350-701 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 350-701 certification? Our 350-701 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 350-701 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 350-701 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which CoA response code is sent if an authorization state is changed successfully on a Cisco IOS device?
A. CoA-NAK
B. CoA-NCL
C. CoA-MAB
D. CoA-ACK
Which Cisco WSA feature supports access control using URL categories?
A. transparent user identification
B. SOCKS proxy services
C. web usage controls
D. user session restrictions
Which two endpoint measures are used to minimize the chances of falling victim to phishing and social engineering attacks? (Choose two.)
A. Patch for cross-site scripting.
B. Perform backups to the private cloud.
C. Protect against input validation and character escapes in the endpoint.
D. Install a spam and virus email filter.
E. Protect systems with an up-to-date antimalware program.
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
A. DNS tunneling
B. DNSCrypt
C. DNS security
D. DNSSEC
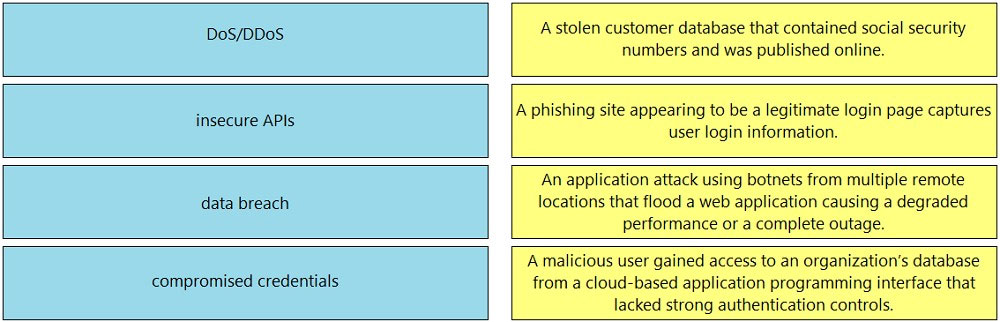
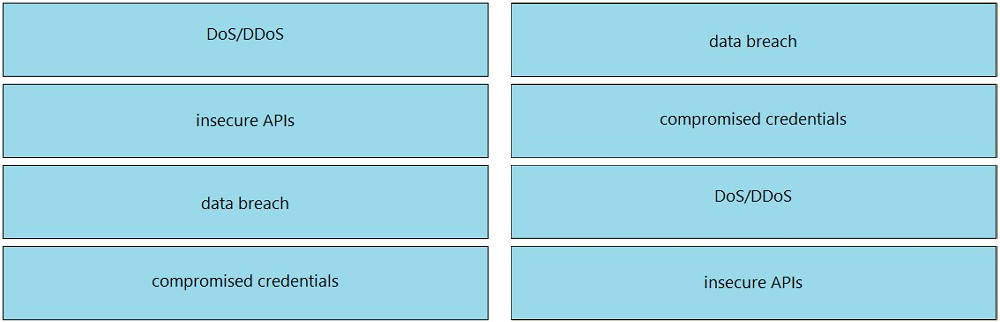
DRAG DROP - Drag and drop the threats from the left onto examples of that threat on the right. Select and Place:
Which firewall deployment mode allows inspection of traffic between servers in the same IP subnet?
A. routed
B. multicontext
C. virtual
D. transparent
An engineer is configuring cloud logging on Cisco ASA and needs events to compress. Which component must be configured to accomplish this goal?
A. Cisco analytics
B. CDO event viewer
C. SWC service
D. SDC VM
Which Cisco security solution secures public, private, hybrid, and community clouds?
A. Cisco ISE
B. Cisco ASAv
C. Cisco Cloudlock
D. Cisco pxGrid
A security engineer must add destinations into a destination list in Cisco Umbrella. What describes the application of these changes?
A. The changes are applied only after the configuration is saved in Cisco Umbrella.
B. The user role of Block Page Bypass or higher is needed to perform these changes.
C. The changes are applied immediately if the destination list is part of a policy.
D. The destination list must be removed from the policy before changes are made to it.
Which technology reduces data loss by identifying sensitive information stored in public computing environments?
A. Cisco SDA
B. Cisco Firepower
C. Cisco HyperFlex
D. Cisco Cloudlock
Refer to the exhibit. All servers are in the same VLAN/Subnet DNS Server-1 and DNS Server-2 must communicate with each other and all servers must communicate with default gateway multilayer switch. Which type of private VLAN ports should be configured to prevent communication between DNS servers and the file server?
A. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as promiscuous port, GigabitEthernet0/3 and GigabrtEthernet0/4 as isolated ports
B. Configure GigabitEthernet0/1 as community port, GigabitEthernet0/2 as isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as promiscuous ports
C. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as community port, and GigabitEthernet0/3 and GigabitEthernet0/4 as isolated ports
D. Configure GigabitEthernet0/1 as promiscuous port, GigabitEthernet0/2 as isolated port, and GigabitEthernet0/3 and GigabitEthernet0/4 as community ports
Refer to the exhibit. What is the result of this Python script of the Cisco DNA Center API?
A. adds a switch to Cisco DNA Center
B. receives information about a switch
C. deletes a switch from Cisco DNA Center
D. adds authentication to a switch
What are two trojan malware attacks? (Choose two.)
A. frontdoor
B. sync
C. smurf
D. rootkit
E. backdoor
Which SNMPv3 configuration must be used to support the strongest security possible?
A. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
B. asa-host(config)#snmp-server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
C. asa-host(config)#snmp-server group myv3 v3 noauth asa-host(config)#snmp-server user andy myv3 auth sha cisco priv 3des ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
D. asa-host(config)#snmp-server group myv3 v3 priv asa-host(config)#snmp-server user andy myv3 auth sha cisco priv aes 256 ciscXXXXXXXX asa-host(config)#snmp-server host inside 10.255.254.1 version 3 andy
How does Cisco Umbrella protect clients when they operate outside of the corporate network?
A. by forcing DNS queries to the corporate name servers
B. by modifying the registry for DNS lookups
C. by using the Cisco Umbrella roaming client
D. by using Active Directory group policies to enforce Cisco Umbrella DNS servers
Which process is used to obtain a certificate from a CA?
A. enrollment
B. registration
C. approval
D. signing
Refer to the exhibit.The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
A. P2 and P3 only
B. P5, P6, and P7 only
C. P1, P2, P3, and P4 only
D. P2, P3, and P6 only
Refer to the exhibit. A company named ABC has a Cisco Secure Email Gateway and an engineer must configure the incoming mail policy so that emails containing malware files are quarantined instead of dropped and to prevent an increase in false positives causing emails to be dropped erroneously. What must be configured on the Secure Email Gateway?
A. Change the Policies Order.
B. Open Default Policy, Malware File, and then Action Applied to Message.
C. Delete usera1 policy.
D. Open usera1 policy, Messages with Malware Attachments, and then Action Applied to Message.
Which algorithm does ISAKMP use to securely derive encryption and integrity keys?
A. RSA
B. AES
C. 3DES
D. Diffie-Hellman
Which action must be taken in the AMP for Endpoints console to detect specific MD5 signatures on endpoints and then quarantine the files?
A. Configure an advanced custom detection list.
B. Configure an IP Block & Allow custom detection list
C. Configure an application custom detection list
D. Configure a simple custom detection list
Which action blocks specific IP addresses whenever a computer with Cisco Secure Endpoint installed connects to the network?
A. Create an application block list and add the IP addresses.
B. Create an IP Block & Allow list and add the IP addresses.
C. Create an advanced custom detection policy and add the IP addresses.
D. Create a simple custom detection policy and add the IP addresses.
An engineer is adding a Cisco router to an existing environment. NTP authentication is configured on all devices in the environment with the command ntp authentication-key 1 md5 Cisc433392759. There are two routers on the network that are configured as NTP servers for redundancy, 192.168.1.110 and 192.168.1.111. 192.168.1.110 is configured as the authoritative time source. What command must be configured on the new router to use 192.168.1.110 as its primary time source without the new router attempting to offer time to existing devices?
A. ntp server 192.168.1.110 primary key 1
B. ntp server 192.168.1.110 key 1 prefer
C. ntp peer 192.168.1.110 prefer key 1
D. ntp peer 192.168.1.110 key 1 primary
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
A. because defense-in-depth stops at the network
B. because human error or insider threats will still exist
C. to prevent theft of the endpoints
D. to expose the endpoint to more threats
Which feature requires that network telemetry be enabled?
A. Layer 2 device discovery
B. per-interface stats
C. central syslog system
D. SNMP trap notification
An organization is using DNS services for their network and want to help improve the security of the DNS infrastructure. Which action accomplishes this task?
A. Use DNSSEC between the endpoints and Cisco Umbrella DNS servers.
B. Modify the Cisco Umbrella configuration to pass queries only to non-DNSSEC capable zones.
C. Integrate Cisco Umbrella with Cisco CloudLock to ensure that DNSSEC is functional.
D. Configure Cisco Umbrella and use DNSSEC for domain authentication to authoritative servers.
An engineer is deploying Cisco Advanced Malware Protection (AMP) for Endpoints and wants to create a policy that prevents users from executing a file named abc123456789.exe without quarantining that file. What type of Outbreak Control list must the SHA-256 hash value for the file be added to in order to accomplish this?
A. Advanced Custom Detection
B. Simple Custom Detection
C. Isolation
D. Blocked Application
In which form of attack is alternate encoding, such as hexadecimal representation, most often observed?
A. smurf
B. distributed denial of service
C. cross-site scripting
D. rootkit exploit
Which Cisco ISE service checks the state of all the endpoints connecting to a network for compliance with corporate security policies?
A. Threat Centric NAC service
B. posture service
C. Cisco TrustSec
D. compliance module
An organization wants to implement a cloud-delivered and SaaS-based solution to provide visibility and threat detection across the AWS network. The solution must be deployed without software agents and rely on AWS VPC flow logs instead. Which solution meets these requirements?
A. NetFlow collectors
B. Cisco Cloudlock
C. Cisco Stealthwatch Cloud
D. Cisco Umbrella
Which feature is supported when deploying Cisco ASAv within AWS public cloud?
A. multiple context mode
B. user deployment of Layer 3 networks
C. IPv6
D. clustering
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
A. Cisco Container Controller
B. Cisco Cloud Platform
C. Cisco Container Platform
D. Cisco Content Platform
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
A. Port Bounce
B. CoA Terminate
C. CoA Reauth
D. CoA Session Query
Which two Cisco ISE components must be configured for BYOD? (Choose two.)
A. local WebAuth
B. central WebAuth
C. null WebAuth
D. guest
E. dual
Which feature must be configured before implementing NetFlow on a router?
A. syslog
B. IP routing
C. VRF
D. SNMPv3
How is ICMP used as an exfiltration technique?
A. by flooding the destination host with unreachable packets
B. by sending large numbers of ICMP packets with a targeted hosts source IP address using an IP broadcast address
C. by encrypting the payload in an ICMP packet to carry out command and control tasks on a compromised host
D. by overwhelming a targeted host with ICMP echo-request packets
What is a characteristic of a bridge group in a Cisco ASA Firewall running in transparent mode?
A. It has an IP address on its BVI interface and is used for management traffic.
B. It allows ARP traffic with a single access rule.
C. It includes multiple interfaces and access rules between interfaces are customizable.
D. It is a Layer 3 segment and includes one port and customizable access rules.
What are two benefits of adaptive multifactor authentication? (Choose two.)
A. no need to remember passwords
B. secure remote access
C. contextual factor-based authentication
D. improved access management
E. managed encryption policies
An engineer must modify a policy to block specific addresses using Cisco Umbrella. The policy is created already and is actively used by devices, using many of the default policy elements. What else must be done to accomplish this task?
A. Create a destination list for addresses to be allowed or blocked
B. Use content categories to block or allow specific addresses
C. Add the specified addresses to the identities list and create a block action
D. Modify the application settings to allow only applications to connect to required addresses
In which cloud services model is the tenant responsible for virtual machine OS patching?
A. IaaS
B. UCaaS
C. PaaS
D. SaaS
An engineer is configuring Cisco Umbrella and has an identity that references two different policies. Which action ensures that the policy that the identity must use takes precedence over the second one?
A. Place the policy with the most-specific configuration last in the policy order
B. Configure the default policy to redirect the requests to the correct policy
C. Make the correct policy first in the policy order
D. Configure only the policy with the most recently changed timestamp
Which baseline form of telemetry is recommended for network infrastructure devices?
A. SDNS
B. NetFlow
C. passive taps
D. SNMP
Which Cisco ASA Platform mode disables the threat detection features except for Advanced Threat Statistics?
A. cluster
B. multiple context
C. routed
D. transparent
What is a characteristic of Firepower NGIPS inline deployment mode?
A. ASA with Firepower module cannot be deployed
B. It cannot take actions such as blocking traffic
C. It is out-of-band from traffic
D. It must have inline interface pairs configured
A website administrator wants to prevent SQL injection attacks against the company’s customer database, which is referenced by the web server. Which two methods help prevent SQL injection attacks? (Choose two.)
A. using load balancers with NAT
B. performing input validation
C. enforcing TLS 1.3 only
D. using SSL certificates
E. using web application firewalls
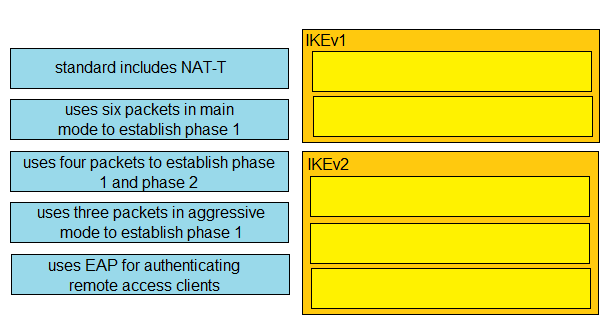
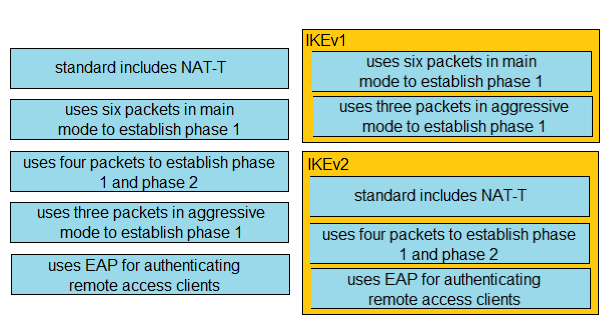
DRAG DROP - Drag and drop the descriptions from the left onto the correct protocol versions on the right. Select and Place:
Which common exploit method is TLS 1.3 designed to prevent?
A. man-in-the-middle attack
B. denial-of-service attack
C. cross-site request forgery
D. cross-site scripting
What must be configured in Cisco ISE to enforce reauthentication of an endpoint session when an endpoint is deleted from an identity group?
A. SNMP probe
B. CoA
C. external identity source
D. posture assessment
What is a difference between encrypted passwords and hardcoded passwords?
A. Encrypted passwords are easier to obtain, and hardcoded passwords are known only to developers.
B. Encrypted passwords are generated by an application user, and hardcoded passwords are generated randomly.
C. Encrypted passwords are used for frontend applications, and hardcoded passwords are used for backend applications.
D. Encrypted passwords are stored in a database, and hardcoded passwords are embedded in the source code.
Which two probes are configured to gather attributes of connected endpoints using Cisco Identity Services Engine? (Choose two.)
A. RADIUS
B. TACACS+
C. DHCP
D. sFlow
E. SMTP
An administrator enables Cisco Threat Intelligence Director on a Cisco FMC. Which process uses STIX and allows uploads and downloads of block lists?
A. editing
B. sharing
C. authoring
D. consumption
Access Full 350-701 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 350-701 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 350-701 certification journey!