312-50V9 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 312-50V9 certification exam? Kickstart your success with our 312-50V9 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 312-50V9 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 312-50V9 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:From the above list identify the user account with System Administrator privileges.
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah F
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
A. Blue Book
B. ISO 26029
C. Common Criteria
D. The Wassenaar Agreement
Which results will be returned with the following Google search query? site:target.com -site:Marketing.target.com accounting
A. Results matching all words in the query
B. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
C. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting
D. Results for matches on target.com and Marketing.target.com that include the word “accounting”
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
A. ping 192.168.2.
B. ping 192.168.2.255
C. for %V in (1 1 255) do PING 192.168.2.%V
D. for /L %V in (1 1 254) do PING -n 1 192.168.2.%V | FIND /I “Reply”
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?
A. Spoof Scan
B. TCP Connect scan
C. TCP SYN
D. Idle Scan
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in-bounds checking mechanism?Output: Segmentation fault -
A. C#
B. Python
C. Java
D. C++
A hacker was able to easily gain access to a website. He was able to log in via the frontend user login form of the website using default or commonly used credentials. This exploitation is an example of what Software design flaw?
A. Insufficient security management
B. Insufficient database hardening
C. Insufficient input validation
D. Insufficient exception handling
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
A. Legal, performance, audit
B. Audit, standards based, regulatory
C. Contractual, regulatory, industry
D. Legislative, contractual, standards based
In the OSI model, where does PPTP encryption take place?
A. Transport layer
B. Application layer
C. Data link layer
D. Network layer
Which of the following is an example of an asymmetric encryption implementation?
A. SHA1
B. PGP
C. 3DES
D. MD5
Which of the following describes the characteristics of a Boot Sector Virus?
A. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR
B. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR
C. Modifies directory table entries so that directory entries point to the virus code instead of the actual program
D. Overwrites the original MBR and only executes the new virus code
Which type of scan measures a person's external features through a digital video camera?
A. Iris scan
B. Retinal scan
C. Facial recognition scan
D. Signature kinetics scan C
The network administrator for a company is setting up a website with e-commerce capabilities. Packet sniffing is a concern because credit card information will be sent electronically over the Internet. Customers visiting the site will need to encrypt the data with HTTPS. Which type of certificate is used to encrypt and decrypt the data?
A. Asymmetric
B. Confidential
C. Symmetric
D. Non-confidential
A security consultant decides to use multiple layers of anti-virus defense, such as end user desktop anti-virus and E-mail gateway. This approach can be used to mitigate which kind of attack?
A. Forensic attack
B. ARP spoofing attack
C. Social engineering attack
D. Scanning attack
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A. Start by foot printing the network and mapping out a plan of attack.
B. Ask the employer for authorization to perform the work outside the company.
C. Begin the reconnaissance phase with passive information gathering and then move into active information gathering.
D. Use social engineering techniques on the friend’s employees to help identify areas that may be susceptible to attack.
Which of the following is a characteristic of Public Key Infrastructure (PKI)?
A. Public-key cryptosystems are faster than symmetric-key cryptosystems.
B. Public-key cryptosystems distribute public-keys within digital signatures.
C. Public-key cryptosystems do not require a secure key distribution channel.
D. Public-key cryptosystems do not provide technical non-repudiation via digital signatures.
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
A.
B. 44EFCE164AB921CQAAD3B435B51404EE
C.
D.
E.
F.
An NMAP scan of a server shows port 25 is open. What risk could this pose?
A. Open printer sharing
B. Web portal data leak
C. Clear text authentication
D. Active mail relay
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
A. Restore a random file.
B. Perform a full restore.
C. Read the first 512 bytes of the tape.
D. Read the last 512 bytes of the tape.
Which of the following is a client-server tool utilized to evade firewall inspection?
A. tcp-over-dns
B. kismet
C. nikto
D. hping A
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
A. Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
B. Package the Sales.xls using Trojan wrappers and telnet them back your home computer [1] Steganography techniques
D. Change the extension of Sales.xls to sales.txt and upload them as attachment to your hotmail account
A hacker has managed to gain access to a Linux host and stolen the password file from /etc/passwd. How can he use it?
A. The password file does not contain the passwords themselves.
B. He can open it and read the user ids and corresponding passwords.
C. The file reveals the passwords to the root user only.
D. He cannot read it because it is encrypted.
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
A. True
B. False
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
A. Fast processor to help with network traffic analysis
B. They must be dual-homed
C. Similar RAM requirements
D. Fast network interface cards
Which of the following is a common Service Oriented Architecture (SOA) vulnerability?
A. Cross-site scripting
B. SQL injection
C. VPath injection
D. XML denial of service issues D
Which set of access control solutions implements two-factor authentication?
A. USB token and PIN
B. Fingerprint scanner and retina scanner
C. Password and PIN
D. Account and password
John the Ripper is a technical assessment tool used to test the weakness of which of the following?
A. Usernames
B. File permissions
C. Firewall rulesets
D. Passwords
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
B. Permit 217.77.88.12 11.12.13.50 RDP 3389
C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
Which among the following is a Windows command that a hacker can use to list all the shares to which the current user context has access?
A. NET FILE
B. NET USE
C. NET CONFIG
D. NET VIEW
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
A. Information reporting
B. Vulnerability assessment
C. Active information gathering
D. Passive information gathering
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts. Which of the following features makes this possible? (Choose two.)
A. It used TCP as the underlying protocol.
B. It uses community string that is transmitted in clear text.
C. It is susceptible to sniffing.
D. It is used by all network devices on the market.
Which of the following types of firewall inspects only header information in network traffic?
A. Packet filter
B. Stateful inspection
C. Circuit-level gateway
D. Application-level gateway
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the Annualized Loss Expectancy (ALE).
A. $62.5
B. $250
C. $125
D. $65.2
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries.) More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Basic example to understand how cryptography works is given below:Which of the following choices is true about cryptography?
A. Algorithm is not the secret, key is the secret.
B. Symmetric-key algorithms are a class of algorithms for cryptography that use the different cryptographic keys for both encryption of plaintext and decryption of ciphertext.
C. Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way.
D. Public-key cryptography, also known as asymmetric cryptography, public key is for decrypt, private key is for encrypt.
When purchasing a biometric system, one of the considerations that should be reviewed is the processing speed. Which of the following best describes what it is meant by processing?
A. The amount of time it takes to convert biometric data into a template on a smart card.
B. The amount of time and resources that are necessary to maintain a biometric system.
C. The amount of time it takes to be either accepted or rejected form when an individual provides Identification and authentication information.
D. How long it takes to setup individual user accounts. C
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
A. IP Security (IPSEC)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS) C
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
A. white box
B. grey box
C. red box
D. black box
In order to show improvement of security over time, what must be developed?
A. Reports
B. Testing tools
C. Metrics
D. Taxonomy of vulnerabilities
A hacker is attempting to see which ports have been left open on a network. Which NMAP switch would the hacker use?
A. -sO
B. -sP
C. -sS
D. -sU
The network administrator at Spears Technology, Inc has configured the default gateway Cisco router's access-list as below: You are hired to conduct security testing on their network. You successfully brute-force the SNMP community string using a SNMP crack tool. The access-list configured at the router prevents you from establishing a successful connection. You want to retrieve the Cisco configuration from the router. How would you proceed?
A. Use the Cisco’s TFTP default password to connect and download the configuration file
B. Run a network sniffer and capture the returned traffic with the configuration file from the router
C. Run Generic Routing Encapsulation (GRE) tunneling protocol from your computer to the router masking your IP address
D. Send a customized SNMP set request with a spoofed source IP address in the range -192.168.1.0
How can rainbow tables be defeated?
A. Password salting
B. Use of non-dictionary words
C. All uppercase character passwords
D. Lockout accounts under brute force password cracking attempts
Emil uses nmap to scan two hosts using this command. nmap -sS -T4 -O 192.168.99.1 192.168.99.7 He receives this output: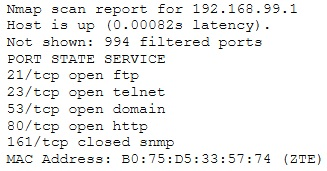
What is his conclusion?
A. Host 192.168.99.7 is an iPad.
B. He performed a SYN scan and OS scan on hosts 192.168.99.1 and 192.168.99.7.
C. Host 192.168.99.1 is the host that he launched the scan from.
D. Host 192.168.99.7 is down. B
You've gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your tool kit you have an Ubuntu 9.10 Linux LiveCD. Which Linux based tool has the ability to change any user's password or to activate disabled Windows accounts?
A. CHNTPW
B. Cain & Abel
C. SET
D. John the Ripper
What is the correct PCAP filter to capture all TCP traffic going to or from host 192.168.0.125 on port 25?
A. tcp.src == 25 and ip.host == 192.168.0.125
B. host 192.168.0.125:25
C. port 25 and host 192.168.0.125
D. tcp.port == 25 and ip.host == 192.168.0.125
Which of the following Nmap commands would be used to perform a stack fingerprinting?
A. Nmap -O -p80
B. Nmap -hU -Q
C. Nmap -sT -p
D. Nmap -u -o -w2
E. Nmap -sS -0p targe
An NMAP scan of a server shows port 69 is open. What risk could this pose?
A. Unauthenticated access
B. Weak SSL version
C. Cleartext login
D. Web portal data leak
What is the main difference between a "Normal" SQL Injection and a "Blind" SQL Injection vulnerability?
A. The request to the web server is not visible to the administrator of the vulnerable application.
B. The attack is called “Blind” because, although the application properly filters user input, it is still vulnerable to code injection.
C. The successful attack does not show an error message to the administrator of the affected application.
D. The vulnerable application does not display errors with information about the injection results to the attacker.
One of your team members has asked you to analyze the following SOA record. What is the TTL? Rutgers.edu.SOA NS1.Rutgers.edu ipad.college.edu (200302028 3600 3600 604800 2400.)
A. 200303028
B. 3600
C. 604800
D. 2400
E. 60
F. 4800
Fingerprinting VPN firewalls is possible with which of the following tools?
A. Angry IP
B. Nikto
C. Ike-scan
D. Arp-scan
A company is using Windows Server 2003 for its Active Directory (AD). What is the most efficient way to crack the passwords for the AD users?
A. Perform a dictionary attack.
B. Perform a brute force attack.
C. Perform an attack with a rainbow table.
D. Perform a hybrid attack.
Free Access Full 312-50V9 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 312-50V9 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 312-50V9 certification journey!

