300-320 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 300-320 certification exam? Kickstart your success with our 300-320 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 300-320 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 300-320 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
You are designing a scalable cluster that contains a combination of Cisco APIC-M and APIC-L controllers. Which controller provides the scalability used in the cluster?
A. APIC-M
B. APIC-EM
C. combination of APIC-M and APIC -I
D. APIC-L
Which security function is inherent in an Application Centric Infrastructure network?
A. Default Inter-EPG connectivity
B. Intrusion Detection
C. Default Denial Network
D. Intrusion Prevention
A company requires a simple network access control solution that allows for software defined segmentation based on user and device contextual information. Which two technologies must be implemented to meet these requirements? (Choose two.)
A. Clean Access
B. Identity Service Engine
C. TrustSec
D. Secure Access Control System
E. NAC Agent
A network engineer is designing an access layer that requires all uplinks to be active. Furthermore, VLANs must span across the entire switch block. What design fulfills this requirement?
A. Layer 2 looped triangle
B. Layer 2 looped square
C. Layer 2 loop-free U
D. Layer 2 loop-free inverted U
What are the two main elements used by RBAC to provide secure access within an Enterprise? (Choose two.)
A. User privileges
B. User roles
C. User profile
D. User locales
E. User domains
A network engineer must select a network technology to simplify the extension of Layer 2 networks between data centers with a requirement of less than 4,000 VLANs. Which two network technologies accomplish this requirement? (Choose two.)
A. MPLS
B. L2TP
C. VXLAN
D. LISP
Which of these Layer 2 access designs does not support VLAN extensions?
A. FlexLinks
B. loop-free U
C. looped square
D. looped triangle
E. loop-free inverted U
An OSPF router should have a maximum of how many adjacent neighbors?
A. 100
B. 80
C. 60
D. 50
An HSRP design requirement states that preemption must be enabled for the active switch, which is a Cisco 4507R. Assume a boot time of 300 seconds. Which setting of the preemption delay timer minimizes the loss of traffic?
A. 50 seconds
B. 100 seconds
C. 150 seconds
D. 200 seconds
An organization is acquiring another company and merging the two company networks. No subnets overlap, but the engineer must limit the networks advertised to the new organization. Which feature implements this requirement?
A. Stub area
B. Interface ACL
C. Route filtering
D. Passive interface
During an upgrade of an existing data center, a network team must design segmentation into existing networks. Due to legacy applications, the IP addresses cannot change. Which firewall deployment model meets these requirements?
A. Routed mode
B. Multicontext mode
C. Transparent mode
D. Cluster mode
When designing data centers for multitenancy, which two benefits are provided by the implementation of VSANs and zoning? (Choose two.)
A. Zones provide the ability to create many logical SAN fabrics on a single Cisco MDS 9100 family switch.
B. VSANs have their own set of services and address space, which prevents an issue in one VSAN from affecting others.
C. VSANs and zones use separate fabrics.
D. Zones allow an administrator to control which initiators can see which targets.
E. VSAN provides a means of restricting visibility and connectivity among devices connected to a zone.
Summary address blocks can be used to support which network application?
A. QoS
B. IPsec tunneling
C. Cisco TrustSec
D. NAT
E. DiffServ
What is the next action taken by the Cisco NAC Appliance after it identifies a vulnerability on a client device?
A. denies the client network resource access
B. repairs the effected devices
C. generates a Syslog message
D. permits the client but limits to guest access
An engineer wants to ensure that common services communicate to several applications in various EPGs. Which two features within Cisco ACI accomplish this goal? (Choose two.)
A. filter
B. contract
C. application profile
D. bridge domain
E. tenant
The network engineering team is interested in deploying NAC within the enterprise network to enhance security. What deployment model should be used if the team requests that the NAC be logically inline with clients?
A. Layer 2 in-band
B. Layer 2 out-of-band
C. Layer 3 in-band
D. Layer 3 out-of-band
Management has chosen to implement a top-of-the-rack data center design. Which two benefits of moving to this model are true? (Choose two.)
A. easier per rack upgrades
B. fewer ports required in the aggregation
C. fewer switches to manage
D. directly connected racks in the row
E. decreased cabling costs AE
A customer has an existing WAN circuit with a capacity of 10 Mbps. The circuit has 6 Mbps of various user traffic and 5 Mbps of real-time audio traffic on average. Which two measures could be taken to avoid loss of real time traffic? (Choose two.)
A. Police the traffic to 3.3 Mbps and allow excess traffic to be remarked to the default queue.
B. Configure congestion avoidance mechanism WRED within the priority queue.
C. Ensure that real time traffic is prioritized over other traffic.
D. Police the traffic to 5 Mbps and allow excess traffic to be remarked to the default queue.
E. Increase the WAN circuit bandwidth.
An engineer is redesigning the infrastructure for a campus environment. The engineer must maximize the use of the links between the core and distribution layers. By which two methods can this usage be maximized? (Choose two.)
A. Design with multiple unequal-cost links between the core and distribution layers.
B. Design the links between the core and distribution layers to use an IGP.
C. Design with multiple equal-cost links between the core and distribution layers.
D. Design the links between the core and distribution layers to use HSRP.
E. Design the links between the core and distribution layers to use RPVSTP+.
An engineer has proposed the deployment of a Cisco ACI fabric solution to introduce automation and zero-touch operation experience to a DC network. Which type of virtualization technology is utilized by the Cisco ACI to encapsulate the traffic inside the fabric and to virtualize the physical infrastructure?
A. IPsec
B. NSX
C. STP
D. VXLAN
Which two design concerns must be addressed when designing a multicast implementation? (Choose two.)
A. only the low-order 23 bits of the MAC address are used to map IP addresses
B. only the low-order 24 bits of the MAC address are used to map IP addresses
C. only the high-order 23 bits of the MAC address are used to map IP addresses
D. only the low-order 23 bits of the IP address are used to map MAC addresses
E. the 0x01004f MAC address prefix is used for mapping IP addresses to MAC addresses
F. the 0x01005e MAC address prefix is used for mapping IP addresses to MAC addresses
When designing a Data Center Interconnect solution, which two statements describe benefits of utilizing A-VPLS for Layer 2 extension? (Choose two.)
A. Redundancy is addressed without enabling Spanning Tree Protocol in the core.
B. The overlay of the Layer 2 connection on the Layer 3 transport hides any physical convergence.
C. Integrated Layer 3 technology responds upon failure.
D. A-VPLS utilizes the Cisco Catalyst 6500 Series VSS feature to provide native dual-homing.
E. A-VPLS provides flow-based load balancing over equal-cost multipath paths.
When a site has Internet connectivity with two different ISP’s, which two strategies are recommended to avoid becoming a BGP transit site? (Choose two.)
A. Advertise all routes to both ISPs.
B. Filter routes outbound to the ISPs.
C. Accept all inbound routes from the ISPs.
D. Filter routes inbound from the ISPs.
E. Use a single service provider.
Which of the following is true concerning best design practices at the switched Access layer of the traditional layer2 Enterprise Campus Network?
A. Cisco NSF with SSO and redundant supervisors has the most impact on the campus in the Access layer
B. Provide host-level redundancy by connecting each end device to 2 separate Access switches
C. Offer default gateway redundancy by using dual connections from Access switches to redundant Distribution layer switches using a FHRP
D. Include a link between two Access switches to support summarization of routing information from the Access to the Distribution layer
Which description of how virtual MAC addresses are assigned to the members of a GLBP group is true?
A. Each device assigns its own address
B. The AVG assigns the addresses
C. The AVF assigns the addresses
D. The device that has the highest IP address assigns the addresses B
What is the maximum number of routers that each OSPF area (including the backbone) should contain?
A. 30
B. 10
C. 50
D. 100
While designing quality of service policies, which two types of traffic must be prioritized as management traffic? (Choose two.)
A. RADIUS
B. SSH
C. SCP
D. HTTPS
E. ICMP
Which two protocols support simple plaintext and MD5 authentication? (Choose two.)
A. EIGRP
B. BGP
C. RIP
D. OSPF
E. IPv6
Which technology can block interfaces and provide a loop-free topology?
A. STP
B. VSS
C. VLAN
D. vPC
Which virtualization technology uses Layer 3 BFD to detect network failures between network devices?
A. VTP
B. VSS
C. vPC
D. Cisco Fabric Path
An engineer is working on an OSPF network design and wants to minimize the failure detection time and the impact on the router CPU. Which technology accomplishes this goal?
A. fast hellos
B. BFD
C. LSA pacing
D. LSA delay interval
Which three authentication services are supported by Cisco NAC Appliance? (Choose three.)
A. RADIUS
B. LDAP
C. Kerberos
D. TACACS+
E. local
F. SNMP
Which unique EIGRP feature allows for faster Layer 3 convergence?
A. fast EIGRP timers
B. feasible successors
C. hybrid routing protocol
D. Cisco proprietary protocol
A company requires redundancy for its multihomed BGP external connections. What two features can be configured on the WAN routers to automate failover for both outbound and inbound traffic? (Choose two.)
A. AS path prepending
B. local preference
C. floating static route
D. HSRP
E. MED
F. weight
An organization is creating a detailed QoS plan that limits bandwidth to specific rates. Which three parameters can be configured when attempting to police traffic within the network? (Choose three.)
A. Violating
B. Committed information rate
C. Peak information rate
D. Shaping rate
E. Bursting
F. Conforming
G. Exceeding
WHich option is correct when using Virtual Switching System
A. Both control planes forward traffic simultaneously
Which technology guarantees loop free network and does not contain the state "listening"?
A. RPVST+
B. STP
C. VSS
An engineer is working on a design solution for a large hub-and-spoke EIGRP network. Which feature helps to make this design more stable while also reducing resource utilization?
A. QoS
B. network summarization
C. stub routing
D. route filtering C
To which network layer should Cisco Express Forwarding be tuned to support load balancing and to make more informed forwarding decisions?
A. Layer 1
B. Layer 2
C. Layer 3
D. Layer 4
E. Layer 5
F. Layer 6
G. Layer 7
Which STP feature can prevent other switches on the network from becoming the root switch, but still allow that interface to particiate in STP otherwise?
A. BPDU Guard
An engineer is designing an OSPF network with multiple nonbackbone areas connected to the backbone area via a hub-and-spoke topology. Each hub-and-spoke topology has a large number of spoke routers connected to the hub that is functioning as an ABR to provide better segmentation. Which two actions improve the stability of this design? (Choose two.)
A. Configure hub-and-spoke areas as stub.
B. Implement summarization on the ASBR routers in the backbone area.
C. Use External Type 2 metric across the OSPF domain.
D. Configure hub-and-spoke areas as totally stubby.
E. Implement summarization on the ABR routers of hub-and-spoke areas.
Which three statements about 802.1X are true
A. it is IEEE standard
B. It works only with wired devices
C. It can allow and deny port access based on device identity
A company has a regulatory requirement that all connections between their sites must be encrypted in a manner that does not require maintenance of permanent tunnels. The remote offices are connected by a private MPLS-based service that requires a dynamically changing key, spoke-to-spoke communication, and reuse of the existing IP header. Which type of transport encryption must be used?
A. GRE VPN
B. DMVPN
C. GETVPN
D. standard IPsec VPN
At which layer in the ACI fabric are policies enforced?
A. endpoint
B. spine
C. APIC
D. leaf
What is an advantage of using the vPC feature in a data center environment?
A. VSS is a requirement.
B. Multiple instances of control plane are formed.
C. The control plane and management plane remain separate.
D. Cisco FabricPath technology does not have to be configured.
An engineer set up a multicast design using all three Cisco supported PIM modes. Which two characteristics of Bidirectional PIM in this situation are true? (Choose two.)
A. Membership to a bidirectional group is signaled via explicit join messages.
B. In Bidirectional PIM, the RP IP address can be shared with any other router interface.
C. Bidirectional PIM is designed to be used for one-to-many applications.
D. A Cisco router cannot support all three PIM modes simultaneously.
E. In Bidirectional PIM, the RP IP address does not need to be a router.
An OSPF router should participate in maximum of how many areas?
A. 3
B. 2
C. 1
D. 4
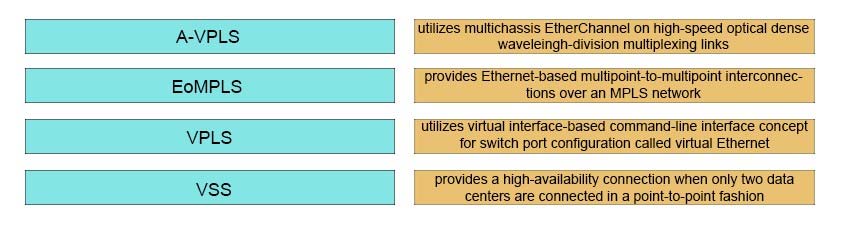
DRAG DROP - Drag and drop the Remote Data Center Layer 2 Extension option from the left onto its function on the right. Select and Place:
How does OTV provide STP isolation?
A. by using STP root optimization
B. by using BPDU filtering
C. by dropping BPDU packets
D. by using BPDU guard C
Refer to the exhibit. A customer discovers router R1 remains active even when the R1 uplink (F0/1) is down. Which two comments can be applied to R1 to allow R2 to take over as the HSRP active? (Choose two.)
A. standby 10 track 50 shutdown
B. standby 10 track 50 decrement 20
C. track 50 ip route 10.10.10.0/24 reachability
D. standby 10 track 50
E. track 50 interface Fa0/1 ip routing
Free Access Full 300-320 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 300-320 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 300-320 certification journey!