CS0-001 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the CS0-001 exam? Start with our CS0-001 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a CS0-001 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free CS0-001 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
An organization is requesting the development of a disaster recovery plan. The organization has grown and so has its infrastructure. Documentation, policies, and procedures do not exist. Which of the following steps should be taken to assist in the development of the disaster recovery plan?A. Conduct a risk assessment.
B. Develop a data retention policy.
C. Execute vulnerability scanning.
D. Identify assets.
During an investigation, a computer is being seized. Which of the following is the FIRST step the analyst should take?A. Power off the computer and remove it from the network.
B. Unplug the network cable and take screenshots of the desktop.
C. Perform a physical hard disk image.
D. Initiate chain-of-custody documentation.
Ransomware is identified on a company's network that affects both Windows and MAC hosts. The command and control channel for encryption for this variant uses TCP ports from 11000 to 65000. The channel goes to good1. Iholdbadkeys.com, which resolves to IP address 72.172.16.2.
Which of the following is the MOST effective way to prevent any newly infected systems from actually encrypting the data on connected network drives while causing the least disruption to normal Internet traffic?A. Block all outbound traffic to web host good1 iholdbadkeys.com at the border gateway.
B. Block all outbound TCP connections to IP host address 172.172.16.2 at the border gateway.
C. Block all outbound traffic on TCP ports 11000 to 65000 at the border gateway.
D. Block all outbound traffic on TCP ports 11000 to 65000 to IP host address 172.172.16.2 at the border gateway.
A threat intelligence feed has posted an alert stating there is a critical vulnerability in the kernel. Unfortunately, the company's asset inventory is not current. Which of the following techniques would a cybersecurity analyst perform to find all affected servers within an organization?A. A manual log review from data sent to syslog
B. An OS fingerprinting scan across all hosts
C. A packet capture of data traversing the server network
D. A service discovery scan on the network
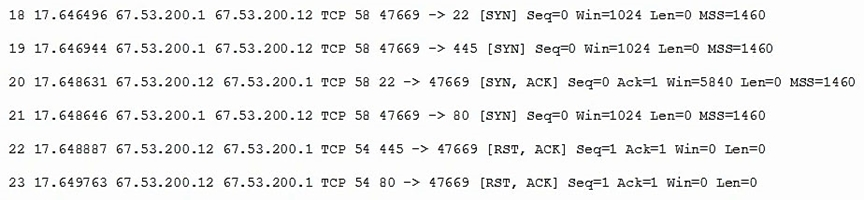
A system administrator is doing network reconnaissance of a company's external network to determine the vulnerability of various services that are running.
Sending some sample traffic to the external host, the administrator obtains the following packet capture:
Based on the output, which of the following services should be further tested for vulnerabilities?A. SSH
B. HTTP
C. SMB
D. HTTPS
Ann, a user, reports to the security team that her browser began redirecting her to random sites while using her Windows laptop. Ann further reports that the OS shows the C: drive is out of space despite having plenty of space recently. Ann claims she not downloaded anything. The security team obtains the laptop and begins to investigate, noting the following:
✑ File access auditing is turned off.
When clearing up disk space to make the laptop functional, files that appear to be cached web pages are immediately created in a temporary directory, filling
up the available drive space.
✑ All processes running appear to be legitimate processes for this user and machine.
✑ Network traffic spikes when the space is cleared on the laptop.
✑ No browser is open.
Which of the following initial actions and tools would provide the BEST approach to determining what is happening?A. Delete the temporary files, run an Nmap scan, and utilize Burp Suite.
B. Disable the network connection, check Sysinternals Process Explorer, and review netstat output.
C. Perform a hard power down of the laptop, take a dd image, and analyze with FTK.
D. Review logins to the laptop, search Windows Event Viewer, and review Wireshark captures.
A company is developing its first mobile application, which will be distributed via the official application stores of the two major mobile platforms.
Which of the following is a prerequisite to making the applications available in the application stores?A. Distribute user certificates.
B. Deploy machine/computer certificates.
C. Obtain a code-signing certificate.
D. Implement a CRL.
A medical organization recently started accepting payments over the phone. The manager is concerned about the impact of the storage of different types of data.
Which of the following types of data incurs the highest regulatory constraints?A. PHI
B. PCI
C. PII
D. IP
Which of the following describes why it is important for an organization's incident response team and legal department to meet and discuss communication processes during the incident response process?A. To comply with existing organization policies and procedures on interacting with internal and external parties
B. To ensure all parties know their roles and effective lines of communication are established
C. To identify which group will communicate details to law enforcement in the event of a security incident
D. To predetermine what details should or should not be shared with internal or external parties in the event of an incident
A security analyst is conducting traffic analysis and observes an HTTP POST to the company's main web server. The POST header is approximately 1000 bytes in length. During transmission, one byte is delivered every ten seconds. Which of the following attacks is the traffic indicative of?A. Exfiltration
B. DoS
C. Buffer overflow
D. SQL injection
A user received an invalid password response when trying to change the password. Which of the following policies could explain why the password is invalid?A. Access control policy
B. Account management policy
C. Password policy
D. Data ownership policy
Which of the following utilities could be used to resolve an IP address to a domain name, assuming the address has a PTR record?A. ifconfig
B. ping
C. arp
D. nbtstat
Company A permits visiting business partners from Company B to utilize Ethernet ports available in Company A's conference rooms. This access is provided to allow partners the ability to establish VPNs back to Company B's network. The security architect for Company A wants to ensure partners from Company B are able to gain direct Internet access from available ports only, while Company A employees can gain access to the Company A internal network from those same ports. Which of the following can be employed to allow this?A. ACL
B. SIEM
C. MAC
D. NAC
E. SAML
An analyst is preparing for a technical security compliance check on all Apache servers. Which of the following will be the BEST to use?A. CIS benchmark
B. Nagios
C. OWASP
D. Untidy
E. Cain & Abel
A cybersecurity analyst is investigating an incident report concerning a specific user workstation. The workstation is exhibiting high CPU and memory usage, even when first started, and network bandwidth usage is extremely high. The user reports that applications crash frequently, despite the fact that no significant changes in work habits have occurred. An antivirus scan reports no known threats. Which of the following is the MOST likely reason for this?A. Advanced persistent threat
B. Zero day
C. Trojan
D. Logic bomb
A logistics company's vulnerability scan identifies the following vulnerabilities on Internet-facing devices in the DMZ:
✑ SQL injection on an infrequently used web server that provides files to vendors
✑ SSL/TLS not used for a website that contains promotional information
The scan also shows the following vulnerabilities on internal resources:
✑ Microsoft Office Remote Code Execution on test server for a human resources system
✑ TLS downgrade vulnerability on a server in a development network
In order of risk, which of the following should be patched FIRST?A. Microsoft Office Remote Code Execution
B. SQL injection
C. SSL/TLS not used
D. TLS downgrade
Due to new regulations, a company has decided to institute an organizational vulnerability management program and assign the function to the security team.
Which of the following frameworks would BEST support the program? (Choose two.)A. COBIT
B. NIST
C. ISO 27000 series
D. ITIL
E. OWASP
A security analyst is assisting in the redesign of a network to make it more secure. The solution should be low cost, and access to the secure segments should be easily monitored, secured, and controlled. Which of the following should be implemented?A. System isolation
B. Honeyport
C. Jump box
D. Mandatory access control
An analyst is reviewing a list of vulnerabilities, which were reported from a recent vulnerability scan of a Linux server.
Which of the following is MOST likely to be a false positive?A. OpenSSH/OpenSSL Package Random Number Generator Weakness
B. Apache HTTP Server Byte Range DoS
C. GDI+ Remote Code Execution Vulnerability (MS08-052)
D. HTTP TRACE / TRACK Methods Allowed (002-1208)
E. SSL Certificate Expiry
While preparing for a third-party audit, the vice president of risk management and the vice president of information technology have stipulated that the vendor may not use offensive software during the audit. This is an example of:A. organizational control.
B. service-level agreement.
C. rules of engagement.
D. risk appetite
During a routine network scan, a security administrator discovered an unidentified service running on a new embedded and unmanaged HVAC controller, which is used to monitor the company's datacenter:
The enterprise monitoring service requires SNMP and SNMPTRAP connectivity to operate. Which of the following should the security administrator implement to harden the system?A. Patch and restart the unknown service.
B. Segment and firewall the controller's network.
C. Disable the unidentified service on the controller.
D. Implement SNMPv3 to secure communication.
E. Disable TCP/UDP ports 161 through 163.
As part of an upcoming engagement for a client, an analyst is configuring a penetration testing application to ensure the scan complies with information defined in the SOW. Which of the following types of information should be considered based on information traditionally found in the SOW? (Choose two.)A. Timing of the scan
B. Contents of the executive summary report
C. Excluded hosts
D. Maintenance windows
E. IPS configuration
F. Incident response policies
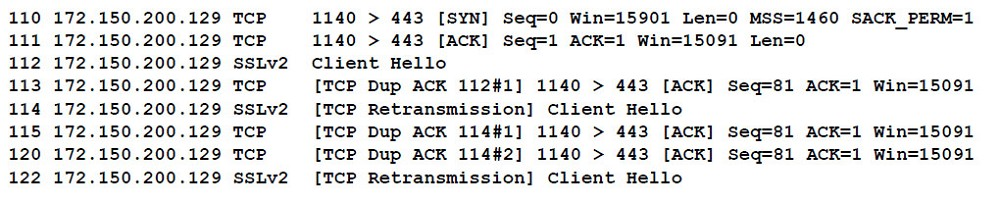
When reviewing network traffic, a security analyst detects suspicious activity:
Based on the log above, which of the following vulnerability attacks is occurring?A. ShellShock
B. DROWN
C. Zeus
D. Heartbleed
E. POODLE
A hacker issued a command and received the following response:
Which of the following describes what the hacker is attempting?A. Penetrating the system
B. Performing a zombie scan
C. OS fingerprinting
D. Topology discovery
File integrity monitoring states the following files have been changed without a written request or approved change. The following change has been made: chmod 777 ""Rv /usr
Which of the following may be occurring?A. The ownership pf /usr has been changed to the current user.
B. Administrative functions have been locked from users.
C. Administrative commands have been made world readable/writable.
D. The ownership of/usr has been changed to the root user.
A technician receives a report that a user's workstation is experiencing no network connectivity. The technician investigates and notices the patch cable running the back of the user's VoIP phone is routed directly under the rolling chair and has been smashed flat over time.
Which of the following is the most likely cause of this issue?A. Cross-talk
B. Electromagnetic interference
C. Excessive collisions
D. Split pairs
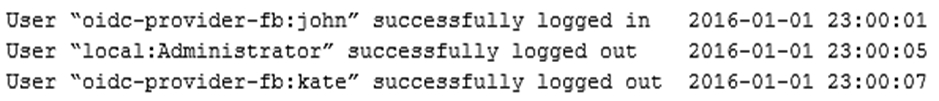
An application contains the following log entries in a file named "authlog.log":
A security analyst has been asked to parse the log file and print out all valid usernames. Which of the following achieves this task?A. grep ""e "successfully" authlog.log | awk "˜{print $2}' | sed s/'//g
B. cat authlog.log | grep "2016-01-01" | echo "valid username found: $2"
C. echo authlog.log > sed "˜s/User//' | print "username exists: $User"
D. cat "authlog.log" | grep "User" | cut ""F' "˜ | echo "username exists: $1"
A security analyst at a small regional bank has received an alert that nation states are attempting to infiltrate financial institutions via phishing campaigns. Which of the following techniques should the analyst recommend as a proactive measure to defend against this type of threat?A. Honeypot
B. Location-based NAC
C. System isolation
D. Mandatory access control
E. Bastion host
During a routine review of firewall logs, an analyst identified that an IP address from the organization's server subnet had been connecting during nighttime hours to a foreign IP address, and had been sending between 150 and 500 megabytes of data each time. This had been going on for approximately one week, and the affected server was taken offline for forensic review. Which of the following is MOST likely to drive up the incident's impact assessment?A. PII of company employees and customers was exfiltrated.
B. Raw financial information about the company was accessed.
C. Forensic review of the server required fall-back on a less efficient service.
D. IP addresses and other network-related configurations were exfiltrated.
E. The local root password for the affected server was compromised.
A company requests a security assessment of its network. Permission is given, but no details are provided. It is discovered that the company has a web presence, and the company's IP address is 70.182.11.4. Which of the following Nmap commands would reveal common open ports and their versions?A. nmap - oV
B. nmap -vO
C. nmap -sv
In comparison to non-industrial IT vendors, ICS equipment vendors generally:A. rely less on proprietary code in their hardware products.
B. have more mature software development models.
C. release software updates less frequently.
D. provide more expensive vulnerability reporting.
The help desk has reported that users are reusing previous passwords when prompted to change them. Which of the following would be the MOST appropriate control for the security analyst to configure to prevent password reuse? (Choose two.)A. Implement mandatory access control on all workstations.
B. Implement role-based access control within directory services.
C. Deploy Group Policy Objects to domain resources.
D. Implement scripts to automate the configuration of PAM on Linux hosts.
E. Deploy a single-sing-on solution for both Windows and Linux hosts.
Alerts have been received from the SIEM, indicating infections on multiple computers. Based on threat characteristics, these files were quarantined by the host- based antivirus program. At the same time, additional alerts in the SIEM show multiple blocked URLs from the address of the infected computers; the URLs were classified as uncategorized. The domain location of the IP address of the URLs that were blocked is checked, and it is registered to an ISP in Russia. Which of the following steps should be taken NEXT?A. Remove those computers from the network and replace the hard drives. Send the infected hard drives out for investigation.
B. Run a full antivirus scan on all computers and use Splunk to search for any suspicious activity that happened just before the alerts were received in the SIEM.
C. Run a vulnerability scan and patch discovered vulnerabilities on the next pathing cycle. Have the users restart their computers. Create a use case in the SIEM to monitor failed logins on the infected computers.
D. Install a computer with the same settings as the infected computers in the DMZ to use as a honeypot. Permit the URLs classified as uncategorized to and from that host.
An administrator has been investigating the way in which an actor had been exfiltrating confidential data from a web server to a foreign host. After a thorough forensic review, the administrator determined the server's BIOS had been modified by rootkit installation. After removing the rootkit and flashing the BIOS to a known good state, which of the following would BEST protect against future adversary access to the BIOS, in case another rootkit is installed?A. Anti-malware application
B. Host-based IDS
C. TPM data sealing
D. File integrity monitoring
A system administrator who was using an account with elevated privileges deleted a large amount of log files generated by a virtual hypervisor in order to free up disk space. These log files are needed by the security team to analyze the health of the virtual machines. Which of the following compensating controls would help prevent this from reoccurring? (Choose two.)A. Succession planning
B. Separation of duties
C. Mandatory vacation
D. Personnel training
E. Job rotation
A web application has a newly discovered vulnerability in the authentication method used to validate known company users. The user ID of Admin with a password of "password" grants elevated access to the application over the Internet. Which of the following is the BEST method to discover the vulnerability before a production deployment?A. Manual peer review
B. User acceptance testing
C. Input validation
D. Stress test the application
An analyst was tasked with providing recommendations of technologies that are PKI X.509 compliant for a variety of secure functions. Which of the following technologies meet the compatibility requirement? (Choose three.)A. 3DES
B. AES
C. IDEA
D. PKCS
E. PGP
F. SSL/TLS
G. TEMPEST
An organization has recently recovered from an incident where a managed switch had been accessed and reconfigured without authorization by an insider. The incident response team is working on developing a lessons learned report with recommendations. Which of the following recommendations will BEST prevent the same attack from occurring in the future?A. Remove and replace the managed switch with an unmanaged one.
B. Implement a separate logical network segment for management interfaces.
C. Install and configure NAC services to allow only authorized devices to connect to the network.
D. Analyze normal behavior on the network and configure the IDS to alert on deviations from normal.
A security analyst has determined that the user interface on an embedded device is vulnerable to common SQL injections. The device is unable to be replaced, and the software cannot be upgraded. Which of the following should the security analyst recommend to add additional security to this device?A. The security analyst should recommend this device be placed behind a WAF.
B. The security analyst should recommend an IDS be placed on the network segment.
C. The security analyst should recommend this device regularly export the web logs to a SIEM system.
D. The security analyst should recommend this device be included in regular vulnerability scans.
A security administrator uses FTK to take an image of a hard drive that is under investigation. Which of the following processes are used to ensure the image is the same as the original disk? (Choose two.)A. Validate the folder and file directory listings on both.
B. Check the hash value between the image and the original.
C. Boot up the image and the original systems to compare.
D. Connect a write blocker to the imaging device.
E. Copy the data to a disk of the same size and manufacturer.
An organization is performing vendor selection activities for penetration testing, and a security analyst is reviewing the MOA and rules of engagement, which were supplied with proposals. Which of the following should the analyst expect will be included in the documents and why?A. The scope of the penetration test should be included in the MOA to ensure penetration testing is conducted against only specifically authorized network resources.
B. The MOA should address the client SLA in relation to reporting results to regulatory authorities, including issuing banks for organizations that process cardholder data.
C. The rules of engagement should include detailed results of the penetration scan, including all findings, as well as designation of whether vulnerabilities identified during the scanning phases are found to be exploitable during the penetration test.
D. The exploitation standards should be addressed in the rules of engagement to ensure both parties are aware of the depth of exploitation that will be attempted by penetration testers.
A security analyst is performing a stealth black-box audit of the local WiFi network and is running a wireless sniffer to capture local WiFi network traffic from a specific wireless access point. The SSID is not appearing in the sniffing logs of the local wireless network traffic. Which of the following is the best action that should be performed NEXT to determine the SSID?A. Set up a fake wireless access point
B. Power down the wireless access point
C. Deauthorize users of that access point
D. Spoof the MAC addresses of adjacent access points
After implementing and running an automated patching tool, a security administrator ran a vulnerability scan that reported no missing patches found. Which of the following BEST describes why this tool was used?A. To create a chain of evidence to demonstrate when the servers were patched.
B. To harden the servers against new attacks.
C. To provide validation that the remediation was active.
D. To generate log data for unreleased patches.
The help desk informed a security analyst of a trend that is beginning to develop regarding a suspicious email that has been reported by multiple users. The analyst has determined the email includes an attachment named invoice.zip that contains the following files:
Locky.js -
xerty.ini
xerty.lib
Further analysis indicates that when the .zip file is opened, it is installing a new version of ransomware on the devices. Which of the following should be done
FIRST to prevent data on the company NAS from being encrypted by infected devices?A. Disable access to the company VPN.
B. Move the files from the NAS to a cloud-based storage solution.
C. Set permissions on file shares to read-only.
D. Add the URL included in the .js file to the company's web proxy filter.
A security analyst received an email with the following key:
Xj3XJ3LLc -
A second security analyst received an email with following key:
3XJ3xjcLLC
The security manager has informed the two analysts that the email they received is a key that allows access to the company's financial segment for maintenance.
This is an example of:A. dual control
B. private key encryption
C. separation of duties
D. public key encryption
E. two-factor authentication
A technician at a company's retail store notifies an analyst that disk space is being consumed at a rapid rate on several registers. The uplink back to the corporate office is also saturated frequently. The retail location has no Internet access. An analyst then observes several occasional IPS alerts indicating a server at corporate has been communicating with an address on a watchlist. Netflow data shows large quantities of data transferred at those times.
Which of the following is MOST likely causing the issue?A. A credit card processing file was declined by the card processor and caused transaction logs on the registers to accumulate longer than usual.
B. Ransomware on the corporate network has propagated from the corporate network to the registers and has begun encrypting files there.
C. A penetration test is being run against the registers from the IP address indicated on the watchlist, generating large amounts of traffic and data storage.
D. Malware on a register is scraping credit card data and staging it on a server at the corporate office before uploading it to an attacker-controlled command and control server.
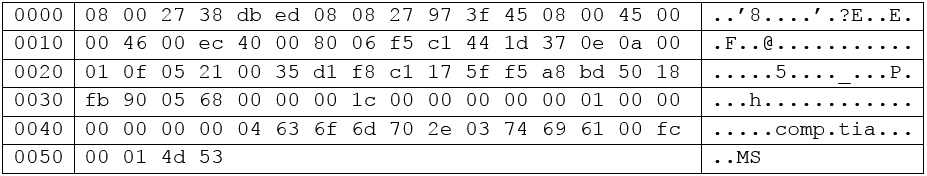
A security analyst is reviewing packet captures to determine the extent of success during an attacker's reconnaissance phase following a recent incident.
The following is a hex and ASCII dump of one such packet:
Which of the following BEST describes this packet?A. DNS BIND version request
B. DNS over UDP standard query
C. DNS over TCP server status query
D. DNS zone transfer request
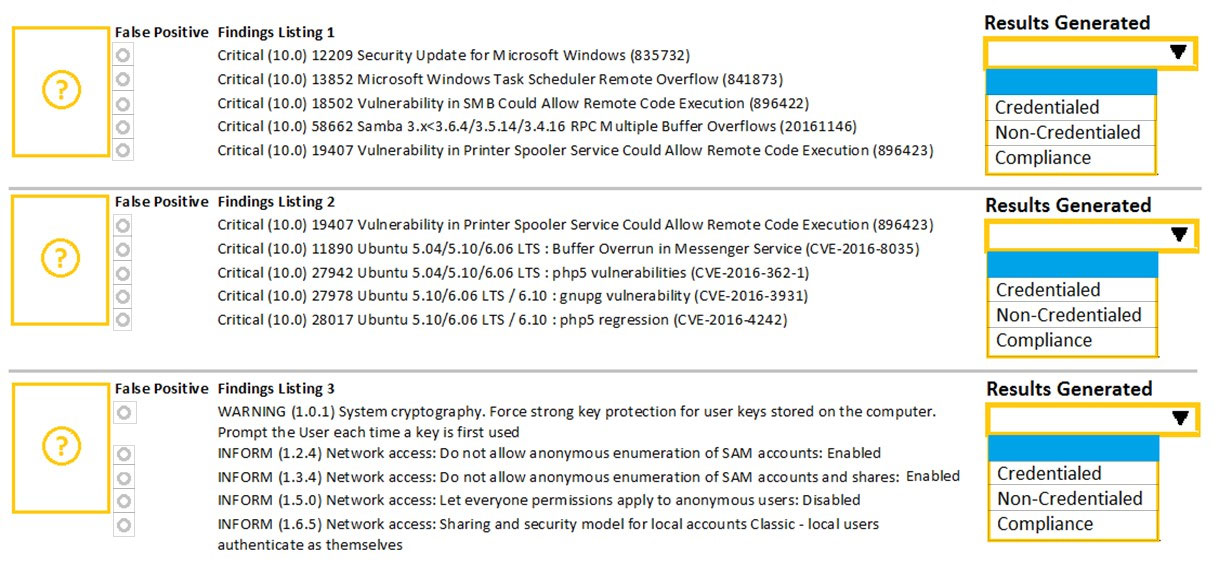
HOTSPOT -
A security analyst performs various types of vulnerability scans.
Review the vulnerability scan results to determine the type of scan that was executed and if a false positive occurred for each device.
Instructions:
Select the Results Generated drop-down option to determine if the results were generated from a credentialed scan, non-credentialed scan, or a compliance scan.
For ONLY the credentialed and non-credentialed scans, evaluate the results for false positives and check the findings that display false positives. NOTE: If you would like to uncheck an option that is currently selected, click on the option a second time.
Lastly, based on the vulnerability scan results, identify the type of Server by dragging the Server to the results.
The Linux Web Server, File-Print Server and Directory Server are draggable.
If at any time you would like to bring back the initial state of the simulation, please select the Reset All button. When you have completed the simulation, please select the Done button to submit. Once the simulation is submitted, please select the Next button to continue.
Hot Area:
A security analyst is assisting with a computer crime investigation and has been asked to secure a PC and deliver it to the forensic lab. Which of the following items would be MOST helpful to secure the PC? (Choose three.)A. Tamper-proof seals
B. Faraday cage
C. Chain of custody form
D. Drive eraser
E. Write blockers
F. Network tap
G. Multimeter
Management is concerned with administrator access from outside the network to a key server in the company. Specifically, firewall rules allow access to the server from anywhere in the company. Which of the following would be an effective solution?A. Honeypot
B. Jump box
C. Server hardening
D. Anti-malware
Free Access Full CS0-001 Practice Test Free Questions
If you're looking for more CS0-001 practice test free questions, click here to access the full CS0-001 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your CS0-001 certification journey!