200-901 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 200-901 certification exam? Kickstart your success with our 200-901 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 200-901 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 200-901 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
A developer is working on an existing feature that needs enhancing. The primary production branch for the application is `prim4a3b8c6d80374' and the branch for working on the feature is `feat145678909'. The developer needs to create a clone of the single branch used for the feature that only has commits included in the current line of history. Which Git command must be used?
A. git clone [url] – -feat145678909 – -single-branch
B. git clone [url] – -branch feat145678909 – -single
C. git clone [url] – -single-branch feat145678909
D. git clone [url] – -branch feat145678909 – -single-branch
A new application is being developed that requires the ability to be copied and moved from one location to another. The existing infrastructure is already heavily utilized, so the new application must have a low resource footprint. The application includes a small PostgreSQL database component. Which application deployment type meets the requirements?
A. Python virtual environment
B. bare metal
C. virtual machine
D. container
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?
A company wants to automate the orders processed on its website using API. The network device that supports the solution must: · support XML encoding · support distributed transactions · support YANG data models · be support software redundancy Which requirement prevents the use of RESTCONF for the solution?
A. software redundancy
B. YANG data models
C. distributed transactions
D. XML encoding
Which configuration management tool has an agentless capability?
A. Puppet
B. CFEngine
C. Ansible
D. Chef
How does a developer create and switch to a new branch called `my-bug- x` to develop a product x?
A. git checkout -b my-bug- x
B. git branch -b my-bug- x
C. git branch my-bug- x
D. git checkout my-bug- x
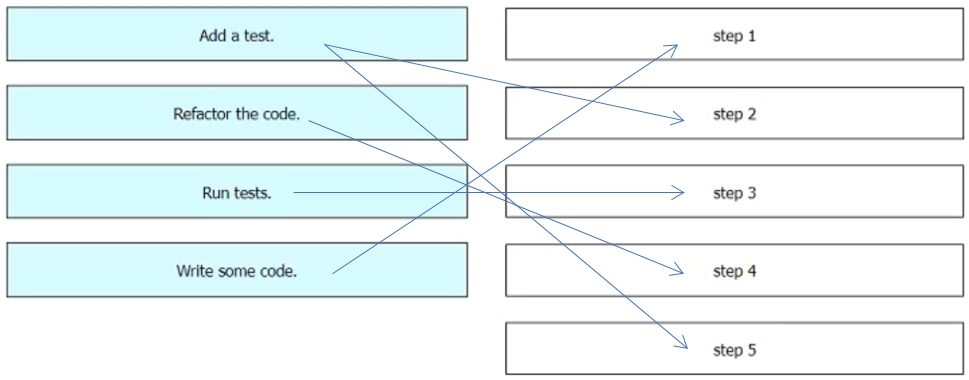
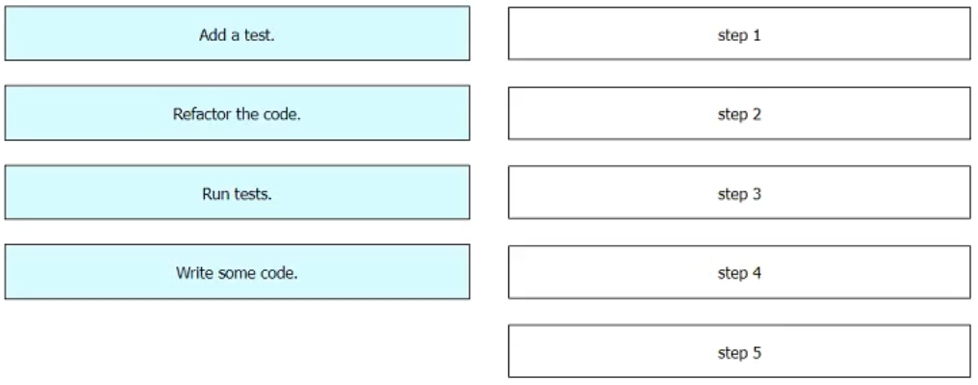
Drag and drop the steps from the left into the order on the right to create a testdriven development cycle. Some options are used more than once.
Select and Place:
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
A. 400
B. 403
C. 405
D. 429
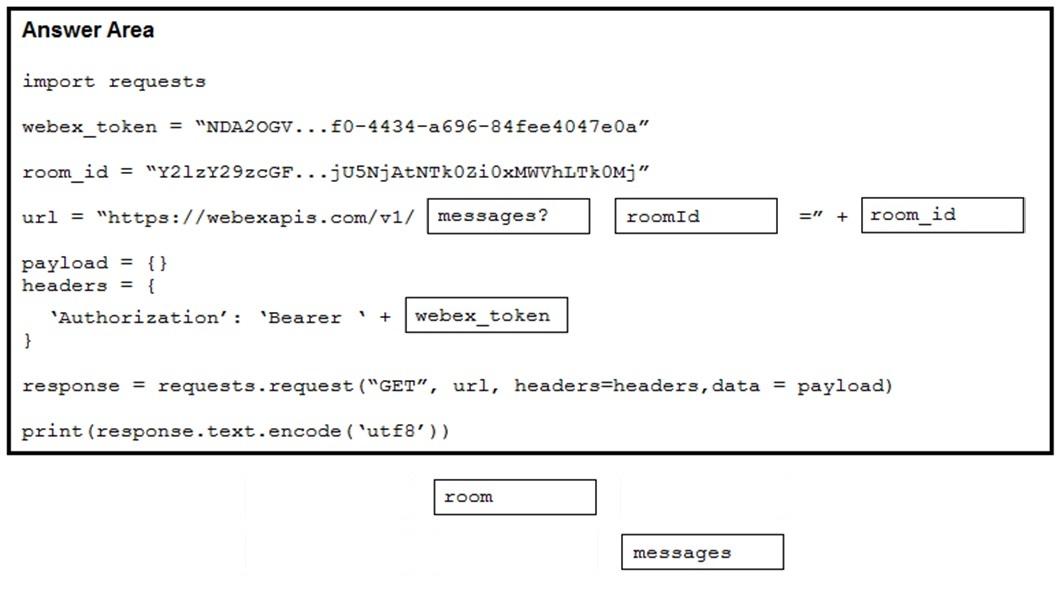
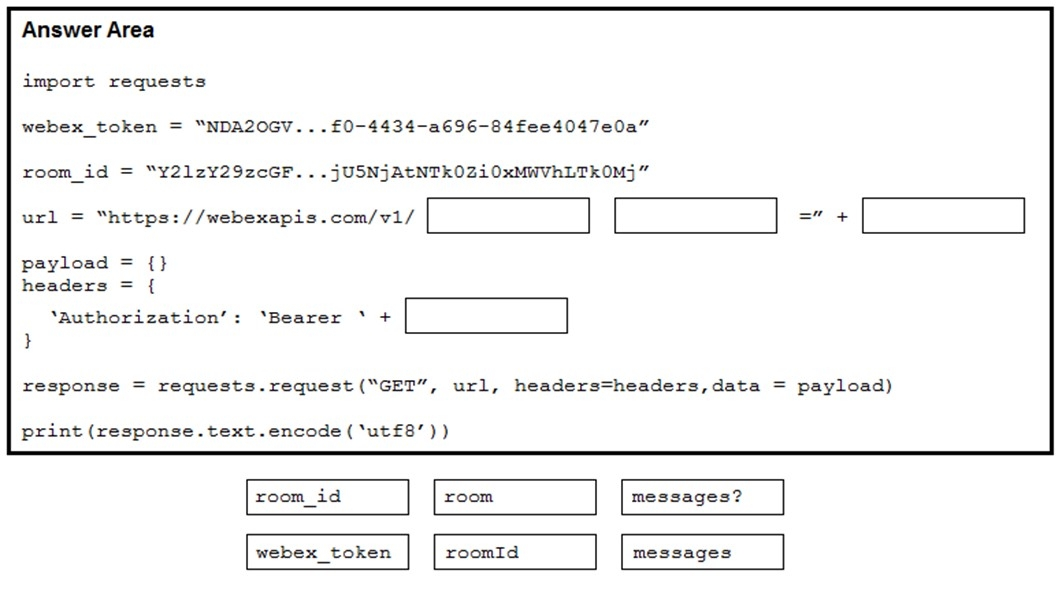
Refer to the exhibit. A developer needs to automatically retrieve all of the messages of a Webex room with the roomId of `Y2lzY29zcGFyazovL3Vz397468502YjU5NjAtNTk0Zi0xMWVhLTk0Mj`. Using the Webex API documentation shown, drag and drop the code snippets from below onto the code to complete the Python script to list all of the messages in the room. Not all options are used.
Select and Place:
An engineer must investigate the problems on a web application and address them to related teams. The engineer verifies the application reachability from the single public IP address with port and discovers that HTTPS access works to three servers of a network farm with IP 172.16.50.1 .2 and .4, but HTTPS access to the server with IP 172.16.50.3 does not work. Which problem type must be addressed as the cause for the case?
A. VPN connectivity
B. NAT
C. blocked transport port
D. proxy
What is a capability of the AXL API?
A. It adds a user to a collaboration space to share information and files.
B. It allows a meeting to be created with users that do not belong to same organization.
C. It collects information about system, cluster, and database settings.
D. It executes SQL commands in Cisco unified Communications Manager.
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario?
A. Database credentials should be accessed by using environment variables defined at runtime.
B. During the transport of webhook messages, the credentials could be unencrypted and leaked.
C. During logging, debugging should be disabled for the webhook message.
D. Hashing the credentials in the database is not secure enough; the credentials should be encrypted.
What are two advantages of the MVC design pattern? (Choose two.)
A. It represents the visualization of data contained with a model.
B. It allows filtering of a set of objects using different criteria.
C. It controls the data flow into a model object and updates a view whenever data changes.
D. It separates low-level data accessing operations from high-level business services.
E. It builds a final object through a step-by-step approach.
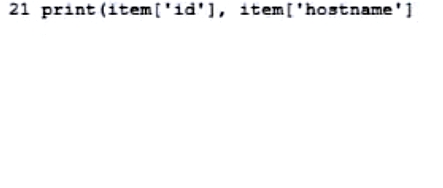
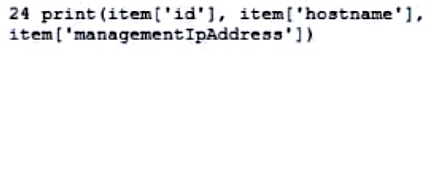
Refer to the exhibit. An engineer sends the request to collect data over Cisco AMP for Endpoints API. The Engineer must list guide and hostname data for all computers, but the first request returns only 500 items out of 2,000. Then, the engineer adds the loop to collect all the data. What must be added to the script where the code is missing to complete the requests?
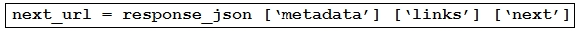

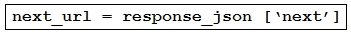
A. C
Refer to the exhibit. A developer must use a token to collect data from Cisco DNA Center API and prepares a Python script to send requests. Which line of codefineeds to be placed on the snippet where the code is missing to obtain a token from the Cisco DNA Center API?
A. token=BasicAuth(`user’,`password’))
B. auth=BasicAuth(`user’,`password’))
C. auth=HTTPBasicAuth(user,password))
D. token=HTTPBasicAuth(user,password))
A developer prepares an API to be used by administrators. API requires username and password to be verified for validated access to data, however username-password combination of users must not be sent to the API service itself. Authentication and authorization will be provided over the same mechanism. Which authentication mechanism must be used by the API service?
A. OAuth Authentication
B. Digest Access Authentication
C. Basic Authentication
D. API Key Authentication
Refer to the exhibit. A developer is using cURL to test connectivity to a webpage. The request times out after 10 seconds. The developer tested connectivity by using Ping and can open a TCP socket to the remote server by using Telnet. Other users confirm that they can access the webpage from their device. The developer has SSH access to the remote server and runs commands to troubleshoot. What causes the issue?
A. Connectivity from the remote server back to the client is down.
B. Firewall rules on the remote server block the client on port 443.
C. Application-layer security features on the remote server block the connection.
D. HTTPS proxy configured on the remote server blocks the connection.
What is a principle of Infrastructure as Code?
A. It requires manual resource provisioning.
B. It encourages overlaps in services.
C. It encourages repeatable processes.
D. It requires the use of large components.
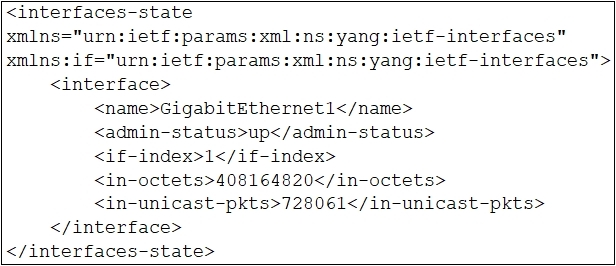
Refer to the exhibit. Which XML snippet has interface information that conforms to the YANG model?



Which network constraint causes the performance of the application to decrease as the number of users accessing the application increases?
A. latency
B. loss
C. bandwidth
D. jitter
DRAG DROP - Drag and drop the Python data transformation methods from the left onto the data formats on the right.
A web app must be accessible from computers and mobile devices. It must maintain the same data structure on both types of devices. What is the advantage of using the MVC design pattern for this app?
A. to asynchronously update the graphical interface
B. to define different algorithms for data manipulation
C. to separate the logic of the graphic interface of the different devices
D. to have only one instance of the objects that contain the data
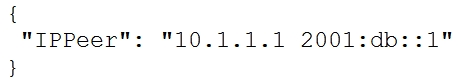
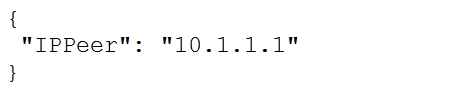
Refer to the exhibit.What is the value of the node defined by this YANG structure?

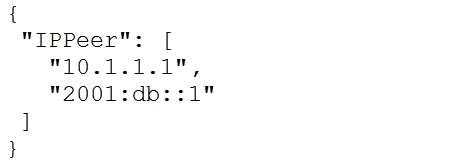
Refer to the exhibit. A developer needs to create a webhook to send all Cisco Webex messages to a third-party tool by using the Cisco Webex API The developer must authenticate with the API before any API calls can be made. To automate the procedure, a Python script is used. Which code snippet must be placed onto the blank in the code?
A. ‘Authentication’: f’Bearer {token}’,
B. ‘Authentication’: f’Basic {token}’,
C. ‘Authorization: f’Basic {token}’,
D. ‘Authorization: f’Bearer {token}’,
Refer to the exhibit. A network engineer is creating a Python script to programmatically save network device configurations. Which code snippet must be placed onto the blank in the code?
A. self.save
B. {self.headers}
C. restconf
D. netconf
What is a benefit of using a version control system?
A. tracks changes to the files
B. enforces change management controls
C. centralizes binary files
D. prevents code from being stored locally
Refer to the exhibit.Which two statements about the network diagram are true? (Choose two.)
A. The subnet address of PC-B has 18 bits dedicated to the network portion.
B. One of the routers has two connected serial interfaces.
C. R1 and R3 are in the same subnet.
D. PC-A and PC-B are in the same subnet.
E. The subnet of PC-C can contain 256 hosts.
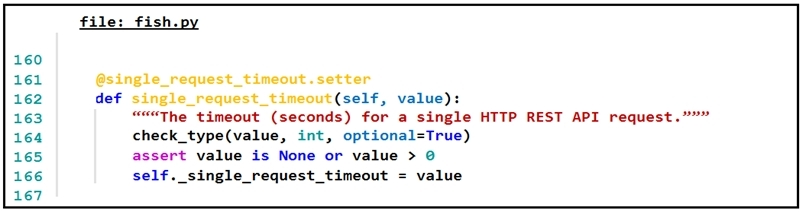
Refer to the exhibit.The output of a unified diff when comparing two versions of a Python script is shown. Which two `single_request_timeout()` functions are defined in sh.py and cat.py? (Choose two.)

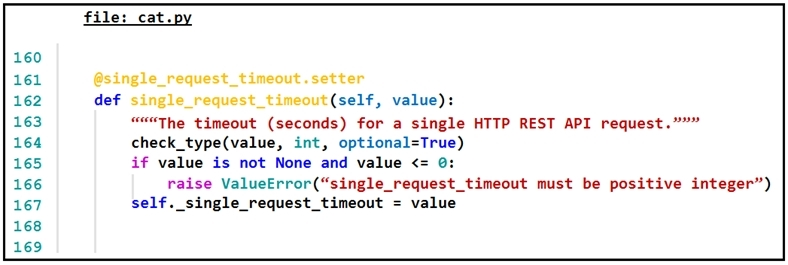
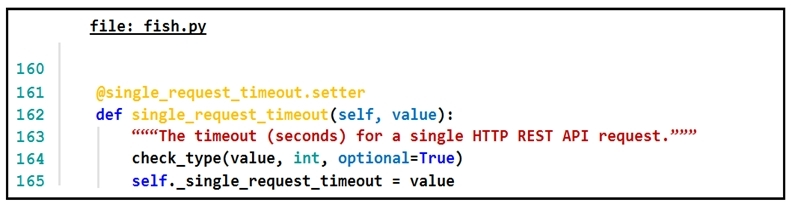
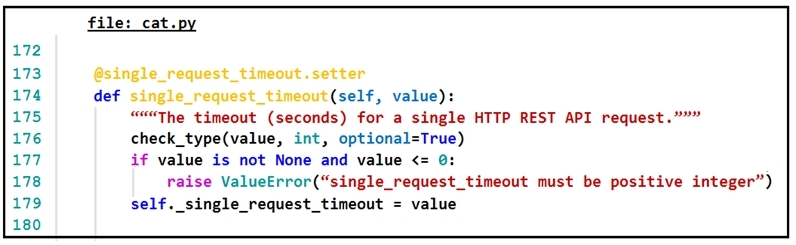
Which automation tool uses NEDs to abstract southbound interfaces?
A. Chef
B. Puppet
C. Ansible
D. Cisco NSO
Refer to the exhibit. A network engineer must change the configuration on devices daily. The Python script must collect CLI arguments from the user, organize data according to the Cisco-IOS-XE-native YANG model, and utilize Cisco REST APIs to make the configuration. Which work flow is being automated by the Python script?
A. updating an existing route on the device
B. adding a new route to a device
C. including a route on the device and overwriting the current routes
D. deleting the route that is passed through the command-line variables
What are two benefits of managing network configuration via APIs? (Choose two.)
A. more security due to locking out manual device configuration
B. configuration on devices becomes less complex
C. eliminates the need of legacy management protocols like SNMP
D. reduction in network changes performed manually
E. increased scalability and consistency of network changes
Package updates from a local server are failing to download. The same updates work when a much slower external repository is used. The server has the configuration: · hostname: devbox111012120 · IP: 192.168.1.51 · Mask: 255.255.255.0 Why are local updates failing?
A. The Internet is down at the moment, which causes the local server to not be able to respond.
B. The Internet connection is too slow.
C. The server is running out of disk space.
D. The update utility is trying to use a proxy to access the internal resource.
Which Cisco compute management platform is a premises based solution that Automates and Orchestrates Cisco and non-Cisco infrastructure?
A. UCS Manager
B. Cisco Integrated Management Controller
C. UCS Director
D. Cisco Intersight
What is a benefit of a model-driven approach for infrastructure automation?
A. It automates the translation of a declarative language of the model into an actionable script.
B. It enforces the generation and verification of all automation scripts through the modeling environment.
C. It provides a small learning curve and helps system administrators with limited coding experience.
D. It ensures that system administrators gain a good understanding of coding, and expand their experience and capabilities.
What is an advantage of using network programmability?
A. Manual configuration is faster.
B. No cloud abstraction occurs.
C. It removes CLI access for devices.
D. It provides for more scalable and replicable network provisioning.
Refer to the exhibit. A developer can access the TLS REST API on server A, but cannot access the API on server
A. The developer can ping server
B. When the developer performs a packet capture on the TLS REST API port on server B, the capture shows that the packet arrived and the server responded. What causes the issue?
C. Port 80 is blocked on the outgoing interface of firewall
D. Port 443 is blocked on the outgoing interface of firewall
E. Port 443 is blocked on the incoming interface of firewall
F. Port 80 is blocked on the incoming interface of firewall
G.
A small company has 5 servers and 50 clients. What are two reasons an engineer should split this network into separate client and server subnets? (Choose two.)
A. Subnets will split domains to limit failures.
B. A router will limit the traffic types between the clients and servers.
C. Subnets provide more IP address space for clients and servers.
D. A router will bridge the traffic between clients and servers.
E. Internet access to the servers will be denied on the router.
Which protocol runs over TCP port 22?
A. SSH
B. NETCONF
C. HTTP
D. Telnet
Refer to the exhibit. What are two results of running the RESTCONF query? (Choose two.)
A. GigabitEthernet1 becomes shut down.
B. Interfaces are created as containers.
C. GigabitEthernet2 becomes shut down.
D. Descriptions for two interfaces are applied.
E. The module left-interfaces:interfaces is created.
What is the purpose of the Cisco VIRL software tool?
A. to verify configurations against compliance standards
B. to automate API work ows
C. to simulate and model networks
D. to test performance of an application
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?
A. Cisco Open NX-OS
B. Cisco NX-OS SDK
C. Cisco Learning Labs
D. Cisco Code Exchange for Nexus
Which type of HTTP method is used by the Meraki and Webex Teams APIs to send webhook notifications?
A. HTTP POST
B. HTTP GET
C. HTTP HEAD
D. HTTP PUT
What are two key capabilities of Cisco Finesse? (Choose two.)
A. Agents access Finesse from a browser without needing to install or configure anything on the client machine.
B. An OpenDNS utility is preconfigured and ready to use on Finesse.
C. Gadget containers provide a seamless experience in a single user interface.
D. Finesse automatically collects telemetry data.
E. Finesse includes an RPC API that enables the development of custom gadgets.
What is a difference between REST and RPC API styles?
A. RPC uses HTML format and REST uses JSON format.
B. RPC has a single style and REST has multiple styles
C. RPC uses the POST operation to update and REST uses the PUT operation to update.
D. RPC is stateful in nature and REST is stateless in nature.
A developer is working on a branch called topic that was created from the master branch to add a new feature to the product. After making a few commits on the branch, the developer wants to compare the changes between the topic and the master branches. Which two Git commands are used? (Choose two.)
A. git diff topic – -cached
B. git diff topic…master
C. git diff topic HEAD
D. git diff topic-master
E. git diff topic master
Refer to the exhibit. A developer needs to write a Python script to automate a task using a NETCONF query. What does the query do?
A. It deletes some device configurations.
B. It deletes all the device configurations.
C. It shuts off the device.
D. It adds a new device configuration.
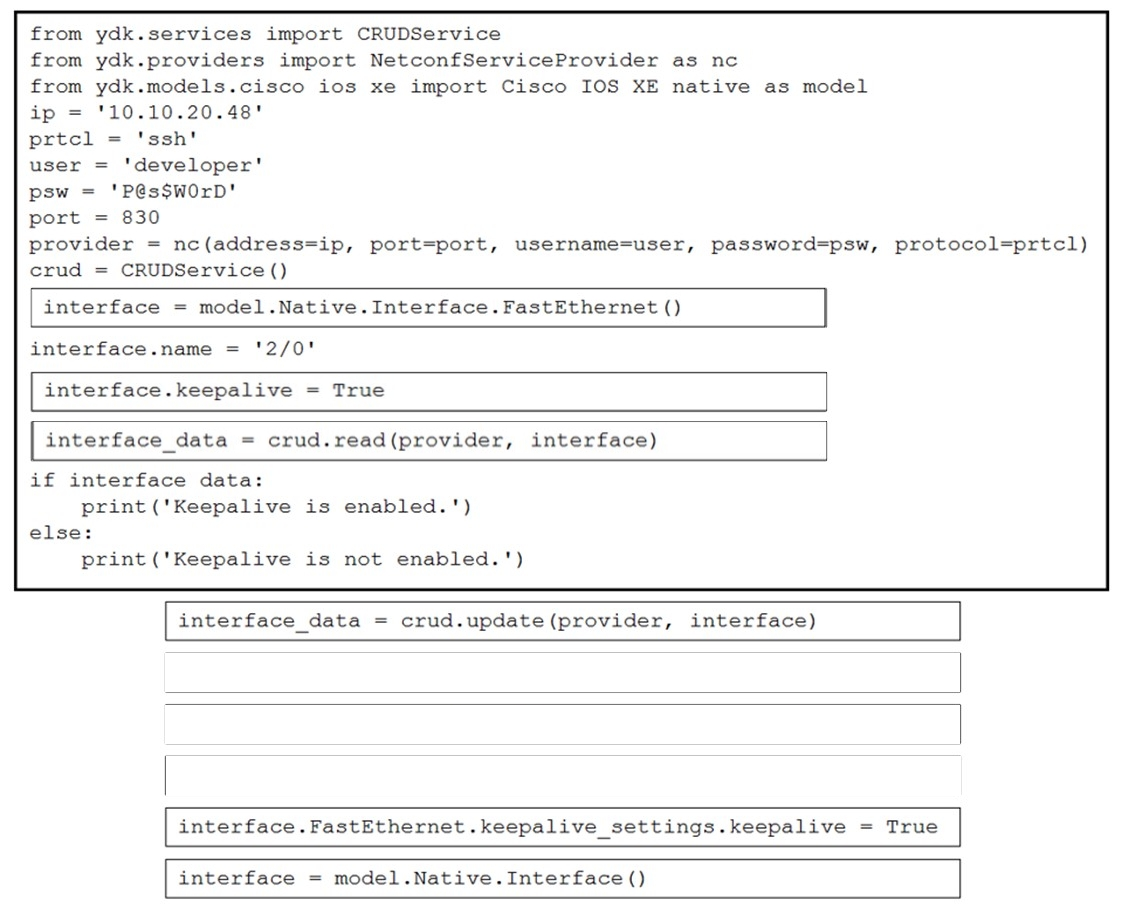
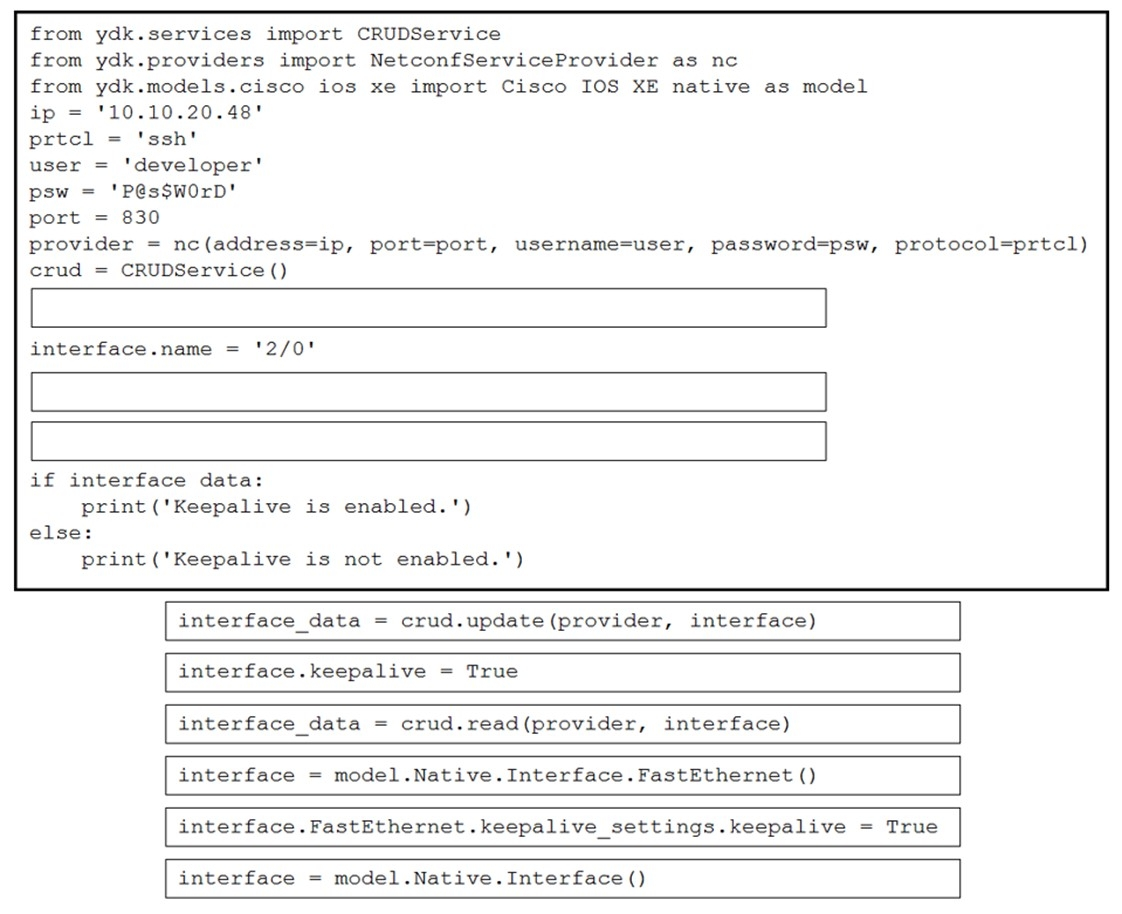
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
Select and Place:
Refer to the exhibit.The definition of the YANG module and a RESTCONF query sent to a Cisco IOS XE device is shown. Why does the RESTCONF interface respond with a 204 status code?
A. The query retrieved the logging severity level.
B. The query updated the logging severity level or created it if not present on the device.
C. The query failed at retrieving the logging severity level.
D. The query failed to set the logging severity level due to an invalid path.
xml/ios/prog/configuration/1611/b_1611_programmability_cg/restconf_programmable_interface.html Community vote distribution
An engineer must configure Cisco Nexus devices and wants to automate this work flow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code, which resource must be used to verify that the code works correctly?
A. Cisco NX-OS SDK
B. Cisco Learning Labs
C. Cisco Code Exchange
D. Cisco Modeling Labs
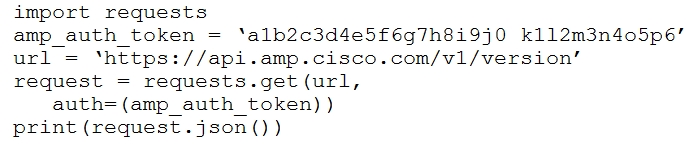
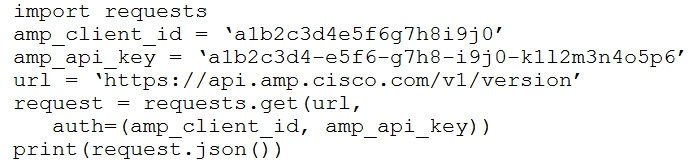
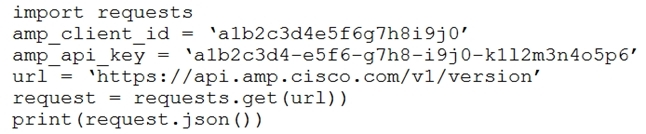
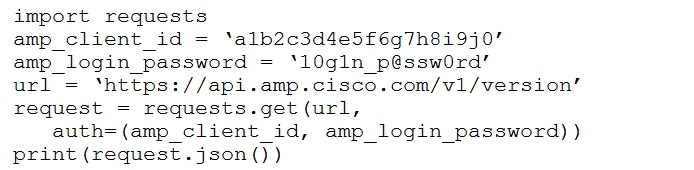
Refer to the exhibit.The documentation outlines how to use credentials for the AMP API. Which script successfully performs an API call using basic authentication?
Free Access Full 200-901 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 200-901 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 200-901 certification journey!