PCCET Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the PCCET exam? Start with our PCCET Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a PCCET practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free PCCET practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
What is one of the elements of SecOps?
A. Zero Trust model
B. Interfaces
C. Infrastructure
D. Finances
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
A. User-ID
B. Lightweight Directory Access Protocol (LDAP)
C. User and Entity Behavior Analytics (UEBA)
D. Identity and Access Management (IAM)
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
A. Shortest Path
B. Hop Count
C. Split Horizon
D. Path Vector
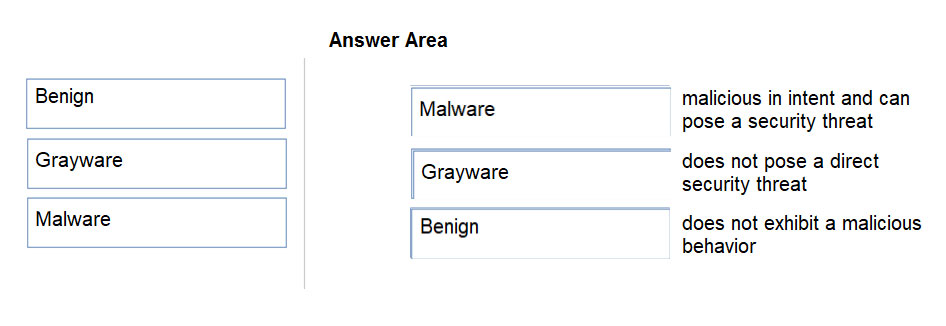
DRAG DROP - Match the Palo Alto Networks WildFire analysis verdict with its definition. Select and Place:
Which three terms are functions of security operations? (Choose three.)
A. Segment
B. Identify
C. Mitigate
D. Investigate
E. Report
On which security principle does virtualization have positive effects?
A. integrity
B. confidentiality
C. availability
D. non-repudiation
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
A. decrypt the infected file using base64
B. alert system administrators
C. quarantine the infected file
D. delete the infected file
E. remove the infected file’s extension
Which analysis detonates previously unknown submissions in a custom-built, evasion-resistant virtual environment to determine real-world effects and behavior?
A. Dynamic
B. Pre-exploit protection
C. Bare-metal
D. Static
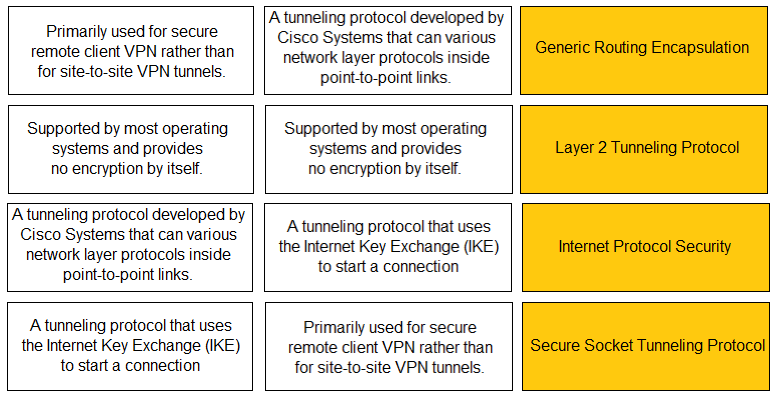
DRAG DROP - Match the description with the VPN technology. Select and Place:
Which of the following is an AWS serverless service?
A. Beta
B. Kappa
C. Delta
D. Lambda
What are three benefits of the cloud native security platform? (Choose three.)
A. Increased throughput
B. Exclusivity
C. Agility
D. Digital transformation
E. Flexibility
Which attacker profile uses the internet to recruit members to an ideology, to train them, and to spread fear and include panic?
A. cybercriminals
B. state-affiliated groups
C. hacktivists
D. cyberterrorists
What is the primary purpose of a case management system?
A. To consolidate alerts into a single queue for streamlined incident handling
B. To incorporate an additional layer in the escalation procedure
C. To be a centralized tool pointing to other, separate alerting systems
D. To minimize the number of duplicate alerts
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
A. XDR
B. STEP
C. SOAR
D. SIEM
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
A. DevSecOps improves pipeline security by assigning the security team as the lead team for continuous deployment
B. DevSecOps ensures the pipeline has horizontal intersections for application code deployment
C. DevSecOps unites the Security team with the Development and Operations teams to integrate security into the CI/CD pipeline
D. DevSecOps does security checking after the application code has been processed through the CI/CD pipeline
Which two network resources does a directory service database contain? (Choose two.)
A. Services
B. /etc/shadow files
C. Users
D. Terminal shell types on endpoints
Before incorporating the DevSecOps process, when was security applied in the software-development lifecycle?
A. In every step of the lifecycle
B. Right in the middle
C. Right at the end, after the development ended
D. Right at the beginning, before the development started
Which tool supercharges security operations center (SOC) efficiency with the world's most comprehensive operating platform for enterprise security?
A. Prisma SAAS
B. WildFire
C. Cortex XDR
D. Cortex XSOAR
What is the proper subnet mask for the network 192.168.55.0/27?
A. 255.255.255.192
B. 255.255.255.248
C. 255.255.255.224
D. 255.255.255.0
From which resource does Palo Alto Networks AutoFocus correlate and gain URL filtering intelligence?
A. Unit 52
B. PAN-DB
C. BrightCloud
D. MineMeld
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
A. NetOps
B. SecOps
C. SecDevOps
D. DevOps
A native hypervisor runs:
A. with extreme demands on network throughput
B. only on certain platforms
C. within an operating system’s environment
D. directly on the host computer’s hardware
Which method is used to exploit vulnerabilities, services, and applications?
A. encryption
B. port scanning
C. DNS tunneling
D. port evasion
What should a security operations engineer do if they are presented with an encoded string during an incident investigation?
A. Save it to a new file and run it in a sandbox.
B. Run it against VirusTotal.
C. Append it to the investigation notes but do not alter it.
D. Decode the string and continue the investigation.
Web 2.0 applications provide which type of service?
A. SaaS
B. FWaaS
C. IaaS
D. PaaS
In an IDS/IPS, which type of alarm occurs when legitimate traffic is improperly identified as malicious traffic?
A. False-positive
B. True-negative
C. False-negative
D. True-positive
What is a common characteristic of serverless and containers?
A. run for prolonged period of time
B. run on specific hosting platforms
C. automate and dynamically scale workloads
D. open source
What does SIEM stand for?
A. Security Infosec and Event Management
B. Security Information and Event Management
C. Standard Installation and Event Media
D. Secure Infrastructure and Event Monitoring
Which key component is used to configure a static route?
A. router ID
B. enable setting
C. routing protocol
D. next hop IP address
With regard to cloud-native security in layers, what is the correct order of the four C's from the top (surface) layer to the bottom (base) layer?
A. container, code, cluster, cloud
B. code, container, cluster, cloud
C. code, container, cloud, cluster
D. container, code, cloud, cluster
What are three benefits of SD-WAN infrastructure? (Choose three.)
A. Improving performance of SaaS applications by requiring all traffic to be back-hauled through the corporate headquarters network
B. Promoting simplicity through the utilization of a centralized management structure
C. Utilizing zero-touch provisioning for automated deployments
D. Leveraging remote site routing technical support by relying on MPLS
E. Improving performance by allowing efficient access to cloud-based resources without requiring back-haul traffic to a centralized location
In a traditional data center what is one result of sequential traffic analysis?
A. simplifies security policy management
B. reduces network latency
C. causes security policies to be complex
D. improves security policy application ID enforcement
Layer 4 of the TCP/IP Model corresponds to which three Layer(s) of the OSI Model? (Choose three.)
A. Transport
B. Presentation
C. Session
D. Application
E. Network
Which pillar of Prisma Cloud application security addresses ensuring that your cloud resources and SaaS applications are correctly configured?
A. visibility, governance, and compliance
B. network protection
C. dynamic computing
D. compute security
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
A. Expedition
B. AutoFocus
C. MineMeld
D. Cortex XDR
What is an example of a Web 3.0 application?
A. Github
B. Bitcoin
C. Pinterest
D. Facebook
Which element of the security operations process is concerned with using external functions to help achieve goals?
A. interfaces
B. business
C. technology
D. people
What is the function of SOAR?
A. It records, monitors, correlates, and analyzes the security events in an IT environment in real time.
B. It helps with the coordination, execution, and automation of tasks between people and tools for faster response to cybersecurity attacks.
C. It collects, integrates, and normalizes your security data to simplify your security operations.
D. It provides prevention, detection, response, and investigation of attacks and threats by gathering and integrating all security data.
What is the primary security focus after consolidating data center hypervisor hosts within trust levels?
A. control and protect inter-host traffic using routers configured to use the Border Gateway Protocol (BGP) dynamic routing protocol
B. control and protect inter-host traffic by exporting all your traffic logs to a sysvol log server using the User Datagram Protocol (UDP)
C. control and protect inter-host traffic by using IPv4 addressing
D. control and protect inter-host traffic using physical network security appliances
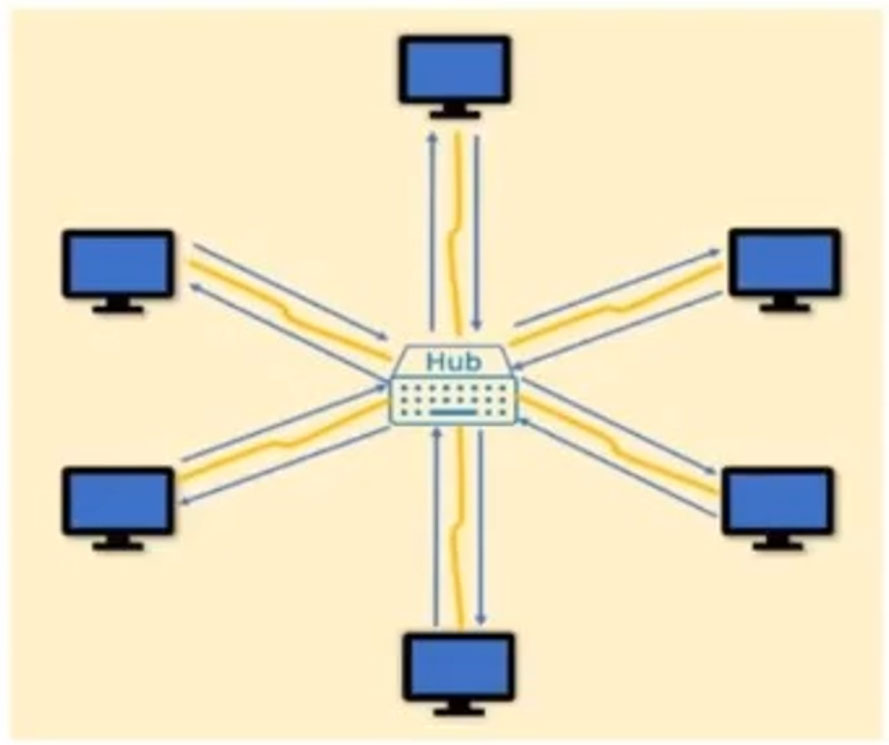
Which type of LAN technology is being displayed in the diagram?
A. Star Topology
B. Spine Leaf Topology
C. Mesh Topology
D. Bus Topology
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account. Which type of attack is this?
A. Whaling
B. Spamming
C. Spear phishing
D. Phishing
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
A. is hardened against cyber attacks
B. runs without any vulnerability issues
C. runs within an operating system
D. allows multiple, virtual (or guest) operating systems to run concurrently on a single physical host computer
What type of DNS record maps an IPV6 address to a domain or subdomain to another hostname?
A. SOA
B. NS
C. AAAA
D. MX
Which type of malware takes advantage of a vulnerability on an endpoint or server?
A. technique
B. patch
C. vulnerability
D. exploit
Which Palo Alto subscription service identifies unknown malware, zero-day exploits, and advanced persistent threats (APTs) through static and dynamic analysis in a scalable, virtual environment?
A. DNS Security
B. URL Filtering
C. WildFire
D. Threat Prevention
What is the definition of a zero-day threat?
A. The amount of time it takes to discover a vulnerability and release a security fix
B. The period between the discovery of a vulnerability and development and release of a patch
C. The day a software vendor becomes aware of an exploit and prevents any further hacking
D. A specific day during which zero threats occurred
What differentiates knowledge-based systems from behavior-based systems?
A. Behavior-based systems find the data that knowledge-based systems store.
B. Knowledge-based systems pull from a previously stored database that distinguishes “bad”.
C. Knowledge-based systems try to find new, distinct traits to find “bad” things.
D. Behavior-based systems pull from a previously stored database that distinguishes “bad”.
Which statement is true about advanced persistent threats?
A. They use script kiddies to carry out their attacks.
B. They have the skills and resources to launch additional attacks.
C. They lack the financial resources to fund their activities.
D. They typically attack only once.
What is a key advantage and key risk in using a public cloud environment?
A. Multi-tenancy
B. Dedicated Networks
C. Dedicated Hosts
D. Multiplexing
What differentiates Docker from a bare metal hypervisor?
A. Docker lets the user boot up one or more instances of an operating system on the same host whereas hypervisors do not
B. Docker uses more resources than a bare metal hypervisor
C. Docker is more efficient at allocating resources for legacy systems
D. Docker uses OS-level virtualization, whereas a bare metal hypervisor runs independently from the OS
Free Access Full PCCET Practice Test Free Questions
If you’re looking for more PCCET practice test free questions, click here to access the full PCCET practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your PCCET certification journey!