350-901 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 350-901 exam? Start with our 350-901 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 350-901 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 350-901 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Which action enhances end-user privacy when an application is built that collects and processes the location data from devices?
A. Use the network device serial number to encrypt the MAC address for each device.
B. Salt the MAC address for each device.
C. Implement an algorithmic information theoretic loss to the MAC address for each device.
D. Pepper the MAC address for each device.
Which two strategies are used to protect personally identifiable information? (Choose two.)
A. Encrypt data in transit.
B. Encrypt hash values of data.
C. Encrypt data at rest.
D. Only hash usernames and passwords for efficient lookup.
E. Only encrypt usernames and passwords for efficient lookup.
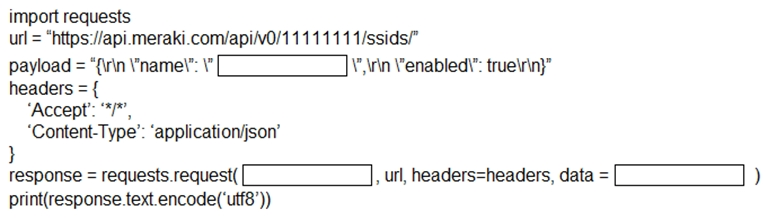
FILL BLANK - Fill in the blanks to complete the Python script to enable the SSID with a name of `371767916` in the network resource `11111111` using the Meraki Dashboard API.
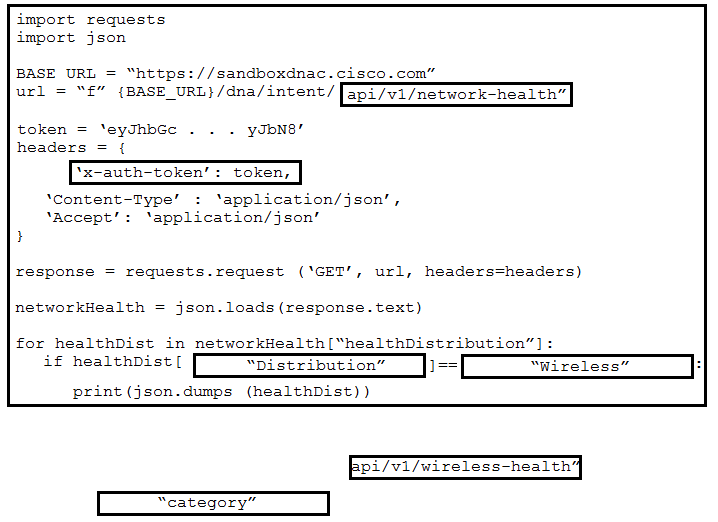
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to retrieve and display wireless network health information. The wireless network devices are being managed by Cisco DNA Center and are compatible with REST API. Not all options are used. Select and Place:

Refer to the exhibits. An application is developed to perform multiple API calls. The calls will be performed on the infrastructure devices. Delays in the information transfer occur when the application is executed. What are two reasons for the issue? (Choose two.)
A. The list devices API call is failing and does not return a result.
B. The requests are being rate limited to prevent multiple calls causing the excessive load.
C. One of the API calls takes roughly three times as long to complete.
D. Listing devices takes longer than usual due to high network latency.
E. The list devices API call is inefficient and should be refactored.
Which database type should be used to store data received from model-driven telemetry?
A. BigQuery database
B. Time series database
C. NoSQL database
D. PostgreSQL database
DRAG DROP -Refer to the exhibit. The self-service Webex bot is failing when many users attempt to interact with it at the same time. Drag and drop the code snippets from the left onto the correct item numbers on the right that match the missing sections in the exhibit to complete this code to handle this high-load situation. Select and Place:
FILL BLANK - A local Docker image has an image ID of 385001111. Fill in the blanks to complete the command in order to tag the image into the "cisco" repository with "version1.0"
The response from a server includes the header ETag: W/`7eb8b94419e371767916ef13e0d6e63d`. Which statement is true?
A. The ETag has a Strong validator directive.
B. The ETag has a Weak validator directive, which is an optional directive.
C. The ETag has a Weak validator directive, which is a mandatory directive.
D. The ETag has a Strong validator directive, which it is incorrectly formatted.
What are two steps in the OAuth2 protocol flow? (Choose two.)
A. The user is authenticated by the authorization server and granted an access token.
B. The user’s original credentials are validated by the resource server and authorization is granted.
C. The user indirectly requests authorization through the authorization server.
D. The user requests an access token by authentication and authorization grant presentation.
E. The user requests the protected resource from the resource server using the original credentials.
Refer to the exhibit. An architect wrote an application to collect device information from the Cisco Meraki Dashboard API. Every time a network change occurs the application collects information and records new endpoint MAC addresses. The application stopped working after the locations and network equipment of a competitor were acquired. Which application approach must be applied to reduce latency and rate limiting?
A. MOS scoring system before collecting information
B. leaky faucet algorithm for fault categorizing
C. error handling to check for reachability first
D. webhooks to trigger updates
DRAG DROP -Refer to the exhibit. Drag and drop the components from the Oauth2 authorization protocol flow on the left onto the letter that matches the location in the exhibit.
Refer to the exhibit. The cisco_devnet Docker swarm service runs across five replicas. The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container. There must be no service outages during the upgrade process. Which two design approaches must be used? (Choose two.)
A. Enable parallel upgrades by using the docker service update command.
B. Ensure that the service is hosted behind a VIP with no session persistence.
C. Ensure that the service replicas are set to a minimum of 5.
D. Update the restart policy of the containers to restart upon failure.
E. Implement rolling upgrades by using the docker service update command.
Which action reduces latency in a microservices application?
A. Run microservices at the edge, on the periphery of the network.
B. Merge microservices that communicate frequently with each other into a single microservice.
C. Build the microservices to use a stateful design.
D. Minimize HTTP header metadata on the request.
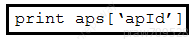
Refer to the exhibit. A Python developer is creating a wireless network device inventory application for local deployment of Cisco access points. The developer is retrieving an access point ID by using a REST API. The output indicates that there was a KeyError when parsing the JSON response. What returns the expected output of 266 at line 14? A.
B.
C.
D.
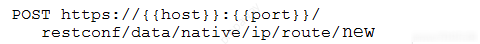
Refer to the exhibit. The information in the exhibit was obtained by using RESTCONF and querying URI /restconf/data/native/ip/route. Which RESTCONF call and which JSON code is used to add a new IP route to a network of 172.30.200.0/24 through the GigabitEthernet2 interface? (Choose two.) A.
B.
C.
D.
E.
F.
Refer to the exhibit. A developer is creating an application to be used in the current network. The application must be compatible with the network devices and platforms. Based on the design and performance, it must be flexible to modifications and future installations. What are two characteristics of the Python application? (Choose two.)
A. The application design maximizes scalability.
B. Config.py contains code related specifically to the Cisco DNA Center Discovery REST API.
C. The application supports only version 2.1.2 of the Cisco DNA Center API.
D. The application design enables code reuse.
E. Discovery.py contains code related specifically to the Cisco DNA Center Discovery REST API.
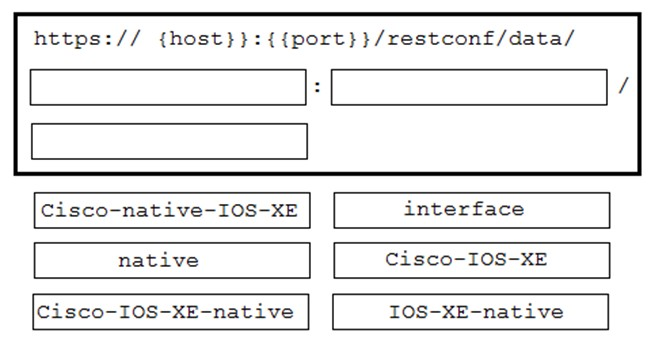
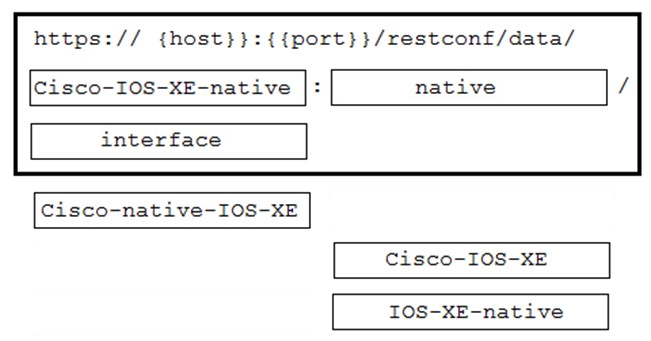
Refer to the exhibit. Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A.

B.

C.

D.

DRAG DROP -Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow. Select and Place:
A developer has created a fix for an application bug with the ID a98453928854x and has installed it on a Cisco Catalyst 9300 series switch. Which command will enable the application called devcorapp?
A. app-hosting start appid devcorapp
B. app-hosting install package usbflash1:devcorapp.tar
C. app-hosting run re-start appid devcorapp bugfix
D. app-hosting activate appid devcorapp
In the three-legged OAuth2 process, after the authorization server presents a form to the resource owner to grant access, what is the next step?
A. The resource owner authenticates and optionally authorizes with the authorization server.
B. The user who owns the resource initiates a request to the OAuth client.
C. If the resource owner allows access, the authorization server sends the OAuth client a redirection.
D. A form to allow or restrict access is submitted by the owner of the resource.
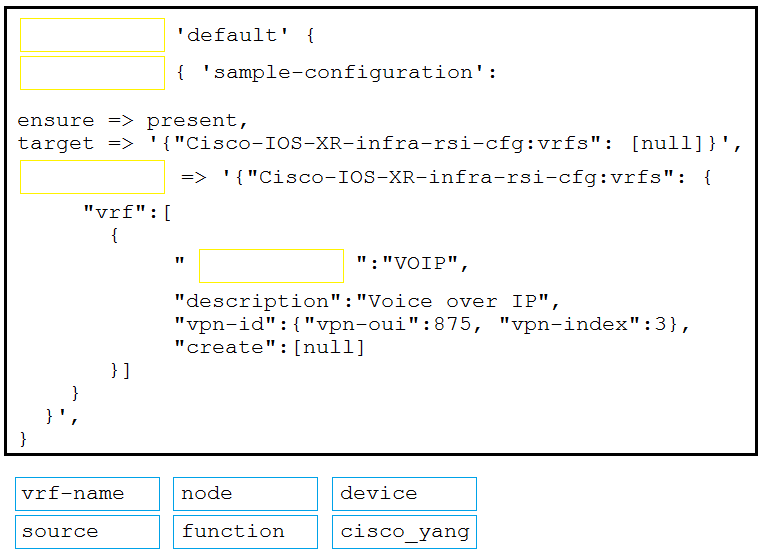
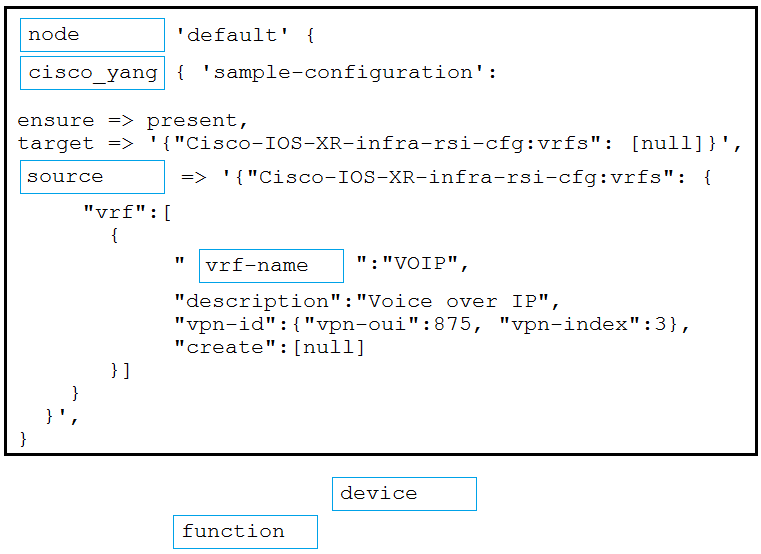
Refer to the exhibit. The YAML represented is using the ios_vrf module. As part of the Ansible playbook workflow, what is the result when this task is run?
A. VRFs not defined in the host_vars file are removed from the device.
B. VRFs not defined in the host_vars file are added to the device, and any other VRFs on the device remain.
C. VRFs defined in the host_vars file are removed from the device.
D. VRFs are added to the device from the host_vars file, and any other VRFs on the device are removed.
How does the use of release packaging allow dependencies to be effectively managed during deployments?
A. removal of release units if they have issues in testing
B. dependencies are tested after the release is deployed
C. designed to prevent any dependencies between release units
D. dependencies are staggered between multiple releases
Refer to the exhibit. An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?
A. {item[“name”]}’
B. {item[“name”]}/ip/address/primary’
C. {item[“name”]}/ip/address
D. {item[“name”]} /ip
Refer to the exhibit. A developer created a Python script to retrieve information about Meraki devices in a local network deployment. After requesting a security review of the code, the security analyst has observed poor secret storage practices. What is the appropriate secret storage approach?
A. Set an OS environment variable for MER_API_KEY to the API key before running the code and no longer set MER_API_KEY within the code.
B. Leverage an external secret vault to retrieve MER_API_KEY and set the vault key as an OS environment variable before running the code.
C. Set the Base64 encoded version of the API key as MER_API_KEY in the code and Base64 decode before using in the header.
D. Leverage an external secret vault to retrieve MER_API_KEY and embed the vault key as a new variable before running the code.
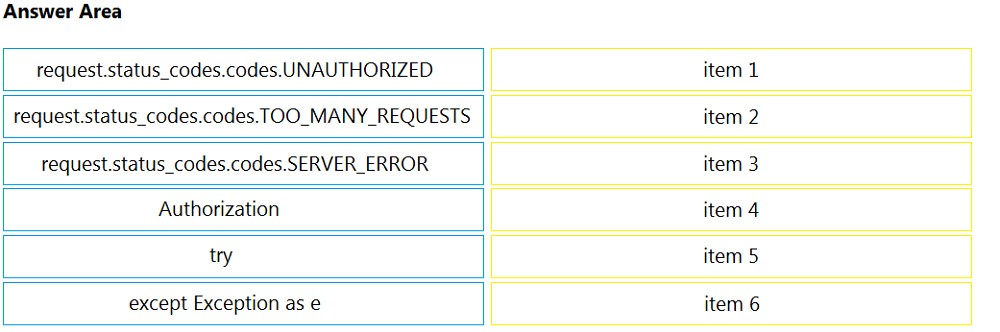
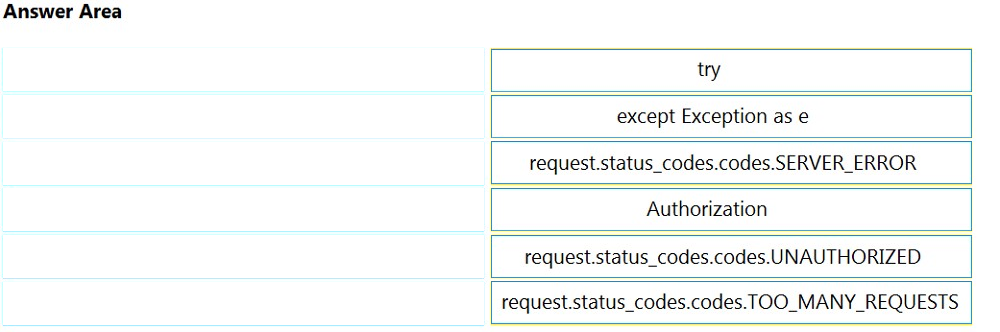
Refer to the exhibit. A Python API server has been deployed. Based on metrics and logs, increased load has been noticed. Which two approaches must be taken to optimize API usage on the server? (Choose two.)
A. Include the Content-Type header in the API response.
B. Leverage middleware caching and respond with HTTP code 204 in the API response.
C. Include the ETag header in the API response.
D. Include the Last-Modified header in the API response.
E. Change the query to be more efficient.
Which command is used to enable application hosting on a Cisco IOS XE device?
A. iox
B. application-hosting
C. iox-service
D. app-hosting
DRAG DROP - Drag and drop the code from the bottom of the code snippet to the blanks in the code to construct a Puppet manifest that configures a VRF instance on a Cisco IOS XR device. Not all options are used. Select and Place:
Into which two areas are AppDynamics APIs categorized? (Choose two.)
A. application-centric
B. analytics-events
C. database-visibility
D. platform-side
E. agent-side
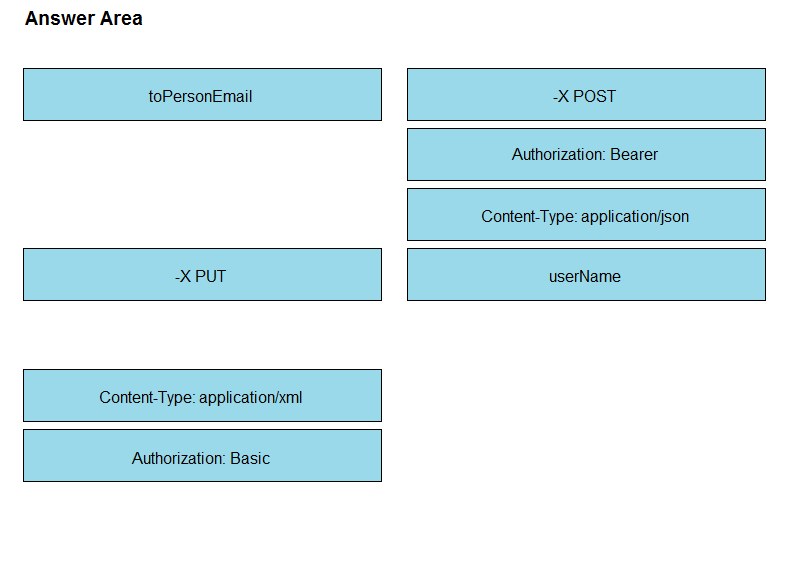
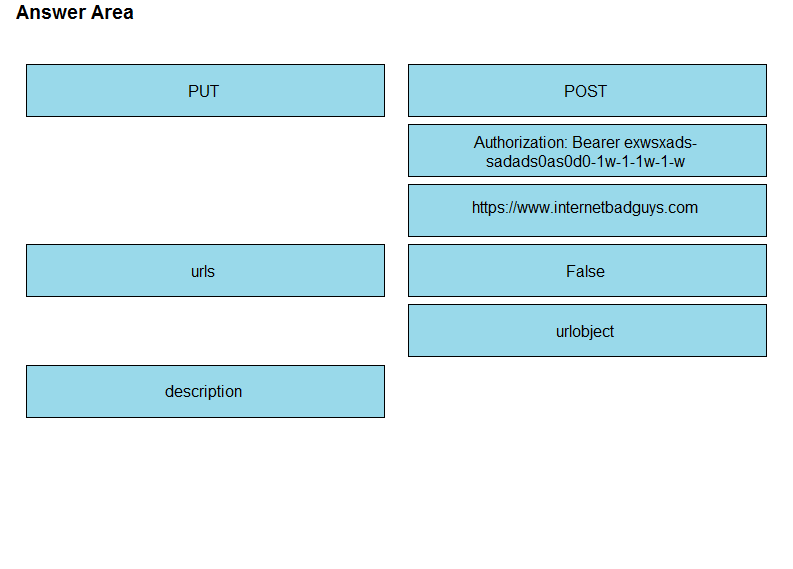
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to create a Webex meeting by using the Webex API. Not all options are used.
Which two statements about a stateless application are true? (Choose two.)
A. Different requests can be processed by different servers.
B. Requests are based only on information relayed with each request.
C. Information about earlier requests must be kept and must be accessible.
D. The same server must be used to process all requests that are linked to the same state.
E. No state information can be shared across servers.
What is a well-defined concept for GDPR compliance?
A. Data controllers must confirm to data subjects as to whether, where, and why personal data is being processed.
B. Personal data that was collected before the compliance standards were set do not need to be protected.
C. Compliance standards apply to organizations that have a physical presence in Europe.
D. Records that are relevant to an existing contract agreement can be retained as long as the contract is in effect.
Which security approach should be used for developing a REST API?
A. Add an API key to each URL string.
B. Use custom security relevant HTTP response codes.
C. Utilize CORS headers.
D. Utilize TLS for end-to-end encryption.
DRAG DROP - Drag and drop the steps from the left into the order on the right to build and run a customized Python Docker image. Not all options are used.
What is a benefit of implementing a Cl pipeline?
A. decreases external dependencies
B. enables a faster feedback loop
C. enforces version control
D. ensures that tests are written before code is written
DRAG DROP -
Refer to the exhibit. A system administrator has installed a Linux-based alarm system in their home that can execute a Bash shell script when an intruder is detected. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a chat-ops script that will notify of alarms via the Webex REST API. Not all code snippets are used. Select and Place:
Where should distributed load balancing occur in a horizontally scalable architecture?
A. firewall-side/policy load balancing
B. network-side/central load balancing
C. service-side/remote load balancing
D. client-side/local load balancing
Refer to the exhibit. The code fetches the latest order from the purchases table for a specific user. An engineer needs to pass query parameters to the execute function to prevent an SQL injection attack. Which code snippet must be placed in the blank in the code to meet this requirement?
A. cursor.execute(“SELECT orders FROM purchases WHEREusername = ‘{}'”.format (username))
B. cursor.execute(“SELECT orders FROM purchases WHEREusername = %(username)s”, {‘username’: username})
C. cursor.execute(“SELECT orders FROM purchases WHEREusername = ‘$s’ % username”.replace(“‘”, “””))
D. cursor.execute (f”SELECT orders FROM purchases WHEREusername = ‘{username}'”)
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
A. URI to which the authorization server will send the user-agent back when access is granted or denied
B. list of the API resources that the application is requesting to access
C. secret that was generated by the authorization server when the application registered as an OAuth integration
D. list of scopes that correspond to the API resources to which the application is requesting to access
E. name of the application under which the application registered as an OAuth integration
DRAG DROP - A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all options are used. Select and Place:
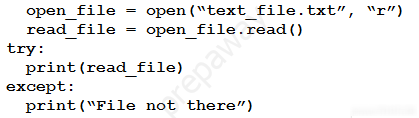
Refer to the exhibit. A developer created the code, but it fails to execute. Which code snippet helps to identify the issue? A.
B.
C.
D.
A developer has issued the git add file1 file2 test.py command to add three files for the next commit, but then decides to exclude test.py from this commit. Which command needs to be used to exclude test.py from this commit but keep the rest of the files?
A. git stash — file1 file 2
B. git clean — test.py
C. git checkout — file1 file2
D. git reset — test.py
{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
A. latitude = response.text[‘lat’] longitude = response.text[‘lng’]
B. latitude = response.json()[‘lat’] longitude = response.json()[‘lng’]
C. latitude = response.json()[0] longitude = response.json()[1]
D. latitude = response.text[0] longitude = response.text[1]
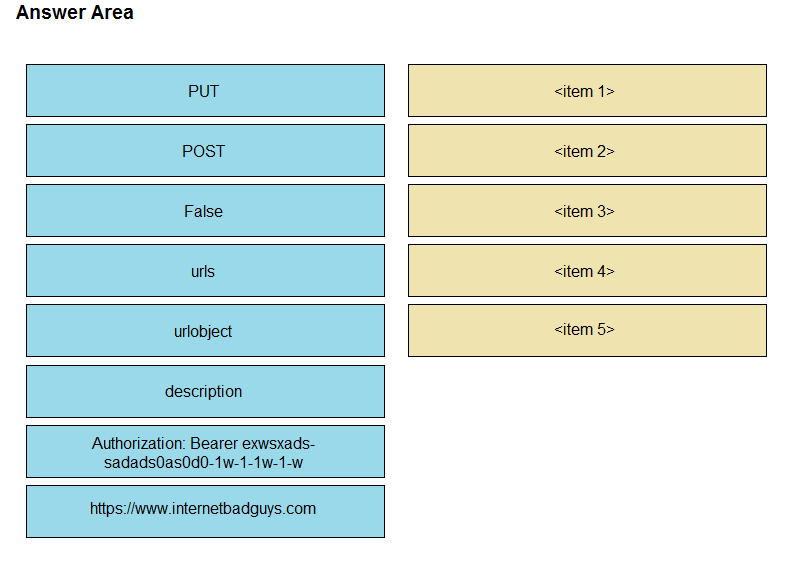
DRAG DROP -Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the curl exhibit to complete the cURL request to FirePower Device Manager API to create objects. Not all code snippets are used. Select and Place:
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to update the script library that is used to connect to the REST API on the network devices. A descriptive error and warning message should be logged when a user uses the script. Not all options are used.
Which two types of organization are subject to GDPR? (Choose two.)
A. only organizations that operate outside the EU
B. any organization that offers goods or services to customers in the EU
C. only organizations that have offices in countries that are part of the EU
D. any organization that operates within the EU
E. only organizations that physically reside in the EU
Which statement about microservices architecture is true?
A. Applications are written in a single unit.
B. It is a complex application composed of multiple independent parts.
C. It is often a challenge to scale individual parts.
D. A single faulty service can bring the whole application down.
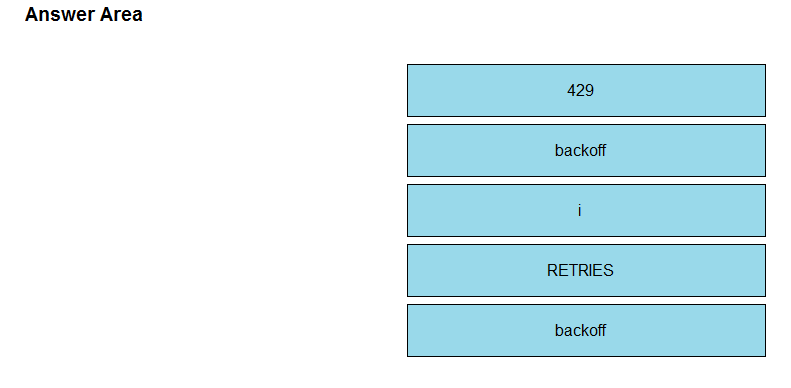
Refer to the exhibit. One part of an application routinely uses the Cisco Meraki API to collate data about all clients. Other parts of the application also use the Meraki API, but a single API key is used within the application. The organization has approximately 4,000 clients across 30 networks. Some of the application users report poor performance and missing data. Which two changes improve the performance of the application? (Choose two.)
A. Check API response payloads for later reuse in real time during code execution.
B. Use random values in the User-Agent header when HTTP calls are made.
C. Use fewer API calls to create a more efficient endpoint.
D. Configure multiple API keys in the application and rotate usage of each one.
E. Check for HTTP code 429 and wait until Retry-After time before further calls are made.
The UCS Python SDK includes modules for Service Profile template creation. Which two UCS Service Profile template types are supported? (Choose two.)
A. initial-template
B. updating-template
C. abstract-template
D. attached-template
E. base-template
A developer creates an application for a Cisco Catalyst 9000 switch in a Docker container. Which action must be taken to host the application on the switch?
A. Export the application as a TAR file and import the file to the switch.
B. Connect the switch to Cisco DNA Center and push the application through the platform.
C. Use the Cisco IOxClient tool to export the application to a ZIP file and push the file to the switch.
D. Copy the application code to a NETCONF file and upload the file to the switch.
Free Access Full 350-901 Practice Test Free Questions
If you’re looking for more 350-901 practice test free questions, click here to access the full 350-901 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 350-901 certification journey!