300-415 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 300-415 certification exam? Kickstart your success with our 300-415 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 300-415 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 300-415 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Which two products are used to deploy Cisco WAN Edge Router virtual platforms? (Choose two.)
A. Sun Enterprise M4000 Server running Sun Solaris
B. Sun SPARC Node running AIX
C. Cisco UCS
D. HP ProLiant DL380 Generation 10 running HP-UX
E. Cisco ENCS 5000 Series
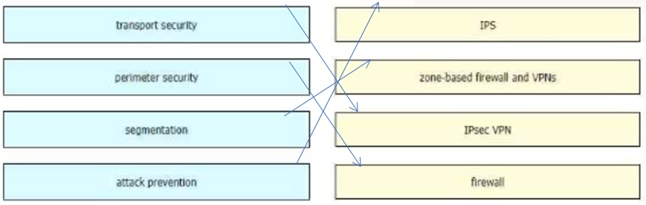
Drag and drop the security terminologies from the left onto the PCI-compliant network features and devices on the right.
Select and Place:

Which capability does Cisco SD-WAN Multi-Region Fabric provide?
A. end-to-end SLA-aware routing
B. overlay support for IP multicast
C. assignment of a single vSmart controller to handle region 0 and noncore regions
D. end-to-end encryption for inter-region traffic
An engineer is applying QoS policy for the transport-side tunnel interfaces to enable scheduling and shaping for a WAN Edge cloud router. Which command accomplishes the task?
A. cloud-qos-service-side
B. qos-scheduler QOS_0
C. rewrite-rule QOS-REQWRITE
D. qos-map QOS
An organization requires the use of integrated preventative engines, exploit protection, and the most updated and advanced signature-based antivirus with sandboxing and threat intelligence to stop malicious attachments before they reach users and get executed. Which Cisco SD-WAN solution meets the requirements?
A. Cisco Trust Anchor module
B. Cisco AMP and Threat Grid
C. URL filtering and Umbrella DNS security
D. Snort IPS
Which REST API call checks the status of an action that is performed on a device?
A. admin status
B. troubleshoot status
C. configuration status
D. monitor status
A network administrator is configuring VRRP to avoid a traffic black hole when the transport side of the network is down on the primary device. What must be configured to get the fastest failover to standby?
A. OMP tracking
B. higher group ID number
C. prefix-list tracking
D. lower timer interval
WAN_Release_17.1/02System_and_Interfaces/06configuring_Network_Interfaces/configuring_VRRP Community vote distribution
A network administrator is tasked to make sure that an OMP peer session is closed after missing three consecutive keepalive messages in 3 minutes. Additionally, route updates must be sent every minute. If a WAN Edge router becomes unavailable, the peer must use last known information to forward packets for 12 hours. Which set of configuration commands accomplishes this task?


Which device should be configured with the service chain IP address to route intersite traffic through a firewall?
A. vSmart
B. spoke WAN Edge
C. hub WAN Edge
D. firewall
For data plane resiliency, what does the Cisco SD-WAN software implement?
A. multiple vBond orchestrators
B. establishing a nity between vSmart controllers and WAN Edge routers
C. OMP
D. BFD
Which protocol is used to measure loss, latency, jitter, and liveliness of the tunnel between WAN Edge router peers?
A. OMP
B. NetFlow
C. BFD
D. IP SLA
How many network interface cards are needed to add in virtual machine settings when installing vSmart controller on VMware vSphere ESXi Hypervisor software?
A. 1
B. 2
C. 3
D. 4
If Smart Account Sync is not used, which Cisco SD-WAN component is used to upload an authorized serial number file?
A. WAN Edge
B. vSmart
C. vBond
D. vManage
Refer to the exhibit. An organization is testing a Cisco SD-WAN solution and decided to have the control plane established first and not the data plane at the time of migration. Which configuration achieves this goal?

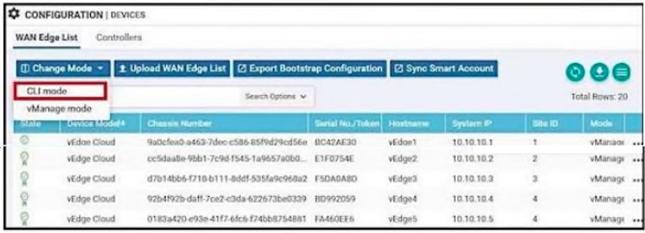
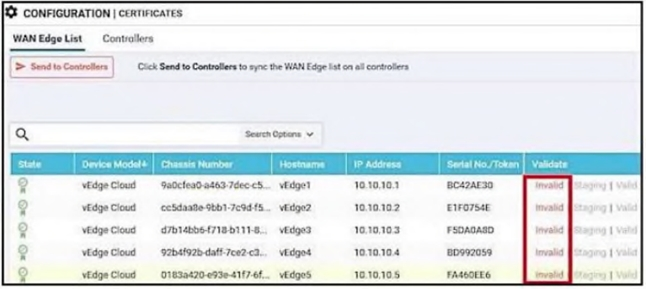
A.
Drag and drop the functions from the left onto the correct templates on the right.
Select and Place:

Which two algorithms authenticate a user when configuring SNMPv3 monitoring on a WAN Edge router? (Choose two.)
A. AES-256
B. MD5
C. SHA-2
D. AES-128
E. SHA-1
Which two services are critical for zero touch provisioning on-boarding? (Choose two.)
A. EMAIL
B. SNMP
C. AAA
D. DHCP
E. DNS
Which policy blocks TLOCs from remotes and allows TLOCs from the data center to form hub-and-spoke peering?
A. centralized data policy
B. localized control policy
C. centralized control policy
D. localized data policy
Which component of the Cisco SD-WAN control plane architecture facilitates the storage of certificates and configurations for network components?
A. vSmart
B. WAN Edge
C. vManage
D. vBond
Which protocol does vManage use to provision the WAN Edge device during the onboarding process?
A. RESTCONF
B. NETCONF
C. EPP
D. HTTPS
Which OMP route is selected if it was learned from the same Cisco SD-WAN device at location S4406T9E02F15?
A. route with the lower origin metric
B. route with the higher OMP route preference value
C. route with the higher router ID
D. route with the lower administrative distance
What are three types of data that JSON uses when Cisco APIC REST API uses JavaScript?
A. GET, PUT, and DELETE
B. SCALAR, OBJECT, and ARRAY
C. GET, PUT, and POST
D. SCALAR, POST, and OBJECT
How many vBond controllers must be installed when vManager is installed in a multitenancy environment for four tenants?
A. One vBond controller is shared between the tenants.
B. Multitenancy deployment requires three vBand controllers.
C. Each tenant requires two vBond controllers for redundancy.
D. Each tenant requires a dedicated vBond controller.
What are two components of vSmart? (Choose two.)
A. key reflection
B. policy engine
C. NAT traversal
D. device template creation
E. monitoring
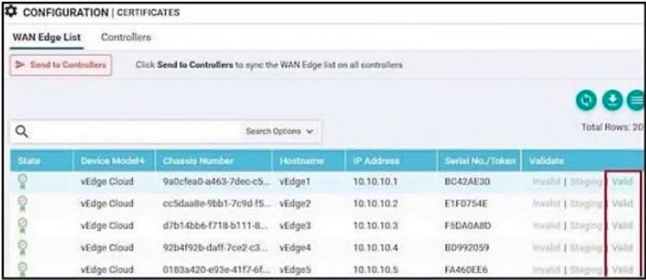
Which configuration step is taken on vManage after WAN Edge list is uploaded to support the on-boarding process before the device comes online?
A. Verify the device certificate
B. Enable the ZTP process
C. Set the device as valid
D. Send the list to controllers
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.)
A. CSR 1000v
B. ISR 4431
C. vEdge 100c
D. vEdge 2000
E. vEdge Cloud
When a WAN Edge device joins the Cisco SD-WAN overlay, which Cisco SD-WAN component orchestrates the connection between the WAN Edge device and a vSmart controller?
A. vManage
B. vBond
C. OMP
D. APIC-EM
How is vBond reachability resolved by vManage?
A. IPsec
B. DNS
C. BGP
D. OMP
An engineer builds a three-node vManage cluster and then realizes that multiple nodes are unnecessary for the size of the company. How should the engineer revert the setup to a single vManage?
A. Use the cluster conversion utility to convert to standalone vManage.
B. Restore vManage from the backup VM snapshot.
C. Leave the cluster as is and point to one vManage.
D. Remove two nodes from the three-node vManage cluster.
What is the procedure to upgrade all Cisco SD-WAN devices to a recent version?
A. The upgrade is performed for a group of WAN Edge devices first to ensure data-plane availability when other controllers are being updated.
B. Upgrade and reboot are performed first on vManage, then on vBond, then on vSmart, and nally on the Cisco WAN Edge devices.
C. The upgrade is performed first on vManage, then on WAN Edge devices, then on vBond, and nally on vSmart. The reboot must start from WAN Edge devices.
D. Upgrade and reboot are performed first on vBond, then on vSmart, and nally on the Cisco WAN Edge devices.
What are the two reasons a customer chooses to use IPsec tunnels over GRE? (Choose two.)
A. IPsec failure detection is faster.
B. Generally, they provide a higher bandwidth for tunnel connection.
C. CFlowd is required.
D. A WAN Edge router is behind NAT.
E. IPsec is more secure.
An engineer is configuring a list that matches all IP prefixes with lengths from /1 to /16 in a centralized control policy. Which list accomplishes this task?
A. 0.0.0.0/0 file 16
B. 0.0.0.0/1 file 16
C. 0.0.0.0/0 ge 1
D. 0.0.0.0/16 ge 1
Which process is continued by Cisco SD-WAN when packet duplication is enabled?
A. Additional headers are added to outgoing packets to perform custom routing policies.
B. Dynamic traffic is compressed and signaled before it is forwarded though the WAN.
C. Copies of packets are sent over multiple WAN circuits to overcome packet loss.
D. Application traffic is analyzed to find patterns and enable custom detection rules.
An engineer must automate certificate signing through Cisco. Which vManage configuration achieves this task?
A. vpn 0 allow-service dns allow-service sshd allow-service netconf
B. vpn 512 dns 208.67.222.222 primary allow-service dns allow-service sshd allow-service netconf
C. vpn 0 dns 208.67.222.222 primary allow-service dns allow-service sshd allow-service netconf
D. vpn 512 allow-service dns allow-service sshd allow-service netconf
Refer to the exhibit. An engineer is troubleshooting a control connection issue. What does `connect` mean in this show control connections output?
A. Control connection is down
B. Control connection is up
C. Control connection attempt is in progress
D. Control connection is connected
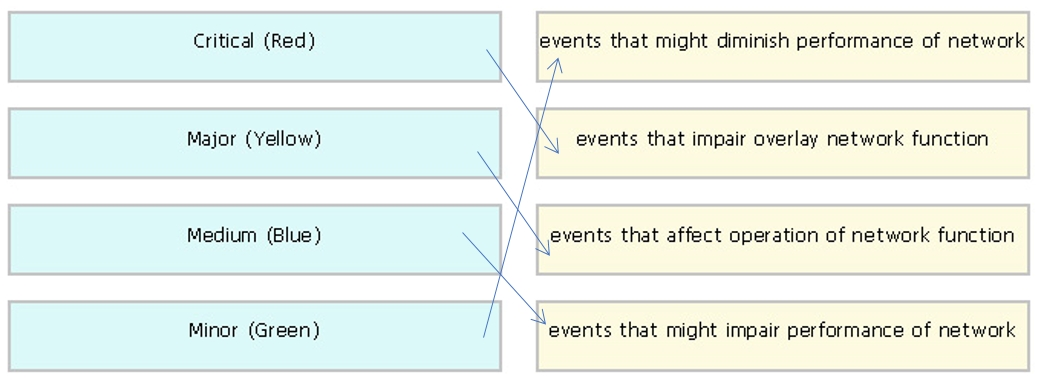
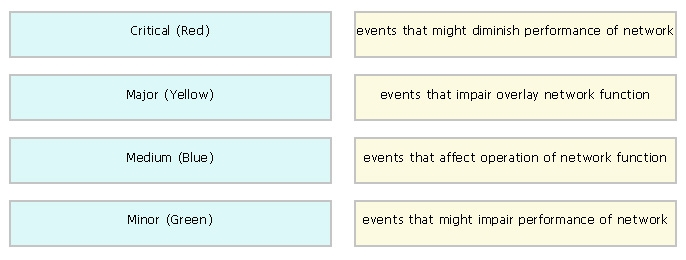
Drag and drop the alarm states from the left onto the corresponding alarm descriptions on the right.
Select and Place:
What is the size of SGT data in the metadata header?
A. 8 bits
B. 16 bits
C. 24 bits
D. 32 bits
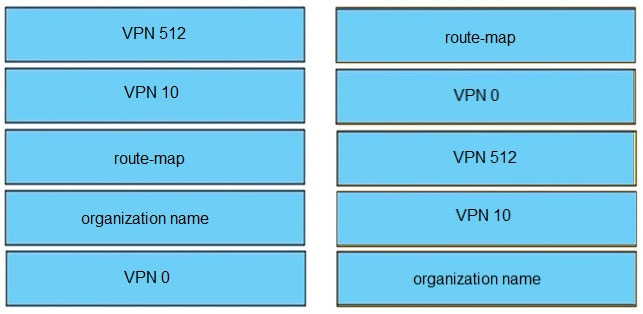
Refer to the exhibit. The engineering must assign community tags to 3 of its 74 critical server networks as soon as they are advertised to BGP peers. These server networks must not be advertised outside AS. Which configuration fulfills this requirement?
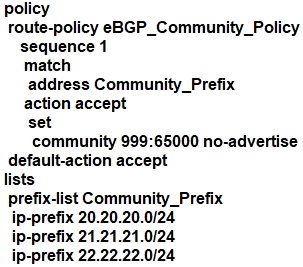
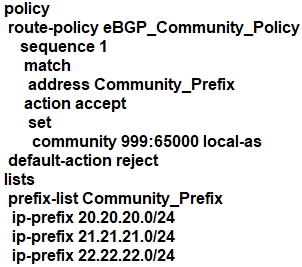
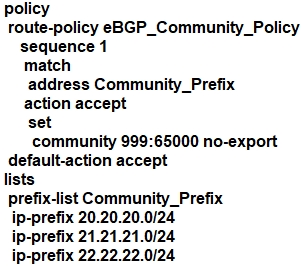
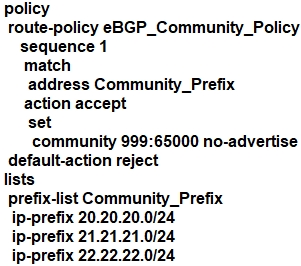
Which configuration component is used in a firewall security policy?
A. intrusion prevention policy
B. numbered sequences of match-action pairs
C. application match parameters
D. URL filtering policy
What prohibits deleting a VNF image from the software repository?
A. if the image is stored by vManage
B. if the image is referenced by a service chain
C. if the image is included in a configured policy
D. if the image is uploaded by a WAN Edge device
How is TLOC defined?
A. It is represented by a unique identifier to specify a site in a SD-WAN architecture.
B. It speci es a Cisco SD-WAN overlay in a multitenant vSMART deployment.
C. It is represented by a group of QoS policies applied to a WAN Edge router.
D. It is a unique collection of GRE or IPsec encapsulations, link color, and system IP address.
What is the minimum Red Hat Enterprise Linux operating system requirement for a Cisco SD-WAN controller deployment via KVM?
A. RHEL 7.5
B. RHEL 4.4
C. RHEL 6.7
D. RHEL 6.5
Refer to the exhibit. A network administrator is configuring OMP in vManage to advertise all the paths for the same prefix from a site that has two WAN Edge devices. Each WAN Edge device is connected to three ISPs and two private MPLS transports. What is the minimum value for `Number of Paths advertised per prefix` that should be configured?
A. 2
B. 3
C. 5
D. 10
Which component is responsible for creating and maintaining the secure DTLS/TLS connection on the vSmart controller?
A. vdaemon
B. OMP
C. SNMP
D. NETCONF
What are the two advantages of deploying cloud-based Cisco SD-WAN controllers? (Choose two.)
A. centralized control and data plane
B. infrastructure as a service
C. management of SLA
D. centralized raid storage of data
E. distributed authentication policies
How is an event monitored and reported for an individual device in the overlay network at site ID:S4300T6E43F36?
A. The device sends event notifications to vManage.
B. The device sends notifications to vSmart that sends them to vManage.
C. The device sends a critical alarm of events to vManage.
D. The device sends a critical alarm to vSmart that sends it to vManage.
Which attribute is used to tie all the controllers together by vManage?
A. vManage system-ip
B. region ID
C. organization name
D. secure device ID
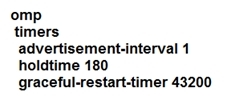
Which timer speci es how long the router keeps routing information in the cache after all OMP sessions are lost at location S4317T8E35F76?
A. graceful restart timer
B. advertisement interval
C. EOR timer
D. hold time
Which plane assists in the automatic onboarding of the SD-WAN routers into the SD-WAN overlay?
A. data
B. orchestration
C. management
D. control
Refer to the exhibit. An enterprise decides to use the Cisco SD-WAN Cloud onRamp for SaaS feature and utilize
A. Q site Biz iNET to reach SaaS Cloud for branch C, currently reaching SaaS Cloud directly. Which role must be assigned to devices at both sites in vManage Cloud Express for this solution to work?
B. Branch to be added as Client Sites and
C. Q as DI
D. Q to be added as Gateway and Branch as DI
E. Branch to be added as DIA and
F. Q as Client Site.
G. Q to be added as Gateway and Branch as Client Site.
Free Access Full 300-415 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 300-415 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 300-415 certification journey!