312-50V9 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 312-50V9 certification exam? Start your preparation the smart way with our 312-50V9 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 312-50V9 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 312-50V9 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which of the following conditions must be given to allow a tester to exploit a Cross-Site Request Forgery (CSRF) vulnerable web application?
A. The victim user must open the malicious link with an Internet Explorer prior to version 8.
B. The session cookies generated by the application do not have the HttpOnly flag set.
C. The victim user must open the malicious link with a Firefox prior to version 3.
D. The web application should not use random tokens.
Diffie-Hellman (DH) groups determine the strength of the key used in the key exchange process. Which of the following is the correct bit size of the Diffie-Hellman (DH) group 5?
A. 768 bit key
B. 1025 bit key
C. 1536 bit key
D. 2048 bit key
The security concept of "separation of duties" is most similar to the operation of which type of security device?
A. Firewall
B. Bastion host
C. Intrusion Detection System
D. Honeypot
Which of the following is the primary objective of a rootkit?
A. It opens a port to provide an unauthorized service
B. It creates a buffer overflow
C. It replaces legitimate programs
D. It provides an undocumented opening in a program
Which command lets a tester enumerate alive systems in a class C network via ICMP using native Windows tools?
A. ping 192.168.2.
B. ping 192.168.2.255
C. for %V in (1 1 255) do PING 192.168.2.%V
D. for /L %V in (1 1 254) do PING -n 1 192.168.2.%V | FIND /I “Reply”
While performing online banking using a Web browser, Kyle receives an email that contains an image of a well-crafted art. Upon clicking the image, a new tab on the web browser opens and shows an animated GIF of bills and coins being swallowed by a crocodile. After several days, Kyle noticed that all his funds on the bank was gone. What Web browser-based security vulnerability got exploited by the hacker?
A. Clickjacking
B. Web Form Input Validation
C. Cross-Site Request Forgery
D. Cross-Site Scripting
When comparing the testing methodologies of Open Web Application Security Project (OWASP) and Open Source Security Testing Methodology Manual (OSSTMM) the main difference is
A. OWASP is for web applications and OSSTMM does not include web applications.
B. OSSTMM is gray box testing and OWASP is black box testing.
C. OWASP addresses controls and OSSTMM does not.
D. OSSTMM addresses controls and OWASP does not.
An engineer is learning to write exploits in C++ and is using the exploit tool Backtrack. The engineer wants to compile the newest C++ exploit and name it calc.exe. Which command would the engineer use to accomplish this?
A. g++ hackersExploit.cpp -o calc.exe
B. g++ hackersExploit.py -o calc.exe
C. g++ -i hackersExploit.pl -o calc.exe
D. g++ –compile –i hackersExploit.cpp -o calc.exe
One way to defeat a multi-level security solution is to leak data via
A. a bypass regulator.
B. steganography.
C. a covert channel.
D. asymmetric routing.
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
A. Cavity virus
B. Polymorphic virus
C. Tunneling virus
D. Stealth virus
While conducting a penetration test, the tester determines that there is a firewall between the tester's machine and the target machine. The firewall is only monitoring TCP handshaking of packets at the session layer of the OSI model. Which type of firewall is the tester trying to traverse?
A. Packet filtering firewall
B. Application-level firewall
C. Circuit-level gateway firewall
D. Stateful multilayer inspection firewall
How does an operating system protect the passwords used for account logins?
A. The operating system performs a one-way hash of the passwords.
B. The operating system stores the passwords in a secret file that users cannot find.
C. The operating system encrypts the passwords, and decrypts them when needed.
D. The operating system stores all passwords in a protected segment of non-volatile memory.
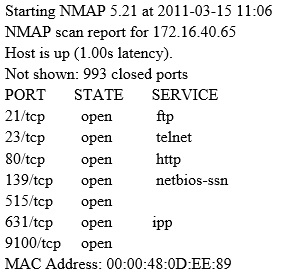
A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
A. The host is likely a Windows machine.
B. The host is likely a Linux machine.
C. The host is likely a router.
D. The host is likely a printer.
An attacker tries to do banner grabbing on a remote web server and executes the following command.Service detection performed. Please report any incorrect results at http://nmap.org/submit/. Nmap done: 1 IP address (1 host up) scanned in 6.42 seconds What did the hacker accomplish?
A. nmap can’t retrieve the version number of any running remote service.
B. The hacker successfully completed the banner grabbing.
C. The hacker should’ve used nmap -O host.domain.com.
D. The hacker failed to do banner grabbing as he didn’t get the version of the Apache web server.
When utilizing technical assessment methods to assess the security posture of a network, which of the following techniques would be most effective in determining whether end-user security training would be beneficial?
A. Vulnerability scanning
B. Social engineering
C. Application security testing
D. Network sniffing
Which of the following resources does NMAP need to be used as a basic vulnerability scanner covering several vectors like SMB, HTTP and FTP?
A. Metasploit scripting engine
B. Nessus scripting engine
C. NMAP scripting engine
D. SAINT scripting engine
Which of the following is a common Service Oriented Architecture (SOA) vulnerability?
A. Cross-site scripting
B. SQL injection
C. VPath injection
D. XML denial of service issues D
Peter extracts the SIDs list from Windows 2000 Server machine using the hacking tool "SIDExtractor". Here is the output of the SIDs:From the above list identify the user account with System Administrator privileges.
A. John
B. Rebecca
C. Sheela
D. Shawn
E. Somia
F. Chang
G. Micah F
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:What is most likely taking place?
A. Ping sweep of the 192.168.1.106 network
B. Remote service brute force attempt
C. Port scan of 192.168.1.106
D. Denial of service attack on 192.168.1.106
An NMAP scan of a server shows port 25 is open. What risk could this pose?
A. Open printer sharing
B. Web portal data leak
C. Clear text authentication
D. Active mail relay
Windows LAN Manager (LM) hashes are known to be weak. Which of the following are known weaknesses of LM? (Choose three.)
A. Converts passwords to uppercase.
B. Hashes are sent in clear text over the network.
C. Makes use of only 32-bit encryption.
D. Effective length is 7 characters.
What is the correct PCAP filter to capture all TCP traffic going to or from host 192.168.0.125 on port 25?
A. tcp.src == 25 and ip.host == 192.168.0.125
B. host 192.168.0.125:25
C. port 25 and host 192.168.0.125
D. tcp.port == 25 and ip.host == 192.168.0.125
A computer science student needs to fill some information into a secured Adobe PDF job application that was received from a prospective employer. Instead of requesting a new document that allowed the forms to be completed, the student decides to write a script that pulls passwords from a list of commonly used passwords to try against the secured PDF until the correct password is found or the list is exhausted. Which cryptography attack is the student attempting?
A. Man-in-the-middle attack
B. Brute-force attack
C. Dictionary attack
D. Session hijacking
Which of the following is an application that requires a host application for replication?
A. Micro
B. Worm
C. Trojan
D. Virus
Pentest results indicate that voice over IP traffic is traversing a network. Which of the following tools will decode a packet capture and extract the voice conversations?
A. Cain
B. John the Ripper
C. Nikto
D. Hping
What is the name of the international standard that establishes a baseline level of confidence in the security functionality of IT products by providing a set of requirements for evaluation?
A. Blue Book
B. ISO 26029
C. Common Criteria
D. The Wassenaar Agreement
How can a rootkit bypass Windows 7 operating system’s kernel mode, code signing policy?
A. Defeating the scanner from detecting any code change at the kernel
B. Replacing patch system calls with its own version that hides the rootkit (attacker’s) actions
C. Performing common services for the application process and replacing real applications with fake ones
D. Attaching itself to the master boot record in a hard drive and changing the machine’s boot sequence/options
Which of the following parameters describe LM Hash (see exhibit): Exhibit:
A. I, II, and III
B. I
C. II
D. I and II
Passive reconnaissance involves collecting information through which of the following?
A. Social engineering
B. Network traffic sniffing
C. Man in the middle attacks
D. Publicly accessible sources
Which of the following is the successor of SSL?
A. TLS
B. RSA
C. GRE
D. IPSec
Which of the following techniques will identify if computer files have been changed?
A. Network sniffing
B. Permission sets
C. Integrity checking hashes
D. Firewall alerts
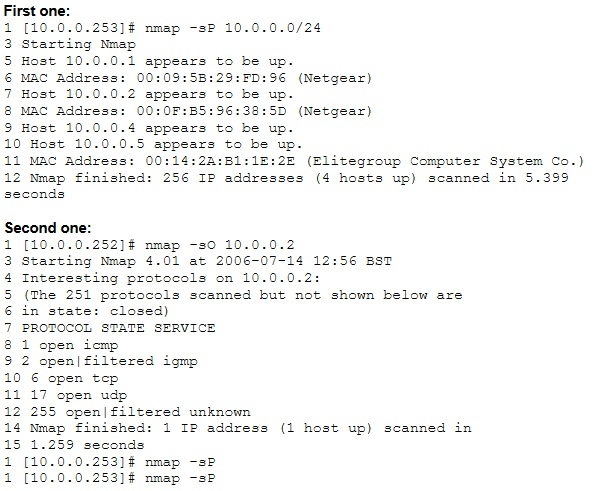
From the two screenshots below, which of the following is occurring?
A. 10.0.0.253 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
B. 10.0.0.253 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
C. 10.0.0.2 is performing an IP scan against 10.0.0.0/24, 10.0.0.252 is performing a port scan against 10.0.0.2.
D. 10.0.0.252 is performing an IP scan against 10.0.0.2, 10.0.0.252 is performing a port scan against 10.0.0.2.
An NMAP scan of a server shows port 69 is open. What risk could this pose?
A. Unauthenticated access
B. Weak SSL version
C. Cleartext login
D. Web portal data leak
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
A. Ignore the problem completely and let someone else deal with it.
B. Create a document that will crash the computer when opened and send it to friends.
C. Find an underground bulletin board and attempt to sell the bug to the highest bidder.
D. Notify the vendor of the bug and do not disclose it until the vendor gets a chance to issue a fix.
Which of the following is a characteristic of Public Key Infrastructure (PKI)?
A. Public-key cryptosystems are faster than symmetric-key cryptosystems.
B. Public-key cryptosystems distribute public-keys within digital signatures.
C. Public-key cryptosystems do not require a secure key distribution channel.
D. Public-key cryptosystems do not provide technical non-repudiation via digital signatures.
An incident investigator asks to receive a copy of the event logs from all firewalls, proxy servers, and Intrusion Detection Systems (IDS) on the network of an organization that has experienced a possible breach of security. When the investigator attempts to correlate the information in all of the logs, the sequence of many of the logged events do not match up. What is the most likely cause?
A. The network devices are not all synchronized.
B. Proper chain of custody was not observed while collecting the logs.
C. The attacker altered or erased events from the logs.
D. The security breach was a false positive.
You have successfully gained access to your client's internal network and successfully comprised a Linux server which is part of the internal IP network. You want to know which Microsoft Windows workstations have file sharing enabled. Which port would you see listening on these Windows machines in the network?
A. 445
B. 3389
C. 161
D. 1433
What are the three types of compliance that the Open Source Security Testing Methodology Manual (OSSTMM) recognizes?
A. Legal, performance, audit
B. Audit, standards based, regulatory
C. Contractual, regulatory, industry
D. Legislative, contractual, standards based
Sid is a judge for a programming contest. Before the code reaches him it goes through a restricted OS and is tested there. If it passes, then it moves onto Sid. What is this middle step called?
A. Fuzzy-testing the code
B. Third party running the code
C. Sandboxing the code
D. String validating the code
Which of the following types of firewalls ensures that the packets are part of the established session?
A. Stateful inspection firewall
B. Circuit-level firewall
C. Application-level firewall
D. Switch-level firewall
Jack was attempting to fingerprint all machines in the network using the following Nmap syntax: invictus@victim_server:~$ nmap -T4 -0 10.10.0.0/24 TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING! Obviously, it is not going through. What is the issue here?
A. OS Scan requires root privileges
B. The nmap syntax is wrong.
C. The outgoing TCP/IP fingerprinting is blocked by the host firewall
D. This is a common behavior for a corrupted nmap application
Smart cards use which protocol to transfer the certificate in a secure manner?
A. Extensible Authentication Protocol (EAP)
B. Point to Point Protocol (PPP)
C. Point to Point Tunneling Protocol (PPTP)
D. Layer 2 Tunneling Protocol (L2TP)
A bank stores and processes sensitive privacy information related to home loans. However, auditing has never been enabled on the system. What is the first step that the bank should take before enabling the audit feature?
A. Perform a vulnerability scan of the system.
B. Determine the impact of enabling the audit feature.
C. Perform a cost/benefit analysis of the audit feature.
D. Allocate funds for staffing of audit log review.
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries.) More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentiality, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Basic example to understand how cryptography works is given below:Which of the following choices is true about cryptography?
A. Algorithm is not the secret, key is the secret.
B. Symmetric-key algorithms are a class of algorithms for cryptography that use the different cryptographic keys for both encryption of plaintext and decryption of ciphertext.
C. Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way.
D. Public-key cryptography, also known as asymmetric cryptography, public key is for decrypt, private key is for encrypt.
Which of the following algorithms provides better protection against brute force attacks by using a 160-bit message digest?
A. MD5
B. SHA-1
C. RC4
D. MD4
Advanced encryption standard is an algorithm used for which of the following?
A. Data integrity
B. Key discovery
C. Bulk data encryption
D. Key recovery C
After trying multiple exploits, you've gained root access to a Centos 6 server. To ensure you maintain access, what would you do first?
A. Create User Account
B. Disable Key Services
C. Disable IPTables
D. Download and Install Netcat
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A. WHOIS
B. IANA
C. CAPTCHA
D. IETF
What technique is used to perform a Connection Stream Parameter Pollution (CSPP) attack?
A. Injecting parameters into a connection string using semicolons as a separator
B. Inserting malicious Javascript code into input parameters
C. Setting a user’s session identifier (SID) to an explicit known value
D. Adding multiple parameters with the same name in HTTP requests
A penetration tester is attempting to scan an internal corporate network from the internet without alerting the border sensor. Which is the most efficient technique should the tester consider using?
A. Spoofing an IP address
B. Tunneling scan over SSH
C. Tunneling over high port numbers
D. Scanning using fragmented IP packets
Access Full 312-50V9 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 312-50V9 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 312-50V9 mock test free today—and take a major step toward exam success!