312-49 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 312-49 certification exam? Kickstart your success with our 312-49 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 312-49 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 312-49 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
What type of equipment would a forensics investigator store in a StrongHold bag?
A. PDAPDA?
B. Backup tapes
C. Hard drives
D. Wireless cards
To preserve digital evidence, an investigator should ____________________.
A. Make two copies of each evidence item using a single imaging tool
B. Make a single copy of each evidence item using an approved imaging tool
C. Make two copies of each evidence item using different imaging tools
D. Only store the original evidence item
Wireless access control attacks aim to penetrate a network by evading WLAN access control measures such as AP MAC filters and Wi-Fi port access controls. Which of the following wireless access control attacks allow the attacker to set up a rogue access point outside the corporate perimeter and then lure the employees of the organization to connect to it?
A. Ad hoc associations
B. Client mis-association
C. MAC spoofing
D. Rogue access points
If an attacker's computer sends an IPID of 31400 to a zombie computer on an open port in IDLE scanning, what will be the response?
A. The zombie will not send a response
B. 31402
C. 31399
D. 31401
An executive has leaked the company trade secrets through an external drive. What process should the investigation team take if they could retrieve his system?
A. Postmortem Analysis
B. Real-Time Analysis
C. Packet Analysis
D. Malware Analysis
What is kept in the following directory? HKLMSECURITYPolicySecrets
A. Cached password hashes for the past 20 users
B. Service account passwords in plain text
C. IAS account names and passwords
D. Local store PKI Kerberos certificates
Why should you note all cable connections for a computer you want to seize as evidence?
A. to know what outside connections existed
B. in case other devices were connected
C. to know what peripheral devices exist
D. to know what hardware existed
A forensics investigator is searching the hard drive of a computer for files that were recently moved to the Recycle Bin. He searches for files in C:RECYCLED using a command line tool but does not find anything. What is the reason for this?
A. He should search in C:WindowsSystem32RECYCLED folder
B. The Recycle Bin does not exist on the hard drive
C. The files are hidden and he must use switch to view them
D. Only FAT system contains RECYCLED folder and not NTFS
Which MySQL log file contains information on server start and stop?
A. Slow query log file
B. General query log file
C. Binary log
D. Error log file
During the trial, an investigator observes that one of the principal witnesses is severely ill and cannot be present for the hearing. He decides to record the evidence and present it to the court. Under which rule should he present such evidence?
A. Rule 1003: Admissibility of Duplicates
B. Limited admissibility
C. Locard’s Principle
D. Hearsay
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
A. Cracks every password in 10 minutes
B. Distribute processing over 16 or fewer computers
C. Support for Encrypted File System
D. Support for MD5 hash verification
A honey pot deployed with the IP 172.16.1.108 was compromised by an attacker. Given below is an excerpt from a Snort binary capture of the attack. Decipher the activity carried out by the attacker by studying the log. Please note that you are required to infer only what is explicit in the excerpt. (Note: The student is being tested on concepts learnt during passive OS fingerprinting, basic TCP/IP connection concepts and the ability to read packet signatures from a sniff dump.) 03/15-20:21:24.107053 211.185.125.124:3500 -> 172.16.1.108:111 TCP TTL:43 TOS:0x0 ID:29726 IpLen:20 DgmLen:52 DF ***A**** Seq: 0x9B6338C5 Ack: 0x5820ADD0 Win: 0x7D78 TcpLen: 32 TCP Options (3) => NOP NOP TS: 23678634 2878772 =+=+=+=+=+=+=+=+=+=+=+=+=+= +=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+= 03/15-20:21:24.452051 211.185.125.124:789 -> 172.16.1.103:111 UDP TTL:43 TOS:0x0 ID:29733 IpLen:20 DgmLen:84 Len: 64 - 01 0A 8A 0A 00 00 00 00 00 00 00 02 00 01 86 A0 . ............. 00 00 00 02 00 00 00 03 00 00 00 00 00 00 00 00 ................ 00 00 00 00 00 00 00 00 00 01 86 B8 00 00 00 01 . .............. 00 00 00 11 00 00 00 00 ........ =+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+=+= 03/15-20:21:24.730436 211.185.125.124:790 -> 172.16.1.103:32773 UDP TTL:43 TOS:0x0 ID:29781 IpLen:20 DgmLen:1104 Len: 1084 - 47 F7 9F 63 00 00 00 00 00 00 00 02 00 01 86 B8
A. The attacker has conducted a network sweep on port 111
B. The attacker has scanned and exploited the system using Buffer Overflow
C. The attacker has used a Trojan on port 32773
D. The attacker has installed a backdoor
Kimberly is studying to be an IT security analyst at a vocational school in her town. The school offers many different programming as well as networking languages. What networking protocol language should she learn that routers utilize?
A. ATM
B. UDP
C. BPG
D. OSPF
One technique for hiding information is to change the file extension from the correct one to the one that might not be noticed by an investigator. For example, [1] extension?
A. The file header
B. The File Allocation Table
C. The file footer
D. The sector map
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information. You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
A. Ping sweep
B. Nmap
C. Netcraft
D. Dig
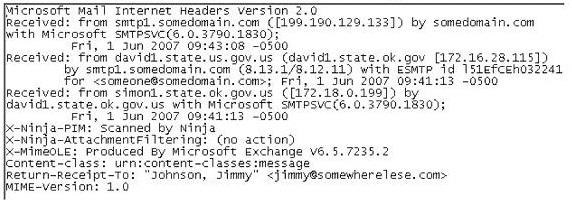
In the following email header, where did the email first originate from?
A. Somedomain.com
B. Smtp1.somedomain.com
C. Simon1.state.ok.gov.us
D. David1.state.ok.gov.us
What does 254 represent in ICCID 89254021520014515744?
A. Industry Identifier Prefix
B. Country Code
C. Individual Account Identification Number
D. Issuer Identifier Number
John and Hillary works at the same department in the company. John wants to find out Hillary's network password so he can take a look at her documents on the file server. He enables Lophtcrack program to sniffing mode. John sends Hillary an email with a link to Error! Reference source not found. What information will he be able to gather from this?
A. Hillary network username and password hash
B. The SID of Hillary network account
C. The SAM file from Hillary computer
D. The network shares that Hillary has permissions
During an investigation of an XSS attack, the investigator comes across the term "[a-zA-Z0-9%]+" in analyzed evidence details. What is the expression used for?
A. Checks for upper and lower-case alphanumeric string inside the tag, or its hex representation
B. Checks for forward slash used in HTML closing tags, its hex or double-encoded hex equivalent
C. Checks for opening angle bracket, its hex or double-encoded hex equivalent
D. Checks for closing angle bracket, hex or double-encoded hex equivalent
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive? 22,164 cylinders/disk 80 heads/cylinder 63 sectors/track
A. 53.26 GB
B. 57.19 GB
C. 11.17 GB
D. 10 GB
What is the slave device connected to the secondary IDE controller on a Linux OS referred to?
A. hda
B. hdd
C. hdb
D. hdc
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/ logs/error.log in Linux. Identify the Apache error log from the following logs.
A. http://victim.com/scripts/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..% c0%af../..%c0%af../winnt/system32/cmd.exe?/c+dir+C:Winnt system32LogfilesW3SVC1
B. [Wed Oct 11 14:32:52 2000] [error] [client 127.0.0.1] client denied by server configuration: /export/home/live/ap/htdocs/test
C. 127.0.0.1 – frank [10/Oct/2000:13:55:36 -0700]”GET /apache_pb.gif HTTP/1.0″ 200 2326
D. 127.0.0.1 – – [10/Apr/2007:10:39:11 +0300] ] [error] “GET /apache_pb.gif HTTP/1.0” 200 2326
You are working on a thesis for your doctorate degree in Computer Science. Your thesis is based on HTML, DHTML, and other web-based languages and how they have evolved over the years. You navigate to archive. org and view the HTML code of news.com. You then navigate to the current news.com website and copy over the source code. While searching through the code, you come across something abnormal: What have you found?
A. Web bug
B. CGI code
C. Trojan.downloader
D. Blind bug
What is the CIDR from the following screenshot?
A. /24A./24A./24
B. /32 B./32 B./32
C. /16 C./16 C./16
D. /8D./8D./8
Which tool does the investigator use to extract artifacts left by Google Drive on the system?
A. PEBrowse Professional
B. RegScanner
C. RAM Capturer
D. Dependency Walker
Gary, a computer technician, is facing allegations of abusing children online by befriending them and sending them illicit adult images from his office computer. What type of investigation does this case require?
A. Administrative Investigation
B. Criminal Investigation
C. Both Criminal and Administrative Investigation
D. Civil Investigation
Watson, a forensic investigator, is examining a copy of an ISO file stored in CDFS format. What type of evidence is this?
A. Data from a CD copied using Windows
B. Data from a CD copied using Mac-based system
C. Data from a DVD copied using Windows system
D. Data from a CD copied using Linux system
You are called by an author who is writing a book and he wants to know how long the copyright for his book will last after he has the book published?
A. 70 years
B. the life of the author
C. the life of the author plus 70 years
D. copyrights last forever
You are working as a Computer forensics investigator for a corporation on a computer abuse case. You discover evidence that shows the subject of your investigation is also embezzling money from the company. The company CEO and the corporate legal counsel advise you to contact law enforcement and provide them with the evidence that you have found. The law enforcement officer that responds requests that you put a network sniffer on your network and monitor all traffic to the subject's computer. You inform the officer that you will not be able to comply with that request because doing so would:
A. Violate your contract
B. Cause network congestion
C. Make you an agent of law enforcement
D. Write information to the subject’s hard drive
Melanie was newly assigned to an investigation and asked to make a copy of all the evidence from the compromised system. Melanie did a DOS copy of all the files on the system. What would be the primary reason for you to recommend a disk imaging tool?
A. A disk imaging tool would check for CRC32s for internal self-checking and validation and have MD5 checksum
B. Evidence file format will contain case data entered by the examiner and encrypted at the beginning of the evidence file
C. A simple DOS copy will not include deleted files, file slack and other information
D. There is no case for an imaging tool as it will use a closed, proprietary format that if compared to the original will not match up sector for sector
Bob has encountered a system crash and has lost vital data stored on the hard drive of his Windows computer. He has no cloud storage or backup hard drives. he wants to recover all those data, which includes his personal photos, music, documents, videos, official email, etc. Which of the following tools shall resolve Bob's purpose?
A. Colasoft’s Capsa
B. Recuva
C. Cain & Abel
D. Xplico
When obtaining a warrant, it is important to:
A. particularlydescribe the place to be searched and particularly describe the items to be seized
B. generallydescribe the place to be searched and particularly describe the items to be seized
C. generallydescribe the place to be searched and generally describe the items to be seized
D. particularlydescribe the place to be searched and generally describe the items to be seized
An attacker has compromised a cloud environment of a company and used the employee information to perform an identity theft attack. Which type of attack is this?
A. Cloud as a subject
B. Cloud as a tool
C. Cloud as an object
D. Cloud as a service
Pick the statement which does not belong to the Rule 804. Hearsay Exceptions; Declarant Unavailable.
A. Statement of personal or family history
B. Prior statement by witness
C. Statement against interest
D. Statement under belief of impending death
Smith, as a part his forensic investigation assignment, seized a mobile device. He was asked to recover the Subscriber Identity Module (SIM card) data in the mobile device. Smith found that the SIM was protected by a Personal Identification Number (PIN) code, but he was also aware that people generally leave the PIN numbers to the defaults or use easily guessable numbers such as 1234. He made three unsuccessful attempts, which blocked the SIM card. What can Jason do in this scenario to reset the PIN and access SIM data?
A. He should contact the network operator for a Temporary Unlock Code (TUK)
B. Use system and hardware tools to gain access
C. He can attempt PIN guesses after 24 hours
D. He should contact the network operator for Personal Unlock Number (PUK)
Software firewalls work at which layer of the OSI model?
A. Application
B. Network
C. Transport
D. Data Link
Why would you need to find out the gateway of a device when investigating a wireless attack?
A. The gateway will be the IP of the proxy server used by the attacker to launch the attack
B. The gateway will be the IP of the attacker computer
C. The gateway will be the IP used to manage the RADIUS server
D. The gateway will be the IP used to manage the access point
Michael works for Kimball Construction Company as senior security analyst. As part of yearly security audit, Michael scans his network for vulnerabilities. Using Nmap, Michael conducts XMAS scan and most of the ports scanned do not give a response. In what state are these ports?
A. Closed
B. Open
C. Stealth
D. Filtered
Which of the following is NOT a graphics file?
A. Picture1.tga
B. Picture2.bmp
C. Picture3.nfo
D. Picture4.psd
If you discover a criminal act while investigating a corporate policy abuse, it becomes a publicsector investigation and should be referred to law enforcement?
A. true
B. false
What should you do when approached by a reporter about a case that you are working on or have worked on?
A. Refer the reporter to the attorney that retained you
B. Say, “no comment”
C. Answer all the reporter’s questions as completely as possible
D. Answer only the questions that help your case
On an Active Directory network using NTLM authentication, where on the domain controllers are the passwords stored?
A. SAM
B. AMS
C. Shadow file
D. Password.conf
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.What RAID level is represented here?
A. RAID Level 0
B. RAID Level 5
C. RAID Level 3
D. RAID Level 1
%3cscript%3ealert("XXXXXXXX")%3c/script%3e is a script obtained from a Cross-Site Scripting attack. What type of encoding has the attacker employed?
A. Double encoding
B. Hex encoding
C. Unicode
D. Base64
What type of attack sends SYN requests to a target system with spoofed IP addresses?
A. SYN flood
B. Ping of death
C. Cross site scripting
D. Land
Which among the following search warrants allows the first responder to get the victim's computer information such as service records, billing records, and subscriber information from the service provider?
A. Citizen Informant Search Warrant
B. Electronic Storage Device Search Warrant
C. John Doe Search Warrant
D. Service Provider Search Warrant
You are carrying out the last round of testing for your new website before it goes live. The website has many dynamic pages and connects to a SQL backend that accesses your product inventory in a database. You come across a web security site that recommends inputting the following code into a search field on web pages to check for vulnerabilities: When you type this and click on search, you receive a pop-up window that says: "This is a test." What is the result of this test?
A. Your website is vulnerable to CSS
B. Your website is not vulnerable
C. Your website is vulnerable to SQL injection
D. Your website is vulnerable to web bugs
Jason is the security administrator of ACMA metal Corporation. One day he notices the company's Oracle database server has been compromised and the customer information along with financial data has been stolen. The financial loss will be in millions of dollars if the database gets into the hands of the competitors. Jason wants to report this crime to the law enforcement agencies immediately. Which organization coordinates computer crimes investigations throughout the United States?
A. Internet Fraud Complaint Center
B. Local or national office of the U.S. Secret Service
C. National Infrastructure Protection Center
D. CERT Coordination Center
Steven has been given the task of designing a computer forensics lab for the company he works for. He has found documentation on all aspects of how to design a lab except the number of exits needed. How many exits should Steven include in his design for the computer forensics lab?
A. Three
B. One
C. Two
D. Four
What technique is used by JPEGs for compression?
A. ZIP
B. TCD
C. DCT
D. TIFF-8
Free Access Full 312-49 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 312-49 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 312-49 certification journey!