312-50V9 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 312-50V9 exam? Start with our 312-50V9 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 312-50V9 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 312-50V9 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Based on the following extract from the log of a compromised machine, what is the hacker really trying to steal?
A. har.txt
B. SAM file
C. wwwroot
D. Repair file
Which of the following parameters describe LM Hash (see exhibit): Exhibit:
A. I, II, and III
B. I
C. II
D. I and II
To send a PGP encrypted message, which piece of information from the recipient must the sender have before encrypting the message?
A. Recipient’s private key
B. Recipient’s public key
C. Master encryption key
D. Sender’s public key
The precaution of prohibiting employees from bringing personal computing devices into a facility is what type of security control?
A. Physical
B. Procedural
C. Technical
D. Compliance
Which tool is used to automate SQL injections and exploit a database by forcing a given web application to connect to another database controlled by a hacker?
A. DataThief
B. NetCat
C. Cain and Abel
D. SQLInjector
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
Jack was attempting to fingerprint all machines in the network using the following Nmap syntax: invictus@victim_server:~$ nmap -T4 -0 10.10.0.0/24 TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING! Obviously, it is not going through. What is the issue here?
A. OS Scan requires root privileges
B. The nmap syntax is wrong.
C. The outgoing TCP/IP fingerprinting is blocked by the host firewall
D. This is a common behavior for a corrupted nmap application
While examining audit logs, you discover that people are able to telnet into the SMTP server on port 25. You would like to block this, though you do not see any evidence of an attack or other wrong doing. However, you are concerned about affecting the normal functionality of the email server. From the following options choose how best you can achieve this objective?
A. Block port 25 at the firewall.
B. Shut off the SMTP service on the server.
C. Force all connections to use a username and password.
D. Switch from Windows Exchange to UNIX Sendmail.
E. None of the above.
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
A. Locate type=ns
B. Request type=ns
C. Set type=ns
D. Transfer type=ns
The security concept of "separation of duties" is most similar to the operation of which type of security device?
A. Firewall
B. Bastion host
C. Intrusion Detection System
D. Honeypot
A person approaches a network administrator and wants advice on how to send encrypted email from home. The end user does not want to have to pay for any license fees or manage server services. Which of the following is the most secure encryption protocol that the network administrator should recommend?
A. IP Security (IPSEC)
B. Multipurpose Internet Mail Extensions (MIME)
C. Pretty Good Privacy (PGP)
D. Hyper Text Transfer Protocol with Secure Socket Layer (HTTPS) C
The chance of a hard drive failure is known to be once every four years. The cost of a new hard drive is $500. EF (Exposure Factor) is about 0.5. Calculate for the Annualized Loss Expectancy (ALE).
A. $62.5
B. $250
C. $125
D. $65.2
You work for Acme Corporation as Sales Manager. The company has tight network security restrictions. You are trying to steal data from the company's Sales database (Sales.xls) and transfer them to your home computer. Your company filters and monitors traffic that leaves from the internal network to the Internet. How will you achieve this without raising suspicion?
A. Encrypt the Sales.xls using PGP and e-mail it to your personal gmail account
B. Package the Sales.xls using Trojan wrappers and telnet them back your home computer [1] Steganography techniques
D. Change the extension of Sales.xls to sales.txt and upload them as attachment to your hotmail account
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
A. NMAP -P 192.168.1-5.
B. NMAP -P 192.168.0.0/16
C. NMAP -P 192.168.1.0,2.0,3.0,4.0,5.0
D. NMAP -P 192.168.1/17
WPA2 uses AES for wireless data encryption at which of the following encryption levels?
A. 64 bit and CCMP
B. 128 bit and CRC
C. 128 bit and CCMP
D. 128 bit and TKIP
A company firewall engineer has configured a new DMZ to allow public systems to be located away from the internal network. The engineer has three security zones set:The engineer wants to configure remote desktop access from a fixed IP on the remote network to a remote desktop server in the DMZ. Which rule would best fit this requirement?
A. Permit 217.77.88.0/24 11.12.13.0/24 RDP 3389
B. Permit 217.77.88.12 11.12.13.50 RDP 3389
C. Permit 217.77.88.12 11.12.13.0/24 RDP 3389
D. Permit 217.77.88.0/24 11.12.13.50 RDP 3389
Which of the following lists are valid data-gathering activities associated with a risk assessment?
A. Threat identification, vulnerability identification, control analysis
B. Threat identification, response identification, mitigation identification
C. Attack profile, defense profile, loss profile
D. System profile, vulnerability identification, security determination
Which statement best describes a server type under an N-tier architecture?
A. A group of servers at a specific layer
B. A single server with a specific role
C. A group of servers with a unique role
D. A single server at a specific layer
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
A. Firewall-management policy
B. Acceptable-use policy
C. Remote-access policy
D. Permissive policy
Which of the following is a characteristic of Public Key Infrastructure (PKI)?
A. Public-key cryptosystems are faster than symmetric-key cryptosystems.
B. Public-key cryptosystems distribute public-keys within digital signatures.
C. Public-key cryptosystems do not require a secure key distribution channel.
D. Public-key cryptosystems do not provide technical non-repudiation via digital signatures.
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
A. Cain
B. John the Ripper
C. Nikto
D. Hping
During a wireless penetration test, a tester detects an access point using WPA2 encryption. Which of the following attacks should be used to obtain the key?
A. The tester must capture the WPA2 authentication handshake and then crack it.
B. The tester must use the tool inSSIDer to crack it using the ESSID of the network.
C. The tester cannot crack WPA2 because it is in full compliance with the IEEE 802.11i standard.
D. The tester must change the MAC address of the wireless network card and then use the AirTraf tool to obtain the key.
A penetration tester is attempting to scan an internal corporate network from the internet without alerting the border sensor. Which is the most efficient technique should the tester consider using?
A. Spoofing an IP address
B. Tunneling scan over SSH
C. Tunneling over high port numbers
D. Scanning using fragmented IP packets
A hacker was able to sniff packets on a company's wireless network. The following information was discovered:Using the Exlcusive OR, what was the original message?
A. 00101000 11101110
B. 11010111 00010001
C. 00001101 10100100
D. 11110010 01011011
Which security control role does encryption meet?
A. Preventative
B. Detective
C. Offensive
D. Defensive
A hacker searches in Google for filetype:pcf to find Cisco VPN config files. Those files may contain connectivity passwords that can be decoded with which of the following?
A. Cupp
B. Nessus
C. Cain and Abel
D. John The Ripper Pro
Which set of access control solutions implements two-factor authentication?
A. USB token and PIN
B. Fingerprint scanner and retina scanner
C. Password and PIN
D. Account and password
While doing a technical assessment to determine network vulnerabilities, you used the TCP XMAS scan. What would be the response of all open ports?
A. The port will send an ACK
B. The port will send a SYN
C. The port will ignore the packets
D. The port will send an RST
Smart cards use which protocol to transfer the certificate in a secure manner?
A. Extensible Authentication Protocol (EAP)
B. Point to Point Protocol (PPP)
C. Point to Point Tunneling Protocol (PPTP)
D. Layer 2 Tunneling Protocol (L2TP)
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
A. Packet filtering firewall
B. Application-level firewall
C. Circuit-level gateway firewall
D. Stateful multilayer inspection firewall
Which of the following LM hashes represent a password of less than 8 characters? (Choose two.)
A.
B. 44EFCE164AB921CQAAD3B435B51404EE
C.
D.
E.
F.
Password cracking programs reverse the hashing process to recover passwords. (True/False.)
A. True
B. False
When setting up a wireless network, an administrator enters a pre-shared key for security. Which of the following is true?
A. The key entered is a symmetric key used to encrypt the wireless data.
B. The key entered is a hash that is used to prove the integrity of the wireless data.
C. The key entered is based on the Diffie-Hellman method.
D. The key is an RSA key used to encrypt the wireless data. A
Which of the following statements regarding ethical hacking is incorrect?
A. Ethical hackers should never use tools or methods that have the potential of exploiting vulnerabilities in an organization’s systems.
B. Testing should be remotely performed offsite.
C. An organization should use ethical hackers who do not sell vendor hardware/software or other consulting services.
D. Ethical hacking should not involve writing to or modifying the target systems.
Which of the following is considered the best way to protect Personally Identifiable Information (PII) from Web application vulnerabilities?
A. Use cryptographic storage to store all PII
B. Use encrypted communications protocols to transmit PII
C. Use full disk encryption on all hard drives to protect PII
D. Use a security token to log into all Web applications that use PII
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
A. Blue Book
B. ISO 26029
C. Common Criteria
D. The Wassenaar Agreement
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in-bounds checking mechanism?Output: Segmentation fault -
A. C#
B. Python
C. Java
D. C++
Switches maintain a CAM Table that maps individual MAC addresses on the network to physical ports on the switch.In MAC flooding attack, a switch is fed with many Ethernet frames, each containing different source MAC addresses, by the attacker. Switches have a limited memory for mapping various MAC addresses to physical ports. What happens when the CAM table becomes full?
A. Switch then acts as hub by broadcasting packets to all machines on the network
B. The CAM overflow table will cause the switch to crash causing Denial of Service
C. The switch replaces outgoing frame switch factory default MAC address of FF:FF:FF:FF:FF:FF
D. Every packet is dropped and the switch sends out SNMP alerts to the IDS port A
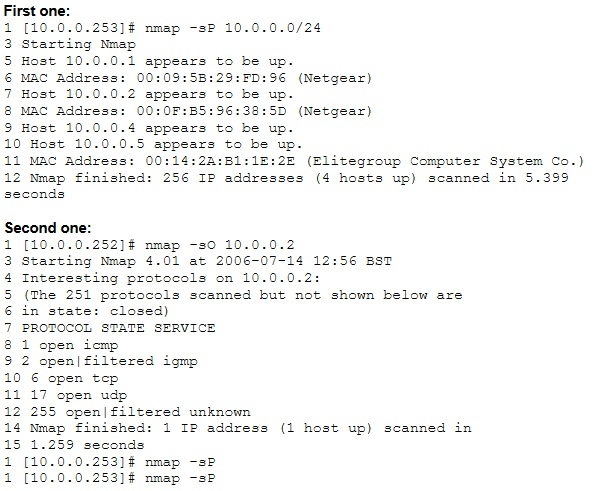
From the two screenshots below, which of the following is occurring?
A. 10.0.0.253 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
B. 10.0.0.253 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
C. 10.0.0.2 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
D. 10.0.0.252 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
Advanced encryption standard is an algorithm used for which of the following?
A. Data integrity
B. Key discovery
C. Bulk data encryption
D. Key recovery C
A hacker has managed to gain access to a Linux host and stolen the password file from /etc/passwd. How can he use it?
A. The password file does not contain the passwords themselves.
B. He can open it and read the user ids and corresponding passwords.
C. The file reveals the passwords to the root user only.
D. He cannot read it because it is encrypted.
Neil notices that a single address is generating traffic from its port 500 to port 500 of several other machines on the network. This scan is eating up most of the network bandwidth and Neil is concerned. As a security professional, what would you infer from this scan?
A. It is a network fault and the originating machine is in a network loop
B. It is a worm that is malfunctioning or hardcoded to scan on port 500
C. The attacker is trying to detect machines on the network which have SSL enabled
D. The attacker is trying to determine the type of VPN implementation and checking for IPSec
Which of the following algorithms provides better protection against brute force attacks by using a 160-bit message digest?
A. MD5
B. SHA-1
C. RC4
D. MD4
You are the Systems Administrator for a large corporate organization. You need to monitor all network traffic on your local network for suspicious activities and receive notifications when an attack is occurring. Which tool would allow you to accomplish this goal?
A. Network-based IDS
B. Firewall
C. Proxy
D. Host-based IDS
You’ve just gained root access to a Centos 6 server after days of trying. What tool should you use to maintain access?
A. Disable Key Services
B. Create User Account
C. Download and Install Netcat
D. Disable IPTables
Bluetooth uses which digital modulation technique to exchange information between paired devices?
A. PSK (phase-shift keying)
B. FSK (frequency-shift keying)
C. ASK (amplitude-shift keying)
D. QAM (quadrature amplitude modulation)
Which of the following is optimized for confidential communications, such as bidirectional voice and video?
A. RC4
B. RC5
C. MD4
D. MD5
Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
A. Restore a random file.
B. Perform a full restore.
C. Read the first 512 bytes of the tape.
D. Read the last 512 bytes of the tape.
An attacker sniffs encrypted traffic from the network and is subsequently able to decrypt it. The attacker can now use which cryptanalytic technique to attempt to discover the encryption key?
A. Birthday attack
B. Plaintext attack
C. Meet in the middle attack
D. Chosen ciphertext attack
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
A. Legal, performance, audit
B. Audit, standards based, regulatory
C. Contractual, regulatory, industry
D. Legislative, contractual, standards based
Free Access Full 312-50V9 Practice Test Free Questions
If you’re looking for more 312-50V9 practice test free questions, click here to access the full 312-50V9 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 312-50V9 certification journey!