350-601 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 350-601 certification exam? Start your preparation the smart way with our 350-601 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 350-601 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 350-601 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Refer to the exhibit. An engineer is troubleshooting intermittent connect issues between the client PC and the DHCP server. What does the last package captured from the Cisco Nexus 2000 Series Switch indicate?
A. The client receives an IP address from the DHCP server.
B. The DHCP server sends an IP address via a broadcast message.
C. The client sends a unicast message to receive an IP address from the DCHP server.
D. The DCHP server releases the IP address from the client.
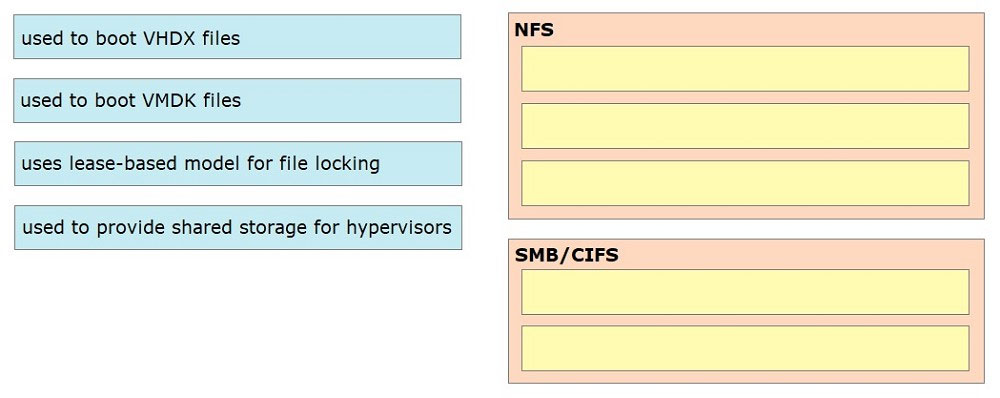
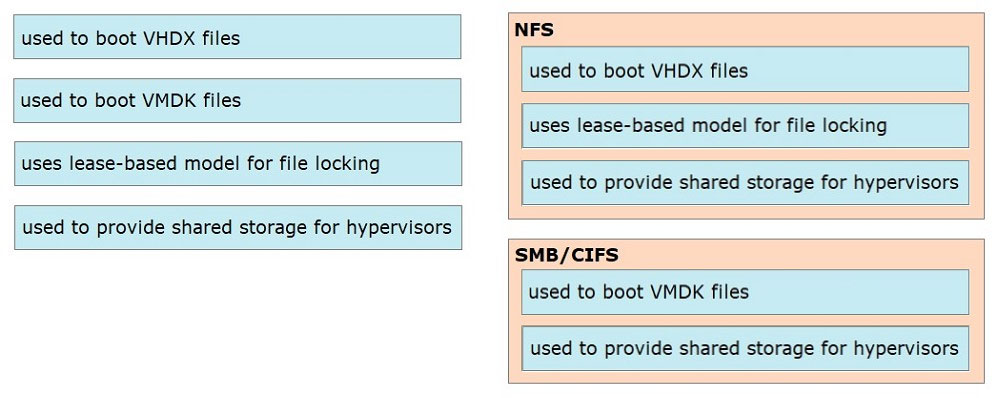
DRAG DROP - Drag and drop the characteristics from the left onto the NAS protocols on the right. Some characteristics are used more than once. Select and Place:
A network engineer is configuring the Cisco UCS service profile template with Ansible using this code: hostname: 192.168.10.23 username: cisco password: f718c4329405726531f6247ff982 name: DCE-CTRL template_type: updating-template uuid_pool: UUID-POOL storage_pronte: DCE-StgProf maintenance_policy: default server_pool: Container-Pool host_firmware_package: 4.1(1a) bios_policy: Docker Which attribute must be used to apply the iSCSI initiator identifiers to all iSCSI vNICs for the service profiles derived from the service template?
A. san_connectivity_policy
B. lan_connectivity_policy
C. boot_policy
D. iqn_pool
A network engineer must restore the running configuration on a Cisco Nexus 5000 Series Switch to an existing snapshot called `stable1`. The restore procedure should proceed only if no errors occur. Which configuration should be used to accomplish this goal?
A. rollback running-config checkpoint stable1 best-effort
B. rollback running-config checkpoint stable1 atomic
C. rollback checkpoint stable1 best-effort running-config best-effort
D. rollback checkpoint stable1 best-effort running-config atomic
What are two requirements when planning a Cisco HyperFlex All Flash standard cluster installation using three Cisco HX240c M5 Series servers? (Choose two.)
A. If the Jumbo MTU option in the HyperFlex installer is enabled, then jumbo frames do not have to be enabled on the upstream switches.
B. This cluster deployment type must support a mix of HDD and SSD.
C. The servers must be discovered, unassociated, and connected to each fabric interconnect.
D. If the Jumbo MTU option in the HyperFlex installer is enabled, then jumbo frames must also be enabled on the upstream switches.
E. The hypervisors must be installed to Cisco FlexFlash SD cards.
A network administrator attempts to automate the provisioning of several new Cisco Nexus switches. The administrator prepares a bootstrap configuration script for the task. Due to the number of switches, a zero-touch provisioning solution is preferred. Additionally, some switches arrive with outdated software and should be automatically upgraded as part of the provisioning workflow. Which solution meets the requirements?
A. Ansible
B. NX-API
C. POAP
D. DHCP
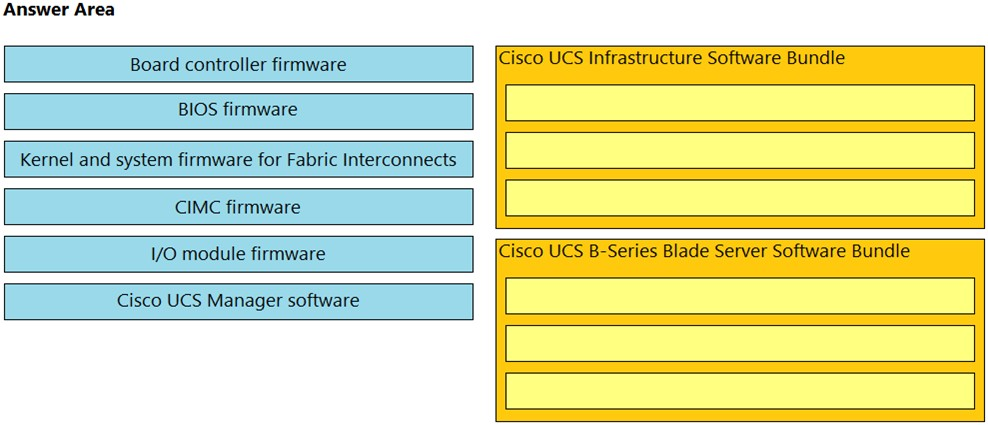
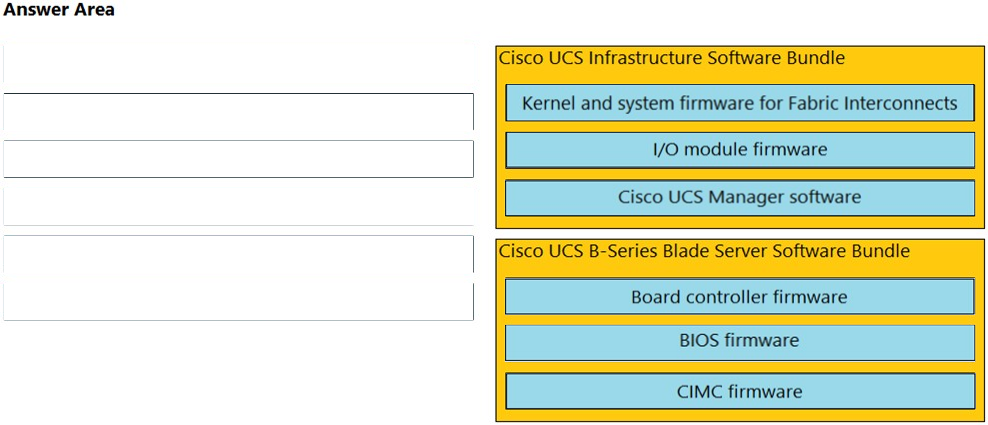
DRAG DROP - Drag and drop the firmware packages from the left onto the software bundles they belong to on the right. Select and Place:
Refer to the exhibit. What is the result of executing this Python code?
A. It sends the switch configuration to Cisco TAC
B. It sends a Cisco device backup to a remote destination
C. It schedules a backup on a Cisco switch using EEM
D. It backs up Cisco switches to Cisco Prime Infrastructure

Refer to the exhibit. A network engineer must monitor the traffic from the server on VLAN 80. All source traffic from the server must be captured on the monitoring device. Which configuration set meets these requirements?
A. switch(config-monitor)# destination interface ethernet 1/1switch(config-monitor)# source vlan 80
B. switch(config-monitor)# destination interface ethernet 1/1switch(config-monitor)# filter vlan 80
C. switch(config-monitor)# destination interface ethernet 1/2switch(config-monitor)# filter vlan 80 rx tx
D. switch(config-monitor)# destination interface ethernet 1/2switch(config-monitor)# source vlan 80 rx
What are two capabilities of the Cisco Network Assurance Engine? (Choose two.)
A. It validates that devices comply with network security policies.
B. It predicts the impact of changes to the network.
C. It predicts the network load on a data center.
D. It ensures that network performance meets an SLA.
E. It verifies the speed of network packet flows by using telemetry.
DRAG DROP - Refer to the exhibit.Drag and drop the code snippets from the bottom onto the blanks in the code to complete the JSON request that implements the ACL presented. Not all code snippets are used.
A customer reports Fibre Channel login requests to a Cisco MDS 9000 Series Switch from an unauthorized source. The customer requires a feature that will allow all devices already logged in and learned to be added to the Fibre Channel active database. Which two features must be enabled to accomplish this goal? (Choose two.)
A. auto-learning
B. smart aliases
C. port security
D. enhanced zoning
E. device aliases
Refer to the exhibit. An engineer must upgrade the N9K_2 device to the latest code. In preparation for the upgrade, the engineer wants to divert all data plane traffic between RTR_1 and RTR_2 to N9K_4 and N9K_5. The traffic redirection must happen without forcing any OSPFv2 adjacency change in the network. Which configuration set must be used on N9K_2 OSPF process 1 to accomplish these goals?
A. area 0 stub no-summary
B. passive-interface default
C. max-metric router-lsa
D. area 0 filter-list route-map DENY_ALL out
Which mroute state is created when Bidirectional PIM is deployed at a site?
A. *,G
B. MVPN Type-6
C. MVPN Type-7
D. S,G
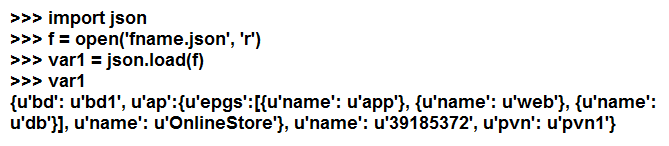
Which data structure results from running this Python code?
A. tuple
B. dictionary
C. set
D. list
What is a feature of an electronic programmable logic device upgrade on a Cisco MDS 9000 Series Switch?
A. Only the modules that are being upgraded are disrupted.
B. An EPLD upgrade is disruptive on all modules.
C. The standby supervisor module can perform the upgrade.
D. An EPLD upgrade is nondisruptive on all modules.
Which two components should be checked when a Cisco Nexus 9000 Series Switch fails to boot using POAP? (Choose two.)
A. POAP feature license
B. DHCP server to bootstrap IP information
C. image noted in the script file against switch bootflash
D. script signed with security key
E. TFTP server that contains the configuration script
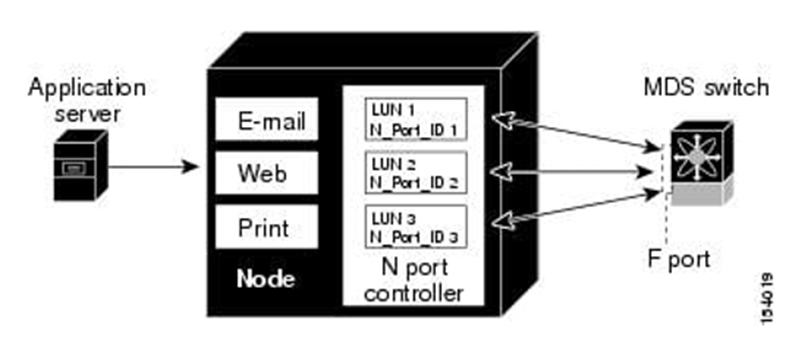
Which two actions must be taken to directly connect a Fibre Channel storage array to a Cisco UCS domain? (Choose two.)
A. Configure a Fibre Channel port channel.
B. Configure the Fibre Channel port as a Fibre Channel storage port.
C. Create a new vHBA dedicated to the storage array.
D. Create a Storage Connection Policy.
E. Configure a new VSAN.
Refer to the exhibit. A source is sending a multicast traffic stream to the receiver. How is the multicast traffic expected to flow through the network when it reaches a vPC peer?
A. • The multicast traffic is not replicated to the ports that joined a multicast group (224.0.0.13) or the peer link.• The multicast traffic stream flows over the vPC link to ensure that orphan ports get the multicast stream in failure scenarios.
B. • The multicast traffic is replicated to the ports that joined a given multicast group and the peer link.• The multicast traffic stream flows from Agg-1 to Agg-2 over the M1-to-M2 peer link and forwards the traffic over Layer 4 to Access-2.
C. • The multicast traffic is replicated to the ports that joined a given multicast group and the peer link.• The multicast traffic stream flows over the peer link to ensure that orphan ports receive the multicast stream in failure scenarios.
D. • The multicast traffic is not replicated to the ports that joined a multicast group (224.0.0.13) or the peer link.• The multicast traffic stream flows from Agg-1 to Agg-2 over the M1-to-M2 peer link and forwards the traffic over Layer 4 to Access-2.
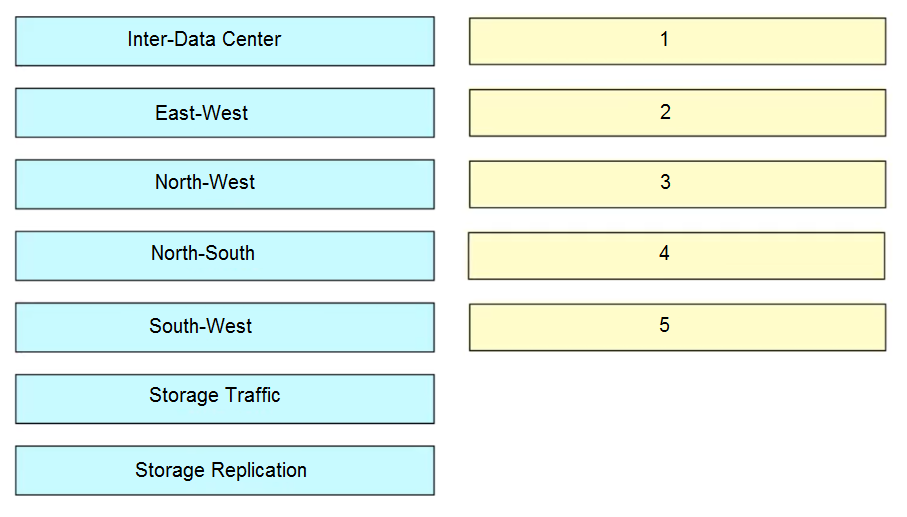
DRAG DROP -Refer to the exhibit. Drag and drop each traffic flow type from the left onto the corresponding number on the right. Not all traffic flow types are used. Select and Place:
An engineer must automate the provisioning of Cisco ACI objects using the Terraform tool. The engineer must ensure that APIC counts the authentication login requests against the threshold to avoid a DOS attack. Which configuration must be used in Terraform to accomplish these goals?
A. resources with user ID and password
B. resources with signature-based authentication
C. provider with user ID and password
D. provider with signature-based authentication
A network engineer configures a converged network adapter (CNA) and must associate a virtual Fibre Channel 7 interface to VSAN 7. The CNA is connected to the interface Eth1/7, and VLAN 700 is mapped to the VSAN. Which configuration must be applied to create the virtual Fibre Channel interface and associate it with the Ethernet physical interface?
A. switch(config)# interface vfc 7 switch(config-if)# bind interface ethernet 1/7
B. switch(config)# vlan 700 switch(config-vlan)# fcoe vsan 7
C. switch(config)# vsan database switch(config-vsan)# vsan 7 interface vfc 7
D. switch(config)# interface ethernet 1/7 switch(config-if)# vfc 7 attach vlan 1,700
Refer to the exhibit. SVR-A in EPG-A/BD-A fails to reach SVR-B in EPG-B/BD-B. Which two conditions should be verified to analyze the traffic between the two EPGs? (Choose two.)
A. A contract exists between EPG-A and EPG-B and allows the traffic.
B. The bridge domain for EPG-B floods ARP packets.
C. EPG-A and EPG-B are excluded from the preferred group.
D. Limit Endpoint Learning is disabled on the bridge domain for EPG-B.
E. SVR-B is learned as an endpoint in EPG-B from Node-112.
Refer to the exhibit. The MDS-EDGE-Switch and MDS-Core-Switch are configured with NPV and NPIV features. The FLOGI from Cisco UCS is received by the MDS-Core-Switch on interface fc1/2. An engineer tried to move all traffic between the MDS-EDGE-Switch and MDS-Core-Switch from interface fc1/2 to fc1/3, but the attempt failed. Which set of actions completes the configuration?
A. Shut down fc1/1 in the MDS-EDGE-Switch. Re-apply the command. Enable interface fc1/1.
B. Disable the NPIV feature in the MDS-EDGE-Switch. Re-enable the NPIV feature. Disable interface fc1/3.
C. Disable the NPV feature in the MDS-EDGE-Switch. Re-enable the NPV feature. Disable interface fc1/1.
D. Shutdown fc1/3 in the MDS-EDGE-Switch. Re-apply the command. Enable interface fc1/3.
An engineer implements an environment with multiple traffic types on a consolidated I/O link between Cisco Nexus 9000 Series Switch and MDS 9000 Series Switch. The configuration must meet these requirements: • The unified I/O link must support LAN and SAN traffic. • A single, multipurpose Ethernet transport must be used. • The configuration must discard MAC addresses that are not part of the current fabric. • The QoS markings must be preserved. Which configuration set meets the requirements?
A. MDS-A(config)# interface fcip4 -MDS-A(config-if)# use-profile 8 -MDS-A(config-if)# peer-info ipaddr 200.200.100.7
B. N9K-2(config)# interface Eth2 -N9K-2(config-if)# switchport mode trunkN9K-2(config-if)# auto qos trust dscp
C. MDS-B(config)# interface fc3 -MDS-B(config-if)# switchport trunk mode onMDS-B(config-if)# switchport trunk allowed vsan 2-5
D. N9K-1(config)# fcoe fcmap 0e.fc.1dN9K-1(config)# int vfc 1 -N9K-1(config-if)# bind interface e1/3
An engineer must implement a Cisco UCS system at a customer site. One of the requirements is to implement SAN boot. The storage system maps the source WWPN to a unique LUN. Which method does Cisco recommend to configure the SAN boot?
A. Define the vHBAs as bootable and leave the boot target definition empty.
B. Create a SAN boot policy in which every initiator is mapped to a different target LUN.
C. Define the vHBAs as bootable and leave the default values on the boot target definition.
D. Create a SAN boot policy in which every initiator is mapped to the same target LUN.
What is required for using Ansible with HTTP/HTTPS protocol in a Cisco NX-OS environment?
A. XML management interface
B. SSH
C. Open Agent Container
D. NX-API
A new employee must be granted access to add VLANs into an existing Cisco UCS Manager and configure NTP synchronization with date and time zone settings. Which two privileges must be granted to the employee to complete the task? (Choose two.)
A. Service Profile Compute (ls-compute)
B. Ext LAN Policy (ext-lan-policy)
C. Service Profile Network Policy (ls-network-policy)
D. Service Profile Config (ls-config)
E. Ext LAN Config (ext-lan-security)
A storage array must be connected to port ethernet1/10 on a Cisco MDS 9000 Series Switch. In addition, the array must connect using the FCoE protocol and be single-homed. Which configuration meets these requirements?
A. vsan database vlan 101 vsan 101 fcoe vsan 101 interface vfc 10 interface 1/10 switchport mode e fcoe vfc 10
B. interface vfc 10 switchport mode f bind interface ethernet 1/10 vsan database vsan 101 vlan 101 fcoe vsan 101 vsan 101 interface vfc 10
C. vlan database vlan 101 vsan vsan 101 fcoe vsan 101 interface vfc 10 interface ethernet1/10 switchport mode trunk bind interface vfc 10 fcoe vsan 101
D. vlan database vlan 101 fcoe vsan 101 enable interface vfc 10 vsan 101 interface vfc 10 switchport mode fcoe switchport access vlan 101 bind interface ethernet1/10
A new user with access privileges in the Finance department moves to a new Admin department. The user must have access privileges to the Admin department data and applications inside the Cisco UCS Manager. Which set of changes must be implemented in Cisco UCS Central for the user to acquire the privileges?
A. Disable the Finance user account and add the authentication service for the Admin privileges.
B. Create a new locale Admin and add the Admin department to the Admin locale.
C. Create an Admin user account and remove the authentication service for the Finance privileges.
D. Delete the old locale Finance and remove the Finance department from the Finance locale.
Refer to the exhibit. An engineer must distribute all the host ports to use all eight configured FEX uplinks. The solution must minimize disruption if an uplink fails. Which action accomplishes this objective?
A. Set the pinning max-links value to 8
B. Configure the eight uplinks in a port channel
C. Change the supported FEX type
D. Statically assign each host interface to a fabric uplink
Refer to the exhibit. A network engineer requires remote access via SSH to a Cisco MDS 9000 Series Switch. The solution must support secure access using the local user database when the RADIUS servers are unreachable from the switches. Which command meets these requirements?
A. aaa authentication none
B. aaa authentication login default group radius
C. aaa authentication login default fallback error local
D. aaa authentication login default group local
Refer to the exhibit. Server1 is connected to a Cisco Nexus 9000 Series Switch via a 1-Gb port channel. The storm control is applied to the Eth0 device with a zero percent value. What does the switch do to traffic that traverses the switch interfaces during the streaming window that exceeds the bandwidth of the interfaces?
A. suppresses all traffic
B. forwards all traffic
C. drops all of the excess traffic
D. forwards half of the traffic
What does this configuration create?
A. three subnets within a bridge domain
B. a CTX1 tenant
C. an L3OUT-1 bridge domain
D. two L3Out domains
An engineer is converting a Cisco MDS switch to support NPIV mode. What should be considered when implementing the solution?
A. It requires mapping of external interface traffic.
B. It must be enabled on VSAN 1 only.
C. It must be enabled globally on all VSANs.
D. It requires the FLOGI database to be disabled.
A network automation engineer must configure a Cisco NX-OS REST API on a Cisco 9000 Series Switch with these requirements: • NX-API REST and the DME database must be enabled. • The NX-API REST must listen for HTTP traffic on port 83. • The HTTPS certificate must be uploaded. Which configuration set must be used to accomplish these goals?
A. feature nxapinxapi (tcp) port 83nxapi certificate {httpscrt}
B. feature nxapinxapi (tcp) port 83nxapi certificate {httpscrt}nxapi certificate enable
C. feature nxapinxapi (http) port 83nxapi certificate {httpscrt}
D. feature nxapinxapi {http} port 83nxapi certificate {httpscrt | httpskey}nxapi certificate enable
Which Cisco UCS Manager XML encoded backup type must be used to back up user names, roles, and service profiles?
A. System Configuration
B. Full State Configuration
C. Logical Configuration
D. All Configuration
An engineer configures a storage environment for a customer with high-security standards. The secure environment is configured in VSAN 50. The customer wants to maintain a configuration and active databases and prevent unauthorized switches from joining the fabric. Additionally, the switches must prevent rogue devices from connecting to their ports by automatically learning the WWPNs of the ports connected to them for the first time. Which two configuration sets must be used to meet these requirements? (Choose two.)
A. fcsp enablefcsp auto-active
B. port-security enableport-security activate vsan 50
C. clear fabric-binding activate vsan 50fabric-binding activate vsan 50
D. fcsp dhchap hash md5 sha1
E. fabric-binding activate vsan 50 force
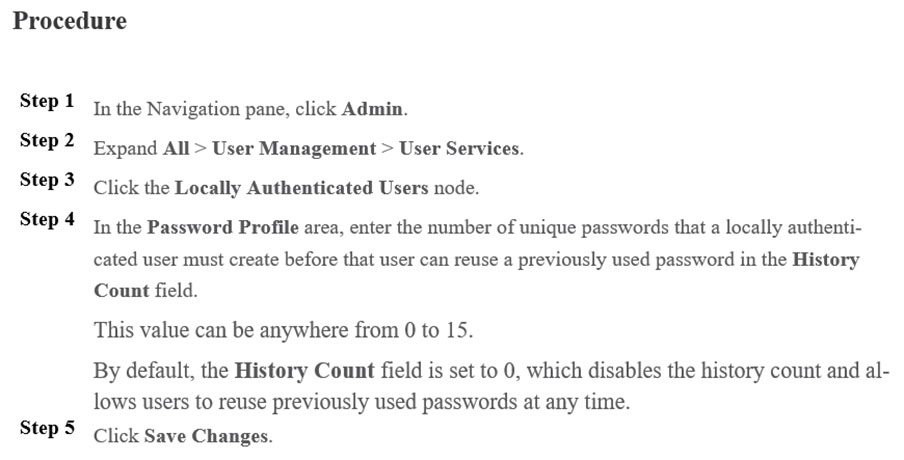
Refer to the exhibit.Which setting must be configured to prevent the reuse of passwords?
A. Change Interval
B. No Change Interval
C. History Count
D. Change Count
What is an advantage of NAS compared to SAN?
A. It provides lossless throughput.
B. It offers enhanced NFS features.
C. It functions in an existing IP environment.
D. It offers enhanced security features.
What is a benefit of Cisco HyperFlex All-Flash Stretched cluster deployment as compared to All-HDD Stretched cluster deployment?
A. lower number of IOPS
B. higher number of IOPS
C. lower cost
D. higher cost
An engineer must perform an initial configuration of VXLAN Tunnel End-Point functionality on the Cisco Nexus 9000 Series platform. All the necessary features are already enabled on the switch. Which configuration set must be used to accomplish this goal?
A. NX9K(config)# interface loopback0 NX9K(config-if)# ip address 10.10.10.11/32 NX9K(config)# interface VLAN10 NX9K(config-if)# ip unnumbered loopback0 NX9K(config)# interface nve1 NX9K(contig-if-nve)# source-interface loopback0
B. NX9K(config)# interface loopback0 NX9K(config-if)# ip address 10.10.10.11/32 NX9K(config)# interface overlay0 NX9K(config-if-overlay)# source-interface loopback0 NX9K(config)# interface VLAN10 NX9K(contig-if-nve)# source-interface loopback0
C. NX9K(config)# interface loopback0 NX9K(config-if)# ip address 10.10.10.11/32 NX9K(config)# interface tunnel1 NX9K(config-if)# tunnel source loopback0 NX9K(config)# interface ethernet1/1 NX9K(contig-if)# ip unnumbered loopback0
D. NX9K(config)# interface loopback0 NX9K(config-if)# ip address 10.10.10.11/32 NX9K(config)# interface nve1 NX9K(config-if-nve)# source-interface loopback0 NX9K(config)# interface ethernet1/1 NX9K(contig-if)# ip unnumbered loopback0
What is the benefit of adding Cisco HyperFlex Hardware Acceleration Cards to a HyperFlex deployment?
A. increased compression efficiency
B. increased network throughput
C. GPU acceleration
D. offline encryption acceleration
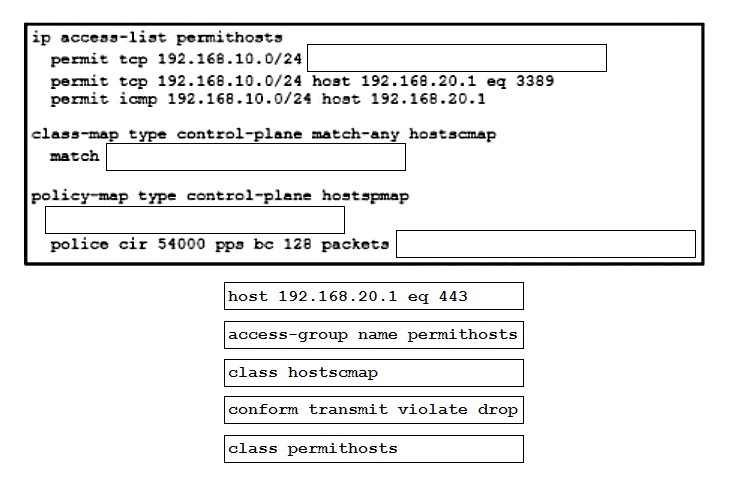
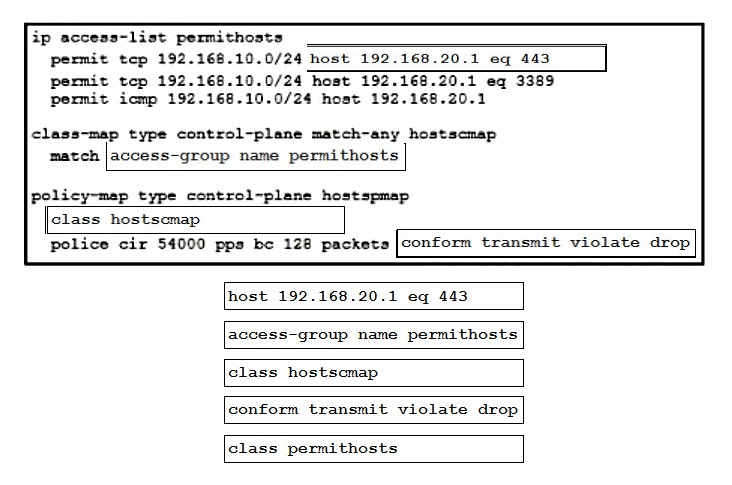
DRAG DROP - An engineer must configure a control plane policy on a Cisco Nexus 9000 Series Switch that is located at IP 192.168.20.1 that meets these requirements: ✑ Only HTTP, RDP, and ICMP traffic is permitted from subnet 192.168.10.0/24. ✑ The committed information rate must be 54000 pps. ✑ The burst size must be 128 packets. ✑ Any other traffic must be dropped. Drag and drop the code snippets from the bottom onto the blanks in the code on the top to complete the configuration. Not all code snippets are used. Select and Place:
An engineer must design an automation solution for the Cisco ACI Fabric to speed up the deployment of logical network elements for tenant provisioning. When creating a solution, the engineer must keep in mind that the tool must support these requirements: * Allow the rapid creation and removal of logical containers. * Support the creation of custom modules and data structures. * Be extensible with external libraries and modules. * Allow rapid testing of code using an on-demand execution environment. Which automation tool meets these requirements?
A. SaltStack
B. YAML
C. Chef
D. Python
Refer to the exhibit. An engineer needs to implement a monitoring session that should meet the following requirements: ✑ Monitor traffic from leaf to leaf switches on a Cisco ACI network ✑ Support filtering traffic from Bridge Domain or VRF Which configuration must be added to meet these requirements?
A. interface eth 1/2 leaf 101
B. application epg epg1 app1
C. interface eth 1/2 switch 101
D. application app1 epg epg1
An engineer must implement a solution that prevents untrusted DHCP servers from compromising the network. The feature must be configured on a Cisco Nexus 7000 Series Switch and applied to VLAN 10. The legitimate DHCP servers are connected to interface Ethernet 2/4. Which configuration set must be used to meet these requirements?
A. n7k-1(config)# ip dhcp snooping vlan 10 n7k-1(config)# interface Ethernet2/4 n7k-1(config-if)# ip dhcp snooping verify vlan 10
B. n7k-1(config)# ip dhcp snooping verify n7k-1(config)# interface Ethernet2/4 n7k-1(config-if)# ip dhcp snooping verify vlan 10
C. n7k-1(config)# ip dhcp snooping vlan 10 n7k-1(config)# interface Ethernet2/4 n7k-1(config-if)# ip dhcp snooping trust
D. n7k-1(config)# ip dhcp snooping verify n7k-1(config)# vlan configuration 10 n7k-1(config-vlan)# ip dhcp snooping trust
An engineer installed a new Nexus switch with the mgm0 interface in vrf management. Connectivity to the rest of the network needs to be tested from the guest shell of the NX-OS. Which command tests connectivity from the guest shell of the NX-OS?
A. [guestshell@guestshell ~]$ dohost ”ping vrf management 173.37.145.84”
B. [guestshell@guestshell ~]$ chvrf management ping 173.37.145.84
C. [guestshell@guestshell ~$ ping 173.37.145.84 vrf management
D. [guestshell@guestshell ~]$ iping vrf management ip 173.37.145.84
What is the impact of a nondisruptive upgrade on fabric and modular switches?
A. The upgrade disrupts the control plane for more than 120 seconds.
B. During the upgrade, new devices cannot log in to the fabric.
C. If a zone server merge is in progress, the upgrade continues without interruption.
D. When the installation is complete, the system BIOS must be updated.
When the default firmware package is set to a new version, which type of policy determines the timing of server reboots during the firmware upgrade?
A. diagnostics
B. maintenance
C. local disk
D. BIOS
Access Full 350-601 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 350-601 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 350-601 mock test free today—and take a major step toward exam success!