MS-101 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the MS-101 exam? Start with our MS-101 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a MS-101 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free MS-101 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
You have a Microsoft 365 tenant. Company policy requires that all Windows 10 devices meet the following minimum requirements: ✑ Require complex passwords. ✑ Require the encryption of data storage devices. Have Microsoft Defender Antivirus real-time protection enabled.You need to prevent devices that do not meet the requirements from accessing resources in the tenant. Which two components should you create? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. a configuration policy
B. a compliance policy
C. a security baseline profile
D. a conditional access policy
E. a configuration profile
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a new Microsoft 365 subscription. You need to prevent users from sending email messages that contain Personally Identifiable Information (PII). Solution: From the Azure portal, you create a Microsoft Azure Information Protection label and an Azure Information Protection policy. Does this meet the goal?
A. Yes
B. No
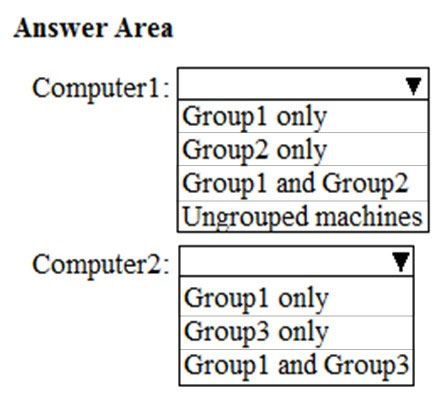
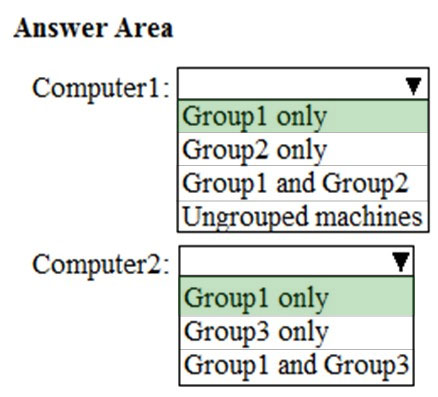
HOTSPOT - Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the device groups shown in the following table.You onboard computers to Microsoft Defender ATP as shown in the following table.
Of which groups are Computer1 and Computer2 members? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
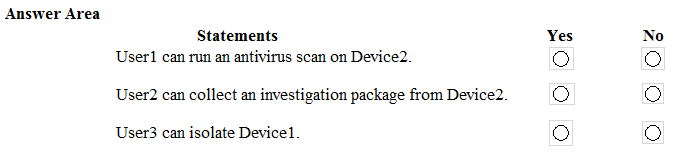
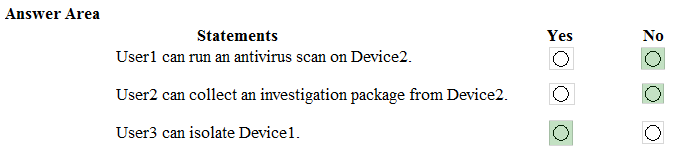
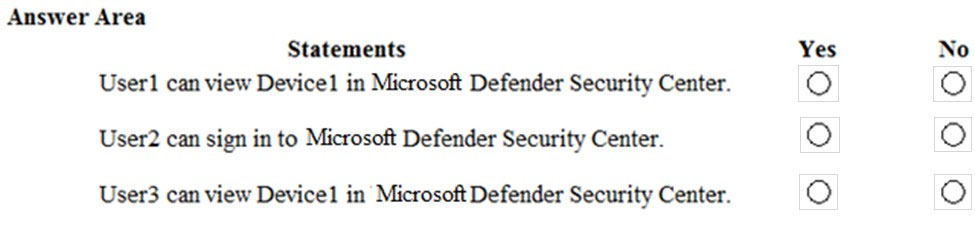
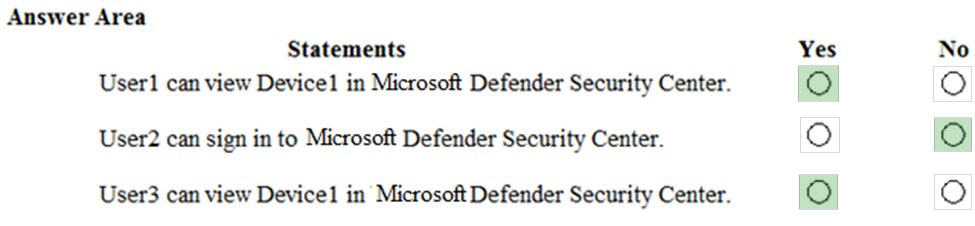
HOTSPOT - You have a Microsoft Azure Activity Directory (Azure AD) tenant that contains the users shown in the following table.Your company uses Microsoft Defender for Endpoint. Microsoft Defender for Endpoint contains the roles shown in the following table.
Microsoft Defender for Endpoint contains the device groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You need to meet the technical requirement for the SharePoint administrator. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
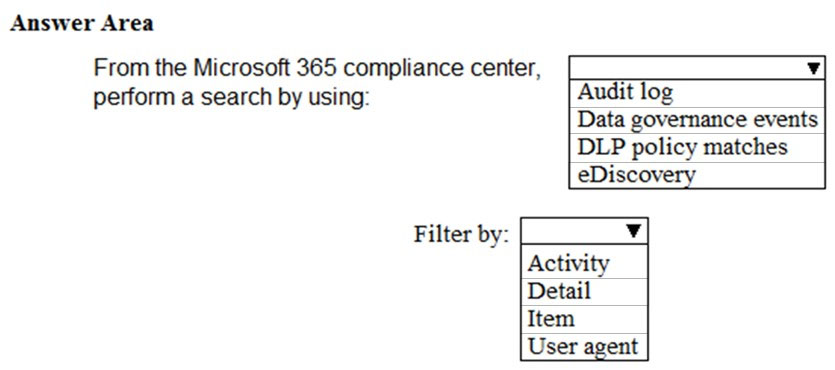
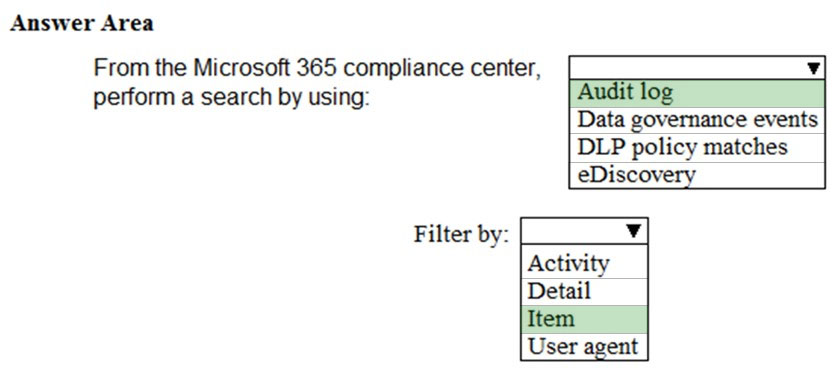
You have a new Microsoft 365 E5 subscription. You plan to use Activity explorer to monitor data loss prevention (DLP) rule activity. You need to ensure that Activity explorer contains data for analysis. What should you do first?
A. Add a new alert policy.
B. Turn on auditing.
C. Create a sensitivity label.
D. Create a new content search.
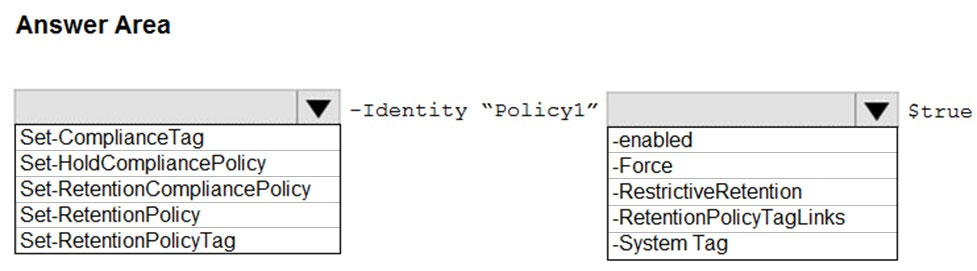
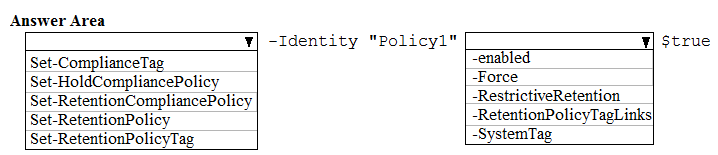
HOTSPOT - From the Security & Compliance admin center, you create a retention policy named Policy1. You need to prevent all users from disabling the policy or reducing the retention period. How should you configure the Azure PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
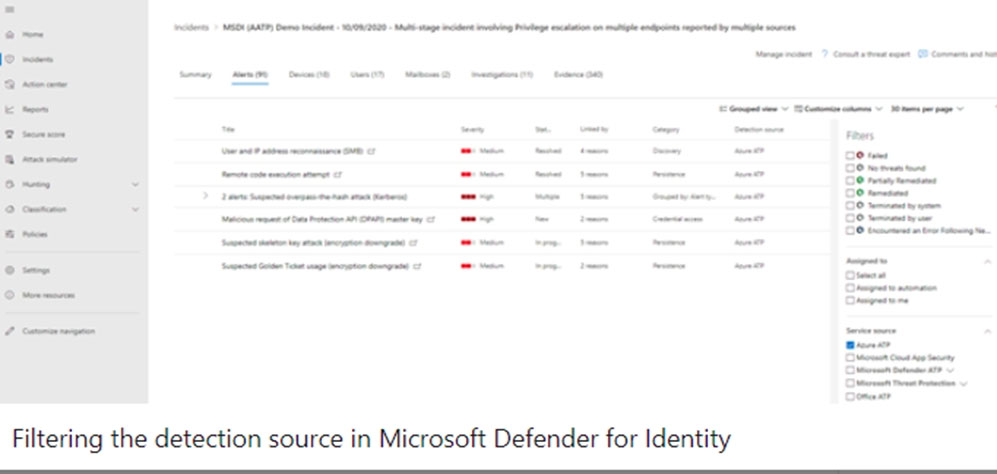
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
A. Microsoft Sentinel
B. Azure Web Application Firewall
C. Microsoft Defender for Identity
D. Azure Arc
You have a Microsoft 365 tenant that contains devices registered for mobile device management. The devices are configured as shown in the following table.You plan to enable VPN access for the devices. What is the minimum number of configuration policies required?
A. 1
B. 3
C. 4
D. 5
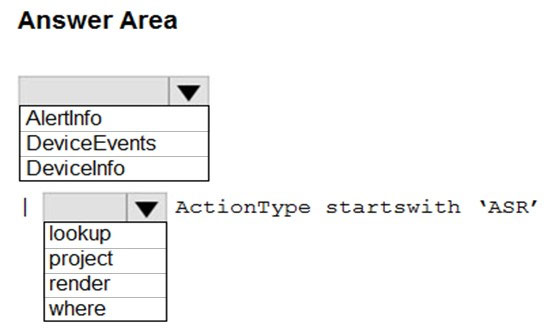
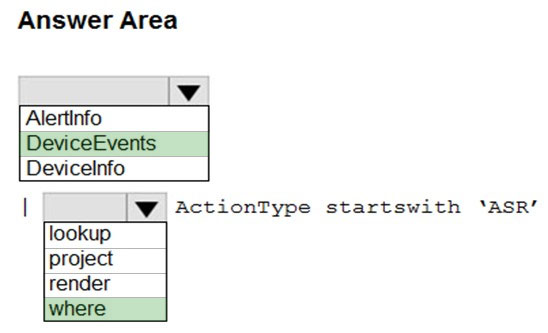
HOTSPOT - You have a Microsoft 365 E5 tenant that contains 100 Windows 10 devices. You plan to attack surface reduction (ASR) rules for the Windows 10 devices. You configure the ASR rules in audit mode and collect audit data in a Log Analytics workspace. You need to find the ASR rules that match the activities on the devices. How should you complete the Kusto query? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E5 tenant that uses Microsoft Endpoint Manager. You have Windows 10 devices enrolled in Microsoft Endpoint Manager. You need to perform the following actions on the devices: • Configure Windows Hello for Business. • Deploy a root certification authority (CA) certificate. Which type of Microsoft Endpoint Manager configuration profile should you use for each action? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
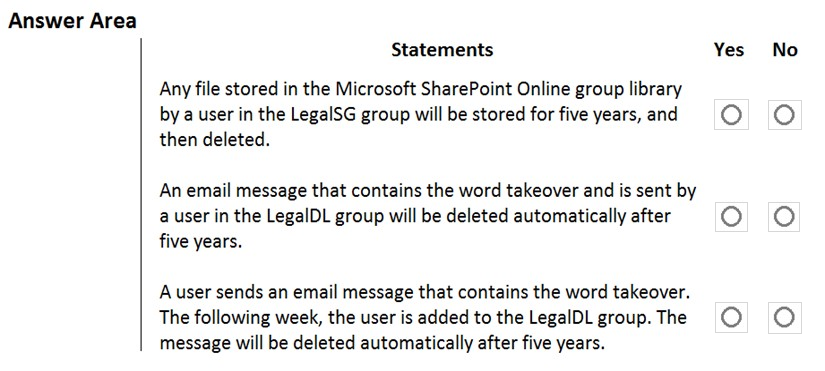
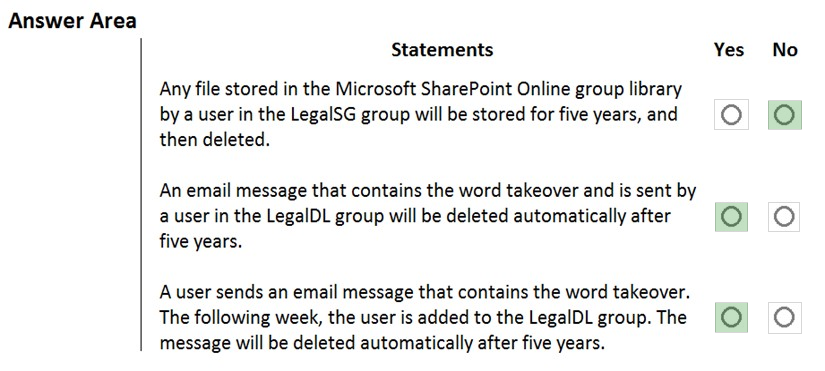
HOTSPOT - You have a Microsoft 365 subscription that contains all the user data. You plan to create the retention policy shown in the Choose Locations exhibit. (Click the Choose Locations tab.)You configure the Advanced retention settings as shown in the Retention exhibit. (Click the Retention tab.)
The locations specified in the policy include the groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
You have an Azure AD tenant. You have 1,000 computers that run Windows 10 Pro and are joined to Azure AD. You purchase a Microsoft 365 E3 subscription. You need to deploy Windows 10 Enterprise to the computers. The solution must minimize administrative effort. What should you do?
A. From the Microsoft Endpoint Manager admin center, create a Windows Autopilot deployment profile. Assign the profile to all the computers. Instruct users to restart their computer and perform a network restart.
B. Enroll the computers in Microsoft Intune. Create a configuration profile by using the Edition upgrade and mode switch template. From the Microsoft Endpoint Manager admin center, assign the profile to all the computers and instruct users to restart their computer.
C. From Windows Configuration Designer, create a provisioning package that has an EditionUpgrade configuration and upload the package to a Microsoft SharePoint Online site. Instruct users to run the provisioning package from SharePoint Online.
D. From the Azure Active Directory admin center, create a security group that has dynamic device membership. Assign licenses to the group and instruct users to sign in to their computer.
HOTSPOT - You have a Microsoft Azure Activity Directory (Azure AD) tenant contains the users shown in the following table.Group3 is a member of Group1. Your company uses Microsoft Defender Advanced Threat Protection (ATP). Microsoft Defender ATP contains the roles shown in the following table.
Microsoft Defender ATP contains the device groups shown in the following table.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point. Hot Area:
Your company has a Microsoft 365 E5 subscription. Users in the research department work with sensitive data. You need to prevent the research department users from accessing potentially unsafe websites by using hyperlinks embedded in email messages and documents. Users in other departments must not be restricted. What should you do?
A. Create a data loss prevention (DLP) policy that has a Content is shared condition.
B. Create a new safe links policy.
C. Create a data loss prevention (DLP) policy that has a Content contains condition.
You have a Microsoft 365 E5 tenant that contains two groups named Group1 and Group2. You need to prevent the members of Group1 from communicating with the members of Group2 by using Microsoft Teams. The solution must comply with regulatory requirements and must not affect other users in the tenant. What should you use?
A. administrative units in Azure Active Directory (Azure AD)
B. information barriers
C. moderated distribution groups
D. communication compliance policies
You have a Microsoft 365 subscription. You need to grant a user named User1 access to download compliance reports from the Microsoft 365 Defender portal. The solution must use the principle of least privilege. What should you do?
A. Add User1 to the Service Assurance User role group.
B. Create a new role group that has the Preview role and add User1 to the role group.
C. Add User1 to the Compliance Administrator role group.
D. Add User1 to the Security Reader role group.
You need to configure Office on the web to meet the technical requirements. What should you do?
A. Assign the Global reader role to User1.
B. Enable sensitivity labels for Office files in SharePoint Online and OneDrive.
C. Configure an auto-labeling policy to apply the sensitivity labels.
D. Assign the Office apps admin role to User1.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. Your network contains an on-premises Active Directory domain. The domain contains 2,000 computers that run Windows 8.1 and have applications installed as shown in the following table.You enroll all the computers in Upgrade Readiness. You need to ensure that App1 and App2 have an UpgradeDecision status of Ready to upgrade. Solution: You set the Importance status of App1 to Business critical. Does this meet the goal?
A. Yes
B. No
HOTSPOT - You have a Microsoft 365 E5 tenant. You create a data loss prevention (DLP) policy to prevent users from using Microsoft Teams to share internal documents with external users. To which two locations should you apply the policy? To answer, select the appropriate locations in the answer area. NOTE: Each correct selection is worth one point.
HOTSPOT - You have a Microsoft 365 E5 subscription that contains a Microsoft SharePoint Online site named Site1 and a data loss prevention (DLP) policy named DLP1. DLP1 contains the rules shown in the following table.Site1 contains the files shown in the following table.
Which policy tips are shown for each file? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
You have the sensitivity labels shown in the following exhibit.Which labels can users apply to content?
A. Label3, Label4, and Label6 only
B. Label1, Label2, Label3, Label4, Label5, and Label6
C. Label1, Label2, and Label5 only
D. Label1, Label3, Label4, and Label6 only
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen. You have a computer that runs Windows 10. You need to verify which version of Windows 10 is installed. Solution: From Device Manager, you view the computer properties. Does this meet the goal?
A. Yes
B. No
You need to recommend a solution for the security administrator. The solution must meet the technical requirements. What should you include in the recommendation?
A. Microsoft Azure Active Directory (Azure AD) Privileged Identity Management
B. Microsoft Azure Active Directory (Azure AD) Identity Protection
C. Microsoft Azure Active Directory (Azure AD) conditional access policies
D. Microsoft Azure Active Directory (Azure AD) authentication methods
You have a Microsoft SharePoint Online site named Site1. On March 1, you delete a document named Document1.docx from Site1. On April 1, you empty the Recycle Bin of Site1. You need to identify the latest date a user who has the SharePoint admin role can recover Document1.docx. Which date should you identify?
A. April 1
B. May 1
C. June 1
D. September 1
E. December 1
Your company has a Microsoft Azure Active Directory (Azure AD) tenant named contoso.com. You sign for Microsoft Store for Business. The tenant contains the users shown in the following table.Microsoft Store for Business has the following Shopping behavior settings: ✑ Allow users to shop is set to On ✑ Make everyone a Basic Purchaser is set to Off You need to identify which users can install apps from the Microsoft for Business private store. Which users should you identify?
A. User3 only
B. User1 only
C. User1 and User2 only
D. User3 and User4 only
You have a Microsoft 365 tenant. You plan to manage incidents in the tenant by using the Microsoft 365 Defender. Which Microsoft service source will appear on the Incidents page of the Microsoft 365 Defender portal?
A. Azure Information Protection
B. Microsoft Defender for Cloud
C. Microsoft Defender for Identity
D. Microsoft Sentinel
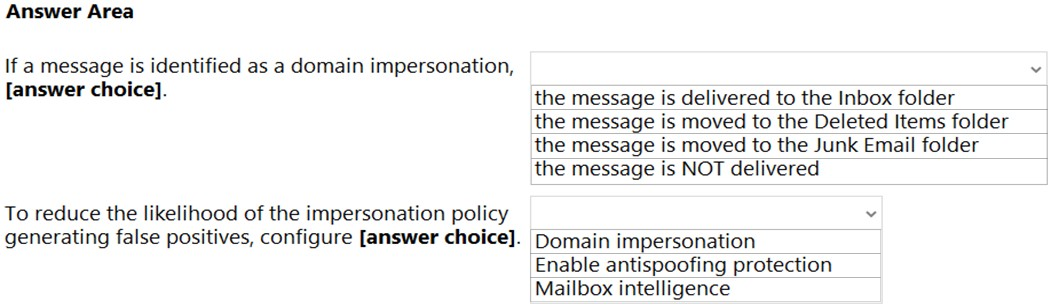
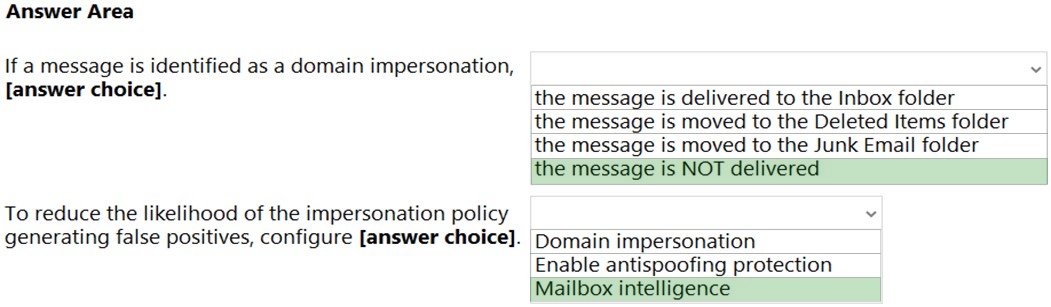
HOTSPOT - You configure an anti-phishing policy as shown in the following exhibit.Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the graphic. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 tenant that contains the devices shown in the following table.You plan to implement attack surface reduction (ASR) rules. Which devices will support the ASR rules?
A. Device1, Device2, Device3, and Device4
B. Device1, Device2, and Device3 only
C. Device2 and Device3 only
D. Device3 only
You need to meet the technical requirement for the EU PII data. What should you create?
A. a data loss prevention (DLP) policy from the Microsoft 365 compliance center
B. a data loss prevention (DLP) policy from the Exchange admin center
C. a retention policy from the Exchange admin center
D. a retention policy from the Microsoft 365 compliance center
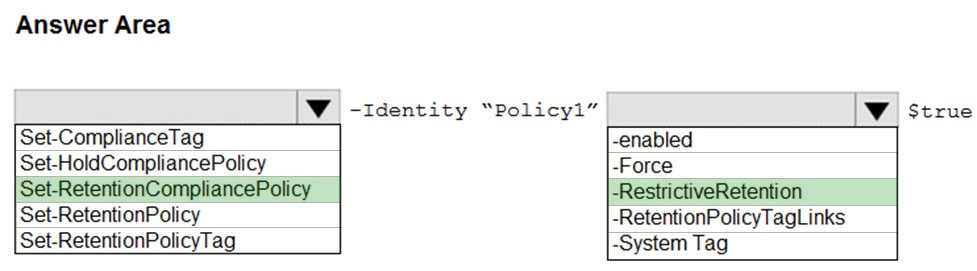
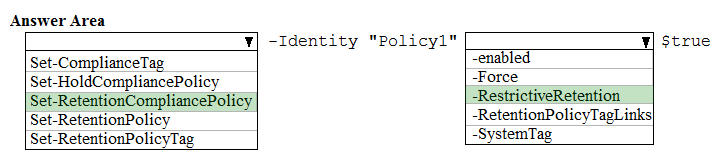
HOTSPOT - From the Microsoft 365 compliance center, you create a retention policy named Policy1. You need to prevent all users from disabling the policy or reducing the retention period. How should you configure the Azure PowerShell command? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
You have a Microsoft 365 E5 tenant. You need to be notified when emails with attachments that contain sensitive personal data are sent to external recipients. Which two policies can you use? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
A. a data loss prevention (DLP) policy
B. a sensitivity label policy
C. a Microsoft Defender for Cloud Apps file policy
D. a communication compliance policy
E. a retention label policy
You have a Microsoft 365 subscription. All users have their email stored in Microsoft Exchange Online. In the mailbox of a user named User1, you need to preserve a copy of all the email messages that contain the word ProjectX. What should you do?
A. From the Microsoft Purview compliance portal, create a data loss prevention (DLP) policy.
B. From the Microsoft Purview compliance portal, create a label and a label policy.
C. From the Microsoft 365 Defender, start a message trace.
D. From the Exchange admin center, create a mail flow rule.
You have computers that run Windows 10 Enterprise and are joined to the domain. You plan to delay the installation of new Windows builds so that the IT department can test application compatibility. You need to prevent Windows from being updated for the next 30 days. Which two Group Policy settings should you configure? Each correct answer presents part of the solution. NOTE: Each correct selection is worth one point.
A. Select when Quality Updates are received
B. Select when Preview Builds and Feature Updates are received
C. Turn off auto-restart for updates during active hours
D. Manage preview builds
E. Automatic updates detection frequency
You have a Microsoft 365 E5 tenant. You plan to create a custom Compliance Manager assessment template based on the ISO 27001:2013 template. You need to export the existing template. Which file format should you use for the exported template?
A. CSV
B. XLSX
C. JSON
D. XML
You have a Microsoft 365 E5 subscription that uses Microsoft Defender for Endpoint. From Microsoft Defender for Endpoint, you turn on the Allow or block file advanced feature. You need to block users from downloading a file named File1.exe. What should you use?
A. a suppression rule
B. an indicator
C. a device configuration profile
You have a Microsoft 365 tenant. You plan to enable BitLocker Disk Encryption (BitLocker) automatically for all Windows 10 devices that enroll in Microsoft Intune. What should you use?
A. an attack surface reduction (ASR) policy
B. an app configuration policy
C. a device compliance policy
D. a device configuration profile
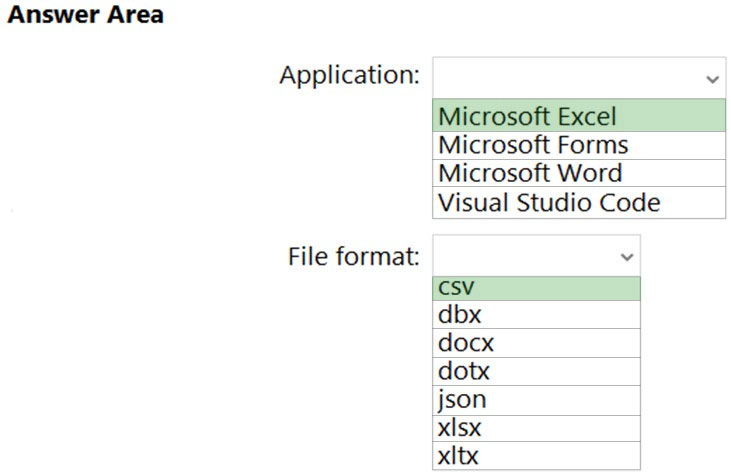
HOTSPOT - You have a Microsoft 365 tenant. You need to create a custom Compliance Manager assessment template. Which application should you use to create the template, and in which file format should the template be saved? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
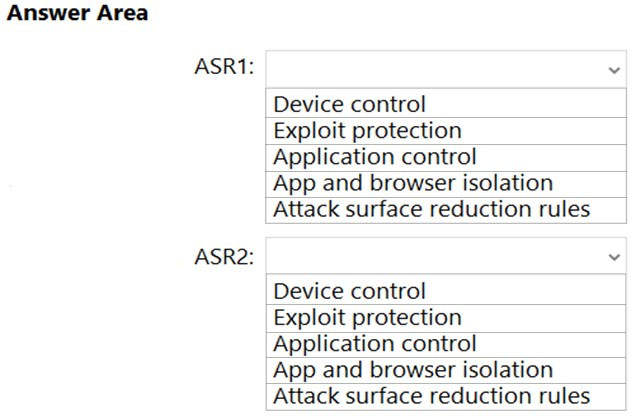
HOTSPOT - You have a Microsoft 365 tenant that contains 100 Windows 10 devices. The devices are managed by using Microsoft Endpoint Manager. You plan to create two attack surface reduction (ASR) policies named ASR1 and ASR2. ASR1 will be used to configure Microsoft Defender Application Guard. ASR2 will be used to configure Microsoft Defender SmartScreen. Which ASR profile type should you use for each policy? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Your network contains an on-premises Active Directory domain named contoso.com. The domain contains 1,000 Windows 10 devices. You perform a proof of concept (PoC) deployment of Microsoft Defender for Endpoint for 10 test devices. During the onboarding process, you configure Microsoft Defender for Endpoint-related data to be stored in the United States. You plan to onboard all the devices to Microsoft Defender for Endpoint. You need to store the Microsoft Defender for Endpoint data in Europe. What should you do first?
A. Create a workspace.
B. Onboard a new device.
C. Delete the workspace.
D. Offboard the test devices.
You have a Microsoft 365 E5 subscription. You plan to implement Microsoft 365 compliance policies to meet the following requirements: ✑ Identify documents that are stored in Microsoft Teams and SharePoint Online that contain Personally Identifiable Information (PII). ✑ Report on shared documents that contain PII. What should you create?
A. an alert policy
B. a data loss prevention (DLP) policy
C. a retention policy
D. a Microsoft Defender for Cloud Apps policy
You have a Microsoft 365 E5 subscription. You need to identify which users accessed Microsoft Office 365 from anonymous IP addresses during the last seven days. What should you do?
A. From the Defender for Cloud Apps admin center, select Users and accounts.
B. From the Microsoft 365 Defender, view the Threat tracker.
C. From the Microsoft 365 admin center, view the Security & compliance report.
D. From the Azure Active Directory admin center, view the Risky sign-ins report.
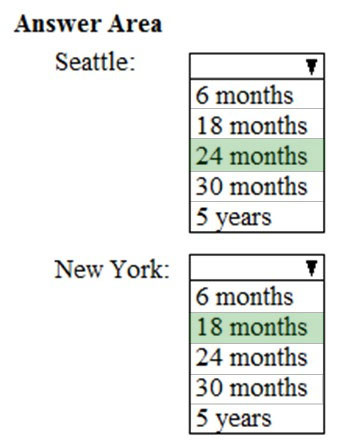
HOTSPOT - As of March, how long will the computers in each office remain supported by Microsoft? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
HOTSPOT - You have a Microsoft 365 E3 subscription. You plan to launch Attack simulation training for all users. Which social engineering technique and training experience will be available? To answer, select the appropriate option. NOTE: Each correct selection is worth one point.
Your company has a Microsoft 365 subscription that uses an Azure Active Directory (Azure AD) tenant named contoso.com. A user named User1 is a member of a dynamic group named Group1. User1 reports that he cannot access documents shared to Group1. You discover that User1 is no longer a member of Group1. You suspect that an administrator made a change that caused User1 to be removed from Group1. You need to identify which administrator made the change. Which audit log activity should you search in the Security & Compliance admin center?
A. Azure AD group administration activities ג€” Removed member from group
B. User administration activities ג€” Updated user
C. Azure AD group administration activities ג€” Updated group
You have two conditional access policies named Policy1 and Policy2. Policy1 has the following settings: ✑ Assignments: - Users and groups: User1 - Cloud apps or actions: Office 365 Exchange Online - Conditions: 0 conditions selected ✑ Access controls: - Grant: Grant access - Session: 0 controls selected ✑ Enable policy: On Policy2 has the following settings: ✑ Assignments: - Users and groups: User1 - Cloud apps or actions: Office 365 Exchange Online - Conditions: 0 conditions selected ✑ Access controls: - Grant: Block access - Session: 0 controls selected ✑ Enable policy: On You need to ensure that User1 can access Microsoft Exchange Online only from devices that are marked as compliant. What should you do?
A. Modify the Grant settings of Policy2.
B. Disable Policy2.
C. Modify the Conditions settings of Policy2.
D. Modify the Grant settings of Policy1.
You plan to use Microsoft Sentinel and Microsoft Defender for Cloud Apps. You need to connect Microsoft Defender for Cloud Apps to Microsoft Sentinel. What should you do in the Microsoft Defender for Cloud Apps portal?
A. From Automatic log upload, add a data source.
B. From Automatic log upload, add a log collector.
C. From Connected apps, add an app connector.
D. From Security extensions, add a SIEM agent.
You have a Microsoft 365 subscription. From the Microsoft 365 compliance center, you create a content search of all the mailboxes that contain the word ProjectX. You need to export the results of the content search. What do you need to download the report?
A. a certification authority (CA) certificate
B. an export key
C. a password
D. a user certificate
HOTSPOT - You have a Microsoft 365 E5 subscription that uses device management in Microsoft Endpoint Manager. You purchase five new Android devices and five new macOS devices. You need to enroll the new devices in Microsoft Intune. What should you use to enroll each device type? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point.
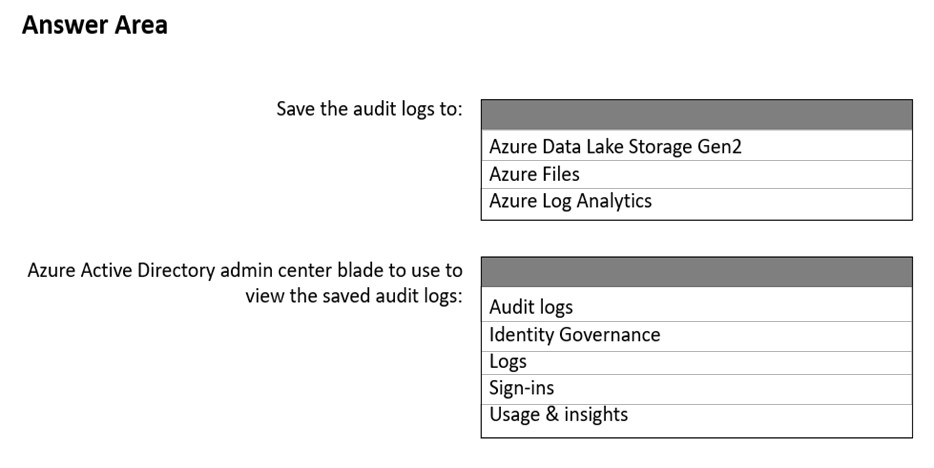
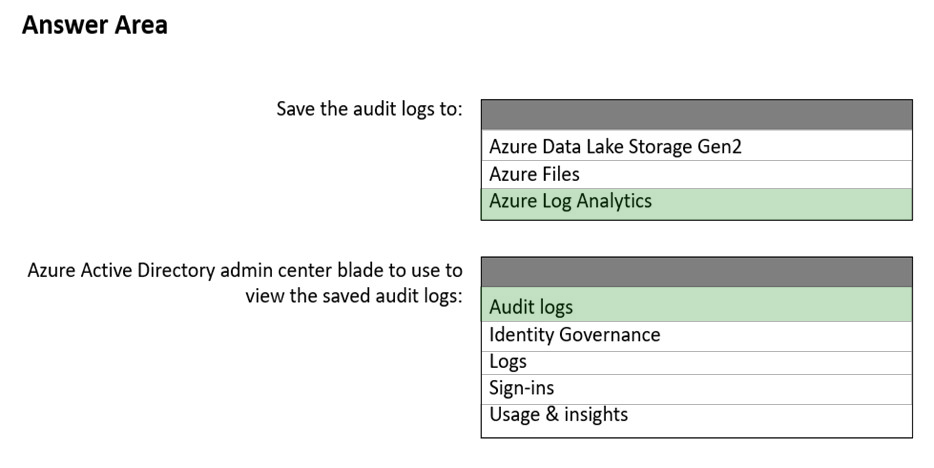
HOTSPOT - You have a Microsoft 365 tenant. You need to retain Azure Active Directory (Azure AD) audit logs for two years. Administrators must be able to query the audit log information by using the Azure Active Directory admin center. What should you do? To answer, select the appropriate options in the answer area. NOTE: Each correct selection is worth one point. Hot Area:
Free Access Full MS-101 Practice Test Free Questions
If you’re looking for more MS-101 practice test free questions, click here to access the full MS-101 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your MS-101 certification journey!