200-301 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 200-301 exam? Start with our 200-301 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 200-301 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 200-301 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
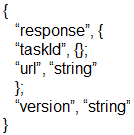
Which output displays a JSON data representation? A.B.
C.
D.
Which SDN plane forwards user-generated traffic?
A. Management plane
B. Control plane
C. Policy plane
D. Data plane
What is a benefit of using private IPv4 addressing?
A. Multiple companies can use the same addresses without conflicts.
B. Direct connectivity is provided to internal hosts from outside an enterprise network.
C. Communication to the internet is reachable without the use of NAT.
D. All external hosts are provided with secure communication to the internet.
By default, how does EIGRP determine the metric of a route for the routing table?
A. It uses the bandwidth and delay values of the path to calculate the route metric.
B. It uses a default metric of 10 for all routes that are learned by the router.
C. It counts the number of hops between the receiving and destination routers and uses that value as the metric.
D. It uses a reference bandwidth and the actual bandwidth of the connected link to calculate the route metric.
Refer to the exhibit. How will the device handle a packet destined to IP address 100.100.100.100?
A. It will always prefer the static route over dynamic routes and choose the routeS 100.100.0.0/16 [1/0] via 192.168.4.1.
B. It will choose the route with the lowest metric,R 100.0.0.0/8 [120/2] via 192.168.3.1, 00:00:13, Ethernet0/3.
C. It will choose the route with the highest metric,D 100.100.100.0/24 [90/435200] via 192.168.2.1, 00:00:13, Ethernet0/2.
D. It will choose the route with the longest match,O 100.100.100.100/32 [110/21] via 192.168.1.1, 00:05:57, Ethernet0/1.
An engineer must configure interswitch VLAN communication between a Cisco switch and a third-party switch. Which action should be taken?
A. configure DSCP
B. configure IEEE 802.1q
C. configure ISL
D. configure IEEE 802.1p
Refer to the exhibit. An engineer configured NAT translations and has verified that the configuration is correct. Which IP address is the source IP after the NAT has taken place?
A. 10.4.4.4
B. 10.4.4.5
C. 172.23.103.10
D. 172.23.104.4
DRAG DROP - Drag and drop the IPv6 address from the left onto the type on the right.
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks. • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window. • All necessary preconfigurations have been applied. • Do not change the enable password or hostname for any device. • Save your configurations to NVRAM before moving to the next item. • Click Next at the bottom of the screen to submit this lab and move to the next question. • When Next is clicked the lab closes and cannot be reopened. Topology -Tasks - All physical cabling is in place and verified. Connectivity for the Switches on ports E0/1, E0/2, and E0/3 must be configured and available for voice and data capabilities. 1. Configure Sw1 and Sw2 with both VLANS, naming them according to the VLAN Name provided in the topology. 2. Configure the E0/1, E0/2, and E0/3 ports on both switches for both VLANS and ensure that Cisco IP phones and PCs pass traffic. 3. Configure Sw1 and Sw2 to allow neighbor discovery via the vendor-neutral protocol on e0/0.
What is the primary purpose of private address space?
A. limit the number of nodes reachable via the Internet
B. simplify the addressing in the network
C. conserve globally unique address space
D. reduce network complexity
What is the role of the root port in a switched network?
A. It replaces the designated port when the designated port fails.
B. It replaces the designated port when the root port fails.
C. It is the best path to the root from a nonroot switch.
D. It is administratively disabled until a failover occurs.
Refer to the exhibit. A packet sourced from 10.10.10.1 is destined for 172.16.3.254. What is the subnet mask of the destination route?
A. 0.0.0.0
B. 255.255.254.0
C. 255.255.255.0
D. 255.255.255.255
Which port-security violation mode drops traffic from unknown MAC addresses and forwards an SNMP trap?
A. shutdown VLAN
B. protect
C. restrict
D. shutdown
Refer to the exhibit. A packet sourced from 172.18.33.2 is destined for 172.18.32.38. Where does the router forward the packet?
A. 10.1.1.1
B. 10.1.1.3
C. Loopback0
D. GigabitEthernet0/0
Which two IP addressing schemes provide internet access to users on the network while preserving the public IPv4 address space? (Choose two.)
A. IPv6 addressing
B. PAT with private internal addressing
C. single public Class A network
D. private networks only
E. custom addresses from ARIN
What is the primary function of a Layer 3 device?
A. to transmit wireless traffic between hosts
B. to analyze traffic and drop unauthorized traffic from the Internet
C. to forward traffic within the same broadcast domain
D. to pass traffic between different networks
What is a characteristic of RSA?
A. It uses preshared keys for encryption.
B. It is a public-key cryptosystem.
C. It is a private-key encryption algorithm.
D. It requires both sides to have identical keys.
An engineer must update the configuration on two PCs in two different subnets to communicate locally with each other. One PC is configured with IP address 192.168.25.128/25 and the other with 192.168.25.100/25. Which network mask must the engineer configure on both PCs to enable the communication?
A. 255.255.255.248
B. 255.255.255.224
C. 255.255.255.0
D. 255.255.255.252
Refer to the exhibit. Switch A is newly configured. All VLANs are present in the VLAN database. The IP phone and PC A on Gi0/1 must be configured for the appropriate VLANs to establish connectivity between the PCs. Which command set fulfills the requirement?
A. SwitchA(config-if)#switchport mode access SwitchA(config-if)#switchport access vlan 50 SwitchA(config-if)#switchport voice vlan 51
B. SwitchA(config-if)#switchport mode trunk SwitchA(config-if)#switchport trunk allowed vlan add 50, 51 SwitchA(config-if)#switchport voice vlan dot1p
C. SwitchA(config-if)#switchport mode trunk SwitchA(config-if)#switchport trunk allowed vlan 50, 51 SwitchA(config-if)#mis qos trust cos
D. SwitchA(config-if)#switchport mode access SwitchA(config-if)#switchport access vlan 50 SwitchA(config-if)#switchport voice vlan untagged
Aside from discarding, which two states does the switch port transition through while using RSTP (802.1w)? (Choose two.)
A. blocking
B. speaking
C. listening
D. learning
E. forwarding
Refer to the exhibit. An extended ACL has been configured and applied to router R2. The configuration failed to work as intended. Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
A. Add a ג€permit ip any anyג€ statement at the end of ACL 101 for allowed traffic.
B. Add a ג€permit ip any anyג€ statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.
Refer to the exhibit. Router R14 is in the process of being configured. Which configuration must be used to establish a host route to a PC 10?
A. ip route 10.80.65.10 255.255.255.254 10.80.65.1
B. ip route 10.80.65.10 255.255.255.255 10.73.65.66
C. ip route 10.73.65.66 0.0.0.255 10.80.65.10
D. ip route 10.73.65.66 255.0.0.0 10.80.65.10
What are the two functions of SSIDs? (Choose two.)
A. uses the maximum of 32 alphanumeric characters
B. controls the speed of the Wi-Fi network
C. used exclusively with controller-based Wi-Fi networks
D. supports a single access point
E. broadcasts by default
Which action protects a network from VLAN hopping attacks?
A. Implement port security on internet-facing VLANs.
B. Change the native VLAN to an unused VLAN ID.
C. Enable dynamic ARP inspection.
D. Configure an ACL to prevent traffic from changing VLANs.
Which two host addresses are reserved for private use within an enterprise network? (Choose two.)
A. 10.172.76.200
B. 12.17.1.20
C. 172.15.2.250
D. 172.31.255.100
E. 192.169.32.10
Refer to the exhibit. Which two values does router R1 use to determine the best path to reach destinations in network 1.0.0.0/8? (Choose two.)
A. lowest cost to reach the next hop
B. highest administrative distance
C. lowest metric
D. highest metric
E. longest prefix match
What is the purpose of classifying network traffic in QoS?
A. configures traffic-matching rules on network devices
B. services traffic according to its class
C. identifies the type of traffic that will receive a particular treatment
D. writes the class identifier of a packet to a dedicated field in the packet header
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window • All necessary preconfigurations have been applied • Do not change the enable password or hostname for any device • Save your configurations to NVRAM before moving to the next item • Click Next at the bottom of the screen to submit this lab and move to the next question • When Next is clicked the lab closes and cannot be reopened Topology -Tasks - R1 has been pre-configured with all the necessary commands. All physical cabling is in place and verified. Connectivity from PC1, PC3, and the Server must be established to the switches, and each port must only allow one VLAN. 1. Configure the VLAN connecting to the switch port for PC3 with the name "SALES" 2. Configure the switch port connecting to Server1 3. Configure the switch port connecting to PC3 4. Ensure R1 discovers SW-1 via the Cisco proprietary neighbor discovery protocol and all other devices on the network are unable to discover SW-1
Refer to the exhibit. An engineer configures interface fa0/1 on SW1 and SW2 to pass traffic from two different VLANs. For security reasons, company policy requires the native VLAN to be set to a nondefault value. Which configuration meets this requirement?
A. Switch(config-if)#switchport mode trunkSwitch(config-if)#switchport trunk encapsulation dot1qSwitch(config-if)#switchport trunk allowed vlan 100,105Switch(config-if)#switchport trunk native vlan 3
B. Switch(config-if)#switchport mode trunkSwitch(config-if)#switchport trunk encapsulation islSwitch(config-if)#switchport trunk allowed vlan 100,105Switch(config-if)#switchport trunk native vlan 1
C. Switch(config-if)#switchport mode dynamicSwitch(config-if)#switchport access vlan 100,105Switch(config-if)#switchport trunk native vlan 1
D. Switch(config-if)#switchport mode accessSwitch(config-if)#switchport trunk encapsulation dot1qSwitch(config-if)#switchport access vlan 100,105Switch(config-if)#switchport trunk native vlan 3
Refer to the exhibit. Which prefix did router R1 learn from internal EIGRP?
A. 192.168.3.0/24
B. 192.168.1.0/24
C. 172.16.1.0/24
D. 192.168.2.0/24
SIMULATION - Guidelines - This is a lab item in which tasks will be performed on virtual devices • Refer to the Tasks tab to view the tasks for this lab item. • Refer to the Topology tab to access the device console(s) and perform the tasks • Console access is available for all required devices by clicking the device icon or using the tab(s) above the console window • All necessary preconfigurations have been applied • Do not change the enable password or hostname for any device • Save your configurations to NVRAM before moving to the next item • Click Next at the bottom of the screen to submit this lab and move to the next question • When Next is clicked the lab closes and cannot be reopened Topology -Tasks - All physical cabling is in place. A company plans to deploy 16 new sites. The sites will utilize both IPv4 and IPv6 networks. 1. Subnet 10.20.0.0/16 to meet the subnet requirements and maximize the number of hosts • Using the second subnet - Assign the first usable IP address to e0/0 on Sw101 - Assign the last usable IP address to e0/0 on Sw102 2. Subnet 2001:db8::/52 to meet the subnet requirements and maximize the number of hosts • Using the second subnet - Assign an IPv6 GUA using a unique 64-Bit interface identifier on e0/0 on Sw101 - Assign an IPv6 GUA using a unique 64-Bit interface identifier on e0/0 on Sw102
Which interface on the WLC is limited to one when LAG is in use?
A. service
B. virtual
C. trunk
D. AP-manager
Refer to the exhibit. A network engineer must configure the link with these requirements: • Consume as few IP addresses as possible. • Leave at least two additional useable IP addresses for future growth. Which set of configurations must be applied?
A. R1(config-if)#ip address 10.10.10.1 255.255.255.252R2(config-if)#ip address 10.10.10.2 255.255.255.252
B. R1(config-if)#ip address 10.10.10.1 255.255.255.240R2(config-if)#ip address 10.10.10.12 255.255.255.240
C. R1(config-if)#ip address 10.10.10.1 255.255.255.248R2(config-if)#ip address 10.10.10.4 255.255.255.248
D. R1(config-if)#ip address 10.10.10.1 255.255.255.0R2(config-if)#ip address 10.10.10.5 255.255.255.0
Refer to the exhibit. PC1 regularly sends 1800 Mbps of traffic to the server. A network engineer needs to configure the EtherChannel to disable Port Channel 1 between SW1 and SW2 when the Ge0/0 and Ge0/1 ports on SW2 go down. Which configuration must the engineer apply to the switch?
A. SW2# configure terminal -SW2(config)# interface port-channel 4SW2(config-if)# port-channel min-links 2
B. SW2# configure terminal -SW2(config)# interface port-channel 4SW2(config-if)# lacp port-priority 32000
C. SW2# configure terminal -SW2(config)# interface port-channel 4SW2(config-if)# lacp max-bundle 2
D. SW2# configure terminal -SW2(config)# lacp system-priority 32000
Refer to the exhibit. Which command provides this output?
A. show ip route
B. show cdp neighbor
C. show ip interface
D. show interface
Which interface is used to send traffic to the destination network?
A. G0/10
B. G0/24
C. G0/5
D. G0/1
Refer to the exhibit. The network engineer is configuring a new WLAN and is told to use a setup password for authentication instead of the RADIUS servers. Which additional set of tasks must the engineer perform to complete the configuration?
A. Disable PMF Enable PSK Enable 802.1x
B. Select WPA Policy Enable CCKM Enable PSK
C. Select WPA Policy Select WPA2 Policy Enable FT PSK
D. Select WPA2 Policy Disable PMF Enable PSK
Which alternative to password authentication is implemented to allow enterprise devices to log in to the corporate network?
A. 90-day renewal policies
B. magic links
C. one-time passwords
D. digital certificates
DRAG DROP - Drag and drop the characteristic from the left onto the IPv6 address type on the right.
Which command implies the use of SNMPv3?
A. snmp-server user
B. snmp-server host
C. snmp-server enable traps
D. snmp-server community
What is the difference between AAA authentication and authorization?
A. Authentication identifies and verifies a user who is attempting to access a system, and authorization controls the tasks the user performs.
B. Authentication controls the system processes a user accesses, and authorization logs the activities the user initiates.
C. Authentication verifies a username and password, and authorization handles the communication between the authentication agent and the user database.
D. Authentication identifies a user who is attempting to access a system, and authorization validates the user’s password.
Which statement about VLAN configuration is true?
A. The switch must be in VTP server or transparent mode before you can configure a VLAN
B. The switch must be in config-vlan mode before you configure an extended VLAN
C. Dynamic inter-VLAN routing is supported on VLAN2 through VLAN 4064
D. A switch in VTP transparent mode save the VLAN databases to the running configuration only
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
A. enable dynamic MAC address learning
B. implement static MAC addressing
C. enable sticky MAC addressing
D. implement auto MAC address learning
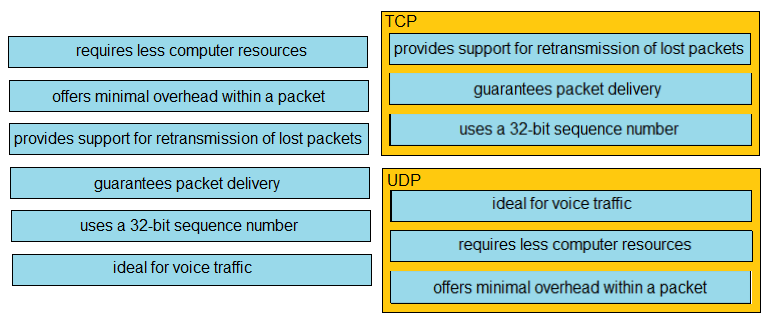
DRAG DROP - Drag and drop the characteristics of transport layer protocols from the left onto the corresponding protocols on the right. Select and Place:
DRAG DROP - Drag and drop the statements about device management from the left onto the corresponding device-management types on the right.
Which two capabilities of Cisco DNA Center make it more extensible as compared to traditional campus device management? (Choose two.)
A. REST APIs that allow for external applications to interact natively
B. adapters that support all families of Cisco IOS software
C. SDKs that support interaction with third-party network equipment
D. modular design that is upgradable as needed
E. customized versions for small, medium, and large enterprises
What is a function of Wireless LAN Controller?
A. register with a single access point that controls traffic between wired and wireless endpoints
B. use SSIDs to distinguish between wireless clients
C. send LWAPP packets to access points
D. monitor activity on wireless and wired LANs
When a switch receives a frame from an unknown source MAC address, which action does the switch take with the frame?
A. It sends the frame to ports within the CAM table identified with an unknown source MAC address.
B. It floods the frame out all interfaces, including the interface it was received on.
C. It associates the source MAC address with the LAN port on which it was received and saves it to the MAC address table.
D. It attempts to send the frame back to the source to ensure that the source MAC address is still available for transmissions.
Which enhancements were implemented as part of WPA3?
A. Forward secrecy and SAE in personal mode for secure initial key exchange
B. 802.1x authentication and AES-128 encryption
C. AES-64 in personal mode and AES-128 in enterprise mode
D. TKIP encryption improving WEP and per-packet keying
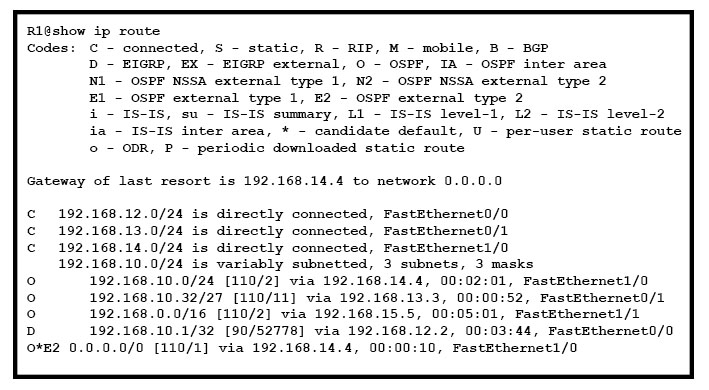
Refer to exhibit. What Administrative distance has route to 192.168.10.1?
A. 1
B. 90
C. 110
D. 120
Free Access Full 200-301 Practice Test Free Questions
If you’re looking for more 200-301 practice test free questions, click here to access the full 200-301 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 200-301 certification journey!