350-901 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 350-901 certification? Our 350-901 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 350-901 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 350-901 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
An application has been developed for monitoring rooms in Cisco Webex. An engineer uses the application to retrieve all the messages from a Cisco Webex room, but the results are slowly presented. Which action optimizes calls to retrieve the messages from the /v1/messages endpoint?
A. Define the ma property by using the pagination functionality.
B. Set the beforeMessage property to retrieve the messages sent before a specific message ID.
C. Avoid unnecessary calls by using a prior request to /v1/rooms to retrieve the last activity property.
D. Filter the response results by specifying the created property in the request.
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?
A. Encrypt the username, hash the password, and store these values.
B. Hash the username, hash the password, and store these values.
C. Encrypt the username, encrypt the password, and store these values.
D. Hash the username, encrypt the password, and store these values.
Refer to the exhibit. A developer is creating an application to be used in the current network. The application must be compatible with the network devices and platforms. Based on the design and performance, it must be flexible to modifications and future installations. What are two characteristics of the Python application? (Choose two.)
A. The application design maximizes scalability.
B. Config.py contains code related specifically to the Cisco DNA Center Discovery REST API.
C. The application supports only version 2.1.2 of the Cisco DNA Center API.
D. The application design enables code reuse.
E. Discovery.py contains code related specifically to the Cisco DNA Center Discovery REST API.
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to permit network traffic between 10.0.0.0/8 and all other networks on port 80 for a Cisco Nexus 9000 switch by using the Puppet module. Not all options are used.
What is an effective strategy for application logging?
A. Use an FTP server for collection.
B. Use a single vendor across the network.
C. Use SNMP for messages.
D. Use the appropriate logging level.
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to retrieve the audit logs that were created after a specific date. Not all options are used.
FILL BLANK - A local Docker image has an image ID of 385001111. Fill in the blanks to complete the command in order to tag the image into the "cisco" repository with "version1.0"
Refer to the exhibit. Which key value pair from the ios_ntp Ansible module removes the NTP server peer?
A. state: absent
B. state: False
C. config: absent
D. config: False
A developer is deploying an application to automate the configuration and management of Cisco network switches and routers. The application must use REST API interface to achieve programmability. The security team mandates that the network must be protected against DDoS attacks. What mitigates the attack without impacting genuine requests?
A. IP address filtering at the application layer
B. traffic routing on the network perimeter
C. API rate limiting at the application layer
D. firewall on the network perimeter
Which transport protocol is used by gNMI?
A. HTTP/2
B. HTTP 1.1
C. SSH
D. MQTT
When end-to-end encryption is implemented, which area is most vulnerable to exploitation?
A. cryptographic key exchange
B. endpoint security
C. cryptographic key generation
D. security of data in transit
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to write a module that will do the following: • examine an HTTP response status for the "Too Many Requests" error and the HTTP Retry-After header • enter the sleep() function • wake from the sleep() function and retry the POST request Not all options are used.
DRAG DROP - A developer is creating a Python function that adds network engineers to a Webex room to troubleshoot after a monitoring alert. Drag and drop the code from the bottom onto the box where the code is missing in the Python function to add the engineers to the room. Not all options are used.
Which Git command enables the developer to revert back to f414f31 commit to discard changes in the current working tree?
A. git reset –hard f414f31
B. git reset checkout –hard f414f31
C. git reset –soft f414f31
D. git checkout f414f31
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to delete a host object by using the Cisco Firepower Device Manager API. Not all options are used.
When an application is designed that requires high availability, what is a reason to use a cross-region cloud?
A. Account for failure in another zone.
B. Minimize costs.
C. Protect from a single component failure.
D. Provide disaster recovery protection.
Which security approach should be used for developing a REST API?
A. Add an API key to each URL string.
B. Use custom security relevant HTTP response codes.
C. Utilize CORS headers.
D. Utilize TLS for end-to-end encryption.
Refer to the exhibit. Which line of code needs to be placed on the snippet where the code is missing to provide API rate-limiting to the requests?
A. int(self.response.headers.post(‘Retry-After’))
B. int(self.response.headers.get(‘Retry-After’))
C. int(response.headers.post(‘Retry-After’))
D. int(response.headers.get(‘Retry-After’))
[1] needs to be removed so that the commit is performed and branches merged. Which git command must be used to unstage the file? [1] [1] [1] [1]
Which HTTP status code indicates that a client application is experiencing intentional rate limiting by the server?
A. 202
B. 401
C. 429
D. 503
Refer to the exhibit. The JSON response is received from the Meraki location API. Which parameter is missing?
A. apMac
B. clientMac
C. clientId
D. accesspoint
Refer to the exhibit. Which cURL request is included in the presented XML as the body of the response? A.
B.
C.
D.
What is an effective logging strategy according to the 12-factor app tenets?
A. Tag and save logs in a local document database that has querying capabilities.
B. Back up log files in a high-availability remote cluster on the public cloud.
C. Timestamp and save logs in a local time-series database that has querying capabilities.
D. Capture logs by the execution environment and route to a centralized destination.
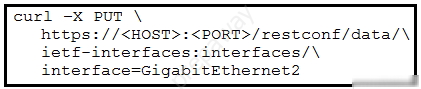
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code on the RESTCONF request to retrieve a list of configured interfaces on a Cisco IOS XE device. Not all options are used.
Refer to the exhibit. Which action will complete the workflow that represents how an API call sends multiple messages?
A. {PUT} messages(roomID)
B. {PUT} messages(BearerToken)
C. {POST} messages(roomID)
D. {POST} messages(BearerToken)
Given an application that implements a basic search function as well as a video upload function, which two load-balancing approaches optimize the application's user experience? (Choose two.)
A. Video upload requests should be routed to the endpoint using an intermediate hop.
B. Search requests should be routed to the endpoint with lowest round-trip latency.
C. Video upload requests should be routed to the endpoint with lowest round-trip latency.
D. Video upload requests should be routed to the endpoint with highest data throughput.
E. Search requests should be routed to the endpoint with highest data throughput.
Which database type should be used to store data received from model-driven telemetry?
A. BigQuery database
B. Time series database
C. NoSQL database
D. PostgreSQL database
A developer deploys a web application in a local data center that is now experiencing high traffic load from users accessing data through REST API calls. Which approach enhances the responsiveness and performance of the API?
A. Ensure that all read requests are clearly identified by the PUT method.
B. Configure API payload to return errors in HTTP 200 responses.
C. Use HTTP POST or other non-read methods for read requests when possible.
D. Use HTTP standard authorization header to submit authentication credentials.
A developer is working on containerizing an application. The “devcorapp” container has been run in detached mode to output the container ID with the command: 1 $ docker run -d devcorapp2 2c573okec2hf6756he4441115314ge859299er674f74313426ff9h535 Which command is used to start an interactive Bash shell in the running container?
A. docker run -it c573okec2hf /bin/bash
B. docker exec -it devcorapp /bin/bash
C. docker exec -it c573okec2hf /bin/bash
D. docker run -it devcorapp /bin/bash
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to enable an SSID by using the Cisco Meraki Dashboard API. Not all options are used.
DRAG DROP - Drag and drop the code snippets from the bottom onto the blanks in the code to display wireless health information. Not all options are used.
Which database type should be used with highly structured data and provides support for ACID transactions?
A. time series
B. document
C. graph
D. relational
A web application is susceptible to cross-site scripting. Which two methods allow this issue to be mitigated? (Choose two.)
A. Use only drop downs.
B. Limit user input to acceptable characters.
C. Encrypt user input on the client side.
D. Use AES encryption to secure the script.
E. Remove all HTML/XML tags from user input.
Which scenario is an example of the pseudonymization of sensitive data that meets GDPR requirements?
A. implementing X-Forwarded-For at the frontend of a web app to enable the source IP addresses of headers to change
B. separating the sensitive data into its own dedicated, secured data store and using tokens in its place.
C. encrypting sensitive data at rest by using native cloud services and data in transit by using SSL/TLS transport.
D. leveraging an application load balancer at the frontend of a web app for SSL/TLS decryption to inspect data in transit.

Refer to the exhibit. A team of developers uses Git to store the code for a new application. Each team member is developing the code for a specific part of the application. When a developer commits new code to the Git repository, the deployment pipeline fails. What is the cause of the unit test failure?
A. The username that was provided for basic authentication is incorrect.
B. The assert statement must check for HTTP code 401 instead of HTTP code 200.
C. The URL in the URL variable is formatted incorrectly.
D. The token that is used during authorization is incorrect.
Refer to the exhibit. An application has been created to serve a whole enterprise. Based on use and department requirements, changes are requested on a quarterly basis. When evaluating the application design, which two actions improve code maintainability? (Choose two.)
A. Place all import statements on a single line at the top of the code.
B. Cache responses to API calls for later reuse on other code.
C. Replace the requests library with the http.client library in the code.
D. Parameterize similar code blocks inside functions and reuse within the code.
E. Add comments in appropriate locations to aid in understanding the code.
Refer to the exhibit. An engineer creates an application that leverages the Ansible framework to provision CPE endpoints that have configuration changes. The application contains an Ansible playbook named provision_cpes.yml that uses the ansible.builtin.script Ansible module to execute these two Python scripts: • gather_and_create.py, which creates a JSON file named bios.json that contains the CPE models and their respective IOS file information • load_and_parse.py, which loads the file data and parses it for later consumption After several successful runs, the application fails. During a review of the Ansible execution logs, the engineer discovers an error output that indicates that one of the stages failed. What is the cause of this issue?
A. gather_and_create.py Python script
B. load_and_parse.py Python script
C. provision_cpes.yml Ansible playbook
D. ansible.builtin-script Ansible module
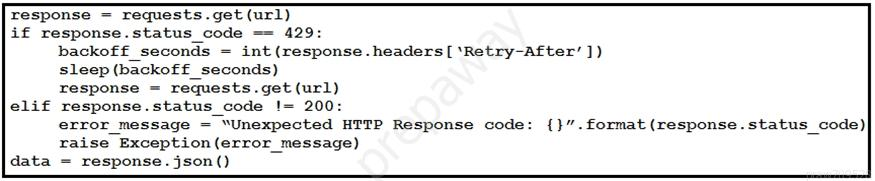
Refer to the exhibit. This snippet of a script has recently started exiting abnormally with an exception stating `Unexpected HTTP Response code: 429`. Which solution handles rate limiting by the remote API? A.
B.
C.
D.
Which two statements are considered best practices according to the 12-factor app methodology for application design? (Choose two.)
A. Application code writes its event stream to stdout.
B. Application log streams are archived in multiple replicated databases.
C. Application log streams are sent to log indexing and analysis systems.
D. Application code writes its event stream to specific log files.
E. Log files are aggregated into a single file on individual nodes.
A developer has issued the git add file1 file2 test.py command to add three files for the next commit, but then decides to exclude test.py from this commit. Which command needs to be used to exclude test.py from this commit but keep the rest of the files?
A. git stash — file1 file 2
B. git clean — test.py
C. git checkout — file1 file2
D. git reset — test.py
Refer to the exhibit. A Docker swarm service is currently running in a local data center. The service is hosting an HTML website. If the container fails, then the service becomes unavailable. The design must meet these requirements: • The service must be highly available and resilient against a data center outage. • The service must be accessible from a single URL. • The HTTP session must remain on the server from which the original request was sent. • Failure of the server must force the client to reconnect. Which two design approaches must be used to meet the requirements? (Choose two.)
A. Create another node in the swarm cluster to scale the service across the nodes over two replicas.
B. Scale the Docker swarm service to 2 and set endpoint-mode to DNSRR instead of the default value of VIP.
C. Configure an external load balancer to route requests to the swarm service by using session persistence.
D. Configure a routing mesh to route requests to the swarm service by using NAT on the network side.
E. Create another swarm cluster within a data center and deploy a secondary instance of the service.
Which two encryption principles should be applied to secure APIs? (Choose two.)
A. Use temporary files as part of the encryption and decryption process.
B. Use encrypted connections to protect data in transit.
C. Reuse source code that contain existing UUIDs.
D. Embed keys in code to simplify the decryption process.
E. Transmit authorization information by using digitally signed payloads.
A developer deployed a web application in a local data center that is experiencing high traffic load from users that access data through REST API calls. Caching helps to enhance the responsiveness and performance of the API usage. Which approach must be used to improve cache performance?
A. Ensure that all read requests are clearly identified by the PUT method.
B. Implement surrogate key tagging to purge requests.
C. Use HTTP POST or other non-read methods for read requests when it is possible.
D. Configure the API payload to return errors in HTTP 200 responses.
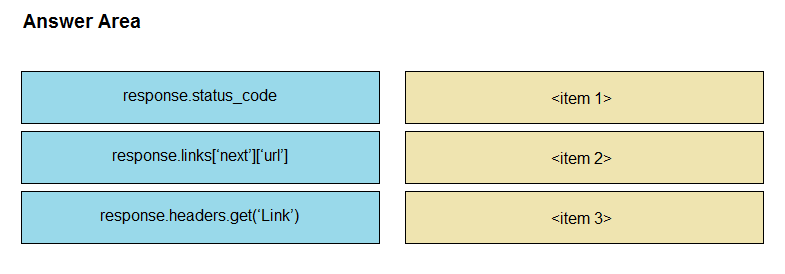
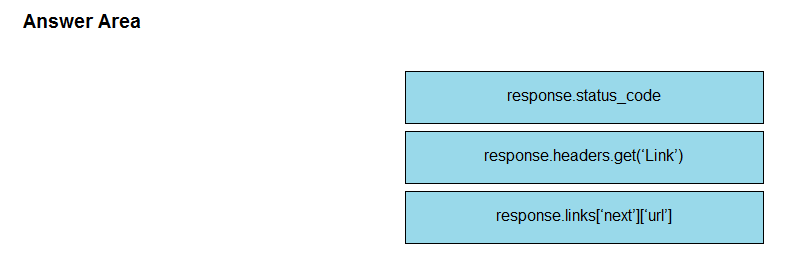
DRAG DROP -Refer to the exhibit. Drag and drop the parts of the Python code from the left onto the item numbers on the right that match the missing sections in the exhibit that consumes REST API pagination. Select and Place:
DRAG DROP - A Python script must query the Cisco DNA Center API for the number of unique wireless clients that are exhibiting poor health behavior. Drag and drop the code from the bottom onto the box where the code is missing to complete the script. Not all options are used.
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
A. Apply ip nat overload on VirtualPortGroup0.
B. Apply ip nat inside on Interface VirtualPortGroup0.
C. Apply ip nat outside on Interface VirtualPortGroup0.
D. Apply ip nat inside on Interface GigabitEthernet1.
An engineer oversees the development of an application that is hosted in the Python Django framework. Containerized microservices are used for the application logic. A remote database for state deposition is used. Which two monitoring solutions provide the application observability to assist with troubleshooting and debugging? (Choose two.)
A. integrated configuration environment
B. continuous deployment pipeline
C. security information and event management
D. resource utilization monitor
E. Cisco Intersight view
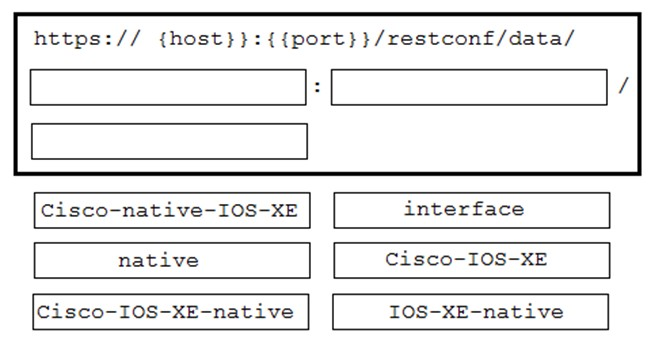
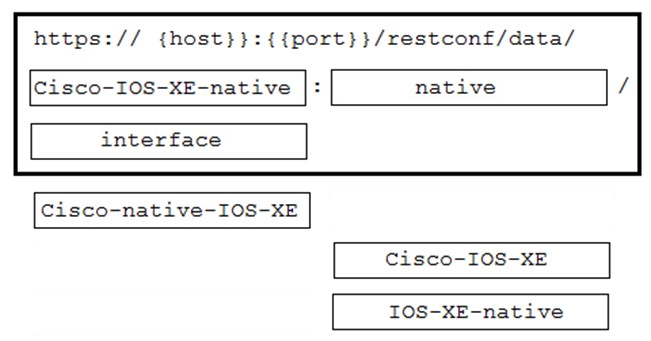
DRAG DROP - A network engineer needs to retrieve interface data using the Cisco IOS XE YANG Model. Drag and drop the components from the bottom onto the box where the code is missing to complete the RESTCONF URI. Not all options are used. Select and Place:
An application uses OAuth to get access to several API resources on behalf of an end user. What are two valid parameters to send to the authorization server as part of the first step of an authorization code grant flow? (Choose two.)
A. URI to which the authorization server will send the user-agent back when access is granted or denied
B. list of the API resources that the application is requesting to access
C. secret that was generated by the authorization server when the application registered as an OAuth integration
D. list of scopes that correspond to the API resources to which the application is requesting to access
E. name of the application under which the application registered as an OAuth integration
Refer to the exhibit. Two editors are concurrently updating an article's headline from their mobile devices. What results from this scenario based on this REST API sequence?
A. The article is marked as ג€Conflictedג€
B. The article headline is ג€Monday Headlinesג€
C. The article headline is ג€Today Headlinesג€
D. The article headline is ג€Top Headlinesג€
Access Full 350-901 Dump Free
Looking for even more practice questions? Click here to access the complete 350-901 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 350-901 dump free questions — and get one step closer to exam success!