350-901 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 350-901 certification exam? Start your preparation the smart way with our 350-901 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 350-901 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 350-901 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
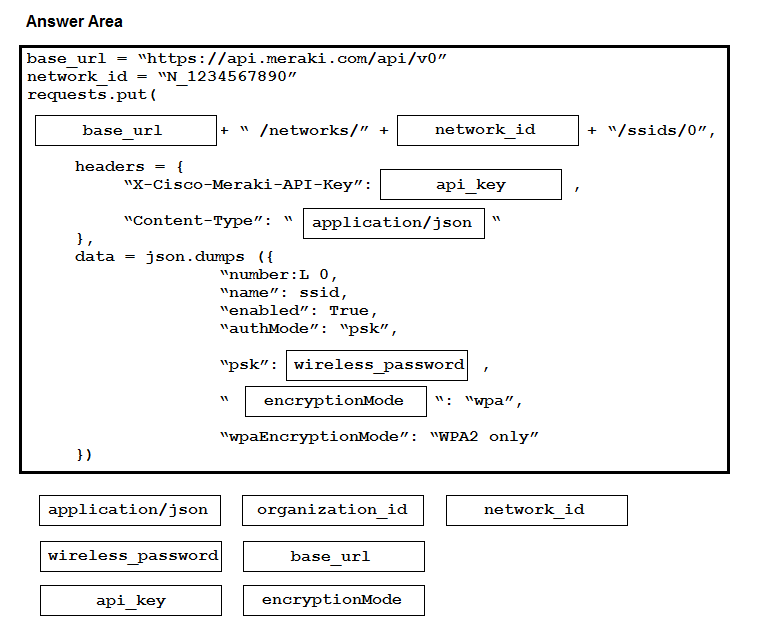
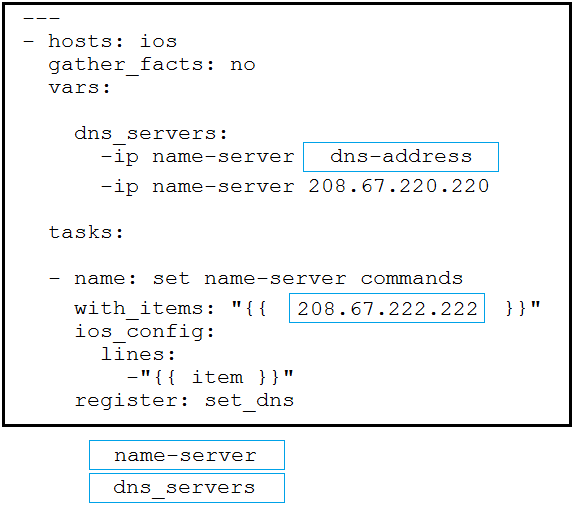
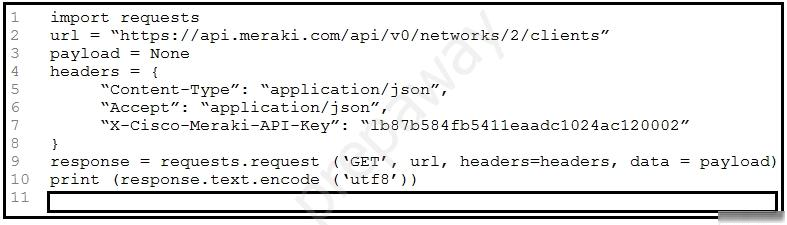
Refer to the exhibit. A developer created a Python script to retrieve information about Meraki devices in a local network deployment. After requesting a security review of the code, the security analyst has observed poor secret storage practices. What is the appropriate secret storage approach?A. Set an OS environment variable for MER_API_KEY to the API key before running the code and no longer set MER_API_KEY within the code.
B. Leverage an external secret vault to retrieve MER_API_KEY and set the vault key as an OS environment variable before running the code.
C. Set the Base64 encoded version of the API key as MER_API_KEY in the code and Base64 decode before using in the header.
D. Leverage an external secret vault to retrieve MER_API_KEY and embed the vault key as a new variable before running the code.
What are two steps in the OAuth2 protocol flow? (Choose two.)A. The user is authenticated by the authorization server and granted an access token.
B. The user's original credentials are validated by the resource server and authorization is granted.
C. The user indirectly requests authorization through the authorization server.
D. The user requests an access token by authentication and authorization grant presentation.
E. The user requests the protected resource from the resource server using the original credentials.
DRAG DROP
-
An engineer sets up two tasks in an Ansible playbook. An NTP server must be defined and retrieve the configuration information of the IP interfaces. Drag and drop the code from the bottom onto the box where the code is missing to complete the playbook. Options may be used more than once. Not all options are used.

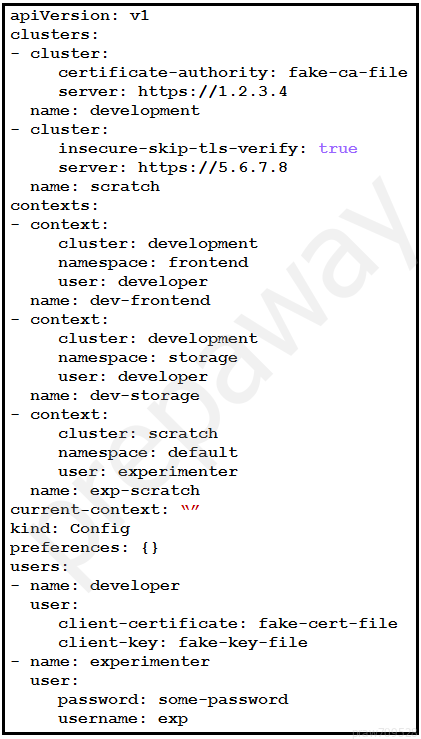
Refer to the exhibit. A kubeconfig file to manage access to clusters is provided.
How many clusters are defined and which of them are accessed using username/password authentication versus certificate?A. two clusters; scratch
B. three clusters; scratch
C. three clusters; development
D. two clusters; development
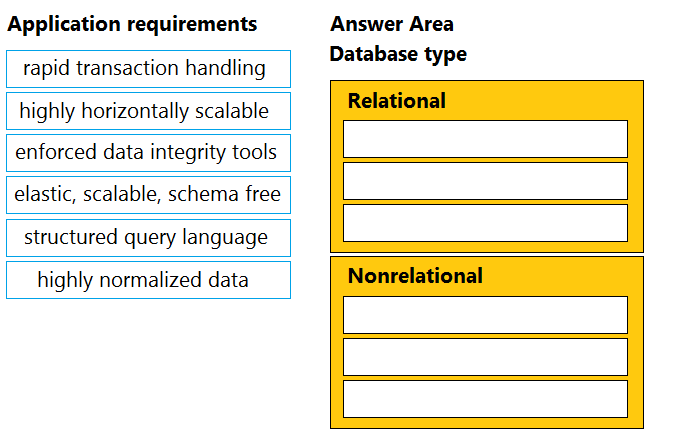
DRAG DROP -
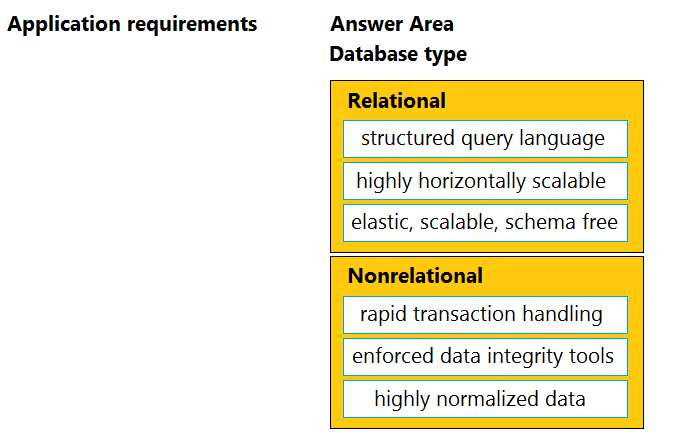
Drag and drop the application requirement on the left onto the database type that should be selected for the requirement on the right.
Select and Place:
Which two situations are flagged by software tools designed for dependency checking in continuous integration environments, such as OWASP? (Choose two.)A. publicly disclosed vulnerabilities related to the included dependencies
B. mismatches in coding styles and conventions in the included dependencies
C. incompatible licenses in the included dependencies
D. test case failures introduced by bugs in the included dependencies
E. buffer overflows to occur as the result of a combination of the included dependencies
DRAG DROP
-
Drag and drop the code snippets from the bottom onto the blanks in the code to update the script library that is used to connect to the REST API on the network devices. A descriptive error and warning message should be logged when a user uses the script. Not all options are used.

An ETag header is included in the HTTP response for an API resource.
What are two benefits of using the value of the ETag for future interactions involving the same API resource? (Choose two.)A. caching and optimization of response payloads
B. creating conditional requests
C. categorizing and comparing this API resource with others
D. checking the integrity of the resource
E. requesting the list of operations authorized for this resource
DRAG DROP
-
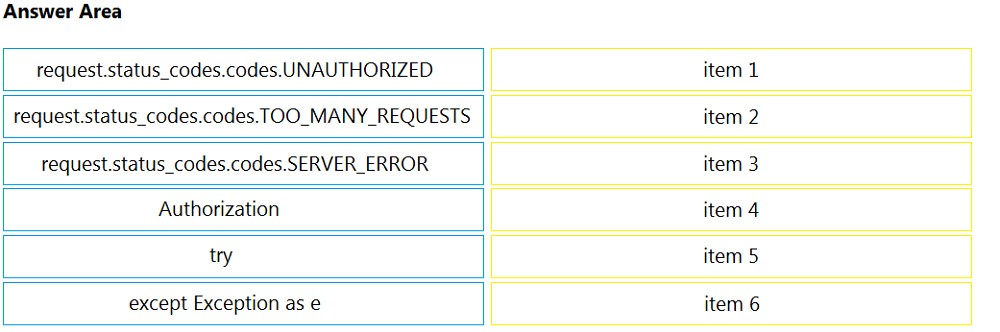
A developer is creating a Python script to analyze errors during REST API call operations. The script will be used with Cisco solutions and devices. Drag and drop the code from the bottom to the box where the code is missing to implement control flow for handling unrecoverable REST API calls. Not all options are used.

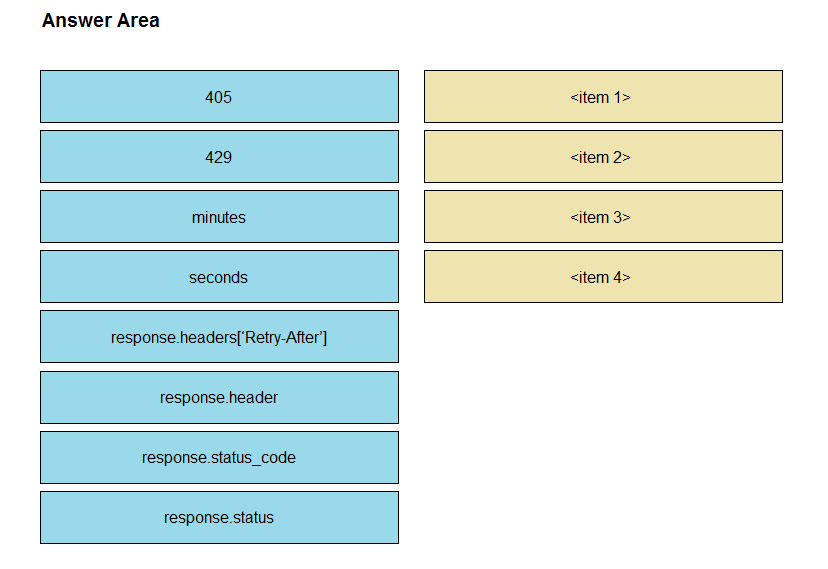
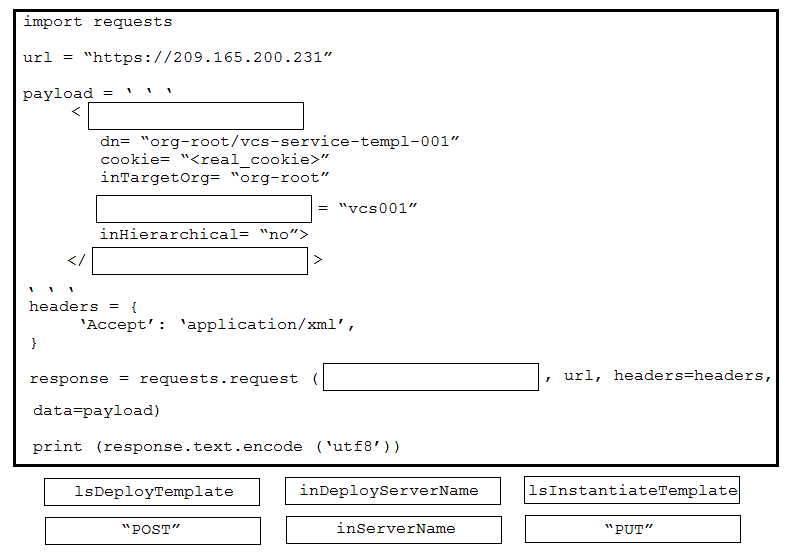
DRAG DROP -
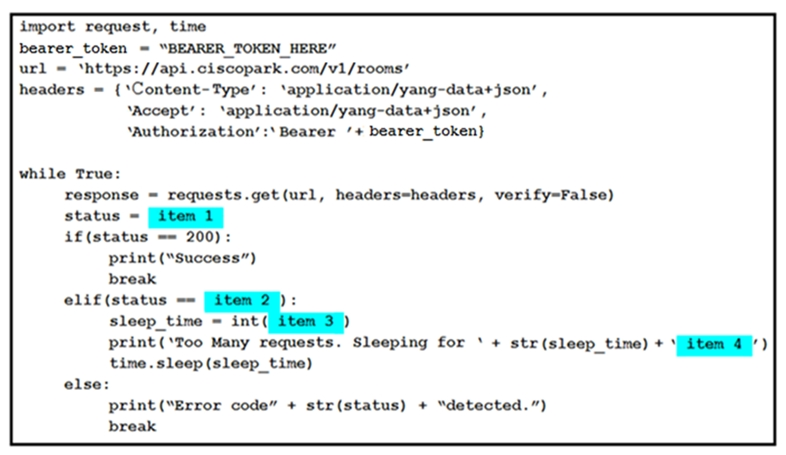
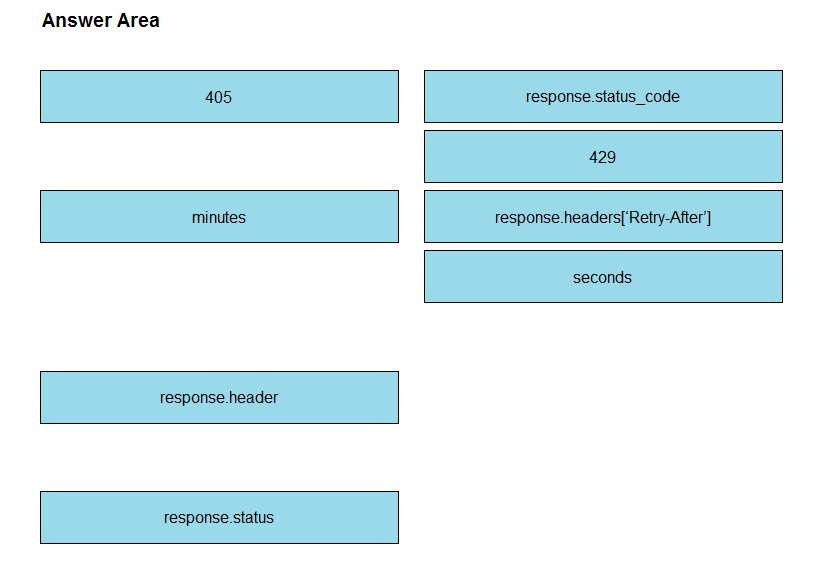
Refer to the exhibit. A developer is creating a Python script to use the Webex REST API to list joined spaces, retry after the server-specified amount of time if a
`Too many requests` response is received, and print any other error that is received. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.
Select and Place:
DRAG DROP
-
Drag and drop the code from the bottom onto the box where the code is missing to configure a Python script that uses RESTCOMF to add an IP address and subnet mask to an interface. Not all options are used.

DRAG DROP -
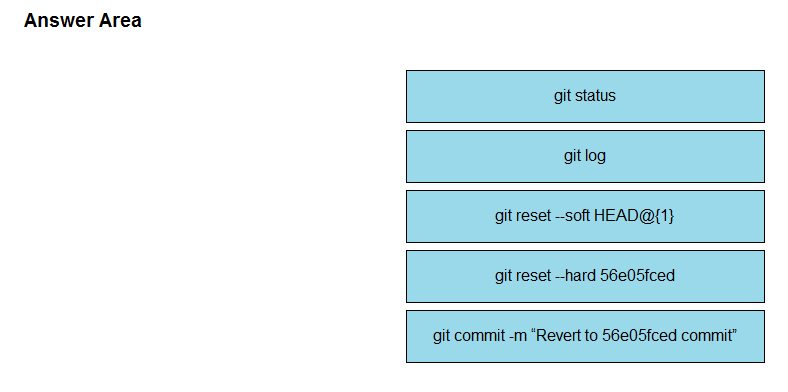
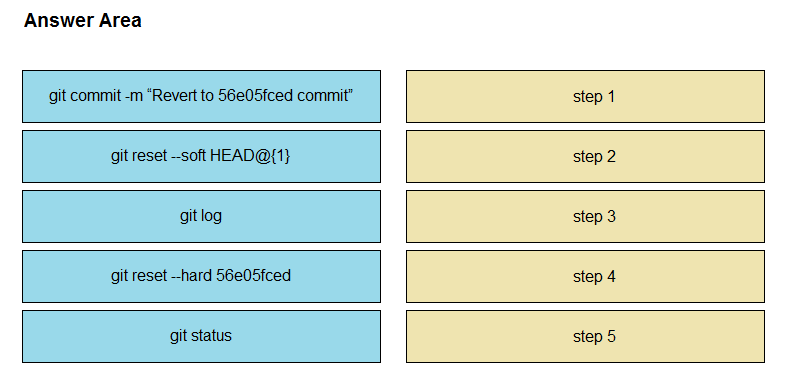
Drag and drop the steps from the left into the correct sequence on the right to describe how to use Git to maintain the current HEAD and revert back to a previous commit, while undoing all intermediate commits.
Select and Place:
DRAG DROP -
Drag and drop the code from the bottom onto the box where the code is missing to provision a new Cisco Unified Computing System server by using the UCS
XML API. Options may be used more than once. Not all options are used.
Select and Place:
What is a benefit of continuous testing?A. increases the number of bugs found in production
B. enables parallel testing
C. removes the requirement for test environments
D. decreases the frequency of code check-ins
What is a characteristic of a monolithic architecture?A. It is an application with multiple independent parts.
B. New capabilities are deployed by restarting a component of the application.
C. A service failure can bring down the whole application.
D. The components are platform-agnostic.
[1]
needs to be removed so that the commit is performed and branches merged. Which git command must be used to unstage the file?
[1]
[1]
[1]
[1]
DRAG DROP -
Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the script to implement control flow.
Select and Place:
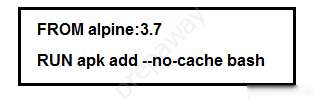
Refer to the exhibit. Which additional line results in the output of Test 1 upon execution of the docker run --rm devnet 1 command in a Dockerfile with this content?A. CMD [ג€/bin/echoג€, ג€Test1ג€]
B. RUN [ג€/bin/echoג€, ג€Test1ג€]
C. ENTRYPOINT [ג€/bin/echoג€, ג€Test1ג€]
D. CMD [ג€/bin/echo Test1ג€]
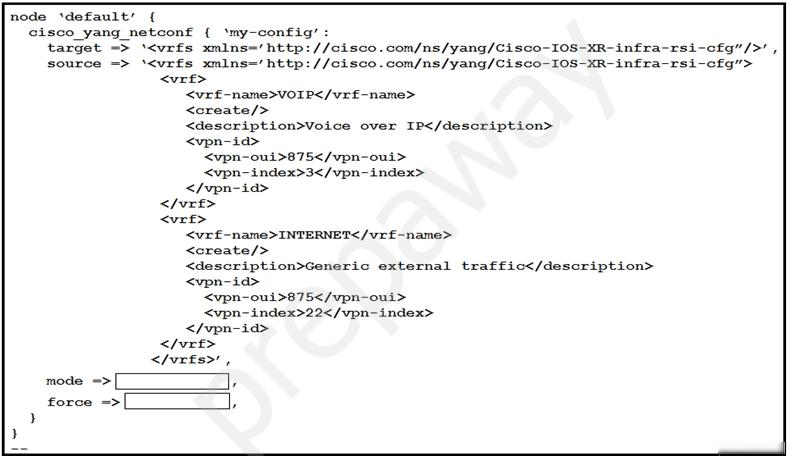
Refer to the exhibit. This script uses ciscoyang to configure two VRF instances on a Cisco IOS-XR device using the Yang NETCONF type.
Which two words are required to complete the script? (Choose two.)A. ensure
B. commit
C. false
D. replace
E. none
Refer to the exhibit. A developer is creating an application to be used in the current network. The application must be compatible with the network devices and platforms. Based on the design and performance, it must be flexible to modifications and future installations. What are two characteristics of the Python application? (Choose two.)A. The application design maximizes scalability.
B. Config.py contains code related specifically to the Cisco DNA Center Discovery REST API.
C. The application supports only version 2.1.2 of the Cisco DNA Center API.
D. The application design enables code reuse.
E. Discovery.py contains code related specifically to the Cisco DNA Center Discovery REST API.
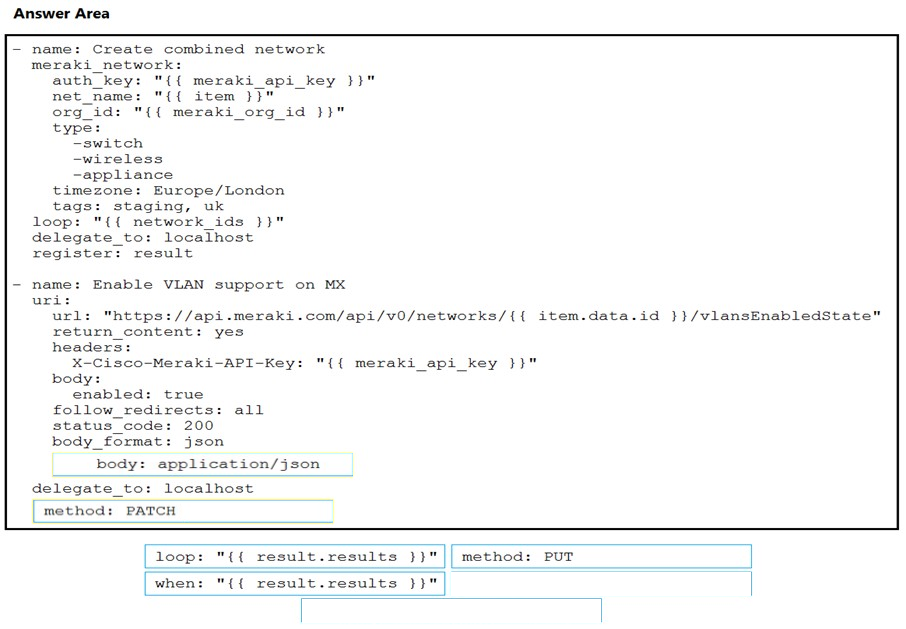
DRAG DROP -
Drag and drop the code from the bottom onto the box where the code is missing on the Ansible task to enable a VLAN on a Meraki MX device. Not all options are used.
Select and Place:

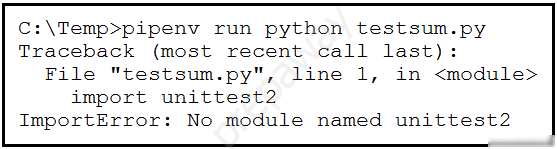
Refer to the exhibit. Pipenv is used to manage dependencies. The test runs successfully on a local environment.
What is the reason for the error when running the test on a CI/CD pipeline?A. All the unit tests in testsum.py failed.
B. Pytest did not detect any functions that start with 'test_'.
C. The pipfile in the local environment was not pushed to the remote repository.
D. Nose2 was not used as the test runner.
DRAG DROP -
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the cURL script that will use RESTCONF to update an interface on a Cisco IOS XE device.
Select and Place:
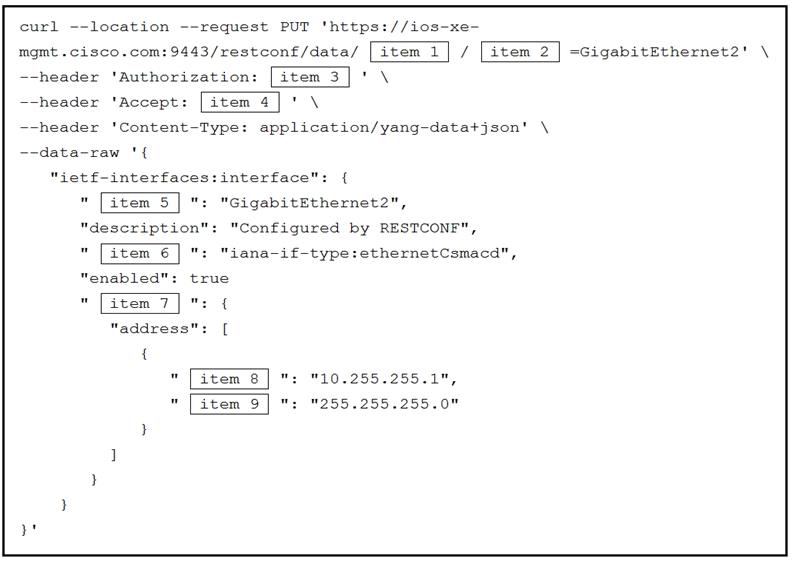
Refer to the exhibit. An engineer needs to configure an interface named GigabitEthernet3 with an IP address on several RESTCONF-enabled Cisco IOS XE devices. Which code snippet must be placed in the blank in the code to meet this requirement?A. {item["name"]}'
B. {item["name"]}/ip/address/primary'
C. {item["name"]}/ip/address
D. {item["name"]} /ip
A local Docker container with a Container ID of 391441516e7a is running a Python application.
Which command is used to connect to a bash shell in the running container?
A.
B.
C.
D.

Refer to the exhibit. Which configuration of method and parameter retrieves the health of a laptop connected to the network from Cisco DNA Center?A. PUT; network-health;
B. GET; client-health;
C. GET; network-device;
D. POST; network-device;
DRAG DROP
-
Drag and drop the components from the left into the order on the right to create the flow of the three-legged OAuth2.

An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?A. Update the base image of the containers.
B. Test the execution of the application with another cloud services platform.
C. Increase the number of containers running per service.
D. Add consistent ג€try/catch(exception)ג€ clauses to the code.
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?A. apt-get install
B. zypper install
C. yum install
D. dnf install
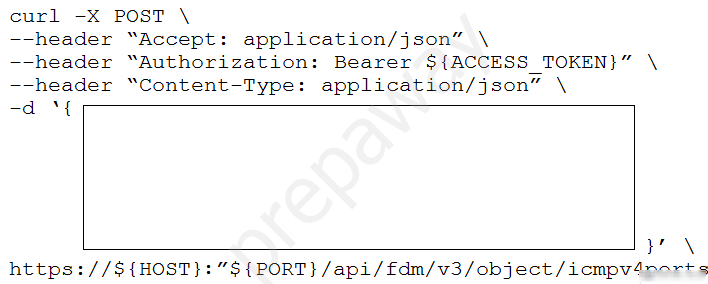
Refer to the exhibits which show the documentation associated with the create port object API call in Cisco Firepower Threat Defense, and a cURL command.
Which data payload completes the cURL command to run the API call?A. "icmpv4Type": "ANY", "name": "string", "type": "icmpv4portobject"
B. "description": "This is an ICMP Echo", "icmpv4Code": "8", "icmpv4Type": "Echo", "isSystemDefined": true, "name": "ICMP Echo", "version": "2.2"
C. "description": "string", "icmpv4Code": "ANY_IPV4", "icmpv4Type": "ANY", "id": "string", "isSystemDefined": "string", "name": "string", "type": "icmpv4portobject", "version": "string"
D. "description": "string", "icmpv4Code": "ANY_IPV4", "icmpv4Type": null, "isSystemDefined": true, "name": "string", "type": "icmpv4portobject"
Refer to the exhibit. A network administrator copies SSL certificates to a Cisco NX-OS switch. An Ansible playbook is created to enable NX-API, which will use the new certificate. In the group_vars/vars.yml file, which code snippet must be used to define the properly formatted variables?A.
B.
C.
D.
A developer has just completed the configuration of an API that connects sensitive internal systems. Based on company policies, the security of the data is a high priority.
Which approach must be taken to secure API keys and passwords?A. Embed them directly in the code.
B. Store them in a hidden file.
C. Store them inside the source tree of the application.
D. Change them periodically.
What are two principles according to the build, release, run principle of the twelve-factor app methodology? (Choose two.)A. Code changes are able to be made at runtime.
B. Separation between the build, release, and run phases.
C. Releases should have a unique identifier.
D. Existing releases are able to be mutated after creation.
E. Release stage is responsible for compilation of assets and binaries.
A developer plans to create a new bugfix branch to fix a bug that was found on the release branch.
Which command completes the task?A. git checkout -t RELEASE BUGFIX
B. git checkout -b RELEASE BUGFIX
C. git checkout -t BUGFIX RELEASE
D. git checkout -b BUGFIX RELEASE
DRAG DROP
-
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to query the last 10 Bluetooth clients seen by APs in their network using the Meraki Dashboard API. Not all options are used.

Given an application that implements a basic search function as well as a video upload function, which two load-balancing approaches optimize the application's user experience? (Choose two.)A. Video upload requests should be routed to the endpoint using an intermediate hop.
B. Search requests should be routed to the endpoint with lowest round-trip latency.
C. Video upload requests should be routed to the endpoint with lowest round-trip latency.
D. Video upload requests should be routed to the endpoint with highest data throughput.
E. Search requests should be routed to the endpoint with highest data throughput.
An application uses OAuth to get access to several API resources on behalf of an end user.
What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)A. URI to which the authorization server will send the user-agent back when access is granted or denied
B. list of the API resources that the application is requesting to access
C. secret that was generated by the authorization server when the application registered as an OAuth integration
D. list of scopes that correspond to the API resources to which the application is requesting to access
E. name of the application under which the application registered as an OAuth integration
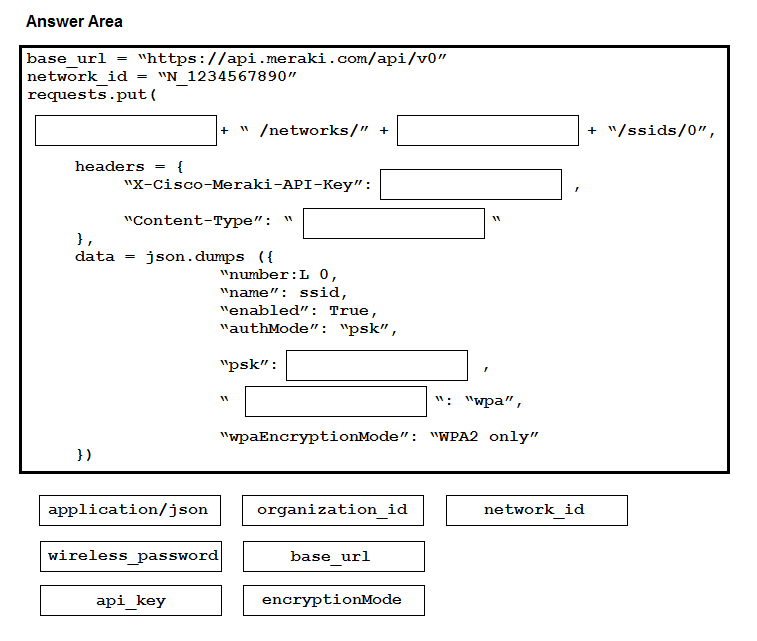
DRAG DROP -
Drag and drop the code onto the snippet to update a SSID in Meraki using the Dashboard API. Not all options are used.
Select and Place:
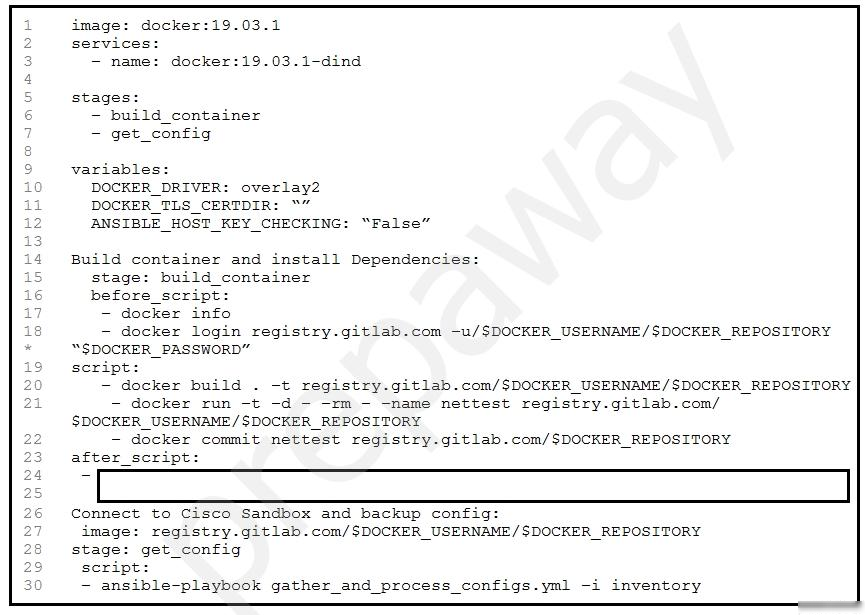
Refer to the exhibit. A developer wants to automatically deploy infrastructure for a containerized application. A .gitlab-ci.yml file must describe a pipeline that builds a container based on a supplied Dockerfile and executes an Ansible playbook on the configured container. What must be added where the code is missing to complete the script?
A.
B.
C.
D.
Refer to the exhibit. Which line of code needs to be placed on the snippet where the code is missing to provide API rate-limiting to the requests?A. int(self.response.headers.post('Retry-After'))
B. int(self.response.headers.get('Retry-After'))
C. int(response.headers.post('Retry-After'))
D. int(response.headers.get('Retry-After'))
A custom dashboard of the network health must be created by using Cisco DNA Center APIs. An existing dashboard is a RESTful API that receives data from
Cisco DNA Center as a new metric every time the network health information is sent from the script to the dashboard.
Which set of requests creates the custom dashboard?A. POST request to Cisco DNA Center to obtain the network health information, and then a GET request to the dashboard to publish the new metric
B. GET request to Cisco DNA Center to obtain the network health information, and then a PUT request to the dashboard to publish the new metric
C. GET request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
D. PUT request to Cisco DNA Center to obtain the network health information, and then a POST request to the dashboard to publish the new metric
DRAG DROP
-
Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy. Not all options are used.

Refer to the exhibit. Which code snippet must be added to the blank in the code to automate the evaluation and handling of errors due to wrong credentials when Basic Authorization is used?A. while response.status_code == 401 :
B. while response.status_code == 403 :
C. while response.get.status_code == 400 :
D. while response.get.status_code == 404 :
Which tool is used to deploy an IOx application to a group of IOx devices at one time?A. ioxclient
B. IOx local manager
C. Fog Network Director
D. Kubernetes
What are two capabilities of AppDynamics when instrumenting an application? (Choose two.)A. runtime application architecture discovery
B. end user experience modeling
C. automatic scaling based on load
D. on-the-fly application editing
E. end user screen capture
DRAG DROP -
Drag and drop the code from the bottom onto the box where the code is missing in the snippet to complete this Ansible playbook. Not all options are used.
Select and Place:
How is an OAuth2 three-legged authentication flow initiated?A. Construct an API call to retrieve the credentials.
B. The user makes a request to the OAuth client.
C. Get the authorization code.
D. Exchange the key for an access token.
Which two statements describe advantages of static code analysis over unit tests? (Choose two.)A. It checks for potential tainted data where input is not checked.
B. It enforces proper coding standards and style.
C. It performs a quick analysis of whether tests will pass or fail when run.
D. It checks for race conditions in threaded applications.
E. It estimates the performance of the code when run.
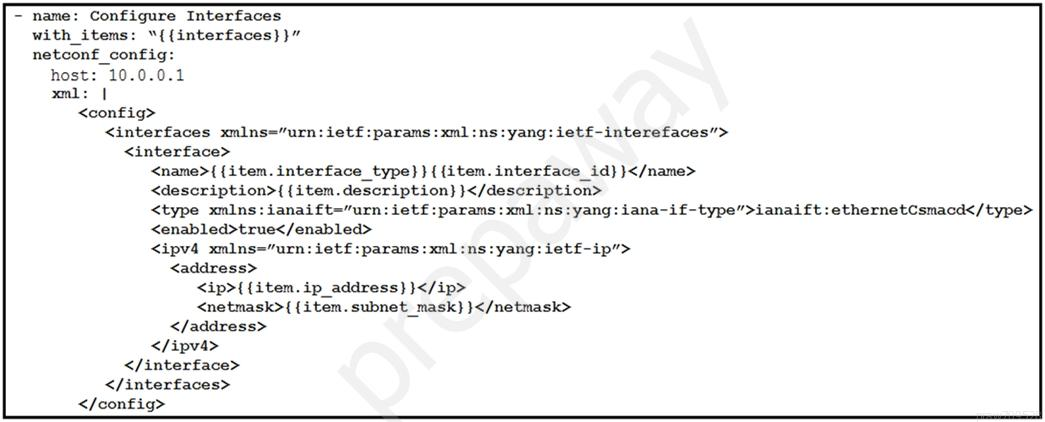
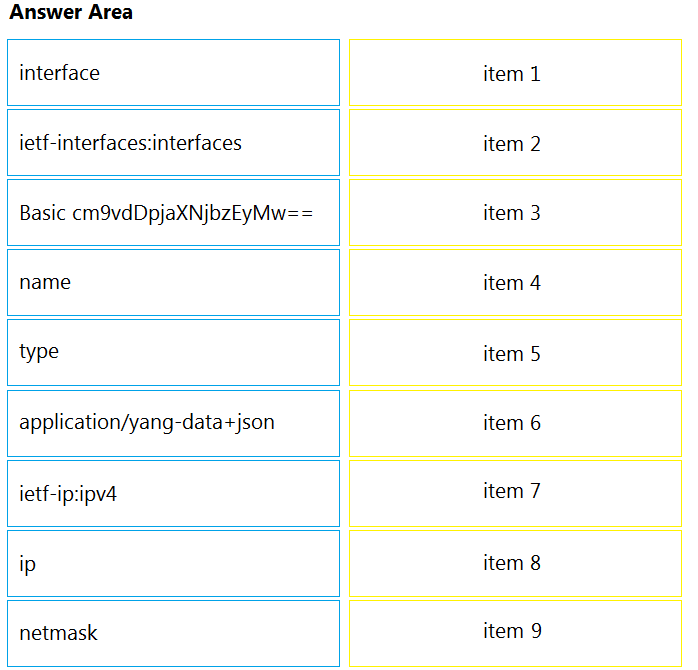
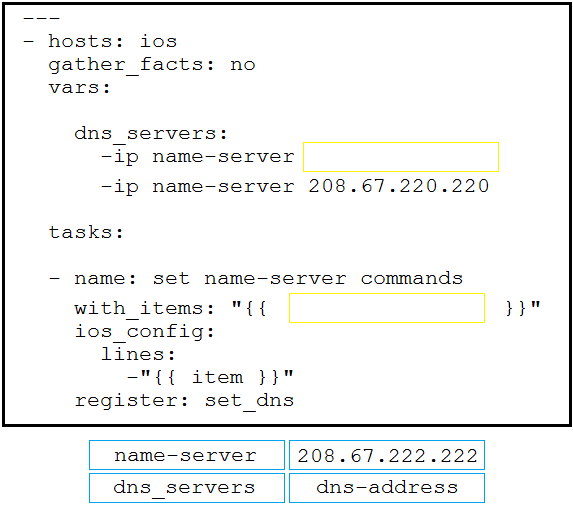
Refer to the exhibit. The Ansible playbook is using the netconf_module to configure an interface using a YANG model. As part of this workflow, which YANG models augment the interface?A. ietf-interfaces and ietf-ip
B. iana-if-type and ietf-interfaces
C. ietf-ip and openconfig-interface
D. ietf-ip and iana-if-type
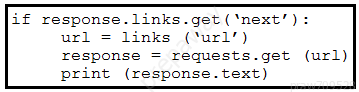
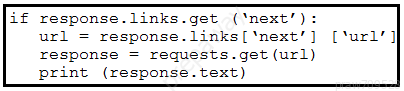
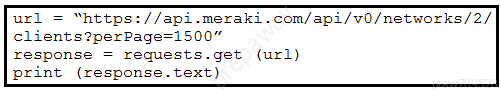
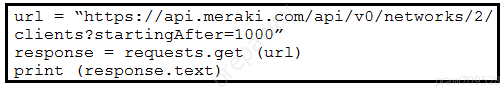
Refer to the exhibit. A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2. The number of client entries per returned page is restricted to 1,000 according to the API specification. Network 2 has 2,500 clients. What must be added where the code is missing to print the content of each response?
A.
B.
C.
D.
Access Full 350-901 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 350-901 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 350-901 mock test free today—and take a major step toward exam success!