300-820 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 300-820 certification exam? Kickstart your success with our 300-820 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 300-820 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 300-820 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Refer to the exhibit. Which SPF record is valid for mycompany.com?
A. v=spf1 a mx ip4:199.209.31.2 -all
B. v=spf1 a mx ip4:10.1.10.23 -all
C. v=spf1 a mx ip4:199.209.31.21 -all
D. v=spf1 a mx ip4:172.16.18.230 -all
Which part of a hybrid cloud-based deployment with Cisco Webex Messenger Service is used for meeting capabilities?
A. Cisco Unified CM is always used for meeting capabilities.
B. Depending on the media flow, the Webex Meeting Center or local Cisco Unified CM meeting resources are used for meeting capabilities.
C. Depending on the origin of the user, the Webex Meeting Center or local Cisco Unified Communications Manager meeting resources are used for meeting capabilities.
D. Cisco Webex Meeting Center is always used for meeting capabilities.
A MRA deployment is being configured where one of the requirements is for registered Jabber users to pull directory photos from an internal server. What should be configured on the Expressway-C so that MRA registered clients reach this server?
A. The directory photo server FQDN must be added to the Expressway-C certificate
B. A search rule must be created to route the requests to Cisco UCM
C. A neighbor zone must be created to the directory photo server
D. The directory photo server must be added to the HTTP allow list
In a Mobile and Remote Access deployment, where must communications be encrypted with TLS?
A. Cisco Expressway-E and endpoints outside the enterprise
B. Cisco Expressway-C, Cisco Unified Communications Manager, and IM&P
C. Cisco Expressway-C, Cisco Expressway-E, and Cisco Unified Communications Manager
D. Cisco Expressway-C, Cisco Expressway-E, and endpoints outside the enterprise
Which two licenses are required for the B2B feature to work? (Choose two.)
A. Traversal Server
B. TURN Relays
C. Rich Media Sessions
D. Advanced Networking
E. Device Provisioning
What is a description of an Interactive Connectivity Establishment?
A. It is used by B2BUA to keep the firewall ports opened for inbound/outbound calls.
B. It allows Mobile and Remote Access endpoints to connect video calls signaling peer-to-peer.
C. It allows calling external endpoints with reduced overhead under VPN connections.
D. It is used to find the best media path between network elements in traversal calls.
Which action is required when using Cisco Jabber for Cloud with Cisco Webex Messenger?
A. Configure, extend, and connect.
B. Configure policies.
C. Configure service discovery for remote access.
D. Configure desk phone control.
An organization has strict rules for meeting specific criteria to approve certificate authorities. A Cisco ESA administrator within the organization is receiving complaints about failed inbound emails from a domain. The administrator is also seeing TLS certificate errors. What is the reason for this issue?
A. Firewall inspection is preventing transmission of certificate data.
B. The certificate authority is not on the system list.
C. The TLSv1.0 protocol is not supported.
D. The certificate chain is broken.
An administrator notices that incoming emails with certain attachments do not get delivered to all recipients when the emails have multiple recipients in different domains like cisco.com and test.com. The same emails when sent only to recipients in cisco.com are delivered properly. How must the Cisco ESA be configured to avoid this behavior?
A. Modify DLP configuration to ensure that all attachments are permitted for test.com.
B. Modify DLP configuration to exempt DLP scanning for messages sent to test.com domain.
C. Modify mail policies so email recipients do not match multiple policies.
D. Modify mail policies for cisco.com to ensure that emails are not dropped.
Which scenario prevents a message from being sent to the quarantine as an action in the scan behavior on Cisco ESA?
A. A policy quarantine is missing.
B. More than one email pipeline is defined.
C. The “modify the message subject” is already set.
D. The “add custom header” action is performed first.
Which two steps are needed to disable local spam quarantine before external quarantine is enabled? (Choose two.)
A. Uncheck the Enable Spam Quarantine check box.
B. Select Monitor and click Spam Quarantine.
C. Check the External Safelist/Blocklist check box.
D. Select External Spam Quarantine and click on Configure.
E. Select Security Services and click Spam Quarantine.
When the Cisco ESA is configured to perform antivirus scanning, what is the default timeout value?
A. 30 seconds
B. 90 seconds
C. 60 seconds
D. 120 seconds
Refer to the exhibit. Which configuration allows the Cisco ESA to scan for executables inside the zip and apply the action as per the content filter?
A. Modify the content filter to look for .exe filename instead of executable filetype.
B. Configure the recursion depth to a higher value.
C. Configure the maximum attachment size to a higher value.
D. Modify the content filter to look for attachment filetype of compressed.
A network engineer is implementing a virus outbreak filter on a Cisco ESA by using the Outbreak Filters feature with plans to perform an additional scan by using a content filter. Which action must be taken by the Outbreak Filters?
A. Scan processed messages by using two engines simultaneously.
B. Send a copy of messages to quarantine.
C. Send processed messages to the Cisco ESA.
D. Scan processed messages by using a secondary instance of the Cisco ESA.
What is a valid content filter action?
A. decrypt on delivery
B. quarantine
C. skip antispam
D. archive
When outbreak filters are configured, which two actions are used to protect users from outbreaks? (Choose two.)
A. redirect
B. return
C. drop
D. delay
E. abandon
An organization wants to prevent proprietary patent documents from being shared externally via email. The network administrator reviewed the DLP policies on the Cisco ESA and could not find an existing policy with the appropriate matching patterns. Which type of DLP policy template must be used to create a policy that meets this requirement?
A. regulatory compliance
B. acceptable use
C. custom policy
D. privacy protection
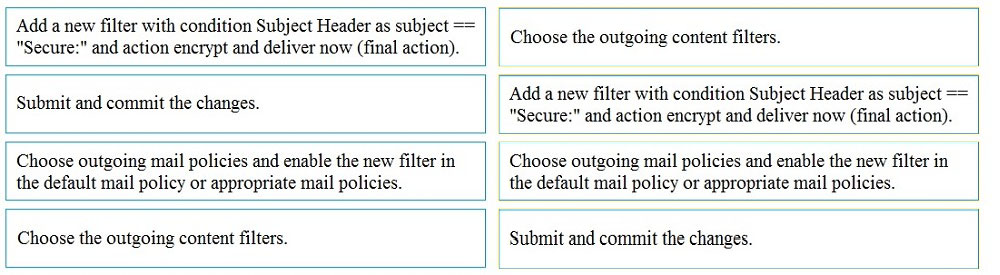
DRAG DROP - An Encryption Profile has been set up on the Cisco ESA. Drag and drop the steps from the left for creating an outgoing content filter to encrypt emails that contains the subject "Secure:" into the correct order on the right. Select and Place:
Which mode should be used when Call Policy is configured on Expressways?
A. extended CPL
B. local CPL, policy service, and off
C. on
D. remote CPL
A company has a single Expressway-E that exhibits high resource utilization. An engineer checks the logs and finds numerous fraudulent attempts from sip: 200@cisco.com . Where must the engineer go to configure a call policy rule and block the desired URI?
A. Call History Configuration > Call Policy > Rules
B. Configuration > Call History > Policy > Rules
C. Configuration > Call Policy > Rules
D. Configuration > Policy > Inbound > Rules
An engineer reviews the configuration of a pair of Expressway servers for a company with the domain example.com. The company allows toll fraud calls to reach the Cisco UCM only when it expects externally registered devices to call internal 5-digit extensions. The search history shows that the fraudulent calls have a destination URI of 8 or more digits and several domains. What must the engineer configure to prevent all toll fraud calls from going past the Expressway-E to the internal network?
A. search rules to only route calls with a destination URI of 5 to 8 digits long on the Expressway-E
B. CPL that blocks calls with a destination domain other than example.com on the Expressway-C.
C. search rules to only route calls with a destination domain of example.com on the Expressway-E
D. CPL to block calls with a destination URI with 8 or more digits on the Expressway-E
An organization wants to enable a Cisco Webex connector to synchronize all employees automatically with Cisco Webex instead of using a manual list. Where is the Webex Hybrid Directory Service configured?
A. Install Cisco Directory Connector on a Microsoft Windows Domain server and configure the software and Webex Control Hub.
B. Enable the directory service in Cisco Unified Communications Manager under Cisco Unified Serviceability and add the service in Webex Control Hub.
C. Enable the directory service on Cisco Expressway Edge for Office 365 or Cisco Expressway Core for internal Active Directory and add the service in Webex Control Hub.
D. Install the Cisco Express Connector and configure the device in Cisco Unified Communications Manager under Cisco Unified Serviceability and add the service in Webex Control Hub.
Which zone is required between Expressway-E and Expressway-C in Mobile and Remote Access deployments?
A. Unified Communications traversal zone
B. neighbor zone
C. DNS zone
D. traversal zone
Which two statements about Mobile and Remote Access certificate are true? (Choose two.)
A. Expressway Core can use private CA signed certificate.
B. You must upload the root certificates in the phone trust store.
C. Expressway must generate certificate signing request.
D. Expressway Edge must use public CA signed certificate.
E. The Jabber client can work with public or private CA signed certificate.
What is the name of the Webex core service that delivers group messaging, one-to-one messaging, presence, and file sharing?
A. Cisco Webex Messaging
B. Cisco Webex App
C. Cisco Webex ONE
D. Cisco Jabber Online
Email encryption is configured on a Cisco ESA that uses CRES. Which action is taken on a message when CRES is unavailable?
A. It is requeued.
B. It is sent in clear text.
C. It is dropped and an error message is sent to the sender.
D. It is encrypted by a Cisco encryption appliance.

Refer to the exhibits. What must be done to enforce end user authentication before accessing quarantine?
A. Enable SPAM notification and use LDAP for authentication.
B. Enable SPAM Quarantine Notification and add the %quarantine_url% variable.
C. Change the end user quarantine access from None authentication to SAAS.
D. Change the end user quarantine access setting from None authentication to Mailbox.
Which two Cisco ESA features are used to control email delivery based on the sender? (Choose two.)
A. incoming mail policies
B. spam quarantine
C. outbreak filter
D. safelists
E. blocklists
Which statement about the Cisco Webex hybrid service is true?
A. Expressway Connector is required for an on-premises Exchange server.
B. Hybrid Message service works only with Jabber cloud deployment.
C. Directory Connector is required for Azure AD.
D. Directory Connector must be deployed for OBTP to work with on-premises video devices.
A Cisco ESA administrator is creating a Mail Flow Policy to receive outbound email from Microsoft Exchange. Which Connection Behavior must be selected to properly process the messages?
A. Delay
B. Accept
C. Relay
D. Reject
When virtual gateways are configured, which two distinct attributes are allocated to each virtual gateway address? (Choose two.)
A. domain
B. IP address
C. DNS server address
D. DHCP server address
E. external spam quarantine
An administrator made changes to a directory connector for Webex AD synchronization. The number of users synchronized is quite large and the change should affect only a limited number of users. How can the administrator check the result before executing the synchronization?
A. Initiate an incremental synchronization from the Director Connector app on the on-premises Windows server because it will ask to save the changes.
B. Initiate a dry run of an incremental synchronization from the Director Connector app on the on-premises Windows server.
C. Initiate a dry run of an incremental synchronization from the Director Connector in Control Hub.
D. Initiate an incremental synchronization from the Director Connector in Control Hub because it will ask to save changes.
An engineer is deploying Mobile and Remote Access to allow external Cisco Jabber users to sign into a Cisco UCM cluster via Cisco Expressways. The users will sign-in in the format username@cisco.com . Contact photos for Jabber are hosted on a webserver with the FQDN of phonebook cisco.com. Which configuration must be completed to allow external Jabber users to see contact photos?
A. An HTTP allow list entry must be made on the Expressway-E for phonebook cisco.com.
B. A SIP allow list entry must be made on the Expressway-E for .*@cisco.com.
C. An HTTP allow list entry must be made on the Expressway-C for phonebook cisco.com.
D. A SIP allow list entry must be made on the Expressway-C for .*@cisco.com.
An administrator needs to configure a Cisco ESA to block specific domains based on their reputation. Which service within the Cisco ESA should be utilized to accomplish this task?
A. Receiving SMTP Policy
B. Data Loss Prevention
C. Anti-Virus
D. Sender Group
What is the purpose of Cisco Email Encryption on Cisco ESA?
A. to ensure anonymity between a recipient and MTA
B. to ensure integrity between a sender and MTA
C. to authenticate direct communication between a sender and Cisco ESA
D. to ensure privacy between Cisco ESA and MTA
An email containing a URL passes through the Cisco ESA that has content filtering disabled for all mail policies. The sender is sampleuser@test1.com , the recipients are testuser1@test2.com , testuser2@test2.com , testuser3@test2.com , and mailer1@test2.com . The subject of the email is Test Document395898847. An administrator wants to add a policy to ensure that the Cisco ESA evaluates the web reputation score before permitting this email. Which two criteria must be used by the administrator to achieve this? (Choose two.)
A. Subject contains “TestDocument”
B. Sender matches test1.com
C. Email body contains a URL
D. Date and time of email
E. Email does not match mailer1@test2.com
How is the communication routed in a Hybrid deployment so that people on Cisco Cloud-Based IM are able to communicate with Cisco Jabber users in the on-premises environment?
A. The Expressway-C enables a connection directly with the Cisco Webex Cloud to enable the hybrid service and allow the two services to communicate.
B. The Expressway-E located in the DMZ establishes a connection with the Cisco Webex Cloud to enable the hybrid service and allow the two services to communicate.
C. The Cisco Unified IM and Presence server establishes a connection using the outgoing path through the Cisco Expressways that terminates in the Cisco Webex Cloud to create the hybrid environment that links the two services together.
D. The Cisco UC server establishes a connection using the outgoing path through the Cisco Expressways that terminates in the Cisco Webex Cloud to create the hybrid environment that links the two services together.
An Expressway-E is configured using a single NIC with NAT. How must the Expressway-C traversal client zone be configured to connect to the Expressway-E?
A. TLS verify must be enabled.
B. The zone profile must be set to default.
C. The peer address must be the Expressway-E NAT address.
D. The peer address must be the Expressway-E LAN 1 IP address.
An engineer must configure the zone to connect to an Expressway-E using Single NIC with NAT. The internal IP address is 192.168.10.63, and the NAT address is 203.0.113.5. What must the engineer configure on the Expressway-C to meet this requirement?
A. traversal zone with the peer address 192.168.10.63
B. neighbor zone with the peer address 192.168.10.63
C. traversal zone with the peer address of 203.0.113.5
D. neighbor zone with the peer address of 203.0.113.5
Which feature must be activated on a Cisco ESA to combat backscatter?
A. Graymail Detection
B. Bounce Profile
C. Forged Email Detection
D. Bounce Verification
Which setting affects the aggressiveness of spam detection?
A. protection level
B. spam threshold
C. spam timeout
D. maximum depth of recursion scan
A Cisco ESA is configured such that emails with a reputation score above -6 are logged and those with a score below -6 are logged, encrypted, and then delivered. An email body contains a shortened URL that exceeds the nested shortened URLs limit. Which action is taken against the email?
A. It is encrypted but not logged.
B. It is logged but not encrypted.
C. It is logged and dropped.
D. It is logged and encrypted.
A list of company executives is routinely being spoofed, which puts the company at risk of malicious email attacks. An administrator must ensure that executive messages are originating from legitimate sending addresses. Which two steps must be taken to accomplish this task? (Choose two.)
A. Create an incoming content filter with SPF detection.
B. Create a content dictionary including a list of the names that are being spoofed.
C. Enable the Forged Email Detection feature under Security Settings.
D. Enable DMARC feature under Mail Policies.
E. Create an incoming content filter with the Forged Email Detection condition.
Which two factors must be considered when message filter processing is configured? (Choose two.)
A. message-filter order
B. lateral processing
C. structure of the combined packet
D. mail policies
E. MIME structure of the message
An engineer is testing mail flow on a new Cisco ESA and notices that messages for domain abc.com are stuck in the delivery queue. Upon further investigation, the engineer notices that the messages pending delivery are destined for 192.168.1.11, when they should instead be routed to 192.168.1.10. What configuration change needed to address this issue?
A. Add an address list for domain abc.com.
B. Modify Destination Controls entry for the domain abc.com.
C. Modify the SMTP route for the domain and change the IP address to 192.168.1.10.
D. Modify the Routing Tables and add a route for IP address to 192.168.1.10.
DRAG DROP - An administrator must ensure that emails sent from cisco_123@externally.com are routed through an alternate virtual gateway. Drag and drop the snippet from the bottom onto the blank in the graphic to finish the message filter syntax. Not all snippets are used.
During the deployment of a Cisco Webex Video Mesh, where do on-premises SIP endpoints send signaling?
A. On-premises endpoints cannot participate in Cisco Webex Video Mesh
B. to the cloud
C. to the switching services
D. to the call control environment (Unified CM or Expressway)
Which antispam feature is utilized to give end users control to allow emails that are spam to be delivered to their inbox, overriding any spam verdict and action on the Cisco ESA?
A. end user allow list
B. end user spam quarantine access
C. end user passthrough list
D. end user safelist
With QoS enabled, which two statements about the Cisco Webex Video Mesh Node signaling and media traffic are true? (Choose two.)
A. From VMN to CUCM SIP endpoints, the source UDP ports from 52500 to 62999 is used for audio traffic.
B. From VMN to Webex Teams clients, the source UDP port 5004 is used for video traffic.
C. From Webex cloud to VMN, the source UDP port 9000 is used for audio traffic.
D. From VMN to video endpoints, the destination UDP port 5004 is used for audio traffic.
E. From VMN to Webex cloud, the destination UDP port 9000 is used for video traffic.
What is a requirement when configuring the Cisco Webex Hybrid Message account for accessing the API of the Cisco UCM IM and Presence Service?
A. Add a new end-user with the ג€Standard AXL API Accessג€ role
B. Use an application user with only the ג€Standard CTI Allow Control of All Devicesג€ role
C. Use an application user not the main administrator account with the ג€Standard AXL API Accessג€ role
D. Use the main administrator account if it includes the ג€Standard AXL API Accessג€ role
Free Access Full 300-820 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 300-820 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 300-820 certification journey!