350-401 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 350-401 certification? Our 350-401 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 350-401 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 350-401 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
By default, which virtual MAC address does HSRP group 12 use?
A. 00:00:0c:07:ac:0c
B. 00:05:5e:00:0c:12
C. 00:5e:0c:07:ac:12
D. 05:43:84:57:29:2c
Refer to the exhibit. What is required to configure a second export destination for IP address 192.168.10.1?
A. Specify a different UDP port.
B. Specify a different TCP port.
C. configure a version 5 flow-export to the same destination.
D. Specify a different flow I
E. Specify a VR
F.
Refer to the exhibit. Which command must be applied to R2 for an OSPF neighborship to form?
A. network 20.1.1.2 255.255.0.0 area 0
B. network 20.1.1.2 0.0.0.0 area 0
C. network 20.1.1.2 255.255.255.255 area 0
D. network 20.1.1.2 0.0.255.255 area 0
How does a Type 2 hypervisor function?
A. It runs on a virtual server and includes its own operating system.
B. It runs directly on a physical server and includes its own operating system.
C. It is installed as an application on an already installed operating system.
D. It enables other operating systems to run on it.
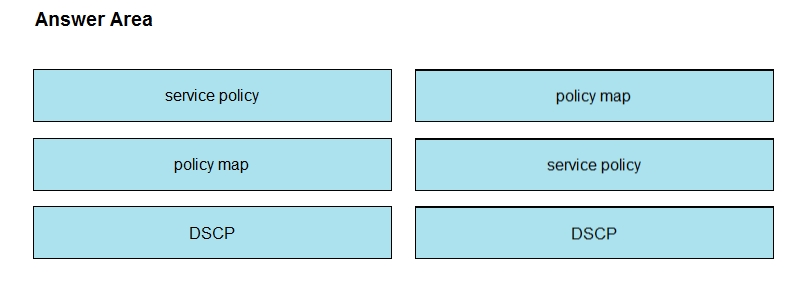
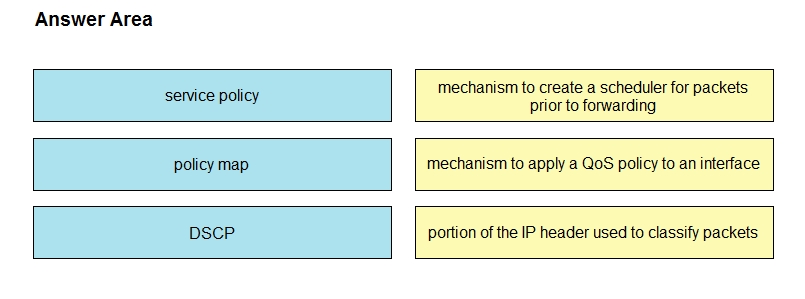
Drag and drop the QoS mechanisms from the left onto their descriptions on the right.
Select and Place:
What is used to validate the authenticity of client and is sent in HTTP requests as a JSON object?
A. SSH
B. HTTPS
C. JWT
D. TLS
How do the MAC address table and TCAM differ?
A. TCAM is populated from the ARP file, and the MAC address table is populated from the switch configuration file
B. TCAM stores Layer 2 forwarding information, and the MAC address table stores QoS information
C. TCAM lookups can match only 1s and 0s, and MAC address lookups can match 1s, 0s and a third “care/don’t care” state
D. TCAM is a type of memory and the MAC address table is a logical structure
By default, which virtual MAC address does HSRP group 14 use?
A. 04:17:01:05:7c:0e
B. 00:05:0c:07:ac:14
C. 00:00:0c:07:ac:0e
D. 00:05:5e:19:0c:14
Which configuration restricts the amount of SSH traffic that a router accepts to 100 kbps?
A. 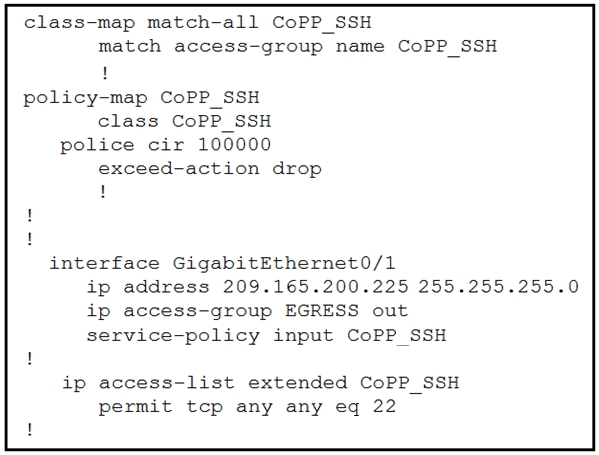
B. 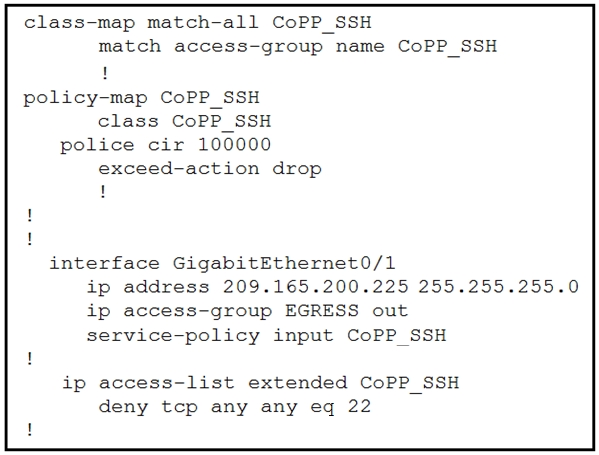
C. 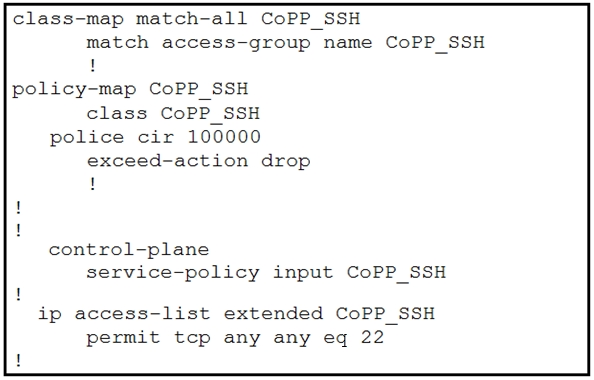
D. 
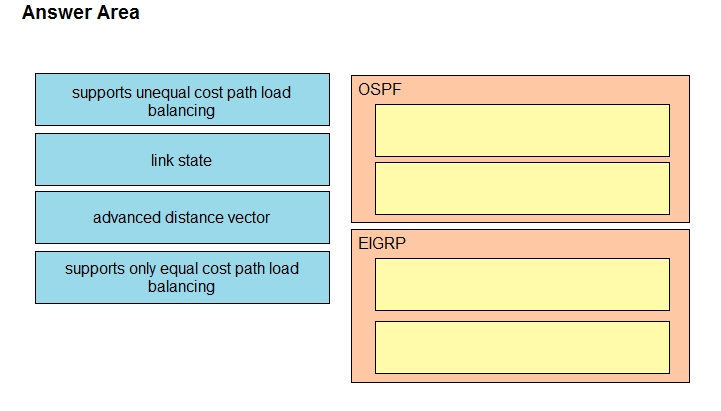
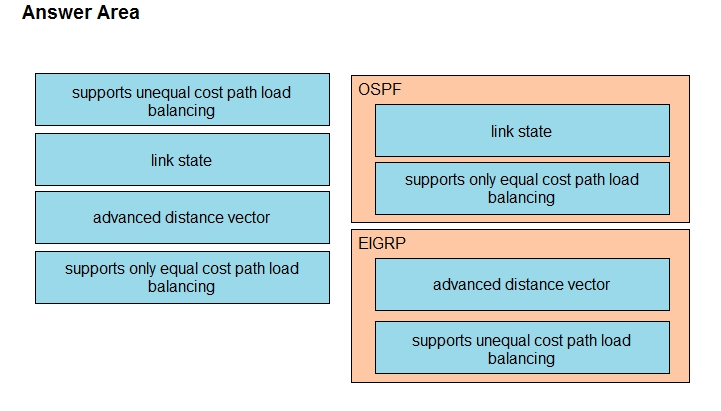
Drag and drop the descriptions from the left onto the routing protocol they describe on the right.
Select and Place:
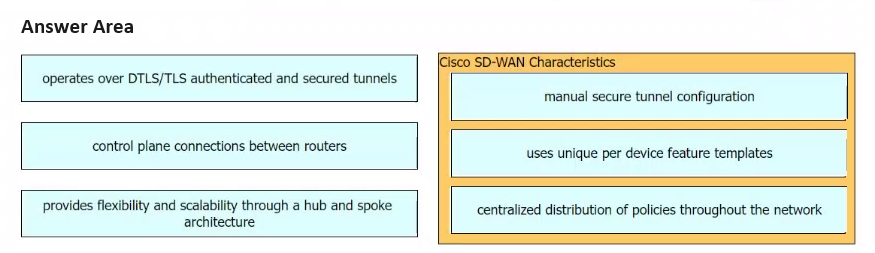
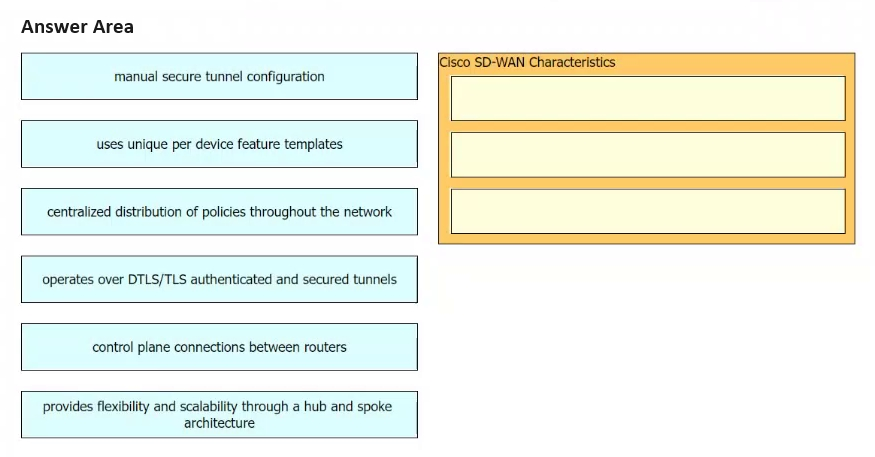
Drag and drop the characteristics of Cisco SD-WAN from the left onto the right. Not all options are used.
Select and Place:
Which A record type should be configured for access points to resolve the IP address of @ wireless LAN controller using ONS?
A. CISCO.CONTROLLER localdomain
B. CISCO.CAPWAP.CONTROLLER localdomain
C. CISCO-CONTROLLER localdomain
D. CISCO-CAPWAP-CONTROLLER.localdomain
Which of the following are examples of Type 2 hypervisors? (Choose three.)
A. VMware ESXi
B. Oracle VirtualBox
C. Oracle Solaris Zones
D. Microsoft Hyper-V
E. Microsoft Virtual PC
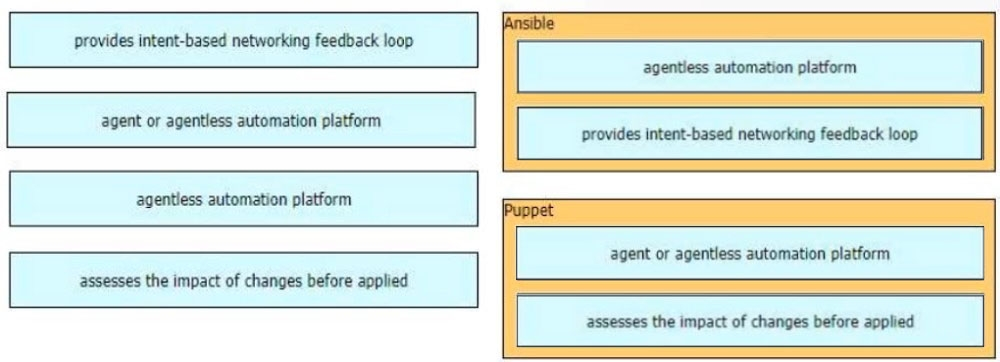
How do agent-based versus agentless configuration management tools compare?
A. Agentless tools use proxy nodes to interface with slave nodes.
B. Agentless tools require no messaging systems between master and slaves.
C. Agent-based tools do not require a high-level language interpreter such as Python or Ruby on slave nodes.
D. Agent-based tools do not require installation of additional software packages on the slave nodes.
Refer to the exhibit. An engineer configures the BGP adjacency between R1 and R2; however, it fails to establish. Which action resolves the issue?
A. Change the network statement on R1 to 172.16.10.0.
B. Change the remote-as number on R1 to 6500.
C. Change the remote-as number for 192.168.100.11.
D. Enable synchronization on R1 and R2.
When a DNS host record is configured for a new Cisco AireOS WLC, which hostname must be added to allow APs to successfully discover the WLC?
A. CONTROLLER-CAPWAP-CISCO
B. CISCO-CONTROLLER-CAPWAP
C. CAPWAP-CISCO-CONTROLLER
D. CISCO-CAPWAP-CONTROLLER
Refer the exhibit. Which configuration elects SW4 as the root bridge for VLAN 1 and puts G0/2 on SW2 into a blocking state?
A. SW4(config)#spanning-tree vlan 1 priority 0 ! SW2(config)#int G0/2 SW2(config-if)#spanning-tree cost 128
B. SW4(config)#spanning-tree vlan 1 priority 0 ! SW2(config)#interface G0/2 SW2(config-if)#spanning-tree vlan 1 port-priority 64
C. SW4(config)#spanning-tree vlan 1 priority 32768 ! SW2(config)#int G0/2 SW2(config-if)#spanning-tree cost 128
D. SW4(config)#spanning-tree vlan 1 priority 32768 ! SW2(config)#interface G0/2 SW2(config-if)#spanning-tree vlan 1 port-priority 0
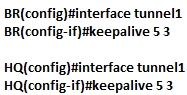
Refer to the exhibit. What is the effect of these commands on the BR and HQ tunnel interfaces?
A. The keepalives are sent every 3 seconds and 5 retries.
B. The tunnel line protocol goes down when the keepalive counter reaches 5.
C. The keepalives are sent every 5 seconds and 3 retries.
D. The tunnel line protocol goes down when the keepalive counter reaches 6.
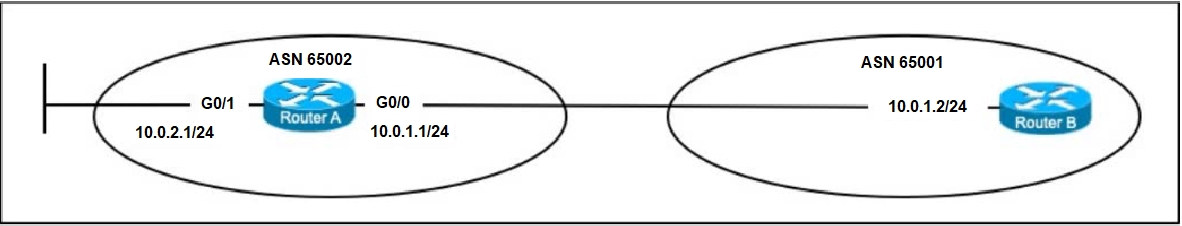
Refer to the exhibit.
A. router bgp 65002
neighbor 10.0.1.2 remote-as 65002
network 10.0.2.0 255.255.255.0
B. router bgp 65001
neighbor 10.0.1.2 remote-as 65002
redistribute static
C. router bgp 65001
neighbor 10.0.1.2 remote-as 65002
network 10.0.1.0 255.255.255.0
D. router bgp 65001
neighbor 10.0.1.2 remote-as 65002
network 10.0.2.0 255.255.255.0
Which function does a fabric wireless LAN controller perform in a Cisco SD-Access deployment?
A. manages fabric-enabled APs and forwards client registration and roaming information to the Control Plane Node
B. coordinates configuration of autonomous nonfabric access points within the fabric
C. performs the assurance engine role for both wired and wireless clients
D. is dedicated to onboard clients in fabric-enabled and nonfabric-enabled APs within the fabric A
A wireless network engineer must configure a WPA2+WPA3 policy with the Personal security type. Which action meets this requirement?
A. Configure the CCMP256 encryption cipher.
B. Configure the CCMP128 encryption cipher.
C. Configure the GCMP256 encryption cipher.
D. Configure the GCMP128 encryption cipher.
Drag and drop the snippets onto the blanks within the code to construct a script that changes the routing from gateway 1 to gateway 2 from 11:00
m. to 12:00 a.m. (2300 to 2400) only, daily. Not all options are used, and some options may be used twice.
Refer to the exhibit. A network engineer troubleshoots an issue with the port channel between SW1 and SW2. Which command resolves the issue?
A. SW2(config-if)#switchport mode trunk
B. SW1(config-if)#channel-group 10 mode active
C. SW1(config-if)#channel-group 10 mode desirable
D. SW2(config-if)#channel-group 10 mode on
What is a characteristic of traffic shaping?
A. drops out-of-profile packets
B. causes TCP retransmits when packets are dropped
C. can be applied in both traffic directions
D. queues out-of-profile packets until the buffer is full
Which statement about multicast RPs is true?
A. RPs are required only when using protocol independent multicast dense mode.
B. RPs are required for protocol independent multicast sparse mode and dense mode.
C. By default, the RP is needed periodically to maintain sessions with sources and receivers.
D. By default, the RP is needed only to start new sessions with sources and receivers.
An engineer must configure an ACL that permits packets which include an ACK in the TCP header. Which entry must be included in the ACL?
A. access-list 110 permit tcp any any eq 21 tcp-ack
B. access-list 10 permit tcp any any eq 21 established
C. access-list 110 permit tcp any any eq 21 established
D. access-list 10 permit ip any any eq 21 tcp-ack
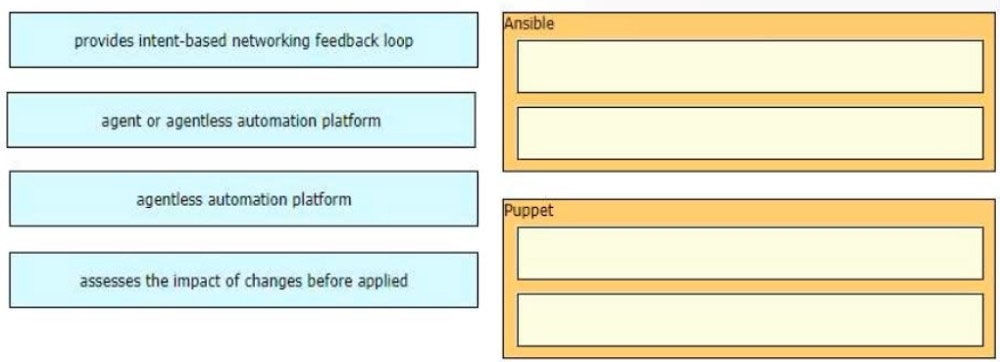
Drag and drop the automation characteristics from the left onto the appropriate tools on the right.
Select and Place:
Which two actions are recommended as security best practices to protect REST API? (Choose two.)
A. Enable dual authentication of the session
B. Use a password hash
C. Use SSL for encryption
D. Use TACACS+ authentication
E. Enable out-of-band authentication
Refer to the exhibit. A network engineer must permit administrators to automatically authenticate if there is no response from either of the AAA servers. Which configuration achieves these results?
A. aaa authentication enable default group radius local
B. aaa authentication login default group radius
C. aaa authentication login default group tacacs+ line
D. aaa authentication login default group radius none
Refer to the exhibit. The administrator troubleshoots an EtherChannel that keeps moving to err-disabled. Which two actions must be taken to resolve the issue? (Choose two.)
A. Ensure that the corresponding port channel interface on the neighbor switch is named Port-channel1.
B. Ensure that the switchport parameters of Port-channel1 match the parameters of the port channel on the neighbor switch.
C. Ensure that interfaces Gi1/0/2 and Gi1/0/3 connect to the same neighboring switch.
D. Reload the switch to force EtherChannel renegotiation.
E. Ensure that the neighbor interfaces of Gi1/0/2 and Gi1/0/3 are configured as members of the same EtherChannel.
Which function is performed by vSmart in the Cisco SD-WAN architecture?
A. aggregation and distribution of VPN routing information
B. execution of localized policies
C. facilitation of NAT detection and traversal
D. redistribution between OMP and other routing protocols
Refer to the exhibit.Which result does the Python code achieve?
A. The code encrypts a base64 decrypted password.
B. The code converts time to the Epoch LINUX time format.
C. The code converts time to the “year/month/day” time format.
D. The code converts time to the yyyymmdd representation.
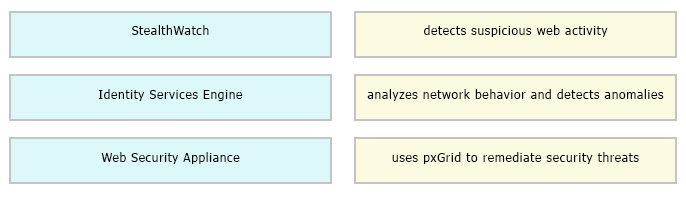
Drag and drop the solutions that comprise Cisco Cyber Threat Defense from the left onto the objectives they accomplish on the right.
Select and Place:
Which technology provides a secure communication channel for all traffic at Layer 2 of the OSI model?
A. SSL
B. Cisco TrustSec
C. MACsec
D. IPsec
Refer to the exhibit.An engineer is troubleshooting a connectivity issue and executes a traceroute. What does the result confirm?
A. The destination port is unreachable.
B. The probe timed out.
C. The destination server reported it is too busy.
D. The protocol is unreachable.
In Cisco routers, the codes for a traceroute command reply are:
! ” success
* ” time out
N ” network unreachable –
H ” host unreachable –
P ” protocol unreachable –
A ” admin denied –
Q ” source quench received (congestion)
? ” unknown (any other ICMP message). In Cisco routers, the codes for a traceroute command reply are:
! ” success
* ” time out
N ” network unreachable –
H ” host unreachable –
P ” protocol unreachable –
A ” admin denied –
Q ” source quench received (congestion)
? ” unknown (any other ICMP message)
What is the recommended minimum SNR for data applications on wireless networks?
A. 20
B. 25
C. 15
D. 10
A local router shows an EBGP neighbor in the Active state. Which statement is true about the local router?
A. The local router is attempting to open a TCP session with the neighboring router.
B. The local router is receiving prefixes from the neighboring router and adding them in RIB-IN.
C. The local router has active prefixes in the forwarding table from the neighboring router.
D. The local router has BGP passive mode configured for the neighboring router.
An engineer must protect their company against ransomware attacks. Which solution allows the engineer to block the execution stage and prevent file encryption?
A. Use Cisco Firepower and block traffic to TOR networks.
B. Use Cisco AMP deployment with the Malicious Activity Protection engine enabled.
C. Use Cisco Firepower with Intrusion Policy and snort rules blocking SMB exploitation.
D. Use Cisco AMP deployment with the Exploit Prevention engine enabled.
Refer to the exhibit. Which configuration is required to summarize the Area 2 networks that are advertised to Area 0?
A. RouterB(config)# router ospf 1 RouterB(config-router)# area 2 range 192.168.36.0 255.255.252.0
B. RouterB(config)# router ospf 1 RouterB(config-router)# network 192.168.38.0 255.255.255.0
C. RouterB(config)# router ospf 1 RouterB(config-router)# network 192.168.38.0 255.255.252.0
D. RouterB(config)# router ospf 1 RouterB(config-router)# area 2 range 192.168.36.0 255.255.255.0 A
Which antenna type should be used for a site-to-site wireless connection?
A. patch
B. dipole
C. omnidirectional
D. Yagi
What is one characteristic of the Cisco SD-Access control plane?
A. It allows host mobility only in the wireless network.
B. It is based on VXLAN technology.
C. Each router processes every possible destination and route.
D. It stores remote routes in a centralized database server.
Which LISP infrastructure device provides connectivity between non-LISP sites and LISP sites by receiving non-LISP traffic with a LISP site destination?
A. PITR
B. map resolver
C. map server
D. PETR
A customer has several small branches and wants to deploy a Wi-Fi solution with local management using CAPWAP. Which deployment model meets this requirement?
A. local mode
B. autonomous
C. SD-Access wireless
D. Mobility Express
Refer to the exhibit. An administrator troubleshoots intermittent connectivity from internal hosts to an external public server. Some internal hosts can connect to the server while others receive an ICMP Host Unreachable message, and these hosts change over time. What is the cause of this issue?
A. The NAT ACL and NAT pool share the same name.
B. The translation does not use address overloading.
C. The NAT ACL does not match all internal hosts.
D. The NAT pool netmask is excessively wide.
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two.)
A. advertisement of network prefixes and their attributes
B. configuration of control and data policies
C. gathering of underlay infrastructure data
D. delivery of crypto keys
E. segmentation and differentiation of traffic
Refer to the exhibit.How should the programmer access the list of VLANs that were received via the API call?
A. VlanNames[`response’]
B. VlanNames[0]
C. VlanNames[`Vlan1′]
D. list(VlanNames)
Which mechanism does OAuth use to strengthen REST API security when compared to BasicAuth?
A. Token
B. SSL
C. Authentication
D. TLS
Refer to the exhibit. R1 is able to ping the R3 fa0/1 interface. Why do the extended pings fail?
A. The maximum packet size accepted by the command is 1476 bytes.
B. The DF bit has been set.
C. R3 is missing a return route to 10.99.69.0/30.
D. R2 and R3 do not have an OSPF adjacency.
In a Cisco SD-Access wireless architecture, which device manages endpoint ID to edge node bindings?
A. fabric control plane node
B. fabric wireless controller
C. fabric border node
D. fabric edge node
Refer to the exhibit.A network engineer is configuring OSPF between router R1 and router R2. The engineer must ensure that a DR/BDR election does not occur on the Gigabit Ethernet interfaces in area 0. Which configuration set accomplishes this goal?
A. R1(config-if)interface Gi0/0 R1(config-if)ip ospf network point-to-point R2(config-if)interface Gi0/0 R2(config-if)ip ospf network point-to- point
B. R1(config-if)interface Gi0/0 R1(config-if)ip ospf network broadcast R2(config-if)interface Gi0/0 R2(config-if)ip ospf network broadcast
C. R1(config-if)interface Gi0/0 R1(config-if)ip ospf database- filter all out R2(config-if)interface Gi0/0 R2(config-if)ip ospf database- filter all out
D. R1(config-if)interface Gi0/0 R1(config-if)ip ospf priority 1 R2(config-if)interface Gi0/0 R2(config-if)ip ospf priority 1
Access Full 350-401 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 350-401 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 350-401 certification journey!