the Cisco DNA Center wireless network health for a site is not greater than 90%. The information is collected from the wireless network devices using GET method of REST API. Not all options are used.
DRAG DROP - Drag and drop the steps from the left into the order on the right to host a Docker-contained application on a Cisco Catalyst 9000 Series Switch.
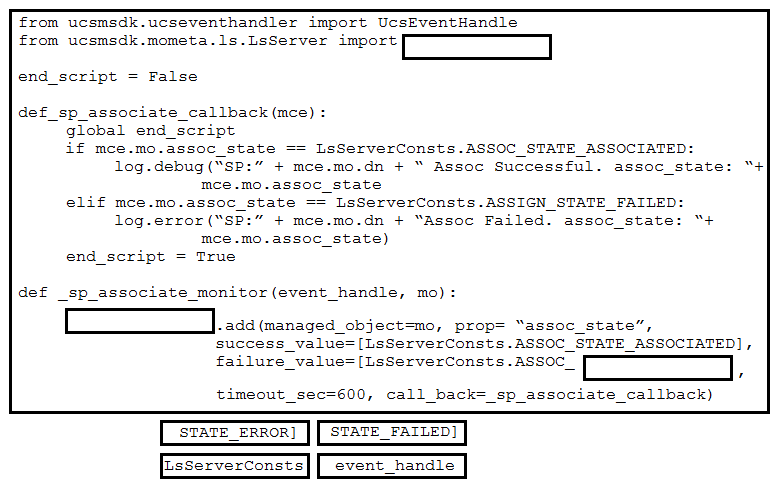
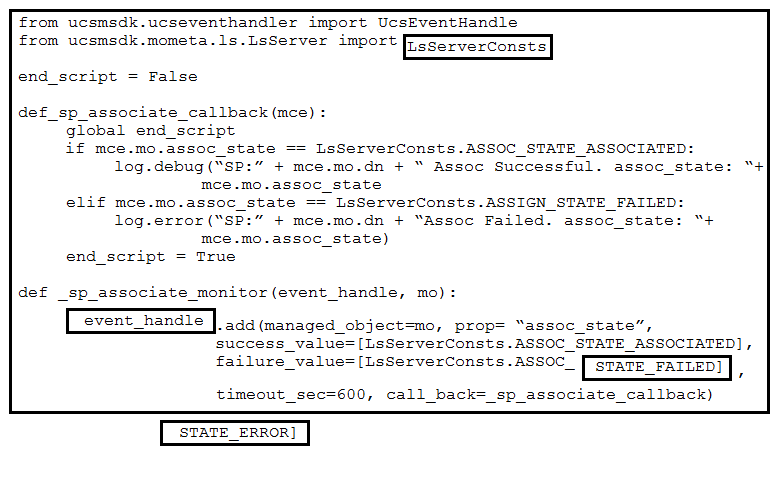
DRAG DROP -Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the code to provision a new UCS server. Not all options are used. Select and Place:
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module creates the NTP server peer?
A. state: absent
B. state: False
C. config: absent
D. config: False
What is an effective strategy for application logging?
A. Use an FTP server for collection.
B. Use a single vendor across the network.
C. Use SNMP for messages.
D. Use the appropriate logging level.
Refer to the exhibit. Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A.

B.

C.

D.

A developer releases a new application for network automaton of Cisco devices deployed in a local data center. The application utilizes complex design patterns such as microservices that host multiple third-party libraries and programming languages. The development must be simplified by implementing an observability- driven development lifecycle. Which two considerations must be taken to meet the requirements? (Choose two.)
A. which monitoring tools to use
B. identifying customer priorities
C. relevant metrics to expose
D. description of low-level errors
E. which KPIs to monitor
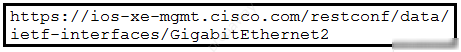
Refer to the exhibit. An engineer is managing a network that consists of Cisco IOS-XE devices. There is a need to retrieve the details of the interface GigabitEthernet2 using RESTCONF. Which URI will accomplish this by providing the same response as shown in the JSON body? A.
B.
C.
D.
Refer to the exhibit. One part of an application routinely uses the Cisco Meraki API to collate data about all clients. Other parts of the application also use the Meraki API, but a single API key is used within the application. The organization has approximately 4,000 clients across 30 networks. Some of the application users report poor performance and missing data. Which two changes improve the performance of the application? (Choose two.)
A. Check API response payloads for later reuse in real time during code execution.
B. Use random values in the User-Agent header when HTTP calls are made.
C. Use fewer API calls to create a more efficient endpoint.
D. Configure multiple API keys in the application and rotate usage of each one.
E. Check for HTTP code 429 and wait until Retry-After time before further calls are made.
Refer to the exhibit. What is the output of this IOS-XE configuration program?
A. interface operational status in IPv6 addresses
B. interface administrative status in IPv4 addresses
C. interface operational status in IPv4 addresses
D. interface administrative status in IPv6 addresses
Refer to the exhibit. Pipenv is used to manage dependencies. The test runs successfully on a local environment. What is the reason for the error when running the test on a CI/CD pipeline?
A. All the unit tests in testsum.py failed.
B. Pytest did not detect any functions that start with ‘test_’.
C. The pipfile in the local environment was not pushed to the remote repository.
D. Nose2 was not used as the test runner.
What is a benefit of using model-driven telemetry?
A. reduces the load on the server by enabling the client to pull data
B. simplifies the development of clients by using a single encoding standard for the data
C. enables operational data to be collected at higher rates and a higher scale
D. enables the application to pull data faster than pushing the data
Which database type should be used to store data received from model-driven telemetry?
A. BigQuery database
B. Time series database
C. NoSQL database
D. PostgreSQL database
A developer must apply a new feature on a live project. After the commit, it was discovered that the wrong file was applied. The developer must undo the single commit and apply the file with the name feat-EXP453928854DPS. Which command must the developer use?
A. git clean
B. git checkout
C. git revert
D. git reset
How does the use of release packaging allow dependencies to be effectively managed during deployments?
A. removal of release units if they have issues in testing
B. dependencies are tested after the release is deployed
C. designed to prevent any dependencies between release units
D. dependencies are staggered between multiple releases
An engineer is developing a Docker container for an application in Python. For security reasons the application needs to be accessible on port 5001 only. Which line should be added to the dockerfile in order to accomplish this?
A. ADD PORT 5001
B. ENTRYPOINT 5001
C. EXPOSE 5001
D. PORT SRC 5001
A network operations team is using the cloud to automate some of their managed customer and branch locations. They require that all of their tooling be ephemeral by design and that the entire automation environment can be recreated without manual commands. Automation code and configuration state will be stored in git for change control and versioning. The engineering high-level plan is to use VMs in a cloud-provider environment, then configure open source tooling onto these VMs to poll, test, and configure the remote devices, as well as deploy the tooling itself. Which configuration management and/or automation tooling is needed for this solution?
A. Ansible
B. Ansible and Terraform
C. NSO
D. Terraform
E. Ansible and NSO
Refer to the exhibit. Which two functions are performed by the load balancer when it handles traffic originating from the Internet destined to an application hosted on the file server farm? (Choose two.)
A. Terminate the TLS over the UDP connection from the router and originate an HTTPS connection to the selected server.
B. Terminate the TLS over the UDP connection from the router and originate an HTTP connection to the selected server.
C. Terminate the TLS over the TCP connection from the router and originate an HTTP connection to the selected server.
D. Terminate the TLS over the TCP connection from the router and originate an HTTPS connection to the selected server.
E. Terminate the TLS over the SCTP connection from the router and originate an HTTPS connection to the selected server.
Refer to the exhibit. A network engineer must integrate error handling for time-outs on network devices using the REST interface. Which line of code needs to be placed on the snippet where the code is missing to accomplish this task?
A. elif resp.status_code == 429 or self._retries < self._MAX_RETRIES:
B. elif resp.status_code == 404 and self._retries < self._MAX_RETRIES:
C. elif resp.status_code == 404 or self._retries < self._MAX_RETRIES:
D. elif resp.status_code == 429 and self._retries < self._MAX_RETRIES:
An engineer is developing an application to use across organizations. The application will process sensitive data and access will be allowed from the internet. The application will need to store the session ID of the users. This must be implemented using a secure management mechanism. Which secret storage approach must the engineer take to meet these requirements?
A. browser cache
B. JavaScript variable
C. persistent cookie
D. non-persistent cookie
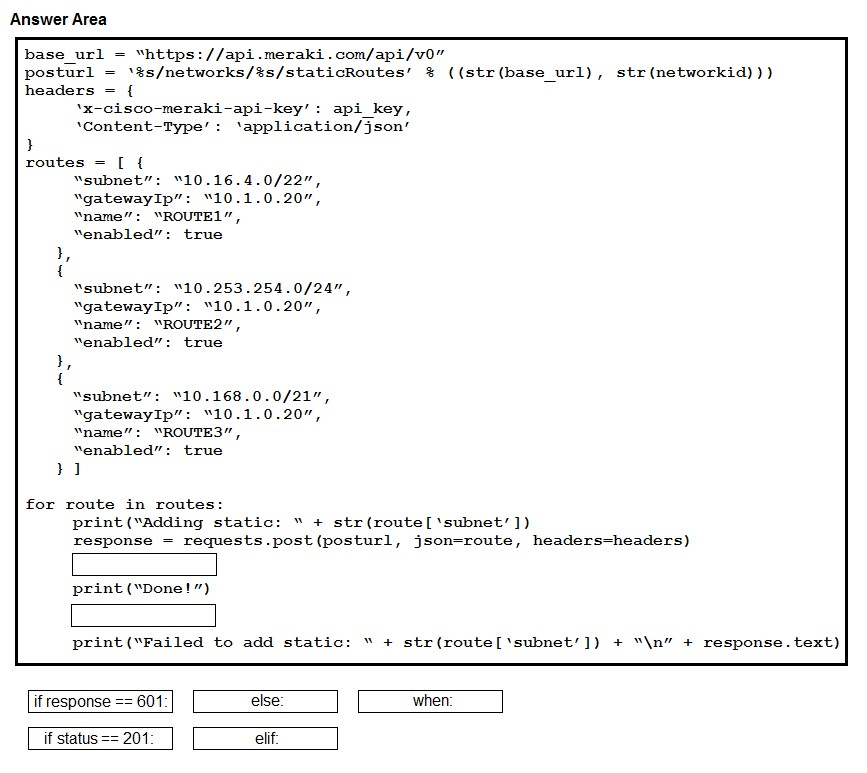
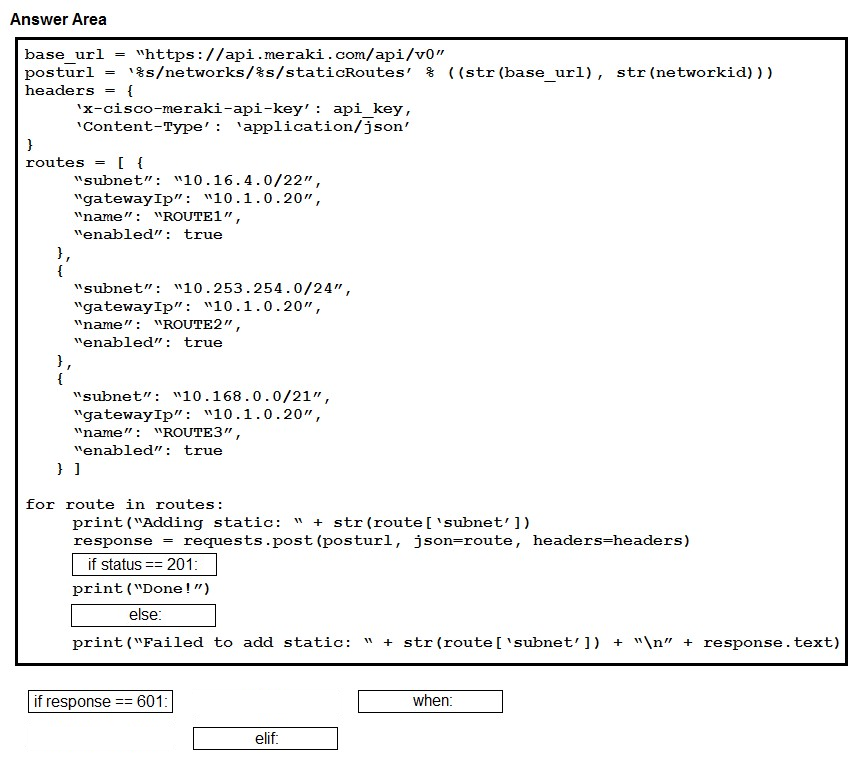
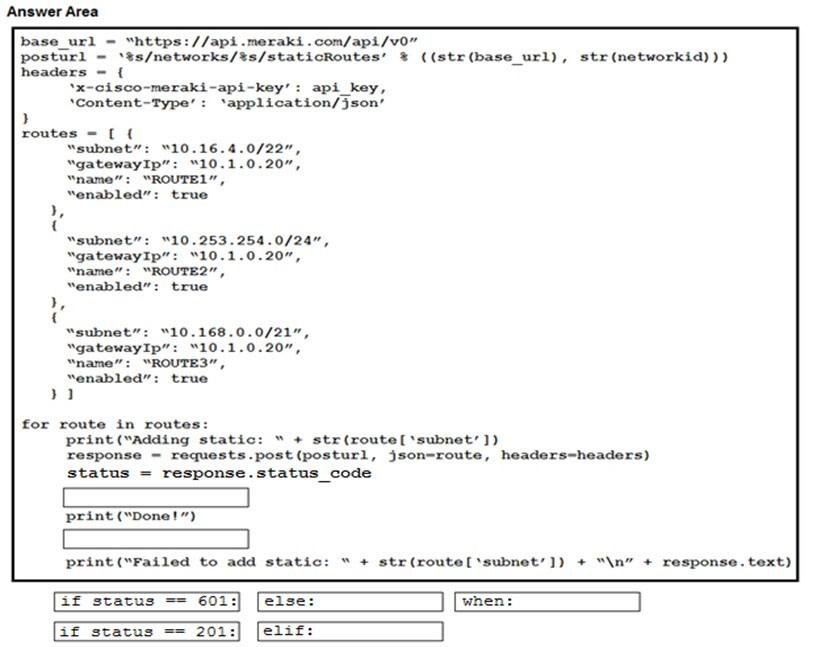
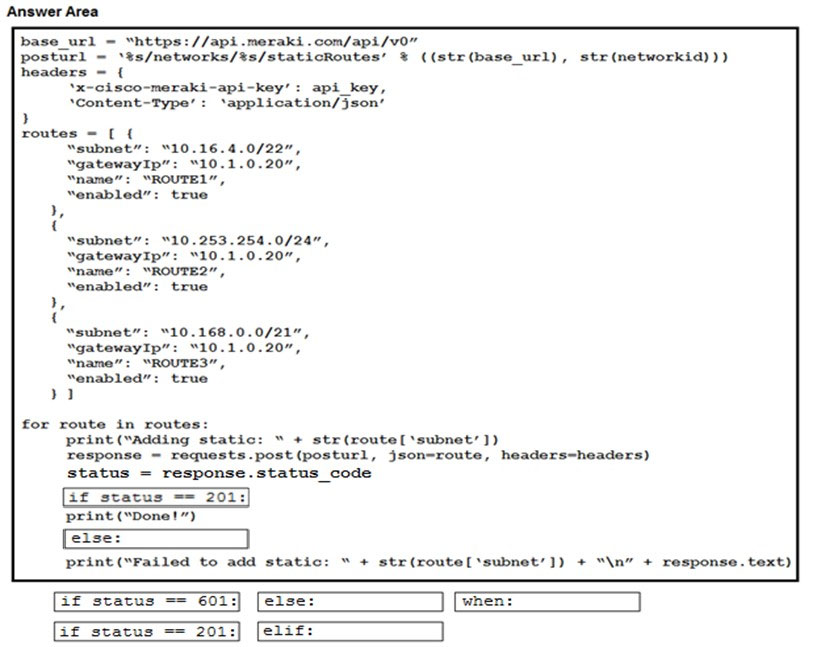
DRAG DROP - Drag and drop the expressions from below onto the code to implement error handling. Not all options are used. Select and Place:
When an application is designed that requires high availability, what is a reason to use a cross-region cloud?
A. Account for failure in another zone.
B. Minimize costs.
C. Protect from a single component failure.
D. Provide disaster recovery protection.
An automated solution is needed to configure VMs in numerous cloud provider environments to connect the environments to an SDWAN. The SDWAN edge VM is provided as an image, in each of the relevant clouds it is given an identity and all required configuration via cloud-init without needing to log into the VM once online. Which configuration management automation tool is needed for this solution?
A. Terraform
B. HyperFlex
C. Intersight
D. Ansible
Refer to the exhibit. A developer created an application to display telemetry metrics that were collected from Cisco devices and hosted it on a local development server. Upon initialization, the application does not behave as expected when a user tries to authenticate with their profile. What is the cause of this problem?
A. The service that the application tries to access from host demo.testapplication.com has not yet been implemented.
B. The application encounters a rate limit when trying to access the host demo.testapplication.com.
C. The application cannot authenticate with the application service hosted on demo.testapplication.com.
D. The service that the application is calling from host demo.testapplication.com encounters an internal failure.
Why do platforms require an API key to connect and stream data?
A. encode exported resources
B. validate the identity of user
C. encrypt transmitted data
D. protect against unauthorized access
An application is made up of multiple microservices, each communicating via APIs. One service is beginning to be a bottleneck for the application because it can take a lot of time to complete requests. An engineer tried adding additional instances of this service behind the load balancer, but it did not have any effect. Which application design change must be implemented in this scenario?
A. Deploy an API gateway to centralize all inbound communication requests and offload authentication.
B. Vendor all dependencies into the service that is causing delays to remove external dependency checks.
C. Move from synchronous to asynchronous interactions with the service and implement a message queue.
D. Leverage serverless architecture instead of containers to gain the advantage of event driven APIs.
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to update the script library that is used to connect to the REST API on the network devices. A descriptive error and warning message should be logged when a user uses the script. Not all options are used.
Free Access Full 350-901 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 350-901 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 350-901 certification journey!