350-401 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 350-401 certification exam? Start your preparation the smart way with our 350-401 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 350-401 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 350-401 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Refer to the exhibit. What does the Python code accomplish?
A. It configures interface e1/32 to be in an admin down state
B. It generates a status code of 403 because the type is incorrect.
C. It configures interface e1/32 to be in an err-disable state.
D. It returns data in JSON-RPC format.
Which technology does VXLAN use to provide segmentation for Layer 2 and Layer 3 traffic?
A. bridge domain
B. VLAN
C. VNI
D. VRF
Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand event none action 1.0 syslog priority critical msg ‘This is a message from ondemand’
B. event manager applet ondemand action 1.0 syslog priority critical msg ‘This is a message from ondemand’
C. event manager applet ondemand event register action 1.0 syslog priority critical msg ‘This is a message from ondemand’
D. event manager applet ondemand event manual action 1.0 syslog priority critical msg ‘This is a message from ondemand’
Refer to the exhibit.Running the script causes the output in the exhibit. What should be the first line of the script?
A. from ncclient import manager
B. import manager
C. from ncclient import *
D. ncclient manager import
Which security actions must be implemented to prevent an API injection attack?
A. Log and monitor failed attempts.
B. Use password hash with biometric authentication.
C. Validate, filter, and sanitize all incoming data.
D. Use short-lived access tokens and authenticate the apps.
Drag and drop the characteristics from the left onto the corresponding switching architectures on the right.
Select and Place:
DRAG DROP - Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
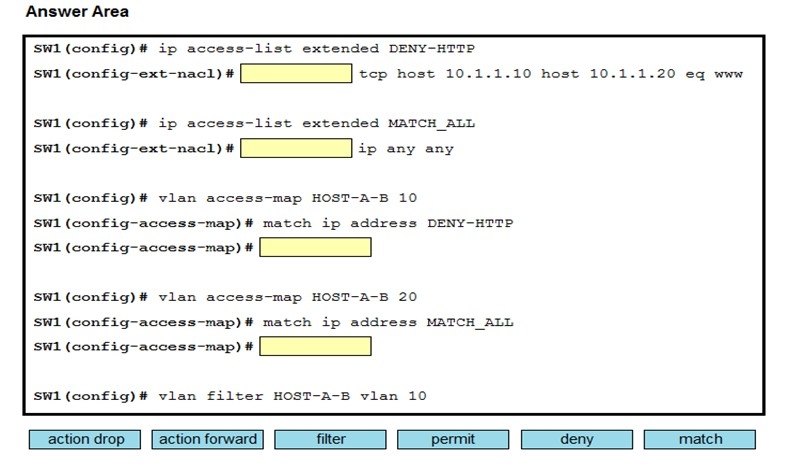
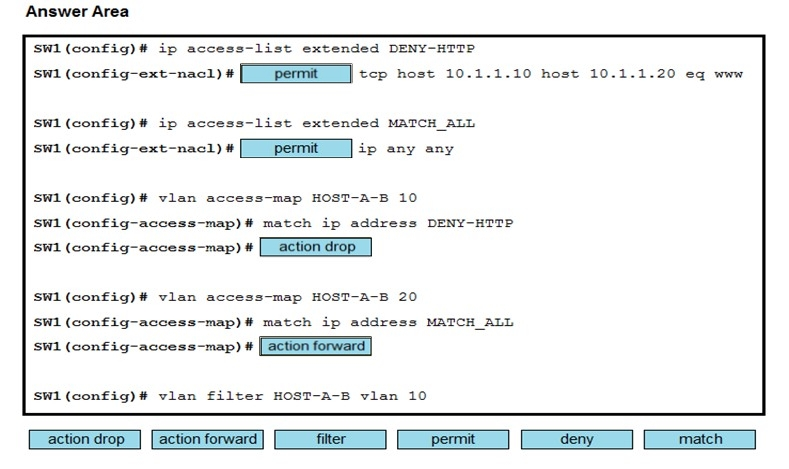
Refer to the exhibit. An engineer must deny HTTP traffic from host A to host B while allowing all other communication between the hosts. Drag and drop the commands into the configuration to achieve these results. Some commands may be used more than once. Not all commands are used. Select and Place:
To increase total throughput and redundancy on the links between the wireless controller and switch, the customer enabled LAG on the wireless controller. Which EtherChannel mode must be configured on the switch to allow the WLC to connect?
A. Active
B. Passive
C. On
D. Auto
Which of the following are the three components of the three-tier hierarchical networking model used in the classical Cisco networks design? (Choose three.)
A. Distribution
B. Core
C. Access
D. Leaf
E. Spine
How does SSO work with HSRP to minimize network disruptions?
A. It enables HSRP to elect another switch in the group as the active HSRP switch.
B. It ensures fast failover in the case of link failure.
C. It enables data forwarding along known routes following a switchover, while the routing protocol reconverges.
D. It enables HSRP to failover to the standby RP on the same device.
Refer to the exhibit.Security policy requires all idle exec sessions to be terminated in 600 seconds. Which configuration achieves this goal?
A. line vty 0 15 absolute-timeout 600
B. line vty 0 15 no exec-timeout
C. line vty 0 15 exec-timeout 10 0
D. line vty 0 4 exec-timeout 600
Refer to the exhibit.What is generated by the script?
A. the router processes
B. the cdp neighbors
C. the routing table
D. the running configuration
Which two conditions occur when the primary route processor fails on a switch that is using dual route processors with stateful switchover? (Choose two.)
A. Data forwarding can continue along known paths until routing protocol information is restored.
B. Data forwarding is stopped until the routing protocols reconverge after the switchover.
C. The standby route processor is fully initialized and state information is maintained.
D. User sessions are immediately recreated on the new active route processor.
E. The standby route processor initialization is started when the primary router processor fails.
An engineer must create a new SSID on a Cisco 9800 wireless LAN controller. The client has asked to use a pre-shared key for authentication. Which profile must the engineer edit to achieve this requirement?
A. Policy
B. RF
C. Flex
D. WLAN
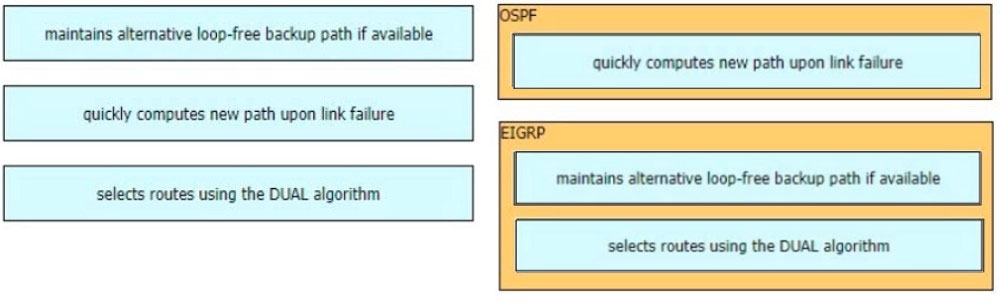
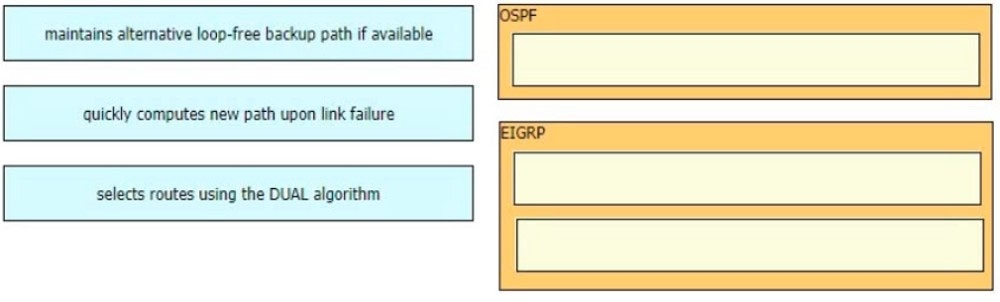
Drag and drop the characteristics from the left onto the routing protocols they describe on the right.
Select and Place:
Which two mechanisms are used with OAuth 2.0 for enhanced validation? (Choose two.)
A. authorization
B. custom headers
C. request management
D. authentication
E. accounting
What is a VPN in a Cisco SD-WAN deployment?
A. common exchange point between two different services
B. attribute to identify a set of services offered in specific places in the SD-WAN fabric
C. virtualized environment that provides traffic isolation and segmentation in the SD-WAN fabric
D. virtual channel used to carry control plane information
Refer to the exhibit.Which GRE tunnel configuration command is missing on R2?
A. tunnel source 172.16.1.0
B. tunnel source 200.1.1.1
C. tunnel destination 200.1.1.1
D. tunnel source 192.168.1.2
Refer to the exhibit. Rapid PVST+ is enabled on all switches. Which command set must be configured on Switch1 to achieve the following results on port fa0/1? When a device is connected, the port transitions immediately to a forwarding state. The interface should not send or receive BPDUs. If a BPDU is received, it continues operating normally.
A. Switch1(config)# spanning-tree portfast bpdu filter default Switch1(config)# interface f0/1 Switch1(config-if)# spanning-tree portfast
B. Switch1(config)# spanning-tree portfast bpduguard default Switch 1 (config)# interface f0/1 Switch1 (config-if)# spanning-tree portfast
C. Switch1(config)# interface f0/1 Switch1(config-if)# spanning-tree portfast
D. Switch1(config)# interface f0/1 Switch1(config-if)# spanning-tree portfast Switch1 (config-if)# spanning-tree bpduguard enable
What is a benefit of data modeling languages like YANG?
A. They create more secure and efficient SNMP OIDs.
B. They provide a standardized data structure, which results in configuration scalability and consistency.
C. They enable programmers to change or write their own applications within the device operating system.
D. They make the CLI simpler and more efficient.
Which devices does Cisco DNA Center configure when deploying an IP-based access control policy?
A. all devices integrating with ISE
B. selected individual devices
C. all devices in selected sites
D. all wired devices
Router R1 must be configured as a UDP responder on port 6336. Which configuration accomplishes this task?
A. (config)#ip sla responder udp-echo ipaddress 10.10.10.1 port 6336
B. (config)#ip sla responder udp-echo ipv4 10.10.10.1 port 6336
C. (config)#ip sla responder ipaddress 10.10.10.1 port 6336
D. (config-if)#ip sla responder udp-port ipaddress 10.10.10.1 port 6336
An engineer is configuring GigabitEthernet1/0/0 for VRRP. When the router has the highest priority in group 5, it must assume the master role. Which command set should the engineer add to the configuration to accomplish this task? interface GigabitEthernet1/0/0 description To IDF A 38- 70-774-10 ip address 172.16.13.2 255.255.255.0
A. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 track 1 decrement 10
B. standby 5 ip 172.16.13.254 standby 5 priority 100 standby 5 preempt
C. vrrp 5 ip 172.16.13.254 vrrp 5 priority 100
D. vrrp 5 ip 172.16.13.254 255.255.255.0 vrrp 5 track 1 decrement 10 vrrp 5 preempt C
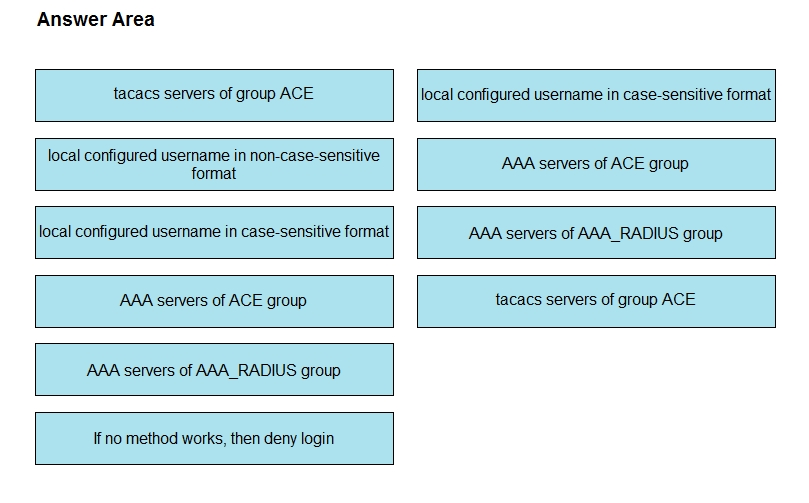
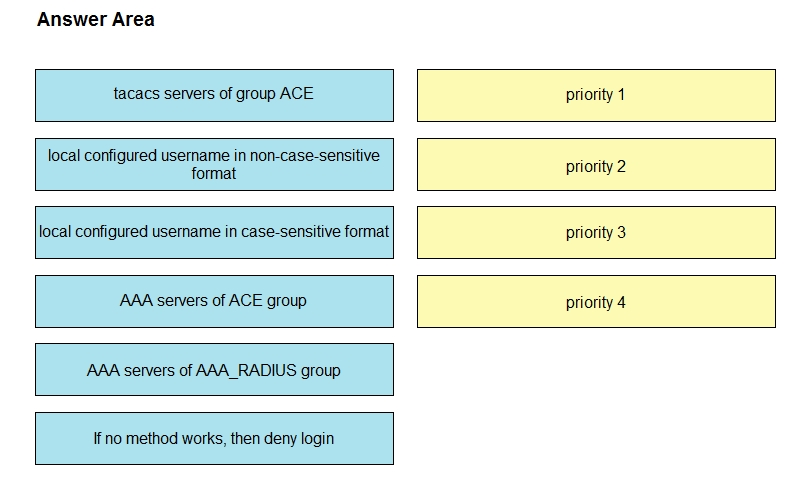
An engineer creates the configuration below. Drag and drop the authentication methods from the left into the order of priority on the right. Not all options are used.
Select and Place:
R1#sh run | i aaa –
aaa new-model
aaa authentication login default group ACE group AAA_RADIUS local-case aaa session-id common R1#
In a Cisco SD-Access solution, which protocol is used by an extended node to connect to a single edge node?
A. VXLAN
B. IS-IS
C. 802.1Q
D. CTS
Refer to the exhibit.A network administrator must configure router B to allow traffic only from network 10.100.2.0 to networks outside of router
A. Which configuration must be applied?
B. RouterB(config)# access-list 101 permit ip 10.100.2.0 0.0.0.255 any
RouterB(config)# access-list 101 deny any
RouterB(config)# int g0/0/0 –
RouterB(config-if)# ip access-group 101 out
C. RouterB(config)# access-list 101 permit ip 10.100.3.0 0.0.0.255 any
RouterB(config)# access-list 101 deny any
RouterB(config)# int g0/0/0 –
RouterB(config-if)# ip access-group 101 out
RouterB(config)# int g0/0/1 –
RouterB(config-if)# ip access-group 101 out
D. RouterB(config)# access-list 101 permit ip 10.100.2.0 0.0.0.255 any
RouterB(config)# access-list 101 deny any
RouterB(config)# int g0/0/2 –
RouterB(config-if)# ip access-group 101 in
E. RouterB(config)# access-list 101 permit ip 10.100.2.0 0.0.0.255 any
RouterB(config)# int g0/0/0 –
RouterB(config-if)# ip access-group 101 out
RouterB(config)# int g0/0/1 –
RouterB(config-if)# ip access-group 101 out
Which algorithms are used to secure REST API from brute attacks and minimize the impact?
A. SHA-512 and SHA-384
B. MD5 algorithm-128 and SHA-384
C. SHA-1, SHA-256, and SHA-512
D. PBKDF2, BCrypt, and SCrypt
What are two best practices when designing a campus Layer 3 infrastructure? (Choose two.)
A. configure passive-interface on nontransit links.
B. Implement security features at the core.
C. Summarize routes from the aggregation layer toward the core layer.
D. Tune Cisco Express Forwarding load balancing hash for ECMP routing.
E. Summarize from the access layer toward the aggregation layer.
Refer to the exhibit. Which type of antenna is shown on the radiation patterns?
A. patch
B. dipole
C. omnidirectional
D. Yagi
What is a command-line tool for consuming REST APIs?
A. Python requests
B. Postman
C. cURL
D. Firefox
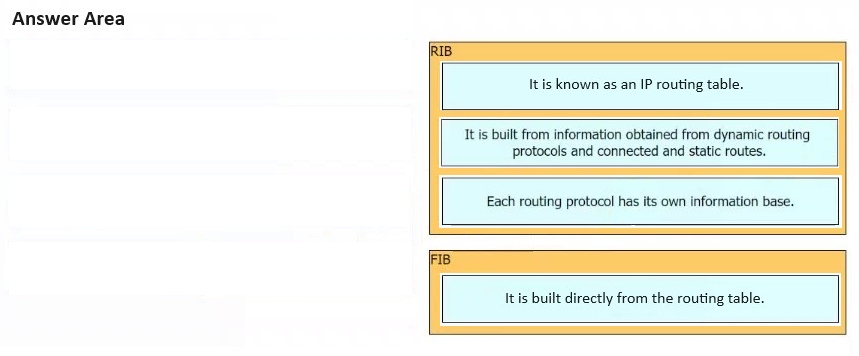
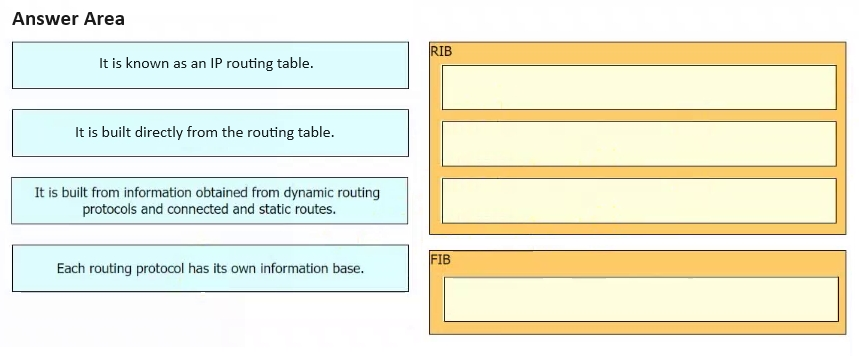
How does the RIB differ from the FIB?
A. The FIB maintains network topologies and routing tables. The RIB is a list of routes to particular network destinations.
B. The FIB includes many routes to a single destination. The RIB is the best route to a single destination.
C. The RIB is used to create network topologies and routing tables. The FIB is a list of routes to particular network destinations.
D. The RIB includes many routes to the same destination prefix. The FIB contains only the best route.
What do Chef and Ansible have in common?
A. They use YAML as their primary configuration syntax.
B. They rely on a procedural approach.
C. They rely on a declarative approach
D. They are clientless architectures.
Which Cisco EIGRP K-values are set to zero by default? (Choose three.)
A. Bandwidth
B. Load
C. Total Delay
D. Reliability
E. MTU
What is a capability of the Cisco DNA Center southbound API?
A. It adds support for managing non-Cisco devices from Cisco DNA Center.
B. It connects to ITSM services such as ServiceNow.
C. It sends webhooks from Cisco DNA Center when alerts are triggered.
D. It allows administrators to make API calls to Cisco DNA Center.
A company has an existing Cisco 5520 HA cluster using SSO. An engineer deploys a new single Cisco Catalyst 9800 WLC to test new features. The engineer successfully configures a mobility tunnel between the 5520 cluster and 9800 WL
A. Clients connected to the corporate WLAN roam seamlessly between access points on the 5520 and 9800 WL
B. After a failure on the primary 5520 WLC, all WLAN services remain functional; however, clients cannot roam between the 5520 and 9800 controllers without dropping their connection. Which feature must be configured to remedy the issue?
C. mobility MAC on the 5520 cluster
D. mobility MAC on the 9800 WLC
E. new mobility on the 5520 cluster
F. new mobility on the 9800 WLC
What is one difference between SaltStack and Ansible?
A. SaltStack uses the Ansible agent on the box, whereas Ansible uses a Telnet server on the box.
B. SaltStack uses an API proxy agent to program Cisco boxes in agent mode, whereas Ansible uses a Telnet connection.
C. SaltStack uses SSH to interact with Cisco devices, whereas Ansible uses an event bus.
D. SaltStack is constructed with minion, whereas Ansible is constructed with YAML.
Refer to the exhibit.Which result does the Python code achieve?
A. The code encrypts a base64 decrypted password.
B. The code converts time to the Epoch LINUX time format.
C. The code converts time to the “year/month/day” time format.
D. The code converts time to the yyyymmdd representation.
Refer to the exhibit. An engineer must configure static NAT on R1 to allow users HTTP access to the web server on TCP port 80. The web server must be reachable through ISP 1 and ISP 2. Which command set should be applied to R1 to fulfill these requirements?
A. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 extendable ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 extendable
B. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80
C. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 no-alias ip nat inside source static tcp 10.1.1.100 80 209.165.201.1 80 no-alias
D. ip nat inside source static tcp 10.1.1.100 80 209.165.200.225 80 ip nat inside source static tcp 10.1.1.100 8080 209.165.201.1 8080 A
If the maximum power level assignment for global TPC 802.11a/n/ac is configured to 10 dBm. which power level effectively doubles the transmit power?
A. 13 dBm
B. 14 dBm
C. 17 dBm
D. 20 dBm
Which protocol is responsible for data plane forwarding in a Cisco SD-Access deployment?
A. IS-IS
B. OSPF
C. VXLAN
D. LISP
A customer wants to connect a device to an autonomous Cisco AP configured as a WG
A. The WGB is configured properly: however, it fails to associate to a
CAPWAP-enabled AP. Which change must be applied in the advanced WLAN settings to resolve this issue?
B. Enable Aironet I
C. Enable passive client.
D. Disable AAA override.
E. Disable FlexConnect local switching.
Which statement about Cisco Express Forwarding is true?
A. The CPU of a router becomes directly involved with packet-switching decisions.
B. It uses a fast cache that is maintained in a router data plane.
C. It maintains two tables in the data plane: the FIB and adjacency table.
D. It makes forwarding decisions by a process that is scheduled through the IOS scheduler.
By default, which virtual MAC address does HSRP group 30 use?
A. 05:0c:5e:ac:07:30
B. 00:00:0c:07:ac:1e
C. 00:43:19:74:89:1e
D. 00:05:0c:07:ac:30
Refer to the exhibit.Users cannot reach the web server at 192.168.100.1. What is the root cause for the failure?
A. The server is attempting to load balance between links 10.100.100.1 and 10.100.200.1.
B. There is a loop in the path to the server.
C. The gateway cannot translate the server domain name.
D. The server is out of service.
Select the devices from the below options that can be fart of Cisco SDWAN Solution. (Choose two.)
A. ISR 2900
B. ASR 1000
C. IR8300
D. FTD 1120
E. ASR 9000
Which JSON script is properly formatted?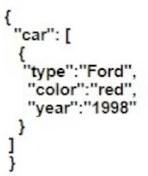


A. C
A customer requests a network design that supports these requirements: FHRP redundancy multivendor router environment IPv4 and IPv6 hosts Which protocol does the design include?
A. VRRP version 2
B. VRRP version 3
C. GLBP
D. HSRP version 2
Which configuration protects the password for the VTY lines against over-the-shoulder attacks?
A. line vty 0 15
password $2$FpM7f82!
B. username admin secret 7 6j809J23kpp438337113N7%e$
C. line vty 0 4
password $2$FpM7f82!
D. service password-encryption
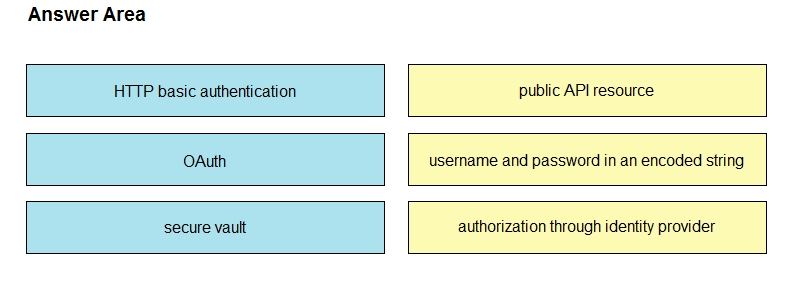
Drag and drop the REST API authentication methods from the left onto their descriptions on the right.
Select and Place:

Access Full 350-401 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 350-401 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 350-401 mock test free today—and take a major step toward exam success!