350-401 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 350-401 exam? Start with our 350-401 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 350-401 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 350-401 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
What do Cisco DNA southbound APIs provide?
A. interface between the controller and the consumer
B. RESTful API interface for orchestrator communication
C. interface between the controller and the network devices
D. NETCONF API interface for orchestrator communication
Which API does Cisco DNA Center use to retrieve information about images?
A. SWIM
B. Img-Mgmt
C. PnP
D. Client Health
What are some of the key differences between HSRPv1 and HSRPv2? (Choose two.)
A. HSRPv1 uses the multicast address of 224.0.0.102 while HSRPv2 uses 225.0.0.2.
B. HSRP uses a group range of 0-255, while HSRP uses a group range of 0-4095.
C. HSRPv1 uses seconds based timers, while HSRPv2 uses milliseconds based timers.
D. HSRPv1 provides support for IPv6, while HSRPv2 supports IPv4 only.
Why is an AP joining a different WLC than the one speci ed through option 43?
A. The AP is joining a primed WLC
B. The APs broadcast traffic is unable to reach the WLC through Layer 2
C. The AP multicast traffic is unable to reach the WLC through Layer 3
D. The WLC is running a different software version
20conventions.-,Overview%20of%20the%20Wireless%20LAN%20Controller%20(WLC)%20Discovery%20and%20Join%20Process,- In%20a%20Cisco
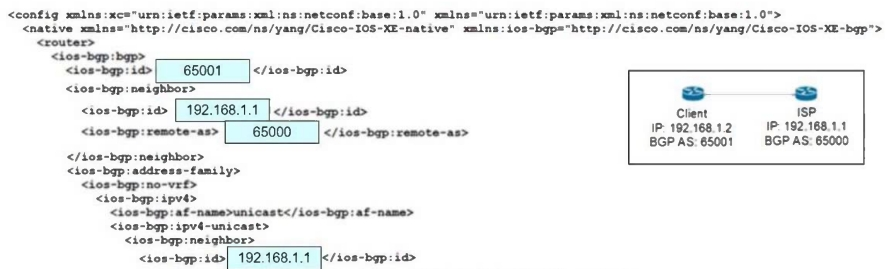
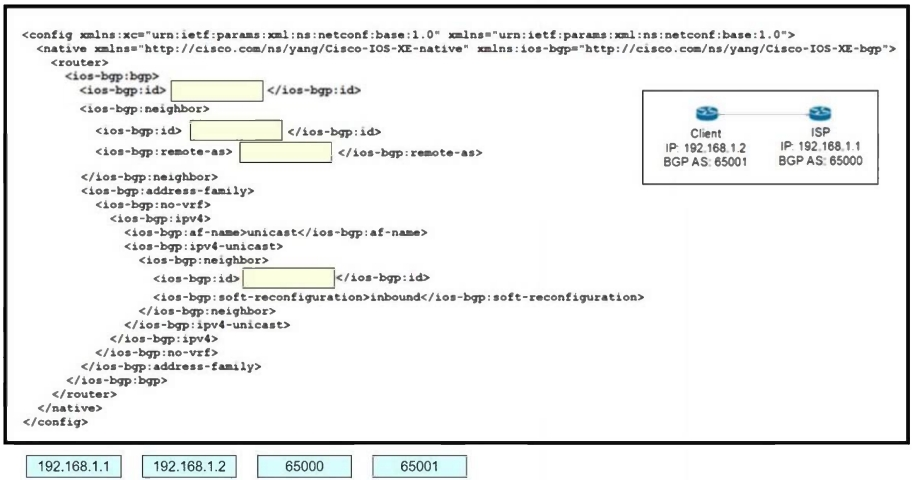
Refer to the exhibit.An engineer must establish eBGP peering between router R3 and router R4. Both routers should use their loopback interfaces as the BGP router I
A. Which configuration set accomplishes this task?
B. R3(config)#router bgp 200 R3(config-router)#neighbor 10.4.4.4 remote-as 100 R3(config-router)# neighbor 10.4.4.4 update-source Loopback0 R4(config)#router bgp 100 R4(config-router)#neighbor 10.3.3.3 remote-as 200 R4(config-router)#network 10.3.3.3 update-source Loopback0
C. R3(config)#router bgp 200 R3(config-router)#neighbor 10.24.24.4 remote-as 100 R3(config-router)#neighbor 10.24.24.4 update-source Loopback0 R4(config)#router bgp 100 R4(config-router)#neighbor 10.24.24.3 remote-as 200 R4(config-router)#neighbor 10.24.24.3 update- source Loopback0
D. R3(config)#router bgp 200 R3(config-router)#neighbor 10.4.4.4 remote-as 100 R3(config-router)#bgp router-id 10.3.3.3 R4(config)#router bgp 100 R4(config-router)#neighbor 10.3.3.3 remote-as 200 R4(config-router)#bgp router-id 10.4.4.4
E. R3(config)#router bgp 200 R3(config-router)#neighbor 10.24.24.4 remote-as 100 R3(config-router)#bgp router-id 10.3.3.3 R4(config)#router bgp 100 R4(config-router)#neighbor 10.24.24.3 remote-as 200 R4(config-router)#bgp router-id 10.4.4.4
Drag and drop the snippets onto the blanks within the code to construct a script that configures BGP according to the topology. Not all options are used, and some options may be used twice.
Select and Place:
Refer to the exhibit. An engineer must configure a Cisco WLC with WPA2 Enterprise mode and avoid global server lists. Which action is required?
A. Enable EAP parameters
B. Apply CISCO ISE default settings
C. Select a RADIUS authentication server
D. Disable the RADIUS server accounting interim update
Refer to the exhibit. What is output by this code?
A. -1 -2 -3 -4
B. 8 7 6 5
C. 4 5 6 7
D. -4 -5 -6 -7
Which Cisco DNA Center application is responsible for group-based access control permissions?
A. Provision
B. Design
C. Assurance
D. Policy
What is a common trait between Ansible and Chef?
A. Both rely on a declarative approach.
B. Both are used for mutable infrastructure.
C. Both require a client to be installed on hosts.
D. Both rely on NETCONF.
Which two features are available only in next-generation rewalls? (Choose two.)
A. application awareness
B. packet filtering
C. stateful inspection
D. deep packet inspection
E. virtual private network
Which method of account authentication does OAuth 2.0 use within REST APIs?
A. username/role combination
B. access tokens
C. cookie authentication
D. basic signature work flow
What is the purpose of an RP in PIM?
A. send join messages toward a multicast source SPT
B. ensure the shortest path from the multicast source to the receiver
C. receive IGMP joins from multicast receivers
D. secure the communication channel between the multicast sender and receiver
Refer to the exhibit. An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected. Which action resolves this issue?
A. Change the source network that is speci ed in access-list 101.
B. Change the access-list destination mask to a wildcard.
C. Change the access-list number in the route map.
D. Change the route-map configuration to VRF_BLU
E.
Which language defines the structure or modeling of data for NETCONF and RESTCONF?
A. YAML
B. XML
C. JSON
D. YANG
What is one characteristic of the Cisco SD-Access control plane?
A. It allows host mobility only in the wireless network.
B. It is based on VXLAN technology.
C. Each router processes every possible destination and route.
D. It stores remote routes in a centralized database server.
A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WL
A. Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WL
B. After a failure on the primary 5520 WLC, all WLAN services remain functional; however, clients cannot roam between the 5520 and 9800 controllers without dropping their connection. Which feature must be configured to remedy the issue?
C. mobility MAC on the 5520 cluster
D. mobility MAC on the 9800 WLC
E. new mobility on the 5520 cluster
F. new mobility on the 9800 WLC
What does the number in an NTP stratum level represent?
A. The number of hops it takes to reach the authoritative time source
B. The amount of offset between the device clock and true time
C. The number of hops it takes to reach the primary time server
D. The amount of drift between the device clock and true time
When using TLS for syslog, which configuration allows for secure and reliable transportation of messages to its default port?
A. logging host 10.2.3.4 vrf mgmt transport tcp port 514
B. logging host 10.2.3.4 vrf mgmt transport udp port 514
C. logging host 10.2.3.4 vrf mgmt transport tcp port 6514
D. logging host 10.2.3.4 vrf mgmt transport udp port 6514
A network is being migrated from IPv4 to IPv6 using a dual-stack approach. Network management is already 100% IPv6 enabled. In a dual-stack network with two dual-stack NetFlow collectors, how many flow exporters are needed per network device in the flexible NetFlow configuration?
A. 1
B. 2
C. 4
D. 8
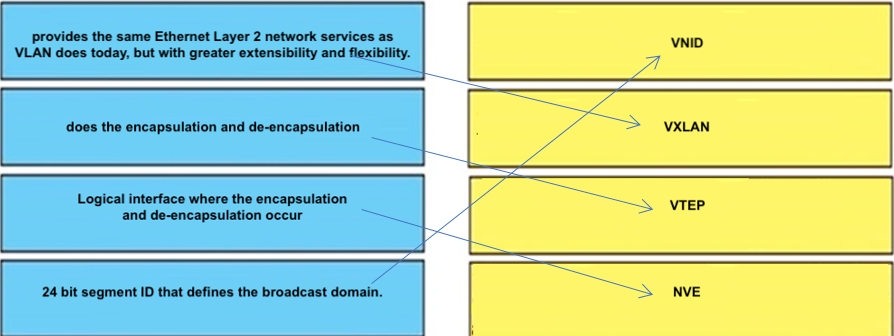
Drag and drop the definitions in the left to their respective Terminology in the right.
Select and Place:

Which function is performed by vSmart in the Cisco SD-WAN architecture?
A. aggregation and distribution of VPN routing information
B. execution of localized policies
C. facilitation of NAT detection and traversal
D. redistribution between OMP and other routing protocols
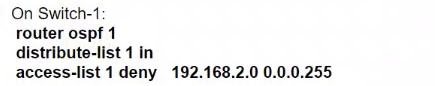
Refer to the exhibit. An engineer must prevent VLAN 20 routes from appearing in the routing table of Switch-1. Which command set must be applied?
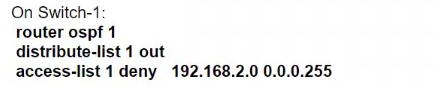
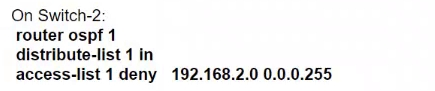
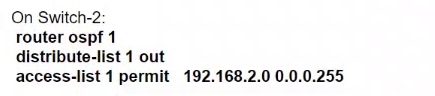
A.
A customer has two Cisco WLCs that manage separate APs throughout a building. Each WLC advertises the same SSID but terminates on different interfaces. Users report that they drop their connections and change IP addresses when roaming. Which action resolves this issue?
A. configure high availability.
B. Enable fast roaming.
C. configure mobility groups.
D. Enable client load balancing
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. patch
B. dipole
C. omnidirectional
D. Yagi
An engineer configures a WLAN with fast transition enabled. Some legacy clients fail to connect to this WLAN. Which feature allows the legacy clients to connect while still allowing other clients to use fast transition based on their OUIs?
A. over the DS
B. 802.11k
C. adaptive R
D. 802.11v
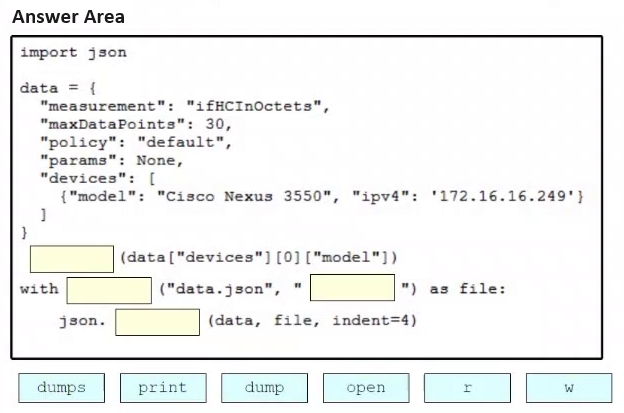
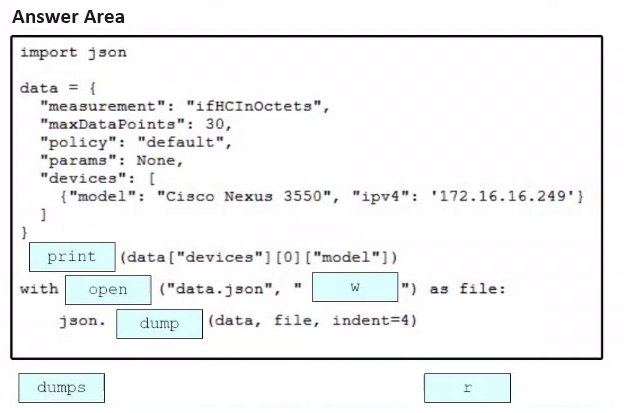
Drag and drop the code snippets from the bottom onto the blanks in the Python script to print the device model to the screen and write JSON data to a file. Not all options are used.
Select and Place:
Which control plane protocol is used between Cisco SD-WAN routers and vSmart controllers?
A. TCP
B. OMP
C. UDP
D. BGP
Refer to the exhibit.Which type of antenna does the radiation pattern represent?
A. multidirectional
B. directional patch
C. omnidirectional
D. Yagi
What is one method for achieving REST API security?
A. using a combination of XML encryption and XML signatures
B. using HTTPS and TLS encryption
C. using a MDS hash to verify the integrity
D. using built-in protocols known as Web Services Security
What is an advantage of utilizing data models in a multivendor environment?
A. lowering CPU load incurred to managed devices
B. improving communication security with binary encoded protocols
C. facilitating a unified approach to configuration and management
D. removing the distinction between configuration and runtime state data
An engineer has deployed a single Cisco 5520 WLC with a management IP address of 172 16.50.5/24. The engineer must register 50 new Cisco AIR-CAP2802I- E-K9 access points to the WLC using DHCP option 43. The access points are connected to a switch in VLAN 100 that uses the 172.16.100.0/24 subnet. The engineer has configured the DHCP scope on the switch as follows: Network 172.16.100.0 255.255.255.0 Default Router 172.16.100.1 - Option 43 ASCII 172.16.50.5 - The access points are failing to join the wireless LAN controller. Which action resolves the issue?
A. configure option 43 Hex F104.AC10.3205
B. configure option 43 Hex F104.CA10.3205
C. configure dns-server 172.16.50.5
D. configure dns-server 172. 16.100.1
Which technology reduces the implementation of STP and leverages both unicast and multicast?
A. VLAN
B. VPC
C. VXLAN
D. VSS
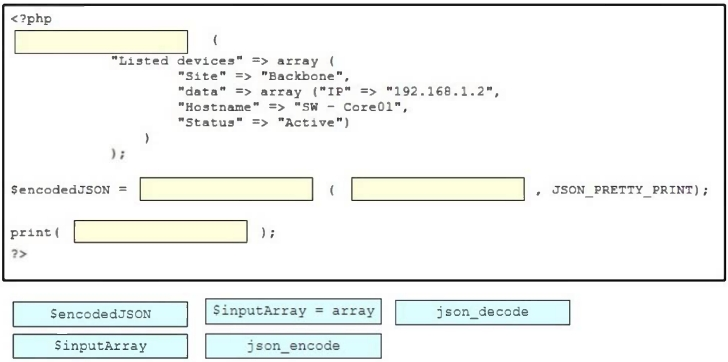
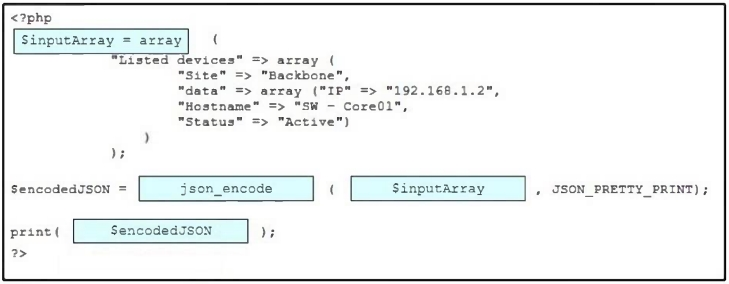
Drag and drop the code snippets from the bottom onto the blanks in the PHP script to convert a PHP array into JSON format. Not all options are used.
Select and Place:
Refer to the exhibit. An engineer is configuring an EtherChannel between Switch1 and Switch2 and notices the console message on Switch2. Based on the output, which action resolves this issue?
A. configure more member ports on Switch1.
B. configure less member ports on Switch2.
C. configure the same port channel interface number on both switches.
D. configure the same EtherChannel protocol on both switches.
Refer to the exhibit. An engineer must prevent the R6 loopback from getting into Area 2 and Area 3 from Area 0. Which action must the engineer take?
A. Apply a filter list outbound on R3 and R7.
B. Apply a filter list inbound on R2 and R9.
C. Apply a filter list inbound on R3 and R7.
D. Apply a filter list outbound on R7 only.
Which configuration saves the running configuration to the startup configuration and logs a "saving configuration automatically" message when a syslog message that contains "SYS-5-CONFIG_I" is received?


A. C
An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority in group 5, it must assume the master role. Which command set should the engineer add to the configuration to accomplish this task? interface GigabitEthernet1/0/0 description To IDF A 38- 70-774-10 ip address 172.16.13.2 255.255.255.0
A. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 track 1 decrement 10
B. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 preempt
C. vrrp 5 ip 172.16.13.254 vrrp 5 priority 100
D. vrrp 5 ip 172.16.13.254 255.255.255.0 vrrp 5 track 1 decrement 10 vrrp 5 preempt C
Which configuration restricts the amount of SSH traffic that a router accepts to 100 kbps?
A. 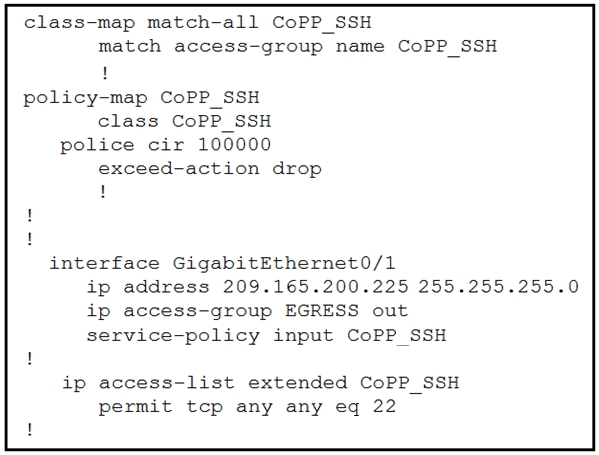
B. 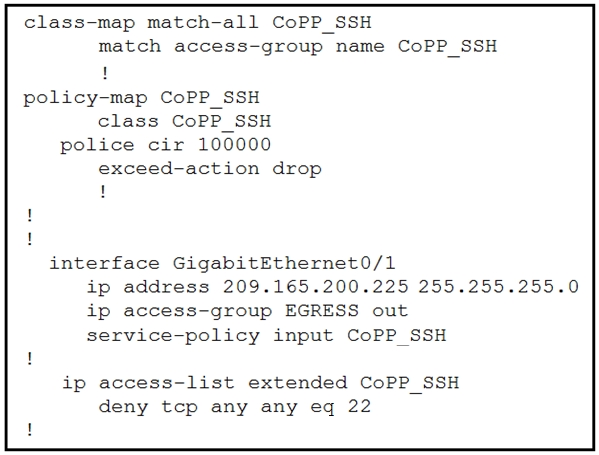
C. 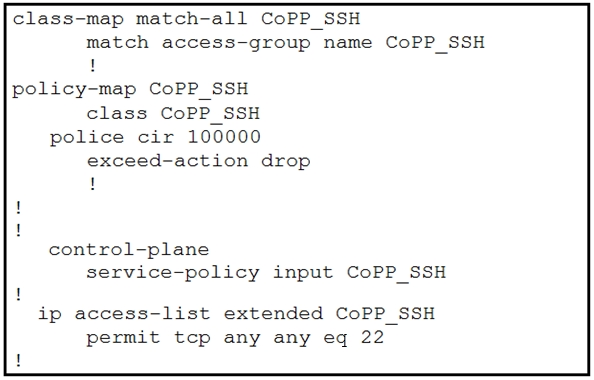
D. 
When does Cisco DNA Center make changes to a device?
A. when the device credentials are added
B. when the network device is assigned to the site and device controllability is turned on
C. when the network device is discovered and device controllability is turned on
D. when a NETCONF port has been configured
Which two security mechanisms are used by Cisco Threat Defense to gain visibility into the most dangerous cyber threats? (Choose two.)
A. virtual private networks
B. file reputation
C. VLAN segmentation
D. traffic Telemetry
E. dynamic enforce policy
An engineer must protect their company against ransomware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco Firepower and block traffic to TOR networks.
B. Use Cisco AMP deployment with the Malicious Activity Protection engine enabled.
C. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
D. Use Cisco AMP deployment with the Exploit Prevention engine enabled.
What are two best practices when designing a campus Layer 3 infrastructure? (Choose two.)
A. configure passive-interface on nontransit links.
B. Implement security features at the core.
C. Summarize routes from the aggregation layer toward the core layer.
D. Tune Cisco Express Forwarding load balancing hash for ECMP routing.
E. Summarize from the access layer toward the aggregation layer.
An engineer must configure router R1 to validate user logins via RADIUS and fall back to the local user database if the RADIUS server is not available. Which configuration must be applied?
A. aaa authentication exec default radius local
B. aaa authentication exec default radius
C. aaa authorization exec default radius local
D. aaa authorization exec default radius
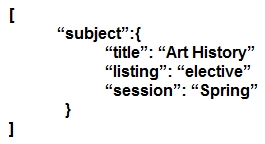
Which JSON script is properly formatted?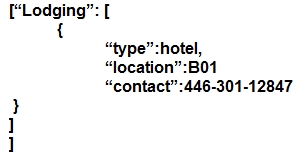
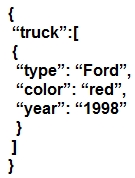
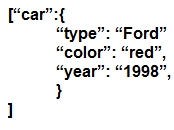
A.
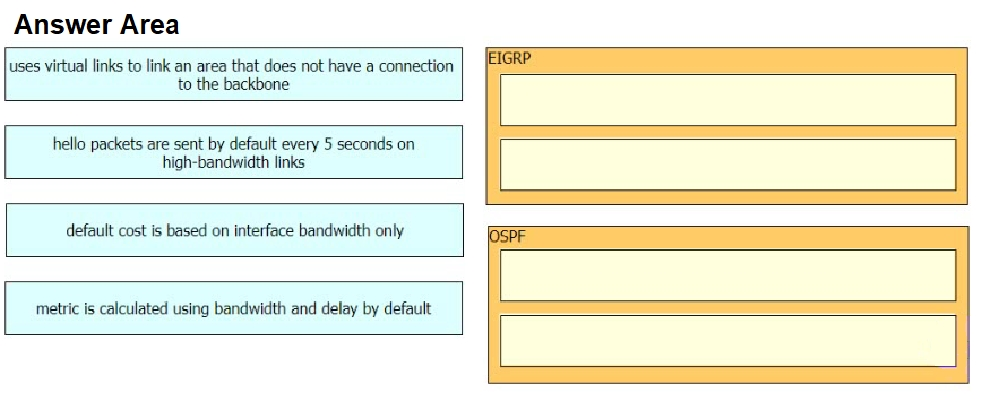
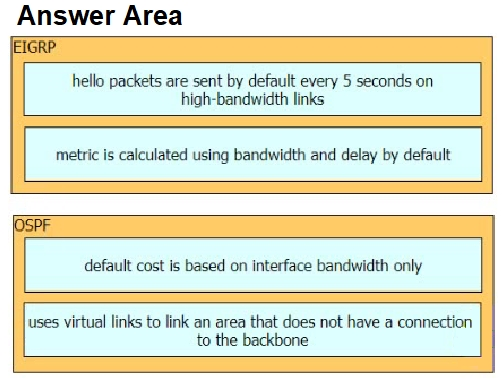
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
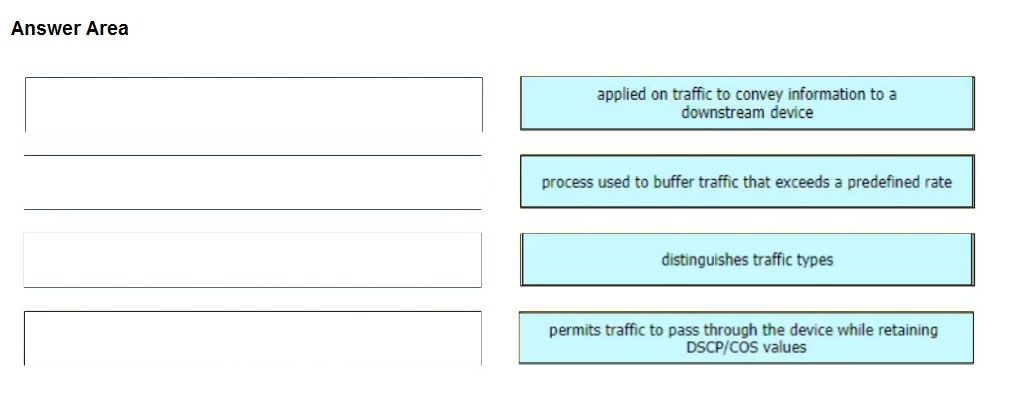
Drag and drop the characteristics from the left onto the QoS components they describe on the right.
Select and Place:

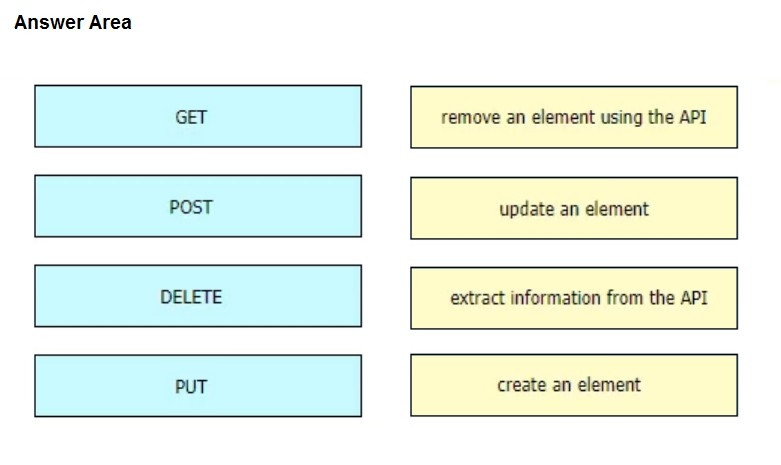
An engineer is working with the Cisco DNA Center API. Drag and drop the methods from the left onto the actions that they are used for on the right.
Select and Place:
What is a characteristic of YANG?
A. It is a Cisco proprietary language that models NETCONF data.
B. It allows model developers to create custom data types.
C. It structures data in an object-oriented fashion to promote model reuse.
D. It provides loops and conditionals to control flow within models.
If a client's radio device receives a signal strength of -67 dBm and the noise floor is -85 dBm, what is the SNR value?
A. 15 dB
B. 16 dB
C. 18 dB
D. 20 dB
Free Access Full 350-401 Practice Test Free Questions
If you’re looking for more 350-401 practice test free questions, click here to access the full 350-401 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 350-401 certification journey!