300-420 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 300-420 exam? Start with our 300-420 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 300-420 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 300-420 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Refer to the exhibit. The full EIGRP routing table is advertised throughout the network. Currently, users experience data loss when any one link in the network fails. An architect must optimize the network to reduce the impact when a link fails. Which solution should the architect include in the design?
A. Run BFD on the inter links between EIGRP neighbors.
B. Summarize the access layer networks from each access layer switch toward the aggregation layer.
C. Reduce the default EIGRP hello interval and hold time.
D. Summarize the access layer networks from the aggregation layer toward the core layer.
What are two valid scaling techniques when an EIGRP network is designed that consists of more than 1000 routers? (Choose two.)
A. Use structured hierarchical topology with route summarization
B. Used sub-second timers
C. Use the distribute-list command to filter routes
D. Modify delay parameters on the links
E. Implement multiple EIGRP autonomous systems
What is a benefit of using VRRPv3 as compared to VRRPv2?
A. VRRPv3 supports IPv4 and IPv6
B. VRRPv3 supports authentication
C. VRRPv3 supports preemption
D. VRRPv3 supports stateful switchover
When a network is designed using IS-IS, which two circuit types are supported? (Choose two.)
A. nonbroadcast multiaccess
B. multiaccess
C. point-to-multipoint
D. nonbroadcast
E. point-to-point
A branch office has a primary L3VPN MPLS connection back to the main office and an IPSEC VPN tunnel that serves as backup. Which design ensures that data is sent over the backup connection only if the primary MPLS circuit is down?
A. Use EIGRP to establish a neighbor relationship with the main office via L3VPN MPLS and the IPSEC VPN tunnel.
B. Use BGP with the multipath feature enabled to force traffic via the primary path when available.
C. Use static routes tied to an IP SLA to prefer the primary path while a floating static route points to the backup connection.
D. Use OSPF with a passive-interface command on the backup connection.
Which design consideration must be made when dual WAN Edge routers are deployed at a branch site?
A. Use BGP AS-path prepending to influence egress traffic and use MED to influence ingress traffic from the branch.
B. HSRP priorities must match the OMP routing policy to prefer one WAN Edge over the other.
C. Traffic must be symmetrical as it egresses the WAN Edges and returns from remote sites for DPI to function properly.
D. Configure BFD between WAN Edge routers to detect sub-second link failures.
An architect must design an IPv6 migration solution for a corporation with remote offices to support: * The customer has IPv4 peering with their service provider. * IPv6 users need access to IPv4 and IPv6 resources. * Existing content providers will migrate to IPv6 in the next two years. * Users will be migrated in a phase-by-phase approach. Which migration solution must the architect choose?
A. NAT46
B. tunneling
C. NAT64
D. dual-stack
Which nonproprietary mechanism can be used to automate rendezvous point distribution in a large PIM domain?
A. Embedded RP
B. BSR
C. Auto-RP
D. Static RP
What are three ways in which Cisco ISE learns information about devices? (Choose three.)
A. network servers the device has accessed
B. traffic generated by the device
C. RADIUS attributes
D. RPC mechanism via HTTPS
E. SMTP agents
F. user authentication to the ISE
An engineer must propose a QoS architecture model that allows an application to inform the network of its traffic profile and to request a particular type of service to support its bandwidth and delay requirements. The application requires consistent and dedicated bandwidth end to end. Which QoS architecture model meets these requirements?
A. DiffServ
B. LLQ
C. WRED
D. IntServ
Refer to the exhibit. An architect is designing a BGP solution to connect a remote branch to a service provider. There are several prefixes within the branch that the company does not want to be advertised to the Internet. Which solution should the architect use to accomplish this?
A. Attach the No-Export community with the prefixes to exclude.
B. Use the BGP No-Advertise community for the prefixes to exclude.
C. Set the BGP Internet community for all prefixes.
D. Implement the NOPEER community.
Which two techniques improve the application experience in a Cisco SD-WAN design? (Choose two.)
A. utilizing forward error correction
B. implementing a stateful application firewall
C. implementing AMP
D. utilizing quality of service
E. implementing Cisco Umbrella
An engineer must design a QoS solution for a customer that is connected to an ISP over a 1Gbps link with a 100Mbps CIR. The ISP aggressively drops all traffic received over the CIR, which is causing numerous TCP retransmissions. The customer is not using any RTP applications but wants to maximize bandwidth usage up to the CIR. Which QoS solution should the engineer choose?
A. policing
B. queuing
C. traffic shaping
D. policer with markdown
Which two statements describes Cisco SD-Access? (Choose two.)
A. software-defined segmentation and policy enforcement based on user identity and group membership
B. an overlay for the wired infrastructure in which traffic is tunneled via a GRE tunnel to a mobility controller for policy and application visibility
C. an automated encryption/decryption engine for highly secured transport requirements
D. programmable overlays enabling network virtualization across the campus
E. a collection of tools and applications that are a combination of loose and tight coupling
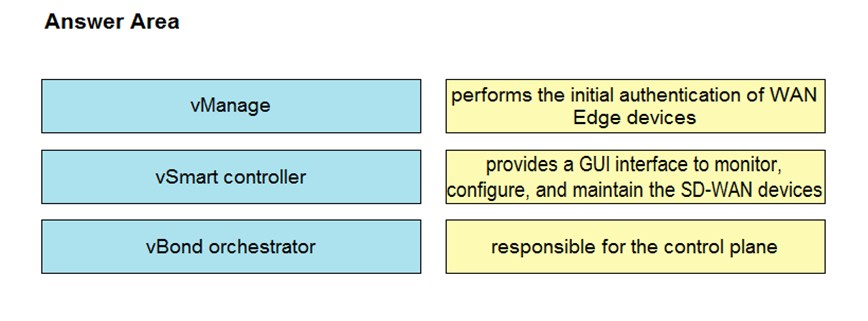
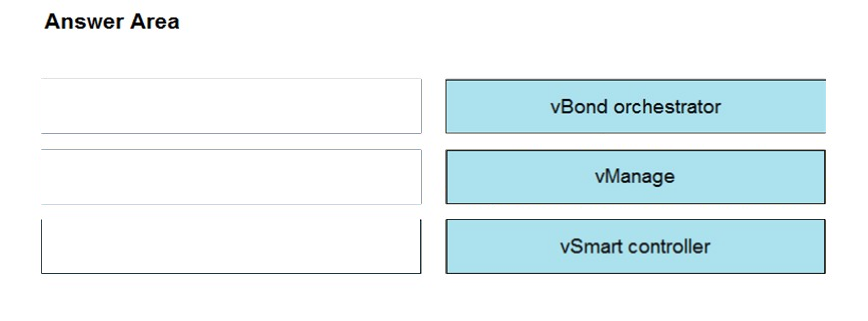
DRAG DROP - Drag and drop the elements from the left onto the functions they perform in the Cisco SD-WAN architecture on the right. Select and Place:
Refer to the exhibit.Which process does the Ethernet LMI protocol follow that is defined by the MEF 16 Technical Specification?
A. broadcasts multicast network routes from the CE to the PE
B. notifies the CE of the availability state of a configured EVC
C. communicates ENI and EVC attributes to the CE
D. broadcasts to all subnets from the CE when an EVC is added
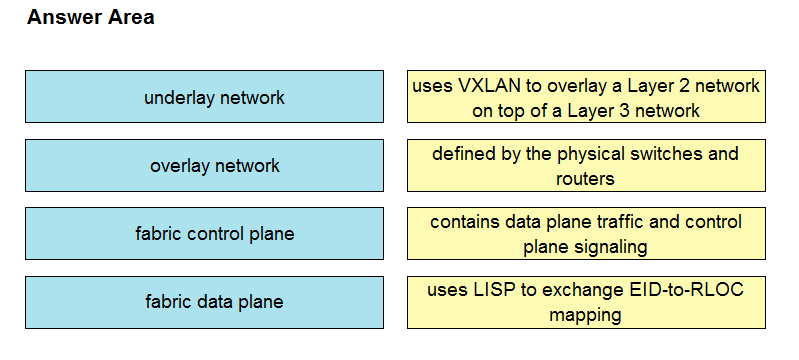
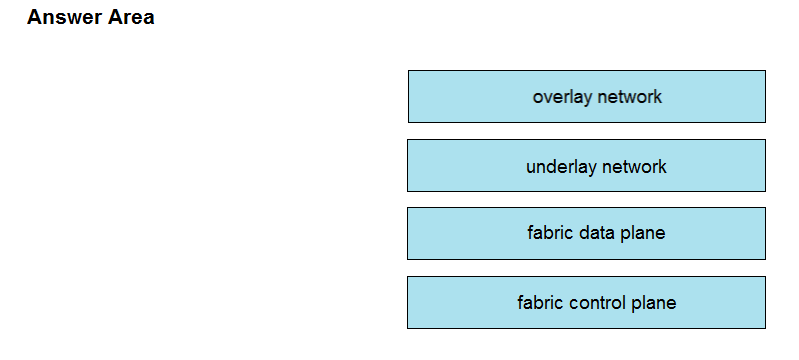
DRAG DROP - Drag and drop the components in a Cisco SD-Access architecture from the left onto their descriptions on the right. Select and Place:
An architect is designing a network that will utilize the spanning tree protocol to ensure a loop-free topology. The network will support an engineering environment where it is necessary for end-users to connect their own network switches for testing purposes. Which feature should the architect include in the design to ensure the spanning-tree topology is not affected by these rogue switches?
A. BPDU Skew Detection
B. BPDU guard
C. loop guard
D. root guard
Refer to the exhibit.An architect must design an IGP solution for an enterprise customer. The design must support: ✑ Physical link flaps should have minimal impact. ✑ Access routers should converge quickly after a link failure. Which two ISIS solutions should the architect include in the design? (Choose two.)
A. Use BGP to IS-IS redistribution to advertise all Internet routes in the Level 1 area.
B. Advertise the IS-IS interface and loopback IP address toward the Internet and data center.
C. Reduce SPF and PRC intervals to improve convergence time.
D. Configure all access and aggregate routers to establish Level 1 / Level 2 adjacencies across the network.
E. Configure access routers to establish a Level 1 adjacency and aggregate routers to establish a Level 1 / Level 2 adjacency.
Which design consideration must be made when using IPv6 overlay tunnels?
A. Overlay tunnels that connect isolated IPv6 networks are considered a final IPv6 network architecture.
B. Overlay tunnels should only be considered as a transition technique toward a permanent solution.
C. Overlay tunnels should be configured only between border devices and require only the IPv6 protocol stack.
D. Overlay tunneling encapsulates IPv4 packets in IPv6 packets for delivery across an IPv6 infrastructure.
Refer to the exhibit. An architect reviews the low-level design of a company's enterprise network and advises optimizing the STP convergence time. Which functionality must be applied to Gi1/0/1-10 to follow the architect's recommendation?
A. UplinkFast
B. root guard
C. BPDU guard
D. PortFast
An engineer must establish a direct connection between two remote offices. The new connection must be established using a logical path, share a common broadcast domain, connect over private WAN, and have as little overhead as possible. Which technology must the engineer choose?
A. GRE
B. L2VPN
C. GET VPN
D. IPsec
A company is using OSPF between its HQ location and a branch office. HQ is assigned area 0 and the branch office is assigned area 1. The company purchases a second branch office, but due to circuit delays to HQ, it decides to connect the new branch office to the existing branch office as a temporary measure. The new branch office is assigned to area 2. Which OSPF configuration enables all three locations to exchange routes?
A. The existing branch office must be configured as a stub area
B. A virtual link must be configured between the new branch office and HQ
C. A sham link must be configured between the new branch office and HQ
D. The new branch office must be configured as a stub area
Refer to the exhibit. The distribution switches serve as the Layer 3 boundary. HSRP preemption is enabled. When the primary switch comes back after a failure, traffic is initially dropped. Which solution must be implemented to improve the design?
A. Increase the hello timers on both HSRP devices.
B. Use the preempt delay feature on the backup HSRP device.
C. Use the preempt delay feature on the primary HSRP device.
D. Configure a higher mac-refresh interval on both HSRP devices.
An architect must develop a campus network solution that includes: ✑ logically segmented and isolated networks ✑ ability to communicate between network segments when required ✑ support for overlapping IP addresses ✑ widely available technologies to avoid purchasing specialized equipment Which solution must the architect select?
A. VSS with IGP
B. 802.1Q with HSRP
C. vPC with HSRP
D. VRF-Lite with OSPF
Which feature of Cisco SD-WAN Secure Direct Cloud Access divides user traffic into different zones and VPNs or VRFs?
A. application-awareness routing
B. perimeter control
C. centralized data policy
D. secure segmentation
An engineer is working for a large cable TV provider that requires multiple sources streaming video on different channels using multicast with no rendezvous point. Which multicast protocol meets these requirements?
A. PIM-SM
B. PIM-SSM
C. any-source multicast
D. BIDIR-PIM
Which option will help build your customers platform during the discovery phase?
A. detailed design
B. high-level design
C. PO
D. POV report
E. business case
When designing interdomain multicast, which two protocols are deployed to achieve communication between multicast sources and receivers? (Choose two.)
A. IGMPv2
B. BIDIR-PIM
C. MP-BGP
D. MSDP
E. MLD
In the SD-WAN underlay network, which WAN Edge VPN ID is defined as the transport VPN and is used to carry control traffic?
A. VPN 0
B. VPN 512
C. VPN 128
D. VPN 256
A company must automate a set of complex changes aligned with DR testing in the network. These changes are specific, and the DR playbook will be adjusted in the future. The playbook has diverse routing and switching assets in scope as well as multiple vendor and hardware platforms. A developer will create a thin, web front-end microservice and integrate with an Open Daylight controller to push changes to the network. Which YANG model should be used?
A. Use an open YANG model to allow the reuse of code and standardize the implementation across platforms.
B. Develop an individualized YANG model to minimize development resources and time to market.
C. Use multiple native vendor YANG models to provide code consistency.
D. Use a single native vendor YANG model to minimize development time.
Refer to the exhibit. Area 10 is a regular OSPF area, and networks 10.1.1.0/24 and 172.16.1.0/24 are internal. Which design provides optimal routing between both networks when the link between routers C and E fails?
A. Move the link between routers C and D to area 10.
B. Create an OSPF virtual link between routers E and F.
C. Create a tunnel between routers E and F in area 10.
D. Make area 10 a not-so-stubby area.
Refer to the exhibit. All routers currently reside in OSPF area 0. The network manager recently used R1 and R2 as aggregation routers for remote branch locations and R3 and R4 as aggregation routers for remote office locations. The network has since been suffering from outages, which are causing frequent SPF runs. To enhance stability and introduce areas to the OSPF network with the minimal number of ABRs possible, which two solutions should the network manager recommend? (Choose two.)
A. a new OSPF area for R1 and R2 connections, with R1 and R2 as ABRs
B. a new OSPF area for R3 and R4 connections, with R5 and R6 as ABRs
C. a new OSPF area for R3 and R4 connections, with R3 and R4 as ABRs
D. a new OSPF area for R1, R2, R3, and R4 connections, with R1, R2, R3, and R4 as ABRs
E. a new OSPF area for R1 and R2 connections, with R5 and R6 as ABRs
Which two activities should occur during an SE’s demo process? (Choose two.)
A. asking the customer to provide network drawings or white board the environment for you.
B. highlighting opportunities that although not currently within scope would result in lower operational costs and complexity.
C. identifying which capabilities require demonstration.
D. determining whether the customer would like to dive deeper during a follow-up.
E. leveraging a company such as Complete Communications to build a financial case.
Which Cisco product were incorporated into Cisco ISE between ISE releases 2.0 and 2.3?
A. Cisco ESA
B. Cisco ASA
C. Cisco ACS
D. Cisco WSA
What are the three foundational elements required for the new operational paradigm? (Choose three.)
A. application QoS
B. policy-based automated provisioning of network
C. multiple technologies at multiple OSI layers
D. assurance
E. centralization
F. fabric
The customer solution requires QoS to support streaming multimedia over a WAN. An architect chooses to use Per-Hop Behavior. Which solution should the engineer use to classify and mark traffic traveling between branch sites?
A. CBWFQ with DSCP AF2
B. LLQ with DSCP EF
C. CBWFQ with DSCP AF3
D. LLQ with DSCP AF4
Refer to the exhibit. A network engineer must design a BGP solution based on: • The route reflector must have one or more direct physical connections to the core routers (R3 and R4). • The route reflector must have full redundancy and avoid a single point of failure. • R2 to R1 link utilization is 90%, and the remaining links are less than 50% utilized. Which two solutions must the design include? (Choose two.)
A. Configure R1 to be a client of R2 and R4.
B. Configure R5 to be a client of R3 and R4
C. Configure R2 to be a client of R1 and R4.
D. Configure R3 to be a client of R2 and R4.
E. Configure R4 to be a client of R1 and R3.
Refer to the exhibit. An architect must design a solution to connect the two ASs. To optimize bandwidth, the design will implement load sharing between router R6 and router R1. Which solution should the design include?
A. Use update-source to specify the Loopback interface.
B. Use next-hop-self attributes only for routes that are learned from eBGP peers.
C. Configure the eBGP TTL to support eBGP multihop.
D. Use maximum-paths to install multiple paths in the routing table.
Which routes does the overlay management protocol advertise in an SD-WAN overlay?
A. underlay, MPLS, and overlay
B. primary, backup, and load-balanced
C. prefix, TLOC, and service
D. Internet, MPLS, and backup
What is the purpose of a TLOC extension in a Cisco SD-WAN network fabric?
A. to facilitate WAN Edge router redundancy within a site
B. to identify the physical interface where a WAN Edge router connects to the WAN transport network
C. to expand the number of colors that are potentially applied to a network transport interface
D. to aggregate multiple physical Interfaces into a single logical interface
A company uses cloud-based applications for voice and video calls, file sharing, content sharing, and messaging. During business hours, these applications randomly become slow and unresponsive. However, other applications work smoothly with the current applied QoS polices. Which solution must the company choose to resolve the issue?
A. Identify the applications with NBAR2 and allocate the required bandwidth accordingly.
B. Identify the port used by each application and apply a minimum bandwidth guarantee.
C. Identify the applications and reserve the required bandwidth on the perimeter routers.
D. Identify the application ports, create groupings, and rate-limit the required bandwidth.
A company plans to transition to IPv6. They will link their IPv4 addresses to the lowest significant bits of the new Ipv6 addresses. A network administrator with an employee id: 4264:42:116 is preparing a mapping schema for the new IPv6 addresses. Which address does the 172.16.10.0/24 network translate to?
A. 2001:db8:abcd::ac10:a00/120
B. 2001:db8:abcd:172:16:10::/96
C. 2001:db8:abcd:11d8:a00/120
D. 2001:db8:ac10:0a00::/64
An engineer is upgrading a company's main site to include a connection to a second ISP. The company will receive full Internet routing tables from both ISPs via BGP. The engineer must ensure that the company does not become a transit autonomous system. Which solution should be included in this design?
A. Tag incoming routes from both ISPs with BGP community no-export.
B. Lower the MED for updates sent to the secondary ISP.
C. Use a route-map to prevent all prefixes from being advertised to either ISP.
D. Modify the local-preference for routes incoming from the primary ISP.
An engineer is designing a QoS policy that queues excess packets for later transmission. Which mechanism must be included in the design?
A. shaping
B. WRED
C. policing
D. RED
In a cisco SD-Access brownfield deployment scenario, which configuration deployment must be taken with Cisco DNA center?
A. Subnet stretching
B. LAN automation
C. Automated UNDERLAY
D. Manual underlay
An engineer is working with NETCONF and Cisco NX-OS based devices. The engineer needs a YANG model that supports a specific feature relevant only to Cisco NX-OS. Which model should the engineer choose?
A. Native
B. IEEE
C. OpenConfig
D. IETF
Which function do reverse path forwarding mechanisms perform in a multicast deployment?
A. They send PIM prune message toward multicast sources.
B. They prevent loops and duplicate packets.
C. They eliminate overlapping multicast addresses.
D. They notify the upstream router of multicast traffic.
Refer to the exhibit.A network engineer is designing a network for AS100. The design should ensure that all traffic enters AS100 via link 1 unless there is a network failure. In the event of a failure, link 2 should function as the path for incoming traffic. Which solution should the design include?
A. Modify the next-hop attribute on R3.
B. Use AS-Path prepending on R3.
C. Modify the next-hop attribute on R4.
D. Use AS-Path prepending on R4.
Which topology within a network underlay eliminates the need for first hop redundancy protocols while improving fault tolerance, increasing resiliency, and simplifying the network?
A. virtualized topology
B. routed access topology
C. Layer 2 topology
D. logical fabric topology
Free Access Full 300-420 Practice Test Free Questions
If you’re looking for more 300-420 practice test free questions, click here to access the full 300-420 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-420 certification journey!