PCCSE Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the PCCSE exam? Start with our PCCSE Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a PCCSE practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free PCCSE practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Console is running in a Kubernetes cluster, and you need to deploy Defenders on nodes within this cluster. Which option shows the steps to deploy the Defenders in Kubernetes using the default Console service name?
A. From the deployment page in Console, choose pod name for Console identifier, generate DaemonSet file, and apply the DaemonSet to twistlock namespace.
B. From the deployment page configure the cloud credential in Console and allow cloud discovery to auto-protect the Kubernetes nodes.
C. From the deployment page in Console, choose twistlock-console for Console identifier, generate DaemonSet file, and apply DaemonSet to the twistlock namespace.
D. From the deployment page in Console, choose twistlock-console for Console identifier, and run the curl | bash script on the master Kubernetes node.
What are the subtypes of configuration policies in Prisma Cloud?
A. Security and Compliance
B. Build and Deploy
C. Build and Run
D. Monitor and Analyze
Which intensity setting for anomaly alerts is used for the measurement of 100 events over 30 days?
A. High
B. Medium
C. Low
D. Very High
Which three actions are required in order to use the automated method within Azure Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose three.)
A. Install boto3 & requests library.
B. Configure IAM Azure remediation script.
C. Integrate with Azure Service Bus.
D. Configure IAM AWS remediation script.
E. Install azure.servicebus & requests library.
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying. How should the customer automate vulnerability scanning for images deployed to Fargate?
A. Set up a vulnerability scanner on the registry
B. Embed a Fargate Defender to automatically scan for vulnerabilities
C. Designate a Fargate Defender to serve a dedicated image scanner
D. Use Cloud Compliance to identify misconfigured AWS accounts
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
A. API_ENDPOINT
B. SQS_QUEUE_NAME
C. SB_QUEUE_KEY
D. YOUR_ACCOUNT_NUMBER
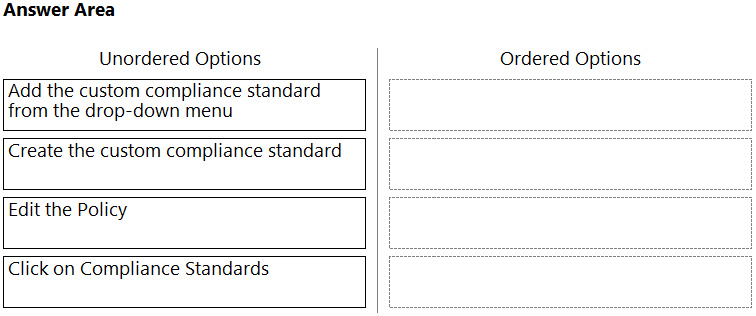
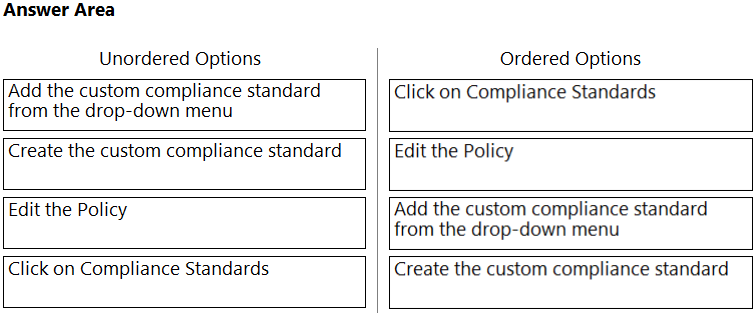
DRAG DROP - Which order of steps map a policy to a custom compliance standard? (Drag the steps into the correct order of occurrence, from the first step to the last.) Select and Place:
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
A. Notifications
B. Policies
C. Alert Rules
D. Events
Which two actions are required in order to use the automated method within Amazon Web Services (AWS) Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose two.)
A. Install boto3 & requests library.
B. Configure IAM Azure remediation script.
C. Integrate with Azure Service Bus.
D. Configure IAM AWS remediation script.
Which container image scan is constructed correctly?
A. twistcli images scan –docker-address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
B. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 myimage/latest
C. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 –container myimage/latest
D. twistcli images scan –address https://us-west1.cloud.twistlock.com/us-3-123456789 –container myimage/latest –details
Which role does Prisma Cloud play when configuring SSO?
A. JIT
B. Service provider
C. SAML
D. Identity provider issuer
A user from an organization is unable to log in to Prisma Cloud Console after having logged in the previous day. Which area on the Console will provide input on this issue?
A. SSO
B. Audit Logs
C. Users & Groups
D. Access Control
Which step is included when configuring Kubernetes to use Prisma Cloud Compute as an admission controller?
A. copy the Console address and set the config map for the default namespace.
B. create a new namespace in Kubernetes called admission-controller.
C. enable Kubernetes auditing from the Defend > Access > Kubernetes page in the Console.
D. copy the admission controller configuration from the Console and apply it to Kubernetes.
Which policy type provides information about connections from suspicious IPs in a customer database?
A. Anomaly
B. Threat detection
C. Network
D. AutoFocus
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
A. Host
B. Container
C. Functions
D. Image
An administrator of Prisma Cloud wants to enable role-based access control for Docker engine. Which configuration step is needed first to accomplish this task?
A. Configure Docker’s authentication sequence to first use an identity provider and then Console.
B. Set Defender’s listener type to TCP.
C. Set Docker’s listener type to TCP.
D. Configure Defender’s authentication sequence to first use an identity provider and then Console.
Which three OWASP protections are part of Prisma Cloud Web-Application and API Security (WAAS) rule? (Choose three.)
A. DoS Protection
B. Local file inclusion
C. SQL injection
D. Suspicious binary
E. Shellshock
Which of the following is a reason for alert dismissal?
A. SNOOZED_AUTO_CLOSE
B. ALERT_RULE_ADDED
C. POLICY_UPDATED
D. USER_DELETED
Which data security default policy is able to scan for vulnerabilities?
A. Objects containing Vulnerabilities
B. Objects containing Threats
C. Objects containing Malware
D. Objects containing Exploits
Which two statements apply to the Defender type Container Defender - Linux?
A. It is implemented as runtime protection in the userspace.
B. It is deployed as a service.
C. It is deployed as a container.
D. It is incapable of filesystem runtime defense.
Which two options may be used to upgrade the Defenders with a Console v20.04 and Kubernetes deployment? (Choose two.)
A. Run the provided curl | bash script from Console to remove Defenders, and then use Cloud Discovery to automatically redeploy Defenders.
B. Remove Defenders DaemonSet, and then use Cloud Discovery to automatically redeploy the Defenders.
C. Remove Defenders, and then deploy the new DaemonSet so Defenders do not have to automatically update on each deployment.
D. Let Defenders automatically upgrade.
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time. What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
A. manual installation of the latest twistcli tool prior to the rolling upgrade
B. all Defenders set in read-only mode before execution of the rolling upgrade
C. a second location where you can install the Console
D. additional workload licenses are required to perform the rolling upgrade
E. an existing Console at version n-1
Where can Defender debug logs be viewed? (Choose two.)
A. /var/lib/twistlock/defender.log
B. From the Console, Manage > Defenders > Manage > Defenders. Select the Defender from the deployed Defenders list, then click Actions > Logs
C. From the Console, Manage > Defenders > Deploy > Defenders. Select the Defender from the deployed Defenders list, then click Actions > Logs
D. /var/lib/twistlock/log/defender.log
Which two information types cannot be seen in the data security dashboard? (Choose two.)
A. Top Publicly Exposed Objects By Data Profile
B. Bucket owner
C. Object content
D. Total objects
E. Object Data Profile by Region
When an alert notification from the alarm center is deleted, how many hours will a similar alarm be suppressed by default?
A. 12
B. 8
C. 24
D. 4
The attempted bytes count displays?
A. traffic that is either denied by the security group or firewall rules or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
B. traffic that is either denied by the security group or firewall rules.
C. traffic that is either denied by the firewall rules or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
D. traffic denied by the security group or traffic that was reset by a host or virtual machine that received the packet and responded with a RST packet.
Which options show the steps required after upgrade of Console?
A. Uninstall Defenders Upgrade Jenkins Plugin Upgrade twistcli where applicable Allow the Console to redeploy the Defender
B. Update the Console image in the Twistlock hosted registry Update the Defender image in the Twistlock hosted registry Uninstall Defenders
C. Upgrade Defenders Upgrade Jenkins Plugin Upgrade twistcli where applicable
D. Update the Console image in the Twistlock hosted registry Update the Defender image in the Twistlock hosted registry Redeploy Console
What is required for Prisma Cloud to successfully execute auto-remediation commands?
A. Access to the cloud platform only for Azure
B. Write access to the cloud platform
C. Read access to the cloud platform
D. Prisma Cloud requires no access to the cloud platform
An administrator has access to a Prisma Cloud Enterprise. What are the steps to deploy a single container Defender on an ec2 node?
A. Pull the Defender image to the ec2 node, copy and execute the curl | bash script, and start the Defender to ensure it is running.
B. Execute the curl | bash script on the ec2 node.
C. Configure the cloud credential in the console and allow cloud discovery to auto-protect the ec2 node.
D. Generate DaemonSet file and apply DaemonSet to the twistlock namespace.
A business unit has acquired a company that has a very large AWS account footprint. The plan is to immediately start onboarding the new company's AWS accounts into Prisma Cloud Enterprise tenant immediately. The current company is currently not using AWS Organizations and will require each account to be onboarded individually. The business unit has decided to cover the scope of this action and determined that a script should be written to onboard each of these accounts with general settings to gain immediate posture visibility across the accounts. Which API endpoint will specifically add these accounts into the Prisma Cloud Enterprise tenant?
A. https://api.prismacloud.io/cloud/
B. https://api.prismacloud.io/account/aws
C. https://api.prismacloud.io/cloud/aws
D. https://api.prismacloud.io/accountgroup/aws
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated. Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
A. 1) https://api.prismacloud.io/compliance/add2) https://api.prismacloud.io/compliance/requirementld/section3) https://api.prismacloud.io/compliance/complianceld/requirement
B. 1) https://api.prismacloud.io/compliance2) https://api.prismacloud.io/compliance/complianceld/requirement3) https://api.prismacloud.io/compliance/requirementld/section
C. 1) https://api.prismacloud.io/compliance/add2) https://api.prismacloud.io/compliance/complianceld/requirement3) https://api.prismacloud.io/compliance/requirementld/section
D. 1) https://api.prismacloud.io/compliance2) https://api.prismacloud.io/compliance/requirementld/section3) https://api.prismacloud.io/compliance/complianceld/requirement
Which field is required during the creation of a custom config query?
A. resource status
B. api.name
C. finding.type
D. cloud.type
A customer has a requirement to scan serverless functions for vulnerabilities. What is the correct option to configure scanning?
A. Configure serverless radar from the Defend > Compliance > Cloud Platforms page.
B. Embed serverless Defender into the function.
C. Configure a function scan policy from the Defend > Vulnerabilities > Functions page.
D. Use Lambda layers to deploy a Defender into the function.
What are two key requirements for integrating Okta with Prisma Cloud when multiple Amazon Web Services (AWS) cloud accounts are being used? (Choose two.)
A. Super Administrator permissions
B. A valid subscription for the IAM security module
C. An Okta API token for the primary AWS account
D. Multiple instances of the Okta app
An administrator has been tasked with a requirement by your DevSecOps team to write a script to continuously query programmatically the existing users, and the user’s associated permission levels, in a Prisma Cloud Enterprise tenant. Which public documentation location should be reviewed to help determine the required attributes to carry out this step?
A. Prisma Cloud Administrator’s Guide (Compute)
B. Prisma Cloud API Reference
C. Prisma Cloud Compute API Reference
D. Prisma Cloud Enterprise Administrator’s Guide
What is the behavior of Defenders when the Console is unreachable during upgrades?
A. Defenders continue to alert, but not enforce, using the policies and settings most recently cached before upgrading the Console.
B. Defenders will fail closed until the web-socket can be re-established.
C. Defenders will fail open until the web-socket can be re-established.
D. Defenders continue to alert and enforce using the policies and settings most recently cached before upgrading the Console.
A customer wants to harden its environment from misconfiguration. Prisma Cloud Compute Compliance enforcement for hosts covers which three options? (Choose three.)
A. Docker daemon configuration files
B. Docker daemon configuration
C. Host cloud provider tags
D. Host configuration
E. Hosts without Defender agents
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
A. Alert Center
B. Alarm Center
C. Alarm Advisor
D. Adoption Advisor
A customer wants to scan a serverless function as part of a build process. Which twistcli command can be used to scan serverless functions?
A. twistcli function scan
B. twistcli scan serverless
C. twistcli serverless AWS
D. twiscli serverless scan
An administrator sees that a runtime audit has been generated for a host. The audit message is: `Service postfix attempted to obtain capability SHELL by executing /bin/sh /usr/libexec/postfix/postfix-script.stop. Low severity audit, event is automatically added to the runtime model` Which runtime host policy rule is the root cause for this runtime audit?
A. Custom rule with specific configuration for file integrity
B. Custom rule with specific configuration for networking
C. Default rule that alerts on capabilities
D. Default rule that alerts on suspicious runtime behavior
An administrator wants to retrieve the compliance policies for images scanned in a continuous integration (CI) pipeline. Which endpoint will successfully execute to enable access to the images via API?
A. GET /api/v22.01/policies/compliance
B. GET /api/v22.01/policies/compliance/ci
C. GET /api/v22.01/policies/compliance/ci/images
D. GET /api/v22.01/policies/compliance/ci/serverless
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
A. News bots
B. Search engine crawlers
C. Web scrapers
D. HTTP libraries
Which two of the following are required to be entered on the IdP side when setting up SSO in Prisma Cloud? (Choose two.)
A. Username
B. SSO Certificate
C. Assertion Consumer Service (ACS) URL
D. SP (Service Provider) Entity ID
Which two required request headers interface with Prisma Cloud API? (Choose two.)
A. Content-type:application/json
B. x-redlock-auth
C. >x-redlock-request-id
D. Content-type:application/xml
The development team is building pods to host a web front end, and they want to protect these pods with an application firewall. Which type of policy should be created to protect this pod from Layer7 attacks?
A. The development team should create a WAAS rule for the host where these pods will be running.
B. The development team should create a WAAS rule targeted at all resources on the host.
C. The development team should create a runtime policy with networking protections.
D. The development team should create a WAAS rule targeted at the image name of the pods.
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.)
A. BitBucket
B. Visual Studio Code
C. CircleCI
D. IntelliJ
The compliance team needs to associate Prisma Cloud policies with compliance frameworks. Which option should the team select to perform this task?
A. Custom Compliance
B. Policies
C. Compliance
D. Alert Rules
In Prisma Cloud Software Release 22.06 (Kepler), which Registry type is added?
A. Azure Container Registry
B. Google Artifact Registry
C. IBM Cloud Container Registry
D. Sonatype Nexus
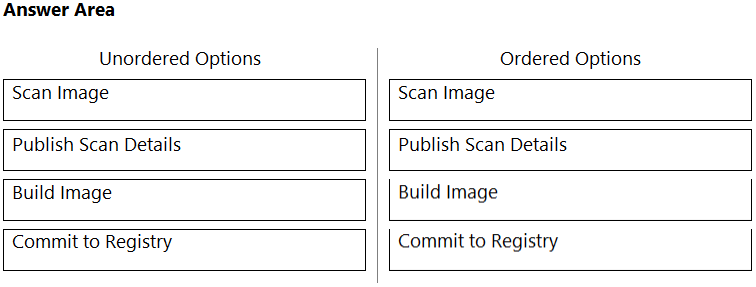
DRAG DROP - What is the order of steps in a Jenkins pipeline scan? (Drag the steps into the correct order of occurrence, from the first step to the last.) Select and Place:
What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
A. Alarm rule
B. Notification rule
C. Alert rule
D. Offline alert
Free Access Full PCCSE Practice Test Free Questions
If you’re looking for more PCCSE practice test free questions, click here to access the full PCCSE practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your PCCSE certification journey!