101 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 101 certification exam? Kickstart your success with our 101 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 101 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 101 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
The BIG-IP determines the lowest connection speed between the client and the server and then uses that for both connections.
A. True
B. False
ARX can classify data based on all of the following EXCEPT:
A. Paths
B. File Size
C. Extensions
D. Security Level
E. File Name
Similar to LTM monitors, GTM monitors use both an Interval and a Timeout value.
A. True
B. False
Monitors can be assigned to which three resources? (Choose three.)
A. NATs
B. pools
C. iRules
D. nodes
E. SNATs
F. pool members
G. virtual servers
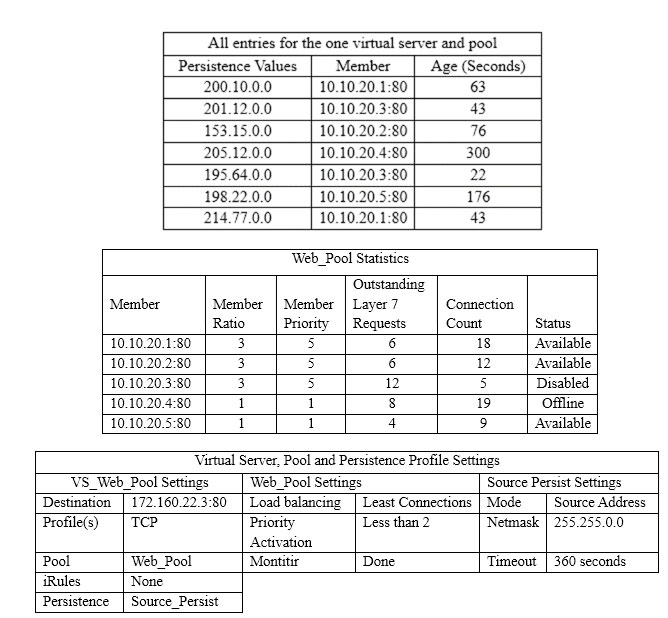
A virtual server is defined using a source address based persistence profile. The last five connections were A, B, C, A, C. Given the conditions shown in the graphic, if a client with IP address 205.12.45.52 opens a connection to the virtual server, which member will be used for the connection?
A. 10.10.20.1:80
B. 10.10.20.2:80
C. 10.10.20.3:80
D. 10.10.20.4:80
E. 10.10.20.5:80
Select the best word or phrase to complete the following sentence. Using the _______ feature in GTM, F5's Application Delivery Firewall solution can handle a significantly higher number of queries than traditional DNS servers.
A. DNS Express
B. BIND
C. Site availability request
D. Location-based routing
Which two processes are involved when BIG-IP systems issue traps? (Choose two.)
A. bigd
B. alertd
C. smtpd
D. syslogng
Monitors can be assigned to which three resources? (Choose three.)
A. Pools
B. Servers
C. Wide-IPs
D. Data Centers
E. Pool Members
If your customer has a policy requirement that cannot be handled in the Visual Policy Editor, what would you use to supplement the Visual Policy Editor?
A. iApps
B. TMOS
C. iControl
D. iRules
When using SNAT, which additional IP addresses will the BIG-IP system change? (Choose two.)
A. The source IP address on the client to BIG-IP request packet.
B. The source IP address on the BIG-IP to pool member request packet.
C. The destination IP address on the BIG-IP to pool member request packet.
D. The source IP address on the BIG-IP to client response packet.
E. The destination IP address on the BIG-IP to client response packet.
F. The destination IP address on the pool member to BIG-IP response packet.
When an optimized TCP connection exists between LTM and the pool member, LTM can accept server responses faster than the client. What is the name of this feature?
A. HTTP caching
B. OneConnect
C. TCP connection queuing
D. Content spooling
E. Priority activation
Which of the following is not a configurable parameter data type?
A. Email
B. Array
C. Binary
D. Decimal
Identifying users by their IP address is a sufficient method of performing authentication and authorization.
A. True
B. False
What is the difference between primary and secondary DNS servers?
A. Only primary servers can issue authoritative responses.
B. Primary servers host the original copy of the zone database file.
C. Primary servers resolve names more efficiently than secondary servers.
D. Secondary servers act as backups and will respond only if the primary fails.
Which of the following statements about cookie persistence is NOT true?
A. The cookie’s timeout value can be customized.
B. They are F5’spreferred persistence method.
C. No persistence information is placed on LTM.
D. Web servers must be configured to send cookies to clients.
E. They do not add a performance impact on LTM.
Which of the following is correct regarding static parameters?
A. A static parameter is stored in a frame cookie.
B. A static parameter is predefined by the web application logic.
C. A static parameter is learned only by using the Deployment Wizard.
D. A static parameter is mapped once when creating the application flow model.
In order to ensure that a specific file type is never moved down to a secondary file tier, the administrator should:
A. Set up an automated bot that accesses that file once a week.
B. This is not possible on the ARX.
C. Set a policy that the file type remains on primary storage.
D. Instruct the end users to put the file in a non-tiered directory.
Which aspect of F5's Intelligent Services Platform helps you extend your security conversation to include F5professionals and customers?
A. Modular Functionality
B. iApps
C. TMOS
D. DevCentral
Which two of the following options can LTM use when all of the pool members are not available or if the pool is overloaded?
A. Floating IPs
B. Fallback host
C. Auto last hop
D. SNAT automap
E. Pool offload
F. Priority group activation
APM provides access control lists at which two OSI layers? (Choose two.)
A. Layer 5
B. Layer 4
C. Layer 7
D. Layer 6
E. Layer 2
Which of the following are four of the benefits of the TMOS architecture? (Choose four.)
A. User authentication
B. Server-side optimization
C. Dynamic DDoS protection
D. Web application security
E. Client-side optimization
F. Antivirus checking
Which two statements are true concerning the default communication between a redundant pair of BIG-IP systems? (Choose two.)
A. Synchronization occurs via a TCP connection using ports 683 and 684.
B. Connection mirroring data is shared via a TCP connection using port 1028.
C. Persistence mirroring data is shared via a TCP connection using port 1028.
D. Connection mirroring data is shared through the serial failover cable unless network failover is enabled.
Using IP Geolocation, an organization can always direct a client request from France to a datacenter in Dublin.
A. True
B. False
What are the best reasons for using the Deployment Wizard? (Choose three.)
A. Flow level parameters checking is required.
B. The application encoding scheme needs to be determined by the BIG-IP ASM System.
C. Sufficient time is available to allow completely automated policy building based on observing live traffic.
D. The application platform must be protected against known attacks for the specific operating system, web server, and database.
Which two methods can be used to determine which BIG-IP is currently active? (Choose two.)
A. The bigtop command displays the status.
B. Only the active system’s configuration screens are active.
C. The status (Active/Standby) is embedded in the command prompt.
D. The ifconfig a command displays the floating addresses on the active system.
One reason APM beats the competition is its ability to perform both user authentication and authorization on a single device.
A. True
B. False
What is the main business driver for bringing Enterprise Manager into the network infrastructure?
A. Consolidate management of administrator and user accounts
B. Consolidate management of licenses
C. Consolidate management of SSL certificates
D. Consolidate management of BIG-IP devices
E. Consolidate management of access policies
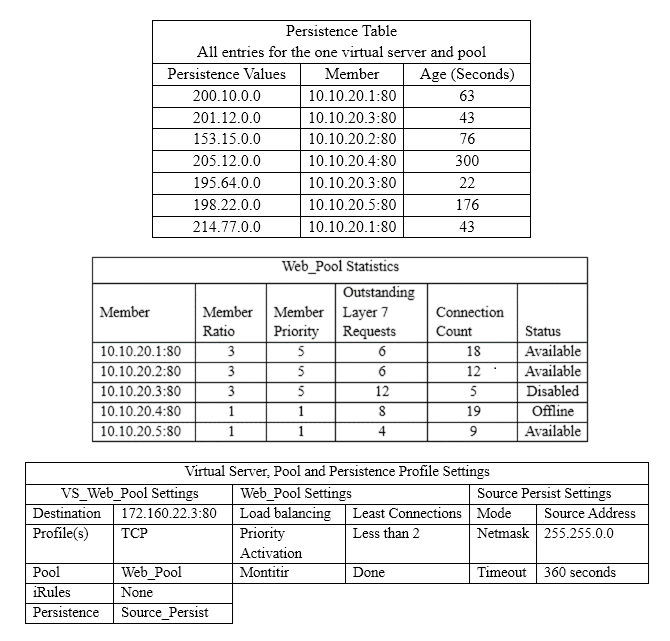
The incoming client IP address is 195.64.45.52 and the last five connections have been sent to members A, C, E, D and B. Given the virtual server, pool, and persistence definitions and statistics shown in the above graphic, which member will be used for the next connection?
A. 10.10.20.1:80
B. 10.10.20.2:80
C. 10.10.20.3:80
D. 10.10.20.4:80
E. 10.10.20.5:80
F. It cannot be determined with the information given.
Which action CANNOT be performed by an iRule?
A. Direct a connection request to a specific pool.
B. Substitute a server’s response with alternate data.
C. Chang the virtual server’s default pool.
D. Direct a client’s request to a pool based on the client’s browser’s language.
E. Limit a given client to a set amount of bandwidth.
F. Discard a client before connecting to a server.
Which of the following are four of the security benefits of TMOS? (Choose four.)
A. It verifies traffic based on antivirus signatures.
B. It provides protection against DDoS.
C. It uses SYN cookies and dynamic connection reapers.
D. It supplies guidance for poorly developed applications.
E. It denies all traffic that hasn’t been defined.
F. It can hide confidential information from outbound traffic.
ASM provides antivirus protection by:
A. Extracting files being uploaded and sending them to an AV system via ICAP
B. Running a local antivirus program on the BIG-IP
C. None of the above
D. Using IP Penalty enforcement to block requests from hackers IPs
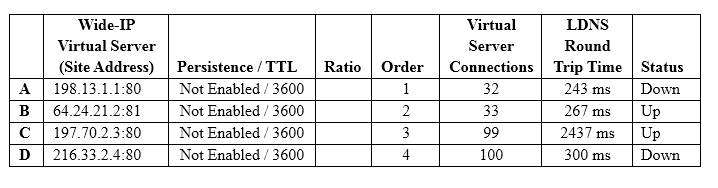
A pool is using Round Trip Time as its load balancing method (Alternate: Round Robin; Fallback:None). The last five resolutions have been C, D, C, D, C. Given the current conditions shown in the table below, which address will be used for the next resolution?
A. A
B. B
C. C
D. D
Which VLANs must be enabled for a SNAT to perform as desired (translating only desired packets)?
A. The SNAT must be enabled for all VLANs.
B. The SNAT must be enabled for the VLANs where desired packets leave the BIG-IP.
C. The SNAT must be enabled for the VLANs where desired packets arrive on the BIG-IP.
D. The SNAT must be enabled for the VLANs where desired packets arrive and leave the BIG-IP.
Which four of these scenarios will benefit from F5's WAN Optimization Module? (Choose four.)
A. An international organization with data centers in different countries.
B. An organization that does not want to rely on using tape backup.
C. An organization with one site but hundreds of Web servers.
D. An organization whose users create extremely large files.
E. An organization that expects their Web site usage to double in the next year.
F. An organization attempting to lower costs by reducing the number of data centers.
Select F5 platforms have which three certifications? (Choose three.)
A. FIPS
B. SECG
C. NEBS
D. IEEE
E. Common Criteria
F. AFSSI
Which of the following is correct regarding User-defined Attack signatures?
A. User-defined signatures use an F5-supplied syntax
B. User-defined signatures may only use regular expressions
C. Attack signatures may be grouped within system-supplied signatures
D. User-defined signatures may not be applied globally within the entire policy
An administrator is adding GTM to the network infrastructure. Which of the following requirements would lead them to select an Authoritative Screening architecture rather than Delegation?
A. They want GTM to examine all DNS queries.
B. They want GTM to make load balancing decisions based on metrics.
C. They have data centers in several countries.
D. They are using several operating systems for the local DNS servers.
Using Fast Cache with ASM will:
A. Improve user experience
B. Improve server performance
C. All of the above
D. Improve BIG-IP ASM performance
Which of the following is NOT a benefit of using SSL offload?
A. It increases the bandwidth between the client and LTM.
B. It enables LTM to decrypt traffic, examine the payload, and then re-encrypt before sending it to a pool member.
C. The organization requires far less SSL certificates.
D. The CPU processing load on backend servers is reduced.
E. It enables iRules to be used on traffic arriving to LTM that is encrypted.
Select the question you would ask your customer related to DNS attacks. Based on the material, choose the most appropriate question.
A. How do you secure you DNS infrastructure against attacks?
B. Do you rely on your network firewall to protect you DNS server?
C. Do you over-provision your DNS infrastructure?
D. Do you regularly update BIND or some other DNS application to the latest release?
What percentage of storage in a typical environment is actively used and modified?
A. 5%
B. 50%
C. 25%
D. 10%
E. 90%
Which of the following statements best describes the ARX architecture?
A. The ARX’s split path architecture has a data path that handles the most common operations, and a control path that handles other operations requiring deeper inspection and updating of the index.
B. The ARX’s architecture has redundancy built in, allowing a single ARX to be deployed in most use cases which provides a huge cost savings to customers.
C. All of the above.
D. It is a software agent that installs on the storage device.
In the following configuration, a virtual server has the following HTTP class configuration:A request arriving for WWW.F5.COM will be matched by which class(es)?
A. Class 1
B. Class 2
C. Both Class 1 and Class 2
D. The request will be dropped
By default, how frequently are log files rotated?
A. hourly
B. daily
C. weekly
D. There is no default; the administrator sets the frequency.
When configuring monitors for individual pool members, which three options can be selected? (Choose three.)
A. inherit the pool’s monitor
B. choose a default monitor
C. inherit the Wide-IP’s monitor
D. assign a monitor to the specific pool member
E. do not assign any monitor to the specific pool member
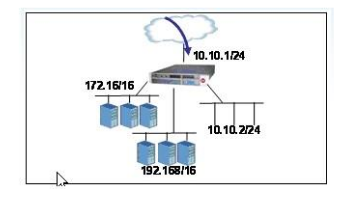
An LTM has the 3 virtual servers, four self IP addresses defined and the networks shown in the exhibit. Selected options for each object are shown below. Settings not shown are at their defaults.A connection attempt is made with a source IP and port of 10.20.100.50:2222 and a destination IP and port of 10.10.2.102:80. When the request is processed, what will be the destination IP address?
A. Destination IP: 10.10.2.102
B. The request will be dropped.
C. Destination IP: pool member in the 192.168/16 network
D. Destination IP: pool member in the 172.16/16 network
To make complex access policies easier to manage, an administrator can create a _______ containing several policy actions, and then add instances of it within the policy? (Fill in)
A. Visual Policy Editor
B. Policy Editor
C. Visual Editor
D. Policy creator
When an administrator creates a new access policy in the Visual Policy Editor, which three options are included by default? (Choose three.)
A. A fallback option
B. An Allow Ad box
C. A Deny End box
D. An empty Resource Assign item
E. A Start box
F. A Block All option
Which item is NOT a function of a properly deployed and configured ASM?
A. Detects attacks
B. Stops hackers from attacking
C. Provides protection visibility
D. Provides security agility
When sizing a WebAccelerator deployment, you should base the WA capacity on the LTMcapacity.
A. True
B. False
Free Access Full 101 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 101 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 101 certification journey!