350-701 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 350-701 certification exam? Kickstart your success with our 350-701 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 350-701 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 350-701 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Refer to the exhibit. A network engineer must retrieve the interface configuration on a Cisco router by using the NETCONF API. The engineer uses a Python script to automate the activity. Which code snippet completes the script?
A.

B.

C.

D.

Which DoS attack uses fragmented packets in an attempt to crash a target machine?
A. teardrop
B. smurf
C. LAND
D. SYN flood
An organization has had some malware infections recently and the management team wants to use Cisco Secure Firewall to enforce file policies to prevent malicious files from being downloaded. The SHA-256 hash value of all files traversing the firewall must be calculated and compared to the hash values of known malware code. Which file rule action is used to block only the files that are confirmed to be malware?
A. Block Malware
B. Detect Files
C. Malware Cloud Lookup
D. Block Files
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two.)
A. accounting
B. assurance
C. automation
D. authentication
E. encryption
Refer to the exhibit. What does the Python script accomplish?
A. It authenticates to a Cisco ISE server using the username or ersad.
B. It lists the LDAP users from the external identity store configured on Cisco ISE.
C. It authenticates to a Cisco ISE with an SSH connection.
D. It allows authentication with TLSv1 SSL protocol.
Which endpoint protection and detection feature performs correlation of telemetry, files, and intrusion events that are flagged as possible active breaches?
A. elastic search
B. file trajectory
C. indication of compromise
D. retrospective detection
What is the ideal deployment mode to use when you need to manage separate security policies for multiple customers on a Cisco ASA device?
A. spanned cluster mode
B. IRB mode
C. VRF mode
D. multiple context mode
When a Cisco WSA checks a web request, what occurs if it is unable to match a user-defined policy?
A. It applies the next identification profile policy.
B. It applies the global policy.
C. It applies the advanced policy.
D. It blocks the request.
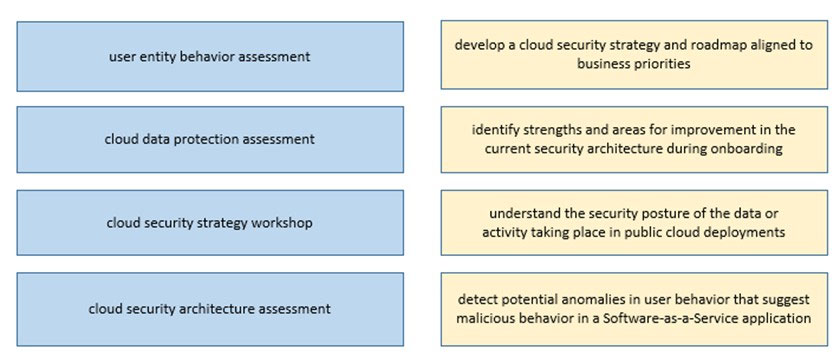
DRAG DROP - Drag and drop the cloud security assessment components from the left onto the definitions on the right. Select and Place:
Refer to the exhibit. What will occur when this device tries to connect to the port?
A. 802. 1X will not work, but MAB will start and allow the device on the network.
B. 802. 1X will work and the device will be allowed on the network.
C. 802. 1X will not work and the device will not be allowed network access.
D. 802. 1X and MAB will both be used and ISE can use policy to determine the access level.
An engineer is implementing NTP authentication within their network and has configured both the client and server devices with the command ntp authentication-key 1 md5 Cisc392481137. The server at 1.1.1.1 is attempting to authenticate to the client at 1.1.1.2, however is unable to do so. Which command is required to enable the client to accept the server's authentication key?
A. ntp server 1.1.1.2 key 1
B. ntp peer 1.1.1.2 key 1
C. ntp server 1.1.1.1 key 1
D. ntp peer 1.1.1.1 key 1
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
A. Service Provider managed
B. User managed
C. Public managed
D. Hybrid managed
E. Enterprise managed
Which feature does the IaaS model provide?
A. software-defined network segmentation
B. granular control of data
C. automatic updates and patching of software
D. dedicated, restricted workstations
An engineer is deploying a Cisco Secure Email Gateway and must ensure it reaches the Cisco update servers to retrieve new rules. The engineer must now manually configure the Outbreak Filter rules on an AsyncOS for Cisco Secure Email Gateway. Only outdated rules must be replaced. Up-to-date rules must be retained. Which action must the engineer take next to complete the configuration?
A. Use the outbreakconfig command in CLI.
B. Select Outbreak Filters.
C. Perform a backup/restore of the database.
D. Click Update Rules Now.
Which type of data does the Cisco Stealthwatch system collect and analyze from routers, switches, and firewalls?
A. NTP
B. SNMP
C. syslog
D. NetFlow
An engineer is configuring guest WLAN access using Cisco ISE and the Cisco WLC. Which action temporarily gives guest endpoints access dynamically while maintaining visibility into who or what connecting?
A. Configure ISE and the WLC for quest redirection and services using a self-registered portal.
B. Modify the WLC configuration to allow any endpoint to access an internet-only VLAN.
C. Configure ISE and the WLC for guest redirection and services using a hotspot portal.
D. Modify the WLC configuration to require local WLC logins for the authentication prompts.
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two.)
A. Check integer, float, or Boolean string parameters to ensure accurate values.
B. Use prepared statements and parameterized queries.
C. Secure the connection between the web and the app tier.
D. Write SQL code instead of using object-relational mapping libraries.
E. Block SQL code execution in the web application database login.
What are two ways that Cisco Container Platform provides value to customers who utilize cloud service providers? (Choose two.)
A. Allows developers to create code once and deploy to multiple clouds
B. helps maintain source code for cloud deployments
C. manages Docker containers
D. manages Kubernetes clusters
E. Creates complex tasks for managing code
Which attack is preventable by Cisco ESA but not by the Cisco WSA?
A. SQL injection
B. phishing
C. buffer overflow
D. DoS
What is the function of Cisco Cloudlock for data security?
A. data loss prevention
B. controls malicious cloud apps
C. detects anomalies
D. user and entity behavior analytics
What is the benefit of integrating Cisco ISE with a MDM solution?
A. It provides compliance checks for access to the network.
B. It provides the ability to update other applications on the mobile device.
C. It provides the ability to add applications to the mobile device through Cisco ISE.
D. It provides network device administration access.
Which feature is configured for managed devices in the device platform settings of the Firepower Management Center?
A. quality of service
B. time synchronization
C. network address translations
D. intrusion policy
Refer to the exhibit. What does the API key do while working with https://api.amp.cisco.com/v1/computers?
A. displays client ID
B. HTTP authorization
C. Imports requests
D. HTTP authentication
Refer to the exhibit. A company named ABC has a Cisco Secure Email Gateway and an engineer must configure the incoming mail policy so that emails containing malware files are quarantined instead of dropped and to prevent an increase in false positives causing emails to be dropped erroneously. What must be configured on the Secure Email Gateway?
A. Change the Policies Order.
B. Open Default Policy, Malware File, and then Action Applied to Message.
C. Delete usera1 policy.
D. Open usera1 policy, Messages with Malware Attachments, and then Action Applied to Message.
During a recent security audit, a Cisco IOS router with a working IPSEC configuration using IKEv1 was flagged for using a wildcard mask with the crypto isakmp key command. The VPN peer is a SOHO router with a dynamically assigned IP address. Dynamic DNS has been configured on the SOHO router to map the dynamic IP address to the host name of vpn.sohoroutercompany.com. In addition to the command crypto isakmp key Cisc123456789 hostname vpn.sohoroutercompany.com, what other two commands are now required on the Cisco IOS router far the VPN to continue to function after the wildcard command is removed? (Choose two.)
A. ip host vpn.sohoroutercompany.com
B. crypto isakmp identity hostname
C. Add the dynamic keyword to the existing crypto map command
D. fqdn vpn.sohoroutercompany.com
E. ip name-server
DRAG DROP - Drag and drop the descriptions from the left onto the encryption algorithms on the right.
What is the function of the Context Directory Agent?
A. reads the AD logs to map IP addresses to usernames
B. relays user authentication requests from Cisco WSA to AD
C. maintains users’ group memberships
D. accepts user authentication requests on behalf of Cisco WSA for user identification
Which action adds IOCs to customize detections for a new attack?
A. Use the initiate Endpoint 1OC scan feature to gather the IOC information and push it to clients.
B. Upload the 10Cs into the Installed Endpoint IOC feature within Cisco Secure Endpoint.
C. Add a custom advanced detection to include the 1OCs needed within Cisco Secure Endpoint.
D. Modify the base policy within Cisco Secure Endpoint to include simple custom detections.
What is a benefit of using telemetry over SNMP to configure new routers for monitoring purposes?
A. Telemetry uses push and pull, which makes it more secure than SNMP.
B. Telemetry uses push and pull, which makes it more scalable than SNMP.
C. Telemetry uses a push method, which makes it faster than SNMP.
D. Telemetry uses a pull method, which makes it more reliable than SNMP.
Which Cisco ASA deployment model is used to filter traffic between hosts in the same IP subnet using higher-level protocols without readdressing the network?
A. multiple context mode
B. single context mode
C. routed mode
D. transparent mode
Which security solution protects users leveraging DNS-layer security?
A. Cisco ISE
B. Cisco Umbrella
C. Cisco ASA
D. Cisco FTD
An organization wants to improve its cybersecurity processes and to add intelligence to its data. The organization wants to utilize the most current intelligence data for URL filtering, reputations, and vulnerability information that can be integrated with the Cisco FTD and Cisco WSA. What must be done to accomplish these objectives?
A. Configure the integrations with Talos intelligence to take advantage of the threat intelligence that it provides.
B. Download the threat intelligence feed from the IETF and import it into the Cisco FTD and Cisco WSA databases.
C. Create an automated download of the Internet Storm Center intelligence feed into the Cisco FTD and Cisco WSA databases to tie to the dynamic access control policies.
D. Create a Cisco pxGrid connection to NIST to import this information into the security products for policy use.
Which information is required when adding a device to Firepower Management Center?
A. username and password
B. encryption method
C. device serial number
D. registration key
Which Talos reputation center allows for tracking the reputation of IP addresses for email and web traffic?
A. IP Block List Center
B. IP and Domain Reputation Center
C. Cisco AMP Reputation Center
D. File Reputation Center
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains, IPs, and files, and helps to pinpoint attackers’ infrastructures and predict future threat?
A. Cisco Umbrella Investigate
B. Cisco Secure Network Analytics
C. Cisco pxGrid
D. Cisco Secure Cloud Analytics
Which protocol provides the strongest throughput performance when using Cisco AnyConnect VPN?
A. DTLSv1
B. TLSv1
C. TLSv1.1
D. TLSv1.2
What is a benefit of using GET VPN over FlexVPN within a VPN deployment?
A. GET VPN supports Remote Access VPNs
B. GET VPN uses multiple security associations for connections
C. GET VPN natively supports MPLS and private IP networks.
D. GET VPN interoperates with non-Cisco devices.
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to network resources?
A. BYOD onboarding
B. MAC authentication bypass
C. client provisioning
D. Simple Certificate Enrollment Protocol
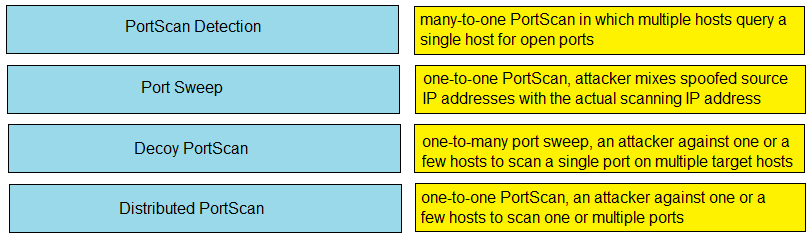
DRAG DROP - Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right. Select and Place:
DRAG DROP - Drag and drop the Cisco Secure Email Gateway benefits from the left to the corresponding deployment options on the right.
What is the primary difference between an Endpoint Protection Platform and an Endpoint Detection and Response?
A. EPP focuses on prevention, and EDR focuses on advanced threats that evade perimeter defenses.
B. EDR focuses on prevention, and EPP focuses on advanced threats that evade perimeter defenses.
C. EPP focuses on network security, and EDR focuses on device security.
D. EDR focuses on network security, and EPP focuses on device security.
What does Cisco AMP for Endpoints use to help an organization detect different families of malware?
A. Tetra Engine to detect malware when the endpoint is connected to the cloud
B. ClamAV Engine to perform email scanning
C. Spero Engine with machine learning to perform dynamic analysis
D. Ethos Engine to perform fuzzy fingerprinting
Which algorithm provides encryption and authentication for data plane communication?
A. AES-GCM
B. SHA-96
C. AES-256
D. SHA-384
What provides visibility and awareness into what is currently occurring on the network?
A. CMX
B. WMI
C. Cisco Prime Infrastructure
D. Telemetry
In which two customer environments is the Cisco WSAv connector traffic direction method selected? (Choose two.)
A. Customer owns ASA Appliance and Virtual Form Factor is required.
B. Customer does not own Cisco hardware and needs Explicit Proxy.
C. Customer owns ASA Appliance and SSL Tunneling is required.
D. Customer needs to support roaming users.
E. Customer does not own Cisco hardware and needs Transparent Redirection (WCCP).
Which solution stops unauthorized access to the system if a user's password is compromised?
A. MFA
B. AMP
C. VPN
D. SSL
Which technology provides a combination of endpoint protection, endpoint detection, and response?
A. Cisco Threat Grid
B. Cisco Umbrella
C. Cisco Talos
D. Cisco AMP
Which attack type attempts to shut down a machine or network so that users are not able to access it?
A. bluesnarfing
B. MAC spoofing
C. smurf
D. IP spoofing
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
A. smurf
B. distributed denial of service
C. cross-site scripting
D. rootkit exploit
An engineer is configuring a Cisco Secure Email Cloud Gateway instance to send logs to an external server for auditing. For security purposes, a username and SSH key with the fingerprint d0:46:03:8e:d7:f1:bb:9b:33:13:94:60:49:da:9b:e3 has been generated on the remote log server that accepts only the SSHv2 protocol. Which log retrieval method must be configured in the log subscription?
A. syslog push
B. manually download
C. SCP push
D. FTP push
Free Access Full 350-701 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 350-701 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 350-701 certification journey!