350-601 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 350-601 certification? Our 350-601 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 350-601 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 350-601 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Refer to the exhibit. Two data center fabrics use VPC data center interconnect. The system MAC value on SW1 is 00:23:04:ee:be:20. Which value must be set to configure the system MAC address?
A. 00:23:04:ee:be:14 on SW3
B. 00:23:04:ee:be:20 on SW3
C. 00:23:04:ee:be:14 on SW2
D. 46:43:32:e5:92:80 on SW2
Refer to the exhibit. A host with a source address 10.10.10.10 sends traffic to multicast group 239.1.1.1. How do the vPC switches forward the multicast traffic?
A. If multicast traffic is received on Switch1 over the vPC peer-link, the traffic is dropped
B. If multicast traffic is received on Po10 Switch1, the traffic is forwarded out on Po1 and Po20
C. If multicast traffic is received on Po11 Switch2, the traffic is forwarded out only on Po20
D. If multicast traffic is received on Po11 Switch2, the traffic is dropped.
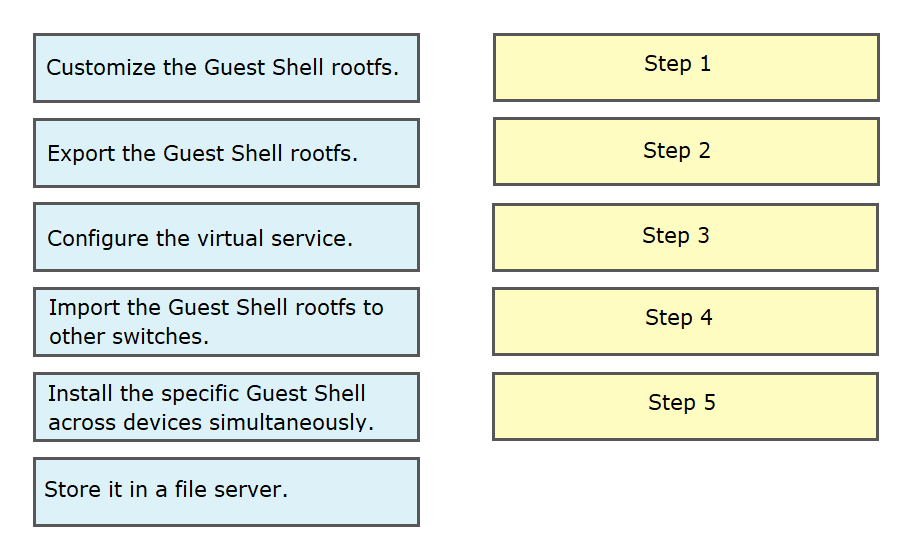
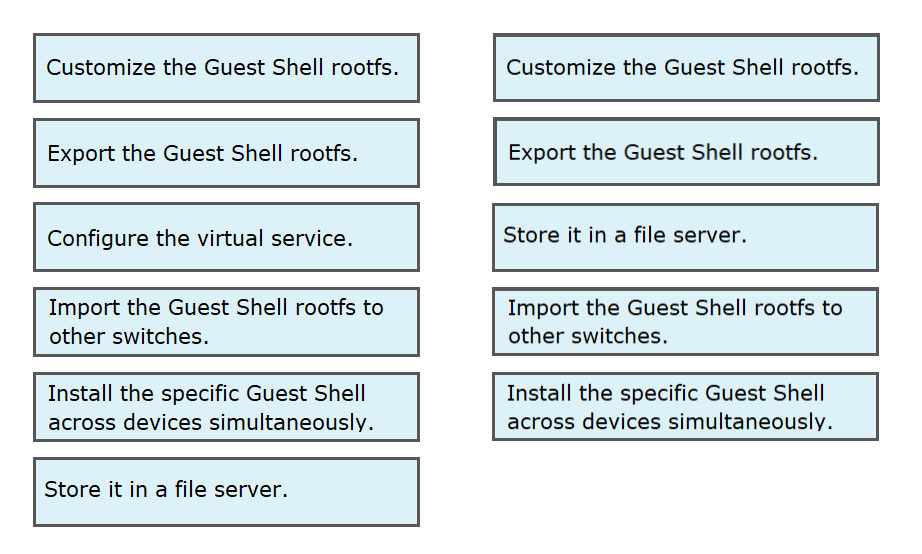
DRAG DROP - An engineer deploys a custom Guest Shell rootfs on a Nexus 9000 Series Switch. Drag and drop the steps from the left into the order required to deploy the solution on the right. Not all options are used. Select and Place:
Refer to the exhibit.
An engineer is implementing an ERSPAN configuration to mirror web server traffic connected to N7K-2. Which ERSPAN configuration must be applied on N7K-1 to forward traffic to the network analyzer?
A.

B.

C.

D.

Refer to the exhibit. An engineer uses Python in Cisco NX-OS guest shell to retrieve the configuration of the EIGRP ASN on interface eth1/1. The engineer has written this script: >>> import json >>> from cli import* Which command set must be used to retrieve the value of the 'asn' key?
A. >>> output = json.loads(clid(‘show ip eigrp neighbors’))>>> output[‘TABLE_asn’][‘ROW_asn’][‘asn’]
B. >>> output = json.dumps(clid(‘show ip eigrp neighbors’))>>> output[‘TABLE_asn’][‘ROW_asn’][‘asn’]
C. >>> output = json.dumps(clid(‘show ip eigrp neighbors’))>>> output[‘asn’]
D. >>> output = json.loads(clid(‘show ip eigrp neighbors’))>>> output[‘asn’]
Which statement describes monitoring Fibre Channel traffic on a Cisco UCS 6332 Fabric Interconnect?
A. Fibre Channel traffic is monitored only on one vHBA per server.
B. Fibre Channel traffic is capable to be monitored as it is encapsulated as FCoE.
C. The monitoring of Fibre Channel traffic is limited to the default VSAN.
D. The destination port for monitoring must be an unassigned Fibre Channel port.
Refer to the exhibit.An engineer configures a new application profile using REST API and receives this error message. Which method can be used before the application profile can be configured?
A. GET to aaaListDomains
B. POST to aaaRefresh
C. POST to aaaLogin
D. POST to aaaLogout
An engineer configures a storage environment for a customer with high-security standards. The secure environment is configured in VSAN 50. The customer wants to maintain a configuration and active databases and prevent unauthorized switches from joining the fabric. Additionally, the switches must prevent rogue devices from connecting to their ports by automatically learning the WWPNs of the ports connected to them for the first time. Which two configuration sets must be used to meet these requirements? (Choose two.)
A. fcsp enablefcsp auto-active
B. port-security enableport-security activate vsan 50
C. clear fabric-binding activate vsan 50fabric-binding activate vsan 50
D. fcsp dhchap hash md5 sha1
E. fabric-binding activate vsan 50 force
Refer to the exhibit. An engineer must create a Bash script to run in the Cisco NX-OS Guest Shell. The script must loop through the available namespaces and output all registered interfaces. Which code snippet completes the script?
A. chvrf “$ns”;
B. echo “$ns”;
C. ifconfig “$ns”;
D. vrfinfo”$ns”;
A small remote office is set to connect to the regional hub site via NSSA ASBR. Which type of LSA is sent to the remote office OSPF area?
A. type 7 LSA
B. type 1 LSA
C. type 5 LSA
D. type 3 LSA
An engineer must configure RBAC in Cisco UCS Manager in an existing data center environment. Which two roles are suitable for configuring LAN connectivity policies? (Choose two.)
A. server-profile
B. network-admin
C. operations
D. enable
E. admin
DRAG DROP -Refer to the exhibit. An engineer implements a dynamically negotiated LACP port channel on SW1. The port channel members must be configured as active/standby ports with Eth1/2 as active and Eth1/1 as standby. The Eth1/1 interface is configured with default priority. Drag and drop the code snippets from the right onto the blanks in the code on the left to complete the Eth1/2 interface configuration for SW1. Not all code snippets are used.
A customer has a requirement to deploy a cloud service and needs to have full control over the underlying OS, data and applications. Which cloud model meets this requirement?
A. MaaS
B. PaaS
C. SaaS
D. IaaS
What is the benefit of using the Cisco Nexus Dashboard single sign-on feature?
A. It provides notifications about end of sale for the deployed switches.
B. It adds a security layer based on multifactor authentication.
C. It manages operations of the infrastructure using a single pane of glass.
D. It allows the user to switch seamlessly between the hosted services.
Which component becomes unavailable for a maximum of 80 seconds during a nondisruptive Cisco NX-OS upgrade?
A. supervisor module
B. default VSAN
C. control plane
D. data plane
Refer to the exhibit. A network engineer configures the VXLAN between the routers in a data center. The VLAN 10 must be extended between routers A and B. The initial VXLAN configuration is completed on Router A. Which configuration finishes the VXLAN configuration on Router A?
A. system bridge-domain 10member vni 10010interface nve1no shutdownsource-interface Io0
B. Interface nve1 -no shutdownsource-interface Io0vni 10100 I2rd auto
C. Interface nve1 -no shutdownsource-interface Io0member vni 10010 mcast-group 231.1.1.1
D. vrf context tenant1vni 10010Interface nve1 -source-interface Io0no shutdownmember vni 10010 interface 10.10.0.1
Refer to the exhibit. A network engineer must configure port E1/31-32 to forward only storage server traffic of VLAN 200 on Cisco fabric interconnects A and B. Port E1/31-32 is not reserved for any other traffic. Which port type must be configured to accomplish this goal?
A. FCoE storage
B. uplink
C. unified uplink
D. FCoE uplink
An engineer is implementing VSANs on a Cisco MDS 9000 Series Switch with a native Fibre Channel. The deployment must meet these requirements: • The host on port fc1/1 must be assigned to VSAN 10. • The port channel 10 ISL must pass multiple VSANs, including VSAN 10. Which configuration set meets these requirements?
A. Activate VSAN 10 in the vFC interface.Associate VSAN 10 to interface vfc 1/1.Enable vsan F-port-channel-trunk on the ISL.Set encapsulation EISL on the switch port.
B. Create VSAN 10 in the VSAN database.Bind VSAN 10 to interface fc1/1 in the VSAN database.Enable VSAN trunking on the ISL.Allow VSAN 10 on the ISL.
C. Configure VSAN 10 in the interface configuration.Attach VSAN 10 to the VSAN database.Enable VSAN trunking on fc1/1.Filter all VSAN on the ISL.
D. Disable VSAN 1 in the VSAN database.Assign VSAN 10 to the ISL.Enable VSAN trunking on the port channel members.Permit VSAN 10 in the FLOGI database.
Which feature of Cisco Nexus Dashboard permits users to switch between site controllers of Cisco ACI?
A. multifactor authentication
B. single sign-on
C. air-gap support
D. cloud-site onboarding
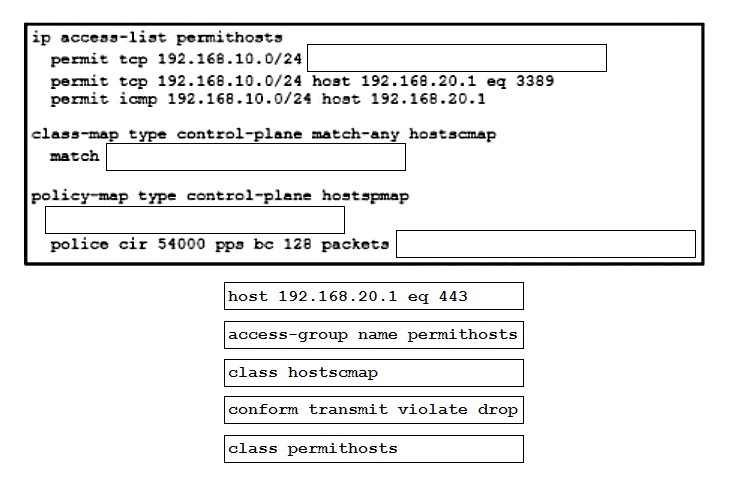
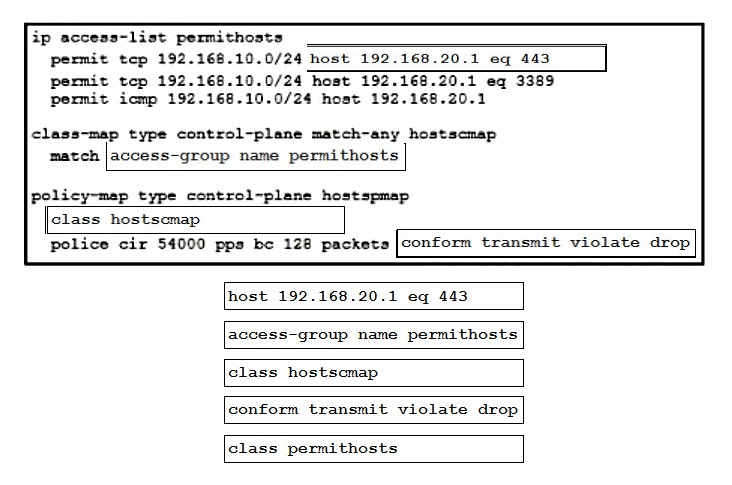
DRAG DROP - An engineer must configure a control plane policy on a Cisco Nexus 9000 Series Switch that is located at IP 192.168.20.1 that meets these requirements: ✑ Only HTTP, RDP, and ICMP traffic is permitted from subnet 192.168.10.0/24. ✑ The committed information rate must be 54000 pps. ✑ The burst size must be 128 packets. ✑ Any other traffic must be dropped. Drag and drop the code snippets from the bottom onto the blanks in the code on the top to complete the configuration. Not all code snippets are used. Select and Place:
DRAG DROP - Drag and drop the NAS and NFS concepts from the left onto the definitions on the right.
A network architect is asked to design and manage geographically distributed data centers across cities and decides to use a Multi-Site Orchestrator deployment. How many orchestrators should be deployed?
A. 5
B. 3
C. 4
D. 2
Which NFS version uses the TCP protocol and needs only one IP port to run the service?
A. NFSv1
B. NFSv2
C. NFSv3
D. NFSv4
Refer to the exhibit. An engineer must configure port security on the Cisco Nexus 5000 Series Switch that meets these requirements: • Port security must be applied on VSAN 10 only. • NWWN 20:10:10:10:10:10:10:10 to log in through SAN port-channel 2. • Any WWN must be allowed to log in through interfaces fc1/1, fc1/2, fc1/3. • Auto learning must be disabled. Which command set satisfies these conditions?
A. Nexus5K(config)# port-security database vsan 10Nexus5K(config-port-security)# nwwn 20:10:10:10:10:10:10:10 interface san-port-channel 2Nexus5K(config-port-security)# any wwn interface fc1/1-3Nexus5K(config-port-security)# port-security commit vsan 10
B. Nexus5K(config)# port-security activate vsan 10 no auto-learnNexus5K(config)# port-security database vsan 10Nexus5K(config-port-security)# nwwn 20:10:10:10:10:10:10:10 interface san-port-channel 2Nexus5K(config-port-security)# any wwn interface fc1/1-3
C. Nexus5K(config)# port-security database vsan 10Nexus5K(config-port-security)# nwwn 20:01:01:01:01:01:01:01 interface san port-channel 5Nexus5K(config-port-security)# any wwn interface fc1/1-3Nexus5K(config)# port-security database diff active vsan 10
D. Nexus5K(config)# port-security database vsan 10Nexus5K(config-port-security)# nwwn 20:01:01:01:01:01:01:01 interface port-channel 5Nexus5K(config-port-security)# any wwn interface fc1/1-3Nexus5K(config)# port-security database diff active vsan 10
An environment consists of a Cisco MDS 9000 Series Switch that uses port channels. An engineer must ensure that frames between the source and the destination follow the same links for a specific flow. Subsequent flows are allowed to use a different link. Which load balancing method should be used to accomplish this goal?
A. src-id/dst-id
B. src-dst-oui
C. src-dst-port
D. src-id/dst-id/oxid
An engineer must recover the Cisco UCS system. The full backup is available on a backup SCP server. Which set of actions recovers the configuration of the Cisco UCS Manager?
A. Create an import-config task.Set the action to Replace.
B. Copy the backup file to a USB drive.Copy the running-config.
C. Factory reset the fabric interconnect.Select the Restore feature.
D. Create a scheduled restore job.Reboot the UCS Manager.
Which two settings must be configured before enabling a Cisco UCS Manager domain for Cisco Intersight connectivity? (Choose two.)
A. SMTP servers
B. SMTP reply-to address
C. NTP servers
D. syslog redirection
E. DNS servers
An infrastructure architect is analyzing the deployment type for an application. Several companies must be able to operate the application environment and integrate it with a third-party protocol. The development team also must have maximum control over their development environment, including the operating system used, Python interpreter, and corresponding libraries. Which cloud deployment solution meets these requirements?
A. private cloud Platform as a Service
B. public cloud Storage as a Service
C. hybrid cloud Software as a Service
D. community cloud Infrastructure as a Service
Refer to the exhibit. A network administrator experiences these issues with the network: • PC1 is experiencing a buffering problem for video applications. • The servers that are connected to SW2 are experiencing packet drops when they connect to the Internet. The engineer wants to configure the required traffic capture to investigate the issue further. Which configuration must be implemented to monitor the traffic?
A. N9K(config)# monitor session 5 txN9K(config-monitor)# description Span_session_5N9K(config-monitor)# source vlan 10-15 rxN9K(config-monitor)# source interface ethernet 1/2N9K(config-monitor)# destination interface ethernet 2/3
B. N9K(config)# monitor session 5 rxN9K(config)# monitor session 5 txN9K(config-monitor)# description Span_session_5N9K(config-monitor)# source interface ethernet 1/1N9K(config-monitor)# source interface ethernet 1/2N9K(config-monitor)# destination interface ethernet 2/3
C. N9K(config)# monitor session 5 txN9K(config-monitor)# description Span_session_5N9K(config-monitor)# source interface ethernet 1/1N9K (config-monitor)# source interface ethernet 1/2N9K(config-monitor)# destination interface ethernet 2/3
D. N9K(config)# monitor session 5 rxN9K(config-monitor)# description Span_session_5N9K(config-monitor)# source vlan 10 rxN9K(config-monitor)# source interface ethernet 1/2N9K(config-monitor)# destination interface ethernet 2/3
An engineer must implement an automation solution to allow the backup of the configuration of Cisco Nexus Series Switches to a centralized location. The solution must: * support the team-developed custom monitoring scripts that are packaged using RPM packaging that the framework must support. * be decoupled from the underlying Cisco Nexus operating system. * have no impact on the operating system of the underlying switch if the resource contention occurs. * use Python to expand the existing automation framework. Which solution meets these requirements?
A. Guest Shell
B. Vegas Shell
C. Bash Shell
D. TCL Shell
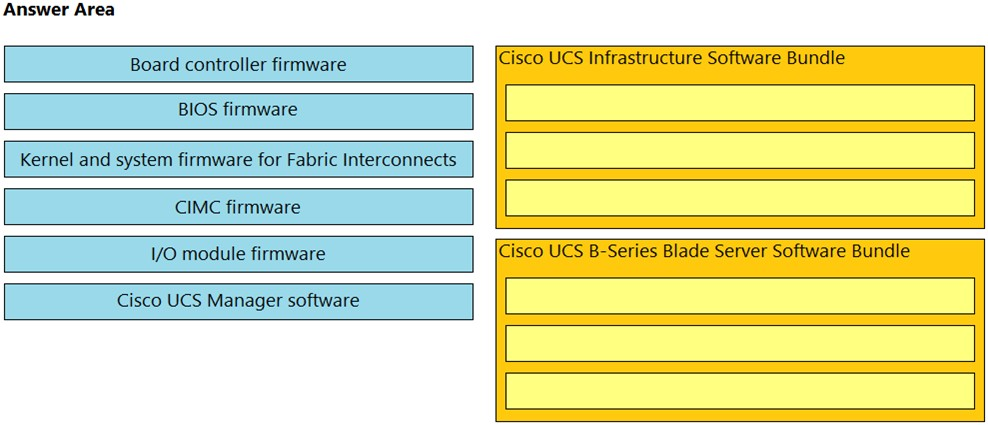
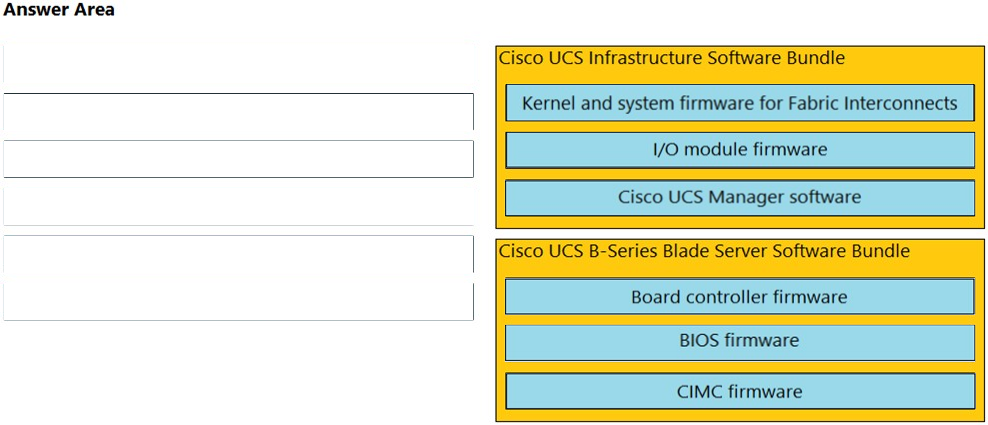
DRAG DROP - Drag and drop the firmware packages from the left onto the software bundles they belong to on the right. Select and Place:
An engineer is performing a configuration on a Cisco Nexus 5000 Series Switch. The requirement is for the current Fibre Channel IDs in VSAN 120 to be saved across reboots. The Cisco environment also must integrate with a third-party solution that requires persistent Fibre Channel IDs for the VSAN. The WWN of the Cisco switch must be 33:e8:00:05:30:00:16:df and its Fibre Channel ID 0x070128. Which command set meets these requirements?
A. fcdomain fcid database vsan 120 wwn 33:e8:00:05:30:00:16:df fcid 0x070128 fcdomain fcid persistent vsan 120
B. fabric-binding database vsan 120 vsan 120 wwn 33:e8:00:05:30:00:16:df fcid 0x070128
C. vsan 120 wwn 33:e8:00:05:30:00:16:df fcid 0x070128 fabric-binding activate vsan 120 purge fcdomain fcid vsan 4
D. ysan 120 wwn 33:e8:00:05:30:00:16:df fcid 0x070128 fcdomain fcid preserve vsan 120
An engineer must configure a monitoring solution for a Cisco Nexus 9000 Series Switch based data center. The solution must provide real-time insight into the network health with subscription-based monitoring. The monitoring must be initiated from the client side, and the data must be sent via encryption. Which configuration steps complete the configuration?
A. Configure Grafana on the Nexus switch. Specify the logging certificate. Enable syslog level 7 export to Grafana.
B. Set the telemetry feature on the Nexus switch. Specify a certificate for telemetry transport. Configure a sensor group and destination.
C. Activate SNMPv3 on the Nexus switch. Set the globalEnforcePriv parameter. Configure an SNMP agent to poll information.
D. Enable GRPC on the Nexus switch. Generate a certificate. Configure gNMI inputs in Telegraf and output to InfluxDB.
What does WWPN uniquely identify in this Fibre Channel fabric?
A. interface
B. zone
C. area
D. switch
Port security is statically configured on a Cisco Nexus 7700 Series switch and F3 line card. The switch is configured with an Advanced Services license. Which two actions delete secured MAC addresses from the interface? (Choose two.)
A. The address must be removed from the configuration.
B. Shutdown and then no shutdown must be run on the interface.
C. The device must be restarted manually.
D. The address must reach the age limit that is configured for the interface.
E. The interface must be converted to a routed port.
A network administrator attempts to automate the provisioning of several new Cisco Nexus switches. The administrator prepares a bootstrap configuration script for the task. Due to the number of switches, a zero-touch provisioning solution is preferred. Additionally, some switches arrive with outdated software and should be automatically upgraded as part of the provisioning workflow. Which solution meets the requirements?
A. Ansible
B. NX-API
C. POAP
D. DHCP
Refer to the exhibit. An engineer must mirror the traffic on a switch. The engineer locates the server port that requires monitoring on switch1, but the packet sniffer is on switch2. The engineer must configure the source IP address on switch1. Which command accomplishes this goal?
A. source ip 209.165.200.225
B. monitor session 10 type erspan-source
C. source interface vlan512
D. monitor erspan origin ip-address 209.165.200.225
Refer to the exhibit. An engineer must upgrade the N9K_2 device to the latest code. In preparation for the upgrade, the engineer wants to divert all data plane traffic between RTR_1 and RTR_2 to N9K_4 and N9K_5. The traffic redirection must happen without forcing any OSPFv2 adjacency change in the network. Which configuration set must be used on N9K_2 OSPF process 1 to accomplish these goals?
A. area 0 stub no-summary
B. passive-interface default
C. max-metric router-lsa
D. area 0 filter-list route-map DENY_ALL out
Which component is disrupted when the Cisco Integrated Management Controller is upgraded on a Cisco UCS Series Server?
A. SAN traffic
B. Cisco UCS Manager
C. KVM sessions
D. data traffic
An engineer must perform an initial configuration of VXLAN and MP-BGP EVPN on the Cisco Nexus 9000 Series platform. The underlay must be OSPF, and the VTEP must run with distributed default gateway on a VLAN interface. Which command set must be applied to meet these requirements?
A. NX9K(config)# feature nv overlayNX9K(config)# feature vn-segment-vlan-basedNX9K(config)# feature bgp -NX9K(config)# nv overlay-evpn -NX9K(config)# feature ospf -NX9K(config)# feature interface-vlan
B. NX9K(config)# feature nv overlayNX9K(config)# feature bfd -NX9K(config)# feature vn-segment-vlan-basedNX9K(config)# nv overlay-evpn -NX9K(config)# feature ngmvpn -NX9K(config)# feature ospf –
C. NX9K(config)# feature nv overlayNX9K(config)# feature bfd -NX9K(config)# feature fabric forwardingNX9K(config)# feature vn-segment-vlan-basedNX9K(config)# nv overlay-evpn -NX9K(config)# feature ospfv3 –
D. NX9K(config)# feature nv overlayNX9K(config)# feature bgp -NX9K(config)# feature bfd -NX9K(config)# feature ngmvpn -NX9K(config)# feature ospf -NX9K(config)# feature interface-vlan
The network team needs permissions to access the Cisco UCS B-Series Servers via the Cisco UCS Manager GUI to configure the network and collect information about faults. The administrator wants to assign these permissions to the newly configured user called netops. Which set of tasks must the administrator perform to accomplish these goals?
A. Implement username netops on the locally authenticated user.Assign the roles of network administrator and operations.
B. Configure username netops on the Cisco UCS Manager login profile.Assign the roles of AAA administrator and operations.
C. Enable username netops on the authenticated users.Assign the roles of storage administrator and facility manager.
D. Deploy username netops on the users locales.Assign the roles of networks security and facility manager.
Refer to the exhibit.A DevOps engineer must create a PowerShell script to display a list of tenants in the Cisco Application Centric Infrastructure (ACI) by using the Cisco ACI PowerShell module. The engineer does NOT know how many results will be returned, so it is important to iterate through all the results. Which code snippet completes the script?
A.

B.

C.

D.

An engineer must add a new VRF (DC:DC) to the network that runs with Multiprotocol Border Gateway Protocol (MP-BGP) and EVPN. The requirement for the new VRF is to allow communication of network prefixes between PE1 and PE2. Which two sets of steps should be taken to complete the VRF configuration? (Choose two.)
A.

B.

C.

D.

E.

Which two statements describe the process of upgrading an EPLD on a Cisco MDS 9000 Series Switch? (Choose two.)
A. EPLDs are only capable to be upgraded to the latest EPLD image.
B. EPLD upgrades are capable to be completed without powering down the module during the upgrade.
C. An upgrade verification identifies the impact of each EPLD upgrade.
D. The EPLDs for all the modules on a switch must be upgraded at the same time.
E. EPLDs are capable to be upgraded without replacing the hardware.
An engineer must implement a VXLAN-based data center interconnect. The long-distance transport provided by a service provider is IP-based, supports a maximum MTU of 1554 bytes, and does not support outbound traffic replication. Which action must be taken to build the data center interconnect?
A. Announce host reachability over BGP.
B. Create an IP access list and associate it with VNI to replicate traffic to remote VTEPs.
C. Configure a route map to associate the IPs of the remote VTEPs.
D. Implement BGP EVPN ingress replication.
Refer to the exhibit.What is the outcome of this command when the EPLD is updated on a Cisco Nexus 9000 Series Switch?
A. displays the compatibility of the EPLD upgrade and the image in the bootflash
B. shows a simulated upgrade of the EPLD
C. upgrades the EPLD on the switch disruptively
D. displays the impact of the upgrade on the operation of the switch
A content delivery network sends video traffic to a multicast distribution device where the receiver requests the traffic from the multicast distribution device through an IGMP join message. When the traffic reaches the multicast distribution device from a CDN, the switching network populates the multicast routing table in the group (S,G), and the multicast distribution device sends the required traffic back to the receiver. Which feature is used to send back the traffic from the streamer to the receiver in the group (S,G)?
A. RP
B. Source Specific Multicast
C. Reverse Path Forwarding
D. IGMP
Refer to the exhibit.An administrator connects a Cisco Nexus Series Switch to the Cisco ACI fabric. The connectivity must allow Cisco Discovery Protocol, LLDP, and LACP. Which action enables the protocols between Switch-1 and the ACI leaf switches?
A. Implement an interface policy group.
B. Activate a leaf interface.
C. Enable an existing interface selector.
D. Configure an interface profile.
Refer to the exhibit.An engineer implements an FCoE Unified Fabric where vPC exists between N9K-A and N9K-B. To avoid rate discards, bandwidth must be regulated to account for sent traffic that exceeds the access speed. Which set of commands completes the configuration?
A. fcoe cost 255 on N9K-Arandom-detect min 10 max 20spanning-tree port type edge on Po10
B. fcoe cost 0 on N9K-Ashape min 0 gbps max 1 gbpsspanning-tree port type edge on Po1
C. fcoe fcf-priority 0 on N9K-Ahardware qos fc rate-shaper lowspanning-tree port type edge trunk on Po10
D. fcoe fcf-priority 255 on N9K-Apolice 50000spanning-tree port type edge trunk on Po1
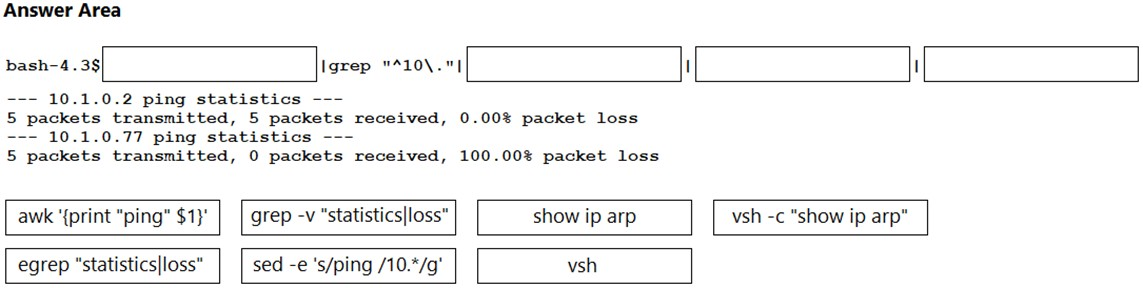
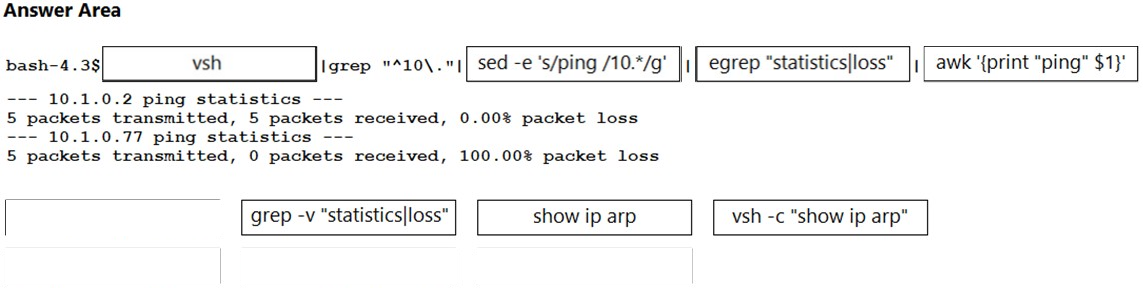
DRAG DROP - A network administrator must automate the process of pinging all the IP addresses from the 10.0.0.0/8 subnet. The subnet is already present on the ARP table of the Cisco Nexus switch. Drag and drop the bash commands to generate the desired output. Not all commands are used. Select and Place:
Access Full 350-601 Dump Free
Looking for even more practice questions? Click here to access the complete 350-601 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 350-601 dump free questions — and get one step closer to exam success!