312-49V10 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 312-49V10 certification exam? Kickstart your success with our 312-49V10 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 312-49V10 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 312-49V10 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
In a complex forensic investigation, a CHFI investigator has been given a 2 TB suspect drive from which they must acquire relevant data as quickly as possible. The investigator uses a verified and tested data acquisition tool to accomplish this task. Given that the suspect drive cannot be retained, and considering the mandatory requirements of the selected tool, which of the following steps is the most critical for the investigator to ensure a forensically sound acquisition?
A. Prioritizing and acquiring only those data that are of evidentiary value
B. Testing lossless compression by applying an MD5, SHA-2, or SHA-3 hash on a file before and after compression
C. Using Microsoft disk compressions tools like DriveSpace and DoubleSpace to exclude slack disk space between the files
D. Compress files by using archiving tools like PKZip, WinZip, and WinRAR
Your organization is implementing a new database system and has chosen MySQL due to its pluggable storage engine capability and ability to handle parallel write operations securely. You are responsible for selecting the best-suited storage engine for your company's needs, which predominantly involves transactional processing, crash recovery, and high data consistency requirements. What would be the most appropriate choice?
A. InnoDB storage engine, because it supports traditional ACID and crash recovery, and is used in online transaction processing systems
B. Memory storage engine, because it offers in-memory tables and implements a hashing mechanism for faster data retrieval
C. MyISAM storage engine, because it offers unlimited data storage and high-speed data loads
D. BDB storage engine, because it provides an alternative to InnoDB and supports additional transaction methods such as COMMIT and ROLLBACK
A CHFI is analyzing suspicious activity on a company's AWS account. She suspects an unauthorized user accessed and deleted a crucial bucket object. To trace the potential perpetrator, she should primarily rely on the following:
A. S3 Server Access logs to understand actions performed on a bucket object
B. AWS CloudTrail logs to determine when and where the specific API calls were made
C. Amazon CloudWatch logs to monitor system and application log data in real time
D. Amazon VPC Flow Logs to scrutinize the IP traffic entering and leaving the specific VPC
Where does Encase search to recover NTFS files and folders?
A. MBR
B. MFT
C. Slack space
D. HAL
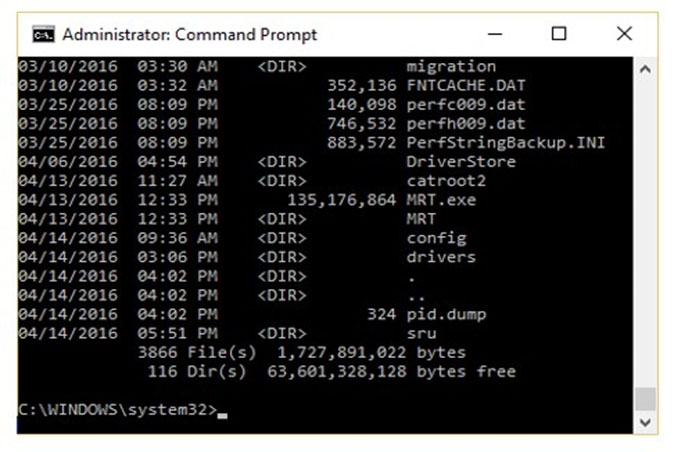
The given image displays information about date and time of installation of the OS along with service packs, patches, and sub-directories. What command or tool did the investigator use to view this output?
A. dir /o:d
B. dir /o:s
C. dir /o:e
D. dir /o:n
In the middle of a high-pressure cybercrime investigation, you stumble upon a cryptic message. It appears to be encoded with the ASCII standard. The encrypted message contains a combination of lower ASCII and higher ASCII codes. Which statement is the most accurate concerning the interpretation of this message?
A. The lower ASCII codes refer to non-printable system codes, while the higher ASCII codes represent alphanumeric characters and punctuation
B. Both lower and higher ASCII codes primarily contain alphanumeric characters and punctuation
C. ASCII codes at the lower end represent alphanumeric characters and punctuation. On the other hand, those at the higher end are typically used to denote non-printable system codes
D. The lower ASCII codes represent basic alphanumeric characters and punctuation, while the higher ASCII codes are generally used for graphics and non-ASCII characters in documents
Robert is a regional manager working in a reputed organization. One day, he suspected malware attack after unwanted programs started to popup after logging into his computer. The network administrator was called upon to trace out any intrusion on the computer and he/she finds that suspicious activity has taken place within Autostart locations. In this situation, which of the following tools is used by the network administrator to detect any intrusion on a system?
A. Hex Editor
B. Internet Evidence Finder
C. Process Monitor
D. Report Viewer
As a Computer Hacking Forensics Investigator, you are analyzing a TCP dump of network traffic during a suspected breach. During the investigation, you noticed that the “Packets dropped by kernel” count was unusually high. Given that the network has a high load, what could be the most probable reason for this situation?
A. The Tcpdump tool was run without the -c flag, causing it to capture packets indefinitely
B. The TCP packets were not matching the input expression of Tcpdump
C. The Boolean expression used with Tcpdump was too restrictive, missing some packets
D. The buffer space in the OS running Tcpdump was insufficient, leading to dropped packets
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
A. Closed
B. Open
C. Stealth
D. Filtered
When operating systems mark a cluster as used but not allocated, the cluster is considered as _________
A. Corrupt
B. Bad
C. Lost
D. Unallocated
When should an MD5 hash check be performed when processing evidence?
A. After the evidence examination has been completed
B. On an hourly basis during the evidence examination
C. Before and after evidence examination
D. Before the evidence examination has been completed
Adam, a forensic investigator, is investigating an attack on Microsoft Exchange Server of a large organization. As the first step of the investigation, he examined the PRIV.EDB file and found the source from where the mail originated and the name of the file that disappeared upon execution. Now, he wants to examine the MIME stream content. Which of the following files is he going to examine?
A. PRIV.STM
B. gwcheck.db
C. PRIV.EDB
D. PUB.EDB
You are using DriveSpy, a forensic tool and want to copy 150 sectors where the starting sector is 1709 on the primary hard drive. Which of the following formats correctly specifies these sectors?
A. 0:1000, 150
B. 0:1709, 150
C. 1:1709, 150
D. 0:1709-1858
What type of analysis helps to identify the time and sequence of events in an investigation?
A. Time-based
B. Functional
C. Relational
D. Temporal
When reviewing web logs, you see an entry for resource not found in the HTTP status code field. What is the actual error code that you would see in the log for resource not found?
A. 202
B. 404
C. 606
D. 999
Investigators can use the Type Allocation Code (TAC) to find the model and origin of a mobile device. Where is TAC located in mobile devices?
A. International Mobile Equipment Identifier (IMEI)
B. Integrated circuit card identifier (ICCID)
C. International mobile subscriber identity (IMSI)
D. Equipment Identity Register (EIR)
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
A. 18 U.S.C. 1029
B. 18 U.S.C. 1362
C. 18 U.S.C. 2511
D. 18 U.S.C. 2703
In a cyber-forensic investigation, a CHFI expert found a Linux system unexpectedly booting into a different OS kernel. The system was configured with the Grand Unified Bootloader (GRUB). The expert suspects that an attacker may have tampered with the bootloader stage of the Linux boot process. Which one of the following is NOT a step performed during the bootloader stage in a normal Linux boot process?
A. Execution of the Linuxrc program to generate the real file system for the kernel
B. Detecting the device that contains the file system and loading the necessary modules
C. Loading the kernel into memory
D. Loading the Linux kernel and optional initial RAM disk
Pick the statement which does not belong to the Rule 804. Hearsay Exceptions; Declarant Unavailable.
A. Statement of personal or family history
B. Prior statement by witness
C. Statement against interest
D. Statement under belief of impending death
A section of your forensics lab houses several electrical and electronic equipment. Which type of fire extinguisher you must install in this area to contain any fire incident?
A. Class B
B. Class D
C. Class C
D. Class A
Chris has been called upon to investigate a hacking incident reported by one of his clients. The company suspects the involvement of an insider accomplice in the attack. Upon reaching the incident scene, Chris secures the physical area, records the scene using visual media. He shuts the system down by pulling the power plug so that he does not disturb the system in any way. He labels all cables and connectors prior to disconnecting any. What do you think would be the next sequence of events?
A. Connect the target media; prepare the system for acquisition; Secure the evidence; Copy the media
B. Prepare the system for acquisition; Connect the target media; copy the media; Secure the evidence
C. Connect the target media; Prepare the system for acquisition; Secure the evidence; Copy the media
D. Secure the evidence; prepare the system for acquisition; Connect the target media; copy the media
Sniffers that place NICs in promiscuous mode work at what layer of the OSI model?
A. Network
B. Transport
C. Physical
D. Data Link
Fill in the missing Master Boot Record component. 1. Master boot code 2. Partition table 3. ____________
A. Signature word
B. Volume boot record
C. Boot loader
D. Disk signature
Preparing an image drive to copy files to is the first step in Linux forensics. For this purpose, what would the following command accomplish? dcfldd if=/dev/zero of=/dev/hda bs=4096 conv=noerror, sync
A. Fill the disk with zeros
B. Low-level format
C. Fill the disk with 4096 zeros
D. Copy files from the master disk to the slave disk on the secondary IDE controller
Tyler is setting up a wireless network for his business that he runs out of his home. He has followed all the directions from the ISP as well as the wireless router manual. He does not have any encryption set and the SSID is being broadcast. On his laptop, he can pick up the wireless signal for short periods of time, but then the connection drops and the signal goes away. Eventually the wireless signal shows back up, but drops intermittently. What could be Tyler issue with his home wireless network?
A. Computers on his wired network
B. Satellite television
C. 2.4Ghz Cordless phones
D. CB radio
Which of the following Windows event logs record events related to device drives and hardware changes?
A. Application log
B. Security log
C. Forwarded events log
D. System log
When investigating a system, the forensics analyst discovers that malicious scripts were injected into benign and trusted websites. The attacker used a web application to send malicious code, in the form of a browser side script, to a different end-user. What attack was performed here?
A. SQL injection attack
B. Cookie poisoning attack
C. Cross-site scripting attack
D. Brute-force attack
When investigating a potential e-mail crime, what is your first step in the investigation?
A. Trace the IP address to its origin
B. Write a report
C. Determine whether a crime was actually committed
D. Recover the evidence
Which part of the Windows Registry contains the user's password file?
A. HKEY_LOCAL_MACHINE
B. HKEY_CURRENT_CONFIGURATION
C. HKEY_USER
D. HKEY_CURRENT_USER
Jeff is a forensics investigator for a government agency's cyber security office. Jeff is tasked with acquiring a memory dump of a Windows 10 computer that was involved in a DDoS attack on the government agency's web application. Jeff is onsite to collect the memory. What tool could Jeff use?
A. Memcheck
B. RAMMapper
C. Autopsy
D. Volatility
In a computer that has Dropbox client installed, which of the following files related to the Dropbox client store information about local Dropbox installation and the Dropbox user account, along with email IDs linked with the account?
A. config.db
B. install.db
C. sigstore.db
D. filecache.db
A computer forensics investigator or forensic analyst is a specially trained professional who works with law enforcement as well as private businesses to retrieve information from computers and other types of data storage devices. For this, the analyst should have an excellent working knowledge of all aspects of the computer. Which of the following is not a duty of the analyst during a criminal investigation?
A. To recover data from suspect devices
B. To fill the chain of custody
C. To create an investigation report
D. To enforce the security of all devices and software in the scene
A cybersecurity forensic investigator analyzes log files to investigate an SQL Injection attack. While going through the Apache across.log, they come across a GET request from the IP 10.0.0.19 containing an encoded query string: GET /sqli/examplel.php?name=root' UniON SeLeCT 1,table_name,3,4,5 From information_schema.tables where Table_Schema=DatabasE() limit 1,2--- What is the intention behind the attacker’s query?
A. To erase the data in the specific tables of the database
B. To retrieve the names of the tables in the database
C. To bypass the website’s authentication mechanism and view all user details
D. To manipulate the order of the columns in the database
Which of the following is found within the unique instance ID key and helps investigators to map the entry from USBSTOR key to the MountedDevices key?
A. ParentIDPrefix
B. LastWrite
C. UserAssist key
D. MRUListEx key
If an attacker's computer sends an IPID of 31400 to a zombie computer on an open port in IDLE scanning, what will be the response?
A. The zombie will not send a response
B. 31402
C. 31399
D. 31401
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
A. SAM
B. AMS
C. Shadow file
D. Password.conf
In a computer forensics investigation, what describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. rules of evidence
B. law of probability
C. chain of custody
D. policy of separation
The MAC attributes are timestamps that refer to a time at which the file was last modified or last accessed or originally created. Which of the following file systems store MAC attributes in Coordinated Universal Time (UTC) format?
A. File Allocation Table (FAT)
B. New Technology File System (NTFS)
C. Hierarchical File System (HFS)
D. Global File System (GFS)
During an incident response to a data breach in a company's AWS environment, a forensic investigator is tasked to analyze and extract data from different storage types for further examination. What would be the most appropriate and effective course of action given that Amazon S3, EBS, and EFS were used?
A. Implement ACL permissions for S3 buckets, and attach the affected EFS to a Linux instance for data extraction
B. Create IAM policies to restrict access, and proceed with data extraction from EBS and EFS storage types
C. Extract all data directly from Amazon S3 and EBS, and attach the EFS to a Linux instance for data extraction
D. Snapshot the affected EBS volumes and S3 buckets, and mount EFS to a Linux instance for analysis
After attending a CEH security seminar, you make a list of changes you would like to perform on your network to increase its security. One of the first things you change is to switch the RestrictAnonymous setting from 0 to 1 on your servers. This, as you were told, would prevent anonymous users from establishing a null session on the server. Using Userinfo tool mentioned at the seminar, you succeed in establishing a null session with one of the servers. Why is that?
A. RestrictAnonymous must be set to “10” for complete security
B. RestrictAnonymous must be set to “3” for complete security
C. RestrictAnonymous must be set to “2” for complete security
D. There is no way to always prevent an anonymous null session from establishing
Consider that you are investigating a machine running an Windows OS released prior to Windows Vista. You are trying to gather information about the deleted files by examining the master database file named INFO2 located at C:Recycler. You read an entry named "Dd5.exe". What does Dd5.exe mean?
A. D drive. fifth file deleted, a .exe file
B. D drive, fourth file restored, a .exe file
C. D drive, fourth file deleted, a .exe file
D. D drive, sixth file deleted, a .exe file
You are assisting a Department of Defense contract company to become compliant with the stringent security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers. What type of firewall must you implement to abide by this policy?
A. Packet filtering firewall
B. Circuit-level proxy firewall
C. Application-level proxy firewall
D. Stateful firewall
Company ABC has employed a firewall, IDS, Antivirus, Domain Controller, and SIEM. The company's domain controller goes down. From which system would you begin your investigation?
A. Domain Controller
B. Firewall
C. SIEM
D. IDS
After an unexpected shutdown of a company's database server, the IT forensics team is tasked with collecting data from the Database Plan Cache to investigate potential issues. What query should they use to retrieve the SQL text of all cached entries and acquire additional aggregate performance statistics?
A. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_plan_attributes(plan_handle) followed by: select * from sys.dm_exec_query_stats
B. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_sql_text(plan_handle) followed by: select * from sys.dm_exec_plan_attributes(plan_handle)
C. Use: select * from sys.dm_exec_sql_text(plan_handle) cross apply sys.dm_exec_cached_plans followed by: select * from sys.dm_exec_query_stats
D. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_sql_text(plan_handle) followed by: select * from sys.dm_exec_query_stats
Which password cracking technique uses details such as length of password, character sets used to construct the password, etc.?
A. Dictionary attack
B. Brute force attack
C. Rule-based attack
D. Man in the middle attack
While collecting Active Transaction Logs using SQL Server Management Studio, the query Select * from ::fn_dblog(NULL, NULL) displays the active portion of the transaction log file. Here, assigning NULL values implies?
A. Start and end points for log sequence numbers are specified
B. Start and end points for log files are not specified
C. Start and end points for log files are specified
D. Start and end points for log sequence numbers are not specified
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
A. Security Administrator
B. Network Administrator
C. Director of Information Technology
D. Director of Administration
During a forensic investigation of a system suspected to be involved in cybercrime, the investigator observes discrepancies between the $STANDARD_INFORMATION and $FILE_NAME creation dates for some files. As part of the investigation process, the investigator also noted that a utility called BCWipe was found installed on the system. What would be the investigator's most plausible conclusion based on these observations?
A. The system user used BCWipe to delete specific files securely
B. The system was compromised with malware that altered the metadata
C. The files were encrypted using the BCWipe utility
D. The timestamps for some files have been manipulated, possibly as an anti-forensic measure
What will the following command accomplish? dd if=/dev/xxx of=mbr.backup bs=512 count=1
A. Back up the master boot record
B. Restore the master boot record
C. Mount the master boot record on the first partition of the hard drive
D. Restore the first 512 bytes of the first partition of the hard drive
During an investigation, a forensics analyst discovers an unusual increase in outbound network traffic, network traffic traversing on non-standard ports, and multiple failed login attempts on a host system. The analyst also found that certain programs were using these unusual ports, appearing to be legitimate. If these are the primary Indicators of Compromise, what should be the next immediate step in the investigation to contain the intrusion effectively?
A. Enforcing stringent password policies and re-authenticating all users to prevent further login anomalies
B. Examining the logs for repeated requests for the same file, indicating a possible exploit attempt
C. Analyzing Uniform Resource Locators for any signs of phishing or spamming activities
D. Conducting a deep dive into user-agent strings to determine if there is any spoofing of device OS and browser information
Free Access Full 312-49V10 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 312-49V10 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 312-49V10 certification journey!