312-49V10 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 312-49V10 exam? Start with our 312-49V10 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 312-49V10 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 312-49V10 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Billy, a computer forensics expert, has recovered a large number of DBX files during the forensic investigation of a laptop. Which of the following email clients can he use to analyze the DBX files?
A. Microsoft Outlook
B. Eudora
C. Mozilla Thunderbird
D. Microsoft Outlook Express
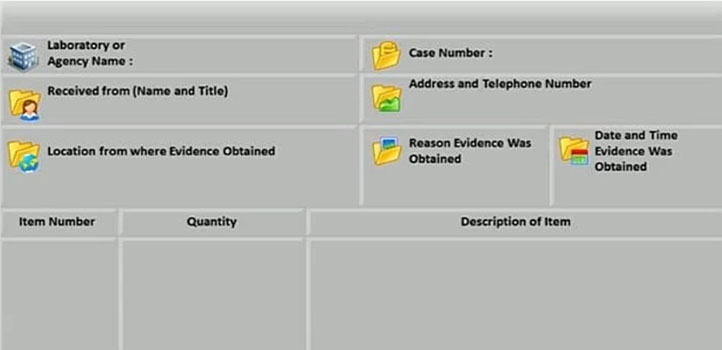
What document does the screenshot represent?
A. Expert witness form
B. Search warrant form
C. Chain of custody form
D. Evidence collection form
What feature of Decryption Collection allows an investigator to crack a password as quickly as possible?
A. Cracks every password in 10 minutes
B. Distribute processing over 16 or fewer computers
C. Support for Encrypted File System
D. Support for MD5 hash verification
What is considered a grant of a property right given to an individual who discovers or invents a new machine, process, useful composition of matter or manufacture?
A. Copyright
B. Design patent
C. Trademark
D. Utility patent
Volatile Memory is one of the leading problems for forensics. Worms such as code Red are memory resident and do write themselves to the hard drive, if you turn the system off they disappear. In a lab environment, which of the following options would you suggest as the most appropriate to overcome the problem of capturing volatile memory?
A. Use VMware to be able to capture the data in memory and examine it
B. Give the Operating System a minimal amount of memory, forcing it to use a swap file
C. Create a Separate partition of several hundred megabytes and place the swap file there
D. Use intrusion forensic techniques to study memory resident infections
Rusty, a computer forensics apprentice, uses the command nbtstat `"c while analyzing the network information in a suspect system. What information is he looking for?
A. Contents of the network routing table
B. Status of the network carrier
C. Contents of the NetBIOS name cache
D. Network connections
What is an investigator looking for in the rp.log file stored in a system running on Windows 10 operating system?
A. Restore point interval
B. Automatically created restore points
C. System CheckPoints required for restoring
D. Restore point functions
Which of the following files gives information about the client sync sessions in Google Drive on Windows?
A. sync_log.log
B. Sync_log.log
C. sync.log
D. Sync.log
An investigator needs to perform data acquisition from a storage media without altering its contents to maintain the integrity of the content. The approach adopted by the investigator relies upon the capacity of enabling read-only access to the storage media. Which tool should the investigator integrate into his/her procedures to accomplish this task?
A. Data duplication tool
B. BitLocker
C. Write blocker
D. Backup tool
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
A. Send DOS commands to crash the DNS servers
B. Perform DNS poisoning
C. Perform a zone transfer
D. Enumerate all the users in the domain
Raw data acquisition format creates _________ of a data set or suspect drive.
A. Segmented image files
B. Simple sequential flat files
C. Compressed image files
D. Segmented files
Which Federal Rule of Evidence speaks about the Hearsay exception where the availability of the declarant is immaterial and certain characteristics of the declarant such as present sense impression, excited utterance, and recorded recollection are also observed while giving their testimony?
A. Rule 801
B. Rule 802
C. Rule 803
D. Rule 804
Brian has the job of analyzing malware for a software security company. Brian has setup a virtual environment that includes virtual machines running various versions of OSes. Additionally, Brian has setup separated virtual networks within this environment. The virtual environment does not connect to the company's intranet nor does it connect to the external Internet. With everything setup, Brian now received an executable file from client that has undergone a cyberattack. Brian ran the executable file in the virtual environment to see what it would do. What type of analysis did Brian perform?
A. Status malware analysis
B. Static OS analysis
C. Static malware analysis
D. Dynamic malware analysis
During a malware forensic investigation, a newly added entry was identified in the Windows AutoStart registry keys after a malware execution on a compromised system. The entry indicates a VB script file named "CaoClboog.vbs" installed in the 'Run' key to achieve persistence and run automatically upon user login. As a Computer Hacking Forensic Investigator (CHFI), where would you expect to find this suspicious entry in the registry hive?
A. HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionExplorerUser Shell Folders, Startup
B. HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun
C. HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRun
D. HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionExplorerShell Folders, Common Startup
Which of the following tool enables a user to reset his/her lost admin password in a Windows system?
A. Advanced Office Password Recovery
B. Active@ Password Changer
C. Smartkey Password Recovery Bundle Standard
D. Passware Kit Forensic
An investigator is checking a Cisco firewall log that reads as follows: Aug 21 2019 09:16:44: %ASA-1 -106021: Deny ICMP reverse path check from 10.0.0.44 to 10.0.0.33 on interface outside What does %ASA-1-106021 denote?
A. Type of request
B. Mnemonic message
C. Firewall action
D. Type of traffic
Someone in the field of forensic investigation is looking at an Apache access log. They're searching for any evidence of a command injection attack. During this process, they find a log entry where the IP address "10.0.0.8" placed a GET request using the command ip=127.0.0.1;ls+/var/www/html. Judging by this data, what might be the individual’s objective behind this attack?
A. The individual behind the attack is attempting a brute-force attack on the host server
B. The individual behind the attack is working towards replacing the target file on the host server
C. The individual behind the attack aims to see what’s inside the /var/www/html directory of the host server
D. The individual behind the attack is working to put an XML external entity into the web application
The Recycle Bin exists as a metaphor for throwing files away, but it also allows a user to retrieve and restore files. Once the file is moved to the recycle bin, a record is added to the log file that exists in the Recycle Bin. Which of the following files contains records that correspond to each deleted file in the Recycle Bin?
A. INFO2
B. INFO1
C. LOGINFO1
D. LOGINFO2
Which of the following is NOT a physical evidence?
A. Removable media
B. Cables
C. Image file on a hard disk
D. Publications
Jason has set up a honeypot environment by creating a DMZ that has no physical or logical access to his production network. In this honeypot, he has placed a server running Windows Active Directory. He has also placed a Web server in the DMZ that services a number of web pages that offer visitors a chance to download sensitive information by clicking on a button. A week later, Jason finds in his network logs how an intruder accessed the honeypot and downloaded sensitive information. Jason uses the logs to try and prosecute the intruder for stealing sensitive corporate information. Why will this not be viable?
A. Entrapment
B. Enticement
C. Intruding into a honeypot is not illegal
D. Intruding into a DMZ is not illegal
Fill in the missing Master Boot Record component. 1. Master boot code 2. Partition table 3. ____________
A. Signature word
B. Volume boot record
C. Boot loader
D. Disk signature
Which of the following is a list of recently used programs or opened files?
A. Most Recently Used (MRU)
B. Recently Used Programs (RUP)
C. Master File Table (MFT)
D. GUID Partition Table (GPT)
In which registry does the system store the Microsoft security IDs?
A. HKEY_CLASSES_ROOT (HKCR)
B. HKEY_CURRENT_CONFIG (HKCC)
C. HKEY_CURRENT_USER (HKCU)
D. HKEY_LOCAL_MACHINE (HKLM)
As a Computer Hacking Forensic Investigator, you are analysing a system with a UEFI boot process underway. You have reached the Boot Device Selection phase, and you notice that the system is attempting to load MBR boot code into memory. What can you infer from this?
A. The system is transitioning to the DXE phase
B. The system is stuck in the Pre-EFI initialization phase
C. The system follows a UEFI boot process
D. The system is going through a legacy BIOS boot process
Which of the following Windows-based tool displays who is logged onto a computer, either locally or remotely?
A. Tokenmon
B. PSLoggedon
C. TCPView
D. Process Monitor
In a virtual test environment, Michael is testing the strength and security of BGP using multiple routers to mimic the backbone of the Internet. This project will help him write his doctoral thesis on "bringing down the Internet". Without sniffing the traffic between the routers, Michael sends millions of RESET packets to the routers in an attempt to shut one or all of them down. After a few hours, one of the routers finally shuts itself down. What will the other routers communicate between themselves?
A. The change in the routing fabric to bypass the affected router
B. More RESET packets to the affected router to get it to power back up
C. RESTART packets to the affected router to get it to power back up
D. STOP packets to all other routers warning of where the attack originated
You just passed your ECSA exam and are about to start your first consulting job running security audits for a financial institution in Los Angeles. The IT manager of the company you will be working for tries to see if you remember your ECSA class. He asks about the methodology you will be using to test the company's network. How would you answer?
A. Microsoft Methodology
B. Google Methodology
C. IBM Methodology
D. LPT Methodology
What is the target host IP in the following command? c:>firewalk -F 80 10.10.150.1 172.16.28.95 -p UDP
A. 172.16.28.95
B. 10.10.150.1
C. Firewalk does not scan target hosts
D. This command is using FIN packets, which cannot scan target hosts
During an international cybercrime investigation, your team discovers an intercepted email with a sequence of special characters. Believing that the Unicode standard might have been used in encoding the message, which of the following elements could serve as the strongest indicator of this suspicion?
A. The presence of characters from multiple modern and historic scripts
B. The presence of over 128.000 different characters in the intercepted email
C. The presence of a unique number for each character, irrespective of the platform, program, and language
D. The presence of characters from a single non-English script
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive? 22,164 cylinders/disk 80 heads/cylinder 63 sectors/track
A. 53.26 GB
B. 57.19 GB
C. 11.17 GB
D. 10 GB
When obtaining a warrant, it is important to:
A. particularlydescribe the place to be searched and particularly describe the items to be seized
B. generallydescribe the place to be searched and particularly describe the items to be seized
C. generallydescribe the place to be searched and generally describe the items to be seized
D. particularlydescribe the place to be searched and generally describe the items to be seized
A forensic investigator discovers an Android smartwatch at the crime scene during an investigation. The investigator realizes the smartwatch was potentially involved in the crime, but the device associated with it was not found at the scene. What is the most suitable initial step for the investigator to retrieve meaningful data from the smartwatch?
A. The investigator should first physically dismantle the smartwatch to access its internal storage
B. The investigator should immediately turn off the smartwatch to prevent data manipulation
C. The investigator should start by understanding the smartwatch’s basic framework, including its APIs
D. The investigator should directly analyze data stored on the smartwatch using IoT forensics tools
Which of the following options will help users to enable or disable the last access time on a system running Windows 10 OS?
A. wmic service
B. Reg.exe
C. fsutil
D. Devcon
What is the primary function of the tool CHKDSK in Windows that authenticates the file system reliability of a volume?
A. Repairs logical file system errors
B. Check the disk for hardware errors
C. Check the disk for connectivity errors
D. Check the disk for Slack Space
Web browsers can store relevant information from user activities. Forensic investigators may retrieve files, lists, access history, cookies, among other digital footprints. Which tool can contribute to this task?
A. MZCacheView
B. Google Chrome Recovery Utility
C. Task Manager
D. Most Recently Used (MRU) list
During a computer hacking forensic investigation, an investigator is tasked with acquiring volatile data from a live Linux system with limited physical access. Which methodology would be the most suitable for this scenario?
A. Using Belkasoft Live RAM Capturer to extract the entire contents of the computer’s volatile memory
B. Performing remote acquisition of volatile data from a Linux machine using dd and netcat
C. Using the fmem module and dd command locally to access the RAM and acquire its content directly
D. Performing local acquisition of RAM using the LiME tool
When a user deletes a file, the system creates a $I file to store its details. What detail does the $I file not contain?
A. File Size
B. File origin and modification
C. Time and date of deletion
D. File Name
A cybersecurity forensics investigator is tasked with acquiring data from a suspect's drive for a civil litigation case. The suspect drive is 1TB, and due to time constraints, the investigator decides to prioritize and acquire only data of evidentiary value. The original drive cannot be retained. In this context, which of the following steps should the investigator prioritize?
A. Opt for disk-to-image copying for the large suspect drive
B. Execute logical acquisition considering the one-time opportunity to capture data
C. Utilize DriveSpace or DoubleSpace to reduce the data size
D. Use a reliable data acquisition tool to make a copy of the original drive
An executive has leaked the company trade secrets through an external drive. What process should the investigation team take if they could retrieve his system?
A. Postmortem Analysis
B. Real-Time Analysis
C. Packet Analysis
D. Malware Analysis
What stage of the incident handling process involves reporting events?
A. Containment
B. Follow-up
C. Identification
D. Recovery
Which of the following stand true for BIOS Parameter Block?
A. The BIOS Partition Block describes the physical layout of a data storage volume
B. The BIOS Partition Block is the first sector of a data storage device
C. The length of BIOS Partition Block remains the same across all the file systems
D. The BIOS Partition Block always refers to the 512-byte boot sector
A law enforcement officer may only search for and seize criminal evidence with _______________________, which are facts or circumstances that would lead a reasonable person to believe a crime has been committed or is about to be committed, evidence of the specific crime exists and the evidence of the specific crime exists at the place to be searched.
A. Mere Suspicion
B. A preponderance of the evidence
C. Probable cause
D. Beyond a reasonable doubt
John and Hillary works at the same department in the company. John wants to find out Hillary's network password so he can take a look at her documents on the file server. He enables Lophtcrack program to sniffing mode. John sends Hillary an email with a link to Error! Reference source not found. What information will he be able to gather from this?
A. Hillary network username and password hash
B. The SID of Hillary network account
C. The SAM file from Hillary computer
D. The network shares that Hillary has permissions
Which of the following processes is part of the dynamic malware analysis?
A. Process Monitoring
B. Malware disassembly
C. Searching for the strings
D. File fingerprinting
Julie is a college student majoring in Information Systems and Computer Science. She is currently writing an essay for her computer crimes class. Julie paper focuses on white-collar crimes in America and how forensics investigators investigate the cases. Julie would like to focus the subject. Julie would like to focus the subject of the essay on the most common type of crime found in corporate America. What crime should Julie focus on?
A. Physical theft
B. Copyright infringement
C. Industrial espionage
D. Denial of Service attacks
What file structure database would you expect to find on floppy disks?
A. NTFS
B. FAT32
C. FAT16
D. FAT12
An investigator seized a notebook device installed with a Microsoft Windows OS. Which type of files would support an investigation of the data size and structure in the device?
A. APFS and HFS
B. Ext2 and Ext4
C. HFS and GNUC
D. NTFS and FAT
You are trying to locate Microsoft Outlook Web Access Default Portal using Google search on the Internet. What search string will you use to locate them?
A. allinurl:”exchange/logon.asp”
B. intitle:”exchange server”
C. locate:”logon page”
D. outlook:”search”
What will the following command accomplish in Linux? fdisk /dev/hda
A. Partition the hard drive
B. Format the hard drive
C. Delete all files under the /dev/hda folder
D. Fill the disk with zeros
What is one method of bypassing a system BIOS password?
A. Removing the processor
B. Removing the CMOS battery
C. Remove all the system memory
D. Login to Windows and disable the BIOS password
Free Access Full 312-49V10 Practice Test Free Questions
If you’re looking for more 312-49V10 practice test free questions, click here to access the full 312-49V10 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 312-49V10 certification journey!