300-715 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 300-715 certification exam? Kickstart your success with our 300-715 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 300-715 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 300-715 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
While configuring Cisco TrustSec on Cisco IOS devices, the engineer must set the CTS device ID and password in order for the devices to authenticate with each other. However, after this is complete, the devices are not able to properly authenticate. What issue would cause this to happen even if the device ID and passwords are correct?
A. EAP-FAST is not enabled.
B. The SGT mappings have not been defined.
C. The device aliases are not matching.
D. The devices are missing the configuration cts credentials trustsec verify 1.
A network engineer responsible for the switching environment must provision a new switch to properly propagate security group tags within the TrustSec inline method. Which CLI command must the network engineer enter on the switch to globally enable the tagging of SGTs?
A. cts sxp enable
B. cts manual
C. cts role-based sgt-map
D. cts role-based enforcement
What allows an endpoint to obtain a digital certificate from Cisco ISE during a BYOD flow?
A. Application Visibility and Control
B. Supplicant Provisioning Wizard
C. My Devices Portal
D. Network Access Control
An organization is using Cisco ISE to provide AAA services to non-Cisco switches with IP phones connected. An engineer needs to use Profiling Services to authorize network access for IP phones that do not support 802.1X. What must be configured to accomplish this goal?
A. DHCP
B. SNMPTRAP
C. SNMPQUERY
D. RADIUS
What are two benefits of TACACS+ versus RADIUS for device administration? (Choose two.)
A. TACACS+ has command authorization, and RADIUS does not.
B. TACACS+ uses UDP, and RADIUS uses TCP.
C. TACACS+ supports 802.1X, and RADIUS supports MAB.
D. TACACS+ provides the service type, and RADIUS does not.
E. TACACS+ encrypts the whole payload, and RADIUS encrypts only the password.
A user recently had their laptop stolen. IT has ordered a replacement device for the user and was able to obtain the MAC address of the device 04.57:47:34 35 0A from the vendor before it shipped. Which statement regarding adding MAC addresses to Cisco ISE is correct?
A. MAC addresses can only be manually imported using a .csv file and the import option.
B. MAC addresses can only be manually imported using the REST API.
C. MAC addresses can only be allowed after the device has connected to the network.
D. MAC addresses can be manually added using the + sign under Context Visibility > Endpoints.
An engineer is configuring 802.1X and is testing out their policy sets. After authentication, some endpoints are given an access-reject message but are still allowed onto the network. What is causing this issue to occur?
A. The authorization results for the endpoints include the Trusted security group tag.
B. The authorization results for the endpoints include a dACL allowing access.
C. The switch port is configured with authentication event server dead action authorize vlan.
D. The switch port is configured with authentication open.
Which Cisco ISE deployment model provides redundancy by having every node in the deployment configured with the Administration, Policy Service, and Monitoring personas to protect from a complete node failure?
A. dispersed
B. distributed
C. two-node
D. hybrid
What are two differences between the RADIUS and TACACS+ protocols? (Choose two.)
A. RADIUS offers multiprotocol support, whereas TACACS+ does not.
B. RADIUS is a Cisco proprietary protocol, whereas TACACS+ is an open standard protocol.
C. RADIUS enables encryption of all the packets, whereas with TACACS+, only the password is encrypted.
D. RADIUS combines authentication and authorization, whereas TACACS+ does not.
E. TACACS+ uses TCP port 49, whereas RADIUS uses UDP ports 1812 and 1813.
What should be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A. continue
B. pass
C. drop
D. reject
Which CLI command must be configured on the switchport to immediately run the MAB process if a non-802 1X capable endpoint connects to the port?
A. authentication order mab dot1x
B. dot1x pae authenticator
C. authentication fallback
D. access-session port-control auto
What is the purpose of the ip http server command on a switch?
A. It enables the https server for users for web authentication.
B. It enables dot1x authentication on the switch.
C. It enables MAB authentication on the switch.
D. It enables the switch to redirect users for web authentication.
A client connects to a network and the authenticator device learns the MAC address 04:49:23:86:34:AB of this client. After the MAC address is learned, the 802.1 x authentication process begins on this port. Which ISE deployment mode restricts all traffic initially, applies a rule for access control if 802.1x authentication is successful, and can be configured to grant only limited access if 802.1 x authentication is unsuccessful?
A. open mode
B. monitor mode
C. closed mode
D. low-impact mode
Which two task types are included in the Cisco ISE common tasks support for TACACS+ profiles? (Choose two.)
A. ASA
B. Firepower
C. Shell
D. WLC
E. IOS
An administrator has added a new Cisco ISE PSN to their distributed deployment. Which two features must the administrator enable to accept authentication requests and profile the endpoints correctly, and add them to their respective endpoint identity groups? (Choose two.)
A. Session Services
B. Profiling Services
C. Radius Service
D. Posture Services
E. Endpoint Attribute Filter
A Cisco ISE engineer is creating certificate authentication profile to be used with machine authentication for the network. The engineer wants to be able to compare the user-presented certificate with a certificate stored in Active Directory. What must be done to accomplish this?
A. Add the subject alternative name and the common name to the CAP
B. Use MS-CHAPv2 since it provides machine credentials and matches them to credentials stored in Active Directory.
C. Configure the user-presented password hash and a hash stored in Active Directory for comparison.
D. Enable the option for performing binary comparison.
An administrator enables the profiling service for Cisco ISE to use for authorization policies while in closed mode. When the endpoints connect, they receive limited access so that the profiling probes can gather information and Cisco ISE can assign the correct profiles. They are using the default values within Cisco ISE, but the devices do not change their access due to the new profile. What is the problem?
A. The default profiler configuration is set to No CoA for the reauthentication setting.
B. In closed mode, profiling does not work unless CDP is enabled.
C. The profiler feed is not downloading new information, so the profiler is inactive.
D. The profiling probes are not able to collect enough information to change the device profile.
An enterprise uses a separate PSN for each of its four remote sites. Recently, a user reported receiving an "EAP-TLS authentication failed" message when moving between remote sites. Which configuration must be applied on Cisco ISE?
A. Use a third-party certificate on the network device.
B. Add the device to all PSN nodes in the deployment.
C. Configure an authorization profile for the end users.
D. Renew the expired certificate on one of the PSN.
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
A. Network Access NetworkDeviceName CONTAINS
B. DEVICE Device Type CONTAINS
C. Airespace Airespace-Wlan-Id CONTAINS
D. Radius Called-Station-ID CONTAINS
A network administrator notices that after a company-wide shut down, many users cannot connect their laptops to the corporate SSID. What must be done to permit access in a timely manner?
A. Connect this system as a guest user and then redirect the web auth protocol to log in to the network.
B. Allow authentication for expired certificates within the EAP-TLS section under the allowed protocols.
C. Add a certificate issue from the CA server, revoke the expired certificate, and add the new certificate in system.
D. Authenticate the user’s system to the secondary Cisco ISE node and move this user to the primary with the renewed certificate.
An engineer deploys Cisco ISE and must configure Active Directory to then use information from Active Directory in an authorization policy. Which two components must be configured, in addition to Active Directory groups, to achieve this goal? (Choose two.)
A. Identity Source Sequences
B. LDAP External Identity Sources
C. Active Directory External Identity Sources
D. Library Condition for Identity Group: User Identity Group
E. Library Condition for External Identity: External Groups
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
A. closed
B. restricted
C. monitor
D. low-impact
What is a valid status of an endpoint attribute during the device registration process?
A. block listed
B. pending
C. unknown
D. DenyAccess
An organization is hosting a conference and must make guest accounts for several of the speakers attending. The conference ended two days early but the guest accounts are still being used to access the network. What must be configured to correct this?
A. Create an authorization rule denying sponsored guest access.
B. Create an authorization rule denying guest access.
C. Navigate to the Guest Portal and delete the guest accounts.
D. Navigate to the Sponsor Portal and suspend the guest accounts.
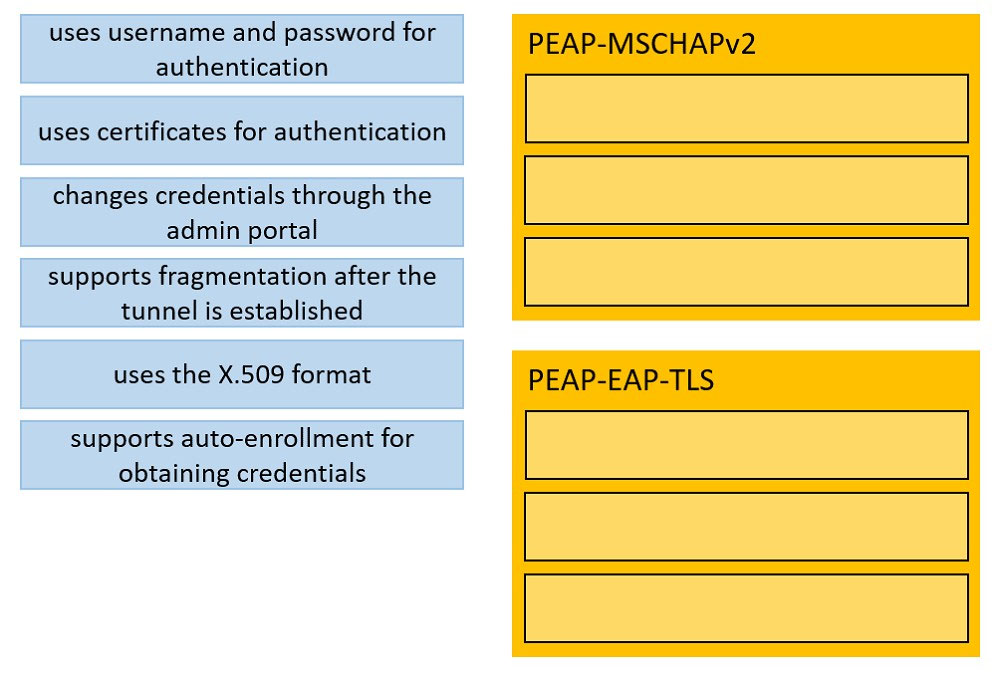
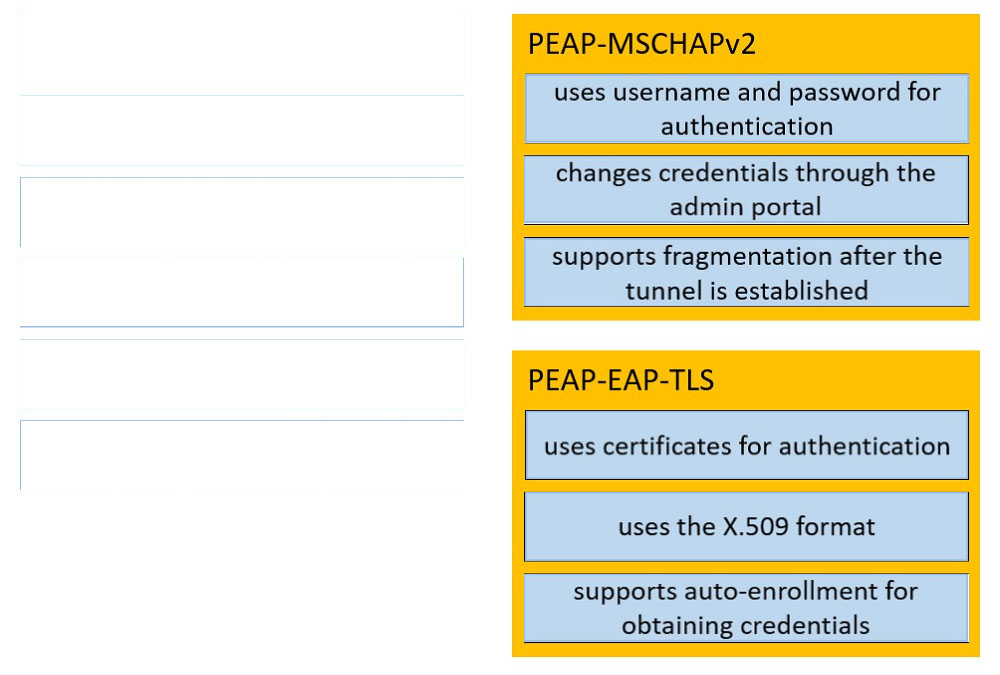
DRAG DROP - An organization wants to implement 802.1X and is debating whether to use PEAP-MSCHAPv2 or PEAP-EAP-TLS for authentication. Drag the characteristics on the left to the corresponding protocol on the right. Select and Place:
Which are two characteristics of TACACS+? (Choose two.)
A. It separates authorization and authentication functions.
B. It combines authorization and authentication functions.
C. It uses UDP port 49.
D. It encrypts the password only.
E. It uses TCP port 49.
Which Cisco ISE solution ensures endpoints have the latest version of antivirus updates installed before being allowed access to the corporate network?
A. Threat Services
B. Profiling Services
C. Provisioning Services
D. Posture Services
An engineer needs to configure a Cisco ISE server to issue a CoA for endpoints already authenticated to access the network. The CoA option must be enforced on a session, even if there are multiple active sessions on a port. What must be configured to accomplish this task?
A. the Reauth CoA option in the Cisco ISE system profiling settings enabled
B. an endpoint profiling policy with the No CoA option enabled
C. an endpoint profiling policy with the Port Bounce CoA option enabled
D. the Port Bounce CoA option in the Cisco ISE system profiling settings enabled
An engineer is configuring Cisco ISE for network device administration and has devices that support both protocols. What are two benefits of choosing TACACS+ over RADIUS for these devices? (Choose two.)
A. TACACS+ uses secure EAP-TLS while RADIUS does not.
B. TACACS+ is FIPS compliant while RADIUS is not.
C. TACACS+ encrypts the entire payload being sent while RADIUS only encrypts the password.
D. TACACS+ is designed for network access control while RADIUS is designed for role-based access.
E. TACACS+ provides the ability to authorize specific commands while RADIUS does not.
A security administrator is using Cisco ISE to create a BYOD onboarding solution for all employees who use personal devices on the corporate network. The administrator generates a Certificate Signing Request and signs the request using an external Certificate Authority server. Which certificate usage option must be selected when importing the certificate into ISE?
A. RADIUS
B. DLTS
C. Portal
D. Admin
An organization is adding nodes to their Cisco ISE deployment and has two nodes designated as primary and secondary PAN and MnT nodes. The organization also has four PSNs. An administrator is adding two more PSNs to this deployment but is having problems adding one of them. What is the problem?
A. Only five PSNs are allowed to be in the Cisco ISE cube if configured this way.
B. One of the new nodes must be designated as a pxGrid node.
C. The new nodes must be set to primary prior to being added to the deployment.
D. The current PAN is only able to track a max of four nodes.
When configuring an authorization policy, an administrator cannot see specific Active Directory groups present in their domain to be used as a policy condition. However, other groups that are in the same domain are seen. What is causing this issue?
A. Cisco ISE’s connection to the AD join point is failing.
B. Cisco ISE only sees the built-in groups, not user created ones.
C. The groups are not added to Cisco ISE under the AD join point.
D. The groups are present but need to be manually typed as conditions.
An administrator connects an HP printer to a dot1x enable port, but the printer is nor accessible. Which feature must the administrator enable to access the printer?
A. change of authorization
B. MAC authentication bypass
C. TACACS authentication
D. RADIUS authentication
A network administrator changed a Cisco ISE deployment from pilot to production and noticed that the JVM memory utilization increased significantly. The administrator suspects this is due to replication between the nodes. What must be configured to minimize performance degradation?
A. Enable the endpoint attribute filter.
B. Review the profiling policies for any misconfiguration.
C. Ensure that Cisco ISE is updated with the latest profiler feed update.
D. Change the reauthentication interval.
An engineer needs to configure a new certificate template in the Cisco ISE Internal Certificate Authority to prevent BYOD devices from needing to re-enroll when their MAC address changes. Which option must be selected in the Subject Alternative Name field?
A. Common Name and GUID
B. MAC Address and GUID
C. Distinguished Name
D. Common Name
A new employee just connected their workstation to a Cisco IP phone. The network administrator wants to ensure that the Cisco IP phone remains online when the user disconnects their workstation from the corporate network. Which CoA configuration meets this requirement?
A. Reauth
B. Disconnect
C. No CoA
D. Port Bounce
A network administrator must configure endpoints using an 802.1X authentication method with EAP identity certificates that are provided by the Cisco ISE. When the endpoint presents the identity certificate to Cisco ISE to validate the certificate, endpoints must be authorized to connect to the network. Which EAP type must be configured by the network administrator to complete this task?
A. EAP-TTLS
B. EAP-TLS
C. EAP-FAST
D. EAP-PEAP-MSCHAPv2
Which two methods should a sponsor select to create bulk guest accounts from the sponsor portal? (Choose two.)
A. Known
B. Monthly
C. Daily
D. Imported
E. Random
Which controller option allows a user to switch from the provisioning SSID to the employee SSID after registration?
A. User Idle Timeout
B. AAA Override
C. Fast SSID Change
D. AP SSID Fallback
An organization has a fully distributed Cisco ISE deployment. When implementing probes, an administrator must scan for unknown endpoints to learn the IP-to- MAC address bindings. The scan is complete on one PSN, but the information is not available on the others. What must be done to make the information available?
A. Cisco ISE must be configured to learn the IP-MAC binding of unknown endpoints via RADIUS authentication, not via scanning.
B. Cisco ISE must learn the IP-MAC binding of unknown endpoints via DHCP profiling, not via scanning.
C. Scanning must be initiated from the MnT node to centrally gather the information.
D. Scanning must be initiated from the PSN that last authenticated the endpoint.
What are the minimum requirements for deploying the Automatic Failover feature on Administration nodes in a distributed Cisco ISE deployment?
A. a primary and secondary PAN and a health check node for the Secondary PAN
B. a primary and secondary PAN and no health check nodes
C. a primary and secondary PAN and a pair of health check nodes
D. a primary and secondary PAN and a health check node for the Primary PAN
When configuring Active Directory groups, an administrator is attempting to retrieve a group that has a name that is ambiguous with another group. What must be done so that the correct group is returned?
A. Use the SID as the identifier for the group.
B. Configure MAB to utilize one group, and 802 1xto utilize the conflicting group.
C. Select both groups, and use a TCT pointer to identity the appropriate one.
D. Utilize MIB entries to identify the desired group.
An administrator is adding network devices for a new medical building into Cisco ISE. These devices must be in a network device group that is identifying them as `Medical Switch` so that the policies can be made separately for the endpoints connecting through them. Which configuration item must be changed in the network device within Cisco ISE to accomplish this goal?
A. Change the device profile to Medical Switch.
B. Change the device type to Medical Switch.
C. Change the device location to Medical Switch.
D. Change the model name to Medical Switch.
Refer to the exhibit. Which two configurations are needed on a catalyst switch to add it as a network access device in a Cisco ISE that is being used for 802.1X authentications? (Choose two.)
A. radius server ISE1address ipv4 192.168.255.17 auth-port 1645 acct-port 1646key 7 0607542D5F4A0213034C1E0A1F0F2E2122733F3429000D12055A5A52
B. tacacs server ISE1address ipv4 192.168.255.15 auth-port 1645 acct-port 1646key 7 0607542D5F4A0213034C1E0A1F0F2E2122733F3429000D12055A5A52
C. radius server ISE1address ipv4 192.168.255.19 auth-port 1645 acct-port 1646key 7 0607542D5F4A0213034C1E0A1F0F2E2122733F3429000D12055A5A52
D. tacacs server ISE1address ipv4 192.168.255.18 auth-port 1645 acct-port 1646key 7 0607542D5F4A0213034C1E0A1F0F2E2122733F3429000D12055A5A52
E. radius server ISE1address ipv4 192.168.255.16 auth-port 1645 acct-port 1646key 7 0607542D5F4A0213034C1E0A1F0F2E2122733F3429000D12055A5A52
An engineer is implementing Cisco ISE and needs to configure 802.1X. The port settings are configured for port-based authentication. Which command should be used to complete this configuration?
A. aaa authentication dot1x default group radius
B. dot1x system-auth-control
C. authentication port-control auto
D. dot1x pae authenticator
A company manager is hosting a conference. Conference participants must connect to an open guest SSID and only use a preassigned code that they enter into the guest portal prior to gaining access to the network. How should the manager configure Cisco ISE to accomplish this goal?
A. Create logins for each participant to give them sponsored access.
B. Create entries in the guest identity group for all participants.
C. Create an access code to be entered in the AUP mode.
D. Create a registration code to be entered on the portal splash page.
An administrator replaced a PSN in the distributed Cisco ISE environment. When endpoints authenticate to it, the devices are not getting the right profiles or attributes and as a result, are not hitting the correct policies. This was working correctly on the previous PSN. Which action must be taken to ensure the endpoints get identified?
A. Verify that the MnT node is tracking the session.
B. Verify the shared secret used between the switch and the PSN.
C. Verify that the profiling service is running on the new PSN.
D. Verify that the authentication request the PSN is receiving is not malformed.
Which RADIUS attribute is used to dynamically assign the Inactivity active timer for MAB users from the Cisco ISE node?
A. session-timeout
B. termination-action
C. radius-server timeout
D. idle-timeout
Which Cisco ISE deployment model is recommended for an enterprise that has over 50,000 concurrent active endpoints?
A. large deployment with fully distributed nodes running all personas
B. medium deployment with primary and secondary PAN/MnT/pxGrid nodes with shared PSNs
C. medium deployment with primary and secondary PAN/MnT/pxGrid nodes with dedicated PSNs
D. small deployment with one primary and one secondary node running all personas
Refer to the exhibit. Which switch configuration change will allow only one voice and one data endpoint on each port?
A. auto to manual
B. mab to dot1x
C. multi-auth to multi-domain
D. multi-auth to single-auth
Free Access Full 300-715 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 300-715 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 300-715 certification journey!