220-1102 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 220-1102 exam? Start with our 220-1102 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 220-1102 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 220-1102 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Which of the following is a proprietary Cisco AAA protocol?
A. TKIP
B. AES
C. RADIUS.
D. TACACS+
A technician is setting up a SOHO router in a user's home. The user wants the router to be configured to prevent access to malicious content and apply internet access protection. Which of the following settings should the technician configure?
A. Port forwarding
B. Content filtering
C. Firmware updates
D. DHCP reservations
A technician receives a help desk ticket from a user who is unable to update a phone. The technician investigates the issue and notices the following error message: insuficient storage space. While analyzing the phone, the technician does not discover any third-party applications or photos. Which of the following is the best way to resolve the issue?
A. Exchange the device for a newer one.
B. Upgrade the onboard storage.
C. Allocate more space by removing factory applications.
D. Move factory applications to external memory.
A technician needs to perform after-hours service starting at 10:00 p.m. The technician is currently 20 minutes late. The customer will also be late. Which of the following should the technician do considering proper communication techniques and professionalism?
A. Do not notify the customer if arriving before the customer.
B. Dismiss the customer and proceed with the after-hours work.
C. Contact the customer if the technician is arriving late.
D. Disclose the experience via social media
Which of the following is the MOST basic version of Windows that includes BitLocker?
A. Home
B. Pro
C. Enterprise
D. Pro for Workstations
Which of the following is the STRONGEST wireless configuration?
A. WPS
B. WPA3
C. WEP
D. WMN
SIMULATION A user reports that after a recent software deployment to upgrade applications, the user can no longer use the Testing program. However, other employees can successfully use the Testing program. INSTRUCTIONS Review the information in each tab to verify the results of the deployment and resolve any issues discovered by selecting the: · Index number of the Event Viewer issue · First command to resolve the issue · Second command to resolve the issue If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.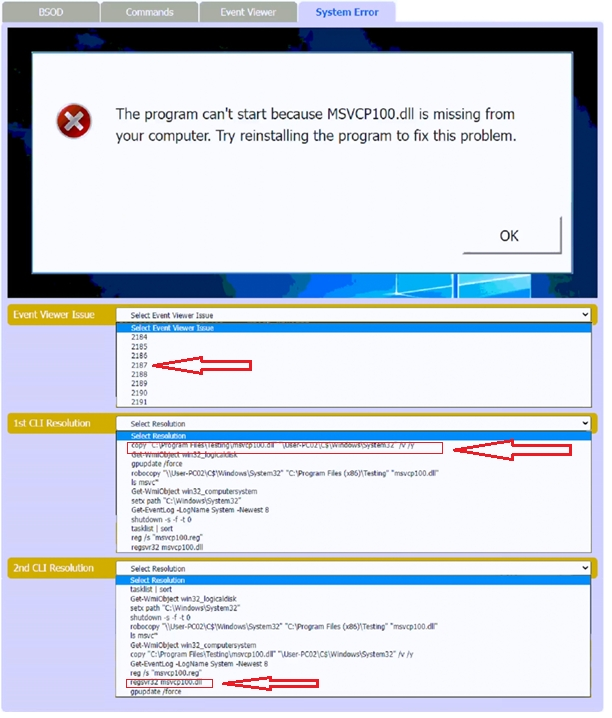
A technician is creating a full inventory of the company's IT hardware. Which of the following should the technician use for documentation management?
A. Checklist for new user setup
B. User information
C. Asset tags and IDs
D. Procurement life cycle
A user has a license for an application that is in use on a personal home laptop. The user approaches a systems administrator about using the same license on multiple computers on the corporate network. Which of the following BEST describes what the systems administrator should tell the user?
A. Use the application only on the home laptop because it contains the initial license.
B. Use the application at home and contact the vendor regarding a corporate license.
C. Use the application on any computer since the user has a license.
D. Use the application only on corporate computers.
Which of the following is used as a password manager in the macOS?
A. Terminal
B. FileVault
C. Privacy
D. Keychain
Which of the following command-line tools will delete a directory?
A. md
B. del
C. dir
D. rd
E. cd
A technician has verified that a user's computer has a virus, and the antivirus software is out of date. Which of the following steps should the technician take NEXT?
A. Quarantine the computer.
B. Use a previous restore point.
C. Educate the end user about viruses.
D. Download the latest virus definitions.
A system dives nearly full, and a technician needs to free up some space. Which of the following tools should the technician use?
A. Disk Cleanup
B. Resource Monitor
C. Disk Defragment
D. Disk Management
A remote user's smartphone is performing very slowly. The user notices that the performance improves slightly after rebooting but then reverts back to performing slowly. The user also notices that the phone does not get any faster after connecting to the company's corporate guest network. A technician sees that the phone has a large number of applications installed on it. Which of the following is the most likely cause of the issue?
A. The user is in a poor signal area.
B. The user has too many processes running.
C. The smartphone has malware on it.
D. The smartphone has been jailbroken.
A network technician is deploying a new machine in a small branch office that does not have a DHCP server. The new machine automatically receives the IP address of 169.254.0.2 and is unable to communicate with the rest of the network. Which of the following would restore communication?
A. Static entry
B. ARP table
C. APIPA address
D. NTP specification
An architecture rm is considering upgrading its computer-aided design (CAD) software to the newest version that forces storage of backups of all CAD files on the software's cloud server. Which of the following is MOST likely to be of concern to the IT manager?
A. All updated software must be tested with all system types and accessories.
B. Extra technician hours must be budgeted during installation of updates.
C. Network utilization will be significantly increased due to the size of CAD files.
D. Large update and installation files will overload the local hard drives.
A user's smartphone data usage is well above average. The user suspects an installed application is transmitting data in the background. The user would like to be alerted when an application attempts to communicate with the internet. Which of the following BEST addresses the user's concern?
A. Operating system updates
B. Remote wipe
C. Antivirus
D. Firewall
A user reports that an air-gapped computer may have been infected with a virus after the user transferred files from a USB drive. The technician runs a computer scan with Windows Defender but does not find an infection. Which of the following actions should the technician take next? (Choose two.)
A. Examine the event logs
B. Connect to the network
C. Document the findings
D. Update the definitions
E. Reimage the computer
F. Enable the firewall
A company is experiencing a DDoS attack. Several internal workstations are the source of the traffic. Which of the following types of infections are the workstations most likely experiencing? (Choose two.)
A. Zombies
B. Keylogger
C. Adware
D. Botnet
E. Ransomware
F. Spyware
A user needs assistance installing software on a Windows PC but will not be in the office. Which of the following solutions would a technician MOST likely use to assist the user without having to install additional software?
A. VPN
B. MSRA
C. SSH
D. RDP
A department has the following technical requirements for a new application: Quad Core processor - 250GB of hard drive space 6GB of RAM Touch screens - The company plans to upgrade from a 32-bit Windows OS to a 64-bit OS. Which of the following will the company be able to fully take advantage of after the upgrade?
A. CPU
B. Hard drive
C. RAM
D. Touch screen
A small business owner wants to install newly purchased software on all networked PCs. The network is not configured as a domain, and the owner wants to use the easiest method possible. Which of the following is the MOST efficient way for the owner to install the application?
A. Use a network share to share the installation files.
B. Save software to an external hard drive to install.
C. Create an imaging USB for each P
D. Install the software from the vendor’s website.
A technician is setting up a desktop computer in a small office. The user will need to access files on a drive shared from another desktop on the network. Which of the following configurations should the technician employ to achieve this goal?
A. configure the network as private.
B. Enable a proxy server.
C. Grant the network administrator role to the user.
D. Create a shortcut to public documents.
A call center technician receives a call from a user asking how to update Windows. Which of the following describes what the technician should do?
A. Have the user consider using an iPad if the user is unable to complete updates.
B. Have the user text the user’s password to the technician.
C. Ask the user to click in the Search field, type Check for Updates, and then press the Enter key.
D. Advise the user to wait for an upcoming, automatic patch.
A technician is working to resolve a Wi-Fi network issue at a doctor's office that is located next to an apartment complex. The technician discovers that employees and patients are not the only people on the network. Which of the following should the technician do to BEST minimize this issue?
A. Disable unused ports.
B. Remove the guest network.
C. Add a password to the guest network.
D. Change the network channel
Which of the following authentication types is the most secure?
A. WPA3
B. WEP
C. RADIUS
D. TACACS+
E. WPS
A user reports being unable to access a sports team's website on an office computer. The administrator tells the user this blocked access is intentional and based on company guidelines. Which of the following is the administrator referring to?
A. NDA
B. AUP
C. VPN
D. SOP
A technician installs specialized software on a workstation. The technician then attempts to run the software. The workstation displays a message indicating the software is not authorized to run. Which of the following should the technician do to most likely resolve the issue?
A. Install the software in safe mode.
B. Attach the external hardware token.
C. Install OS updates.
D. Restart the workstation after installation
A company implemented a BYOD policy and would like to reduce data disclosure caused by malware that may infect these devices. Which of the following should the company deploy to address these concerns?
A. UAC
B. MDM
C. LDAP
D. SSO
A technician is working on a Windows 10 PC that has unwanted applications starting on boot. Which of the following tools should the technician use to disable applications on startup?
A. System configuration
B. Task Manager
C. Performance Monitor
D. Group Policy Editor
A technician needs to transfer a large number of files over an unreliable connection. The technician should be able to resume the process if the connection is interrupted. Which of the following tools can be used?
A. sfc
B. chkdsk
C. git clone
D. robocopy
A user reports a PC is running slowly. The technician suspects high disk I/O. Which of the following should the technician perform NEXT?
A. resmon.exe
B. msconfig.exe
C. dfrgui.exe
D. msinfo32.exe
A user's iPhone was permanently locked alter several failed login attempts. Which of the following will restore access to the device?
A. Fingerprint and pattern
B. Facial recognition and PIN code
C. Primary account and password
D. Secondary account and recovery code
A call center handles inquiries into billing issues for multiple medical facilities. A security analyst notices that call center agents often walk away from their workstations, leaving patient data visible for anyone to see. Which of the following should a network administrator do to BEST prevent data theft within the call center?
A. Encrypt the workstation hard drives.
B. Lock the workstations after five minutes of inactivity.
C. Install privacy screens.
D. Log off the users when their workstations are not in use.
A mobile phone user has downloaded a new payment application that allows payments to be made with a mobile device. The user attempts to use the device at a payment terminal but is unable to do so successfully. The user contacts a help desk technician to report the issue. Which of the following should the technician confirm NEXT as part of the troubleshooting process?
A. If airplane mode is enabled
B. If Bluetooth is disabled
C. If NFC is enabled
D. If Wi-Fi is enabled
E. If location services are disabled
A computer technician is investigating a computer that is not booting. The user reports that the computer was working prior to shutting it down last night. The technician notices a removable USB device is inserted, and the user explains the device is a prize the user received in the mail yesterday. Which of the following types of attacks does this describe?
A. Phishing
B. Dumpster diving
C. Tailgating
D. Evil twin
A user reports that a workstation is operating sluggishly. Several other users operate on the same workstation and have reported that the workstation is operating normally. The systems administrator has validated that the workstation functions normally. Which of the following steps should the systems administrator most likely attempt NEXT?
A. Increase the paging file size.
B. Run the chkdsk command.
C. Rebuild the user’s profile.
D. Add more system memory.
E. Defragment the hard drive.
A technician needs to configure security settings on a Windows 10 workstation. Which of the following should the technician configure to limit password attempts?
A. Account Lockout Policy
B. User Access Control
C. System Protection
D. Firewall
Which of the following data is MOST likely to be regulated?
A. Name in a phone book
B. Name on a medical diagnosis
C. Name on a job application
D. Name on an employer’s website
A PC is taking a long time to boot. Which of the following operations would be best to do to resolve the issue at a minimal expense? (Choose two.)
A. Installing additional RAM
B. Removing the applications from startup
C. Installing a faster SSD
D. Running the Disk Cleanup utility
E. Defragmenting the hard drive
F. Ending the processes in the Task Manager
A company is recycling old hard drives and wants to quickly reprovision the drives for reuse. Which of the following data destruction methods should the company use?
A. Degaussing
B. Standard formatting
C. Low-level wiping
D. Deleting
A user attempts to open some files, but a message appears stating that the files are encrypted. The user was able to access these files before without receiving this message, and no changes have been made within the company. Which of the following has infected the computer?
A. Cryptominer
B. Phishing
C. Ransomware
D. Keylogger
A technician is familiar with most personnel at a customer's location and has clearance to work unsupervised. Which of the following describes how the technician should handle personal communication while on site?
A. Respond to calls and text messages while on site but not when working directly with personnel.
B. Respond to calls and text messages only from family.
C. Respond to calls and text messages only when an emergency situation requires a response.
D. Respond to calls and text messages discreetly while on site.
Which of the following should be used to secure a device from known exploits?
A. Encryption
B. Remote wipe
C. Operating system updates
D. Cross-site scripting
A user is receiving repeated pop-up advertising messages while browsing the internet. A malware scan is unable to locate the source of an infection. Which of the following should the technician check NEXT?
A. Windows updates
B. DNS settings
C. certificate store
D. Browser plug-ins
A user's mobile phone has become sluggish. A systems administrator discovered several malicious applications on the device and reset the phone. The administrator installed MDM software. Which of the following should the administrator do to help secure the device against this threat in the future? (Choose two.)
A. Prevent a device root.
B. Disable biometric authentication.
C. Require a PIN on the unlock screen.
D. Enable developer mode.
E. Block a third-party application installation.
F. Prevent GPS spoofing.
Following the latest Windows update, PDF files are opening in Microsoft Edge instead of Adobe Reader. Which of the following utilities should be used to ensure all PDF files open in Adobe Reader?
A. Network and Sharing Center
B. Programs and Features
C. Default Apps
D. Add or Remove Programs
A user is configuring a new SOHO Wi-Fi router for the first time. Which of the following settings should the user change FIRST?
A. Encryption
B. Wi-Fi channel
C. Default passwords
D. Service set identifier
Which of the following is the MOST cost-effective version of Windows 10 that allows remote access through Remote Desktop?
A. Home
B. Pro for Workstations
C. Enterprise
D. Pro
A user has requested help setting up the fingerprint reader on a Windows 10 laptop. The laptop is equipped with a fingerprint reader and is joined to a domain. Group Policy enables Windows Hello on all computers in the environment. Which of the following options describes how to set up Windows Hello Fingerprint for the user?
A. Navigate to the Control Panel utility, select the Security and Maintenance submenu, select Change Security and Maintenance settings, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
B. Navigate to the Windows 10 Settings menu, select the Accounts submenu, select Sign-in options, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
C. Navigate to the Windows 10 Settings menu, select the Update & Security submenu, select Windows Security, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
D. Navigate to the Control Panel utility, select the Administrative Tools submenu, select the user account in the list, select Windows Hello Fingerprint, and have the user place a fingerprint on the fingerprint reader repeatedly until Windows indicates setup is complete.
Free Access Full 220-1102 Practice Test Free Questions
If you’re looking for more 220-1102 practice test free questions, click here to access the full 220-1102 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 220-1102 certification journey!

