312-50V10 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 312-50V10 exam? Start with our 312-50V10 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 312-50V10 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 312-50V10 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Which results will be returned with the following Google search query? site:target.com site:Marketing.target.com accounting
A. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting.
B. Results matching all words in the query.
C. Results for matches on target.com and Marketing.target.com that include the word “accounting”
D. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
This tool is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools. Which of the following tools is being described?
A. wificracker
B. Airguard
C. WLAN-crack
D. Aircrack-ng
It has been reported to you that someone has caused an information spillage on their computer. You go to the computer, disconnect it from the network, remove the keyboard and mouse, and power it down. What step in incident handling did you just complete?
A. Discovery
B. Recovery
C. Containment
D. Eradication
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
A. -T0
B. -T5
C. -O
D. -A
Which of the following viruses tries to hide from anti-virus programs by actively altering and corrupting the chosen service call interruptions when they are being run?
A. Stealth/ Tunneling virus
B. Macro virus
C. Cavity virus
D. Polymorphic virus
Which of the following Linux commands will resolve a domain name into IP address?
A. >host-t a hackeddomain.com
B. >host-t ns hackeddomain.com
C. >host -t soa hackeddomain.com
D. >host -t AXFR hackeddomain.com
Which method of password cracking takes the most time and effort?
A. Shoulder surfing
B. Brute force
C. Dictionary attack
D. Rainbow tables
Which protocol is used for setting up secure channels between two devices, typically in VPNs?
A. PPP
B. IPSEC
C. PEM
D. SET
An Internet Service Provider (ISP) has a need to authenticate users connecting via analog modems, Digital Subscriber Lines (DSL), wireless data services, and Virtual Private Networks (VPN) over a Frame Relay network. Which AAA protocol is the most likely able to handle this requirement?
A. DIAMETER
B. RADIUS
C. TACACS+
D. Kerberos
Which of the following options represents a conceptual characteristic of an anomaly-based IDS over a signature-based IDS?
A. Produces less false positives
B. Can identify unknown attacks
C. Requires vendor updates for a new threat
D. Cannot deal with encrypted network traffic
Which of the following tools is used to detect wireless LANs using the 802.11 a/b/g/n WLAN standards on a linux platform?
A. Kismet
B. Netstumbler
C. Nessus
D. Abel
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a ____ database structure instead of SQL's ______ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
A. Strict, Abstract
B. Simple, Complex
C. Relational, Hierarchical
D. Hierarchical, Relational
An attacker, using a rogue wireless AP, performed an MITM attack and injected an HTML code to embed a malicious applet in all HTTP connections. When users accessed any page, the applet ran and exploited many machines. Which one of the following tools the hacker probably used to inject HTML code?
A. Wireshark
B. Ettercap
C. Aircrack-ng
D. Tcpdump
What is the purpose of DNS AAAA record?
A. Address prefix record
B. Address database record
C. Authorization, Authentication and Auditing record
D. IPv6 address resolution record
You are a security officer of a company. You had an alert from IDS that indicates that one PC on your Intranet is connected to a blacklisted IP address (C2 Server) on the Internet. The IP address was blacklisted just before the alert. You are staring an investigation to roughly analyze the severity of the situation. Which of the following is appropriate to analyze?
A. Event logs on the PC
B. Internet Firewall/Proxy log
C. IDS log
D. Event logs on domain controller
Some clients of TPNQM SA were redirected to a malicious site when they tried to access the TPNQM main site. Bob, a system administrator at TPNQM SA, found that they were victims of DNS Cache Poisoning. What should Bob recommend to deal with such a threat?
A. The use of security agents in clients’ computers
B. The use of DNSSEC
C. The use of double-factor authentication
D. Client awareness
You have successfully comprised a server having an IP address of 10.10.0.5. You would like to enumerate all machines in the same network quickly. What is the best Nmap command you will use?
A. nmap -T4 -q 10.10.0.0/24
B. nmap -T4 -F 10.10.0.0/24
C. nmap -T4 -r 10.10.1.0/24
D. nmap -T4 -O 10.10.0.0/24
You have successfully gained access to your client's internal network and successfully comprised a Linux server which is part of the internal IP network. You want to know which Microsoft Windows workstations have file sharing enabled. Which port would you see listening on these Windows machines in the network?
A. 161
B. 3389
C. 445
D. 1433
Which utility will tell you in real time which ports are listening or in another state?
A. Netsat
B. Loki
C. Nmap
D. TCPView
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator's bank account password and login information for the administrator's bitcoin account. What should you do?
A. Do not report it and continue the penetration test.
B. Transfer money from the administrator’s account to another account.
C. Do not transfer the money but steal the bitcoins.
D. Report immediately to the administrator.
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
A. hping2 -1 host.domain.com
B. hping2-i host.domain.com
C. hping2 “”set-ICMP host.domain.com
D. hping2 host.domain.com
The tools which receive event logs from servers, network equipment, and applications, and perform analysis and correlation on those logs, and can generate alarms for security relevant issues, are known as what?
A. Network Sniffer
B. Vulnerability Scanner
C. Intrusion Prevention Server
D. Security Incident and Event Monitoring
Which of the following describes the characteristics of a Boot Sector Virus?
A. Modifies directory table entries so that directory entries point to the virus code instead of the actual program.
B. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR.
C. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR.
D. Overwrites the original MBR and only executes the new virus code.
Scenario: 1. Victim opens the attacker's web site. 2. Attacker sets up a web site which contains interesting and attractive content like 'Do you want to make $1000 in a day?'. 3. Victim clicks to the interesting and attractive content URL. 4. Attacker creates a transparent 'iframe' in front of the URL which victim attempts to click, so victim thinks that he/she clicks to the 'Do you want to make $1000 in a day?' url but actually he/she clicks to the content or UPL that exists in the transparent 'iframe' which is setup by the attacker. What is the name of the attack which is mentioned in the scenario?
A. Session Fixation
B. HTML Injection
C. HTTP Parameter Pollution
D. Clickjacking Attack
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing. What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
A. Service Level Agreement
B. Project Scope
C. Rules of Engagement
D. Non-Disclosure Agreement
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A. IANA
B. CAPTCHA
C. IETF
D. WHOIS
Which of the following act requires employer's standard national numbers to identify them on standard transactions?
A. SOX
B. HIPAA
C. DMCA
D. PCI-DSS
A company's Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application. What kind of Web application vulnerability likely exists in their software?
A. Cross-site scripting vulnerability
B. Session management vulnerability
C. SQL injection vulnerability
D. Cross-site Request Forgery vulnerability
What is the least important information when you analyze a public IP address in a security alert?
A. ARP
B. Whois
C. DNS
D. Geolocation
Session splicing is an IDS evasion technique in which an attacker delivers data in multiple, smallsized packets to the target computer, making it very difficult for an IDS to detect the attack signatures. Which tool can be used to perform session splicing attacks?
A. tcpsplice
B. Burp
C. Hydra
D. Whisker
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity. What tool would you most likely select?
A. Snort
B. Nmap
C. Cain & Abel
D. Nessus
DNS cache snooping is a process of determining if the specified resource address is present in the DNS cache records. It may be useful during the examination of the network to determine what software update resources are used, thus discovering what software is installed. What command is used to determine if the entry is present in DNS cache?
A. nslookup -fullrecursive update.antivirus.com
B. dnsnooping “”rt update.antivirus.com
C. nslookup -norecursive update.antivirus.com
D. dns –snoop update.antivirus.com
Which of the following programming languages is most susceptible to buffer overflow attacks, due to its lack of a built-in bounds checking mechanism?
Code:
#include
int main(){
char buffer[8];
strcpy(buffer, ""11111111111111111111111111111"");
}
Output:
Segmentation fault -
A. C#
B. Python
C. Java
D. C++
The change of a hard drive failure is once every three years. The cost to buy a new hard drive is $300. It will require 10 hours to restore the OS and software to the new hard disk. It will require a further 4 hours to restore the database from the last backup to the new hard disk. The recovery person earns $10/hour. Calculate the SLE, ARO, and ALE. Assume the EF = 1(100%). What is the closest approximate cost of this replacement and recovery operation per year?
A. $1320
B. $440
C. $100
D. $146
Which of the following areas is considered a strength of symmetric key cryptography when compared with asymmetric algorithms?
A. Scalability
B. Speed
C. Key distribution
D. Security
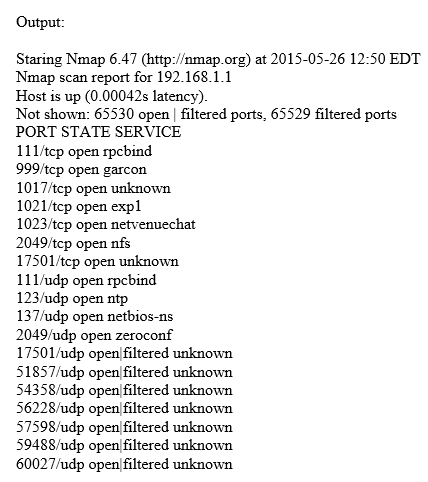
Which of the following Nmap commands will produce the following output?
A. nmap “”sT “”sX “”Pn “”p 1-65535 192.168.1.1
B. nmap “”sN “”Ps “”T4 192.168.1.1
C. nmap “”sS “”sU “”Pn “”p 1-65535 192.168.1.1
D. nmap “”sS “”Pn 192.168.1.1
Which of the following is not a Bluetooth attack?
A. Bluesnarfing
B. Bluedriving
C. Bluesmacking
D. Bluejacking
In Risk Management, how is the term "likelihood" related to the concept of "threat?"
A. Likelihood is the likely source of a threat that could exploit a vulnerability.
B. Likelihood is the probability that a threat-source will exploit a vulnerability.
C. Likelihood is a possible threat-source that may exploit a vulnerability.
D. Likelihood is the probability that a vulnerability is a threat-source.
Insecure direct object reference is a type of vulnerability where the application does not verify if the user is authorized to access the internal object via its name or key. Suppose a malicious user Rob tries to get access to the account of a benign user Ned. Which of the following requests best illustrates an attempt to exploit an insecure direct object reference vulnerability?
A. “GET/restricted/goldtransfer?to=Rob&from=1 or 1=1′ HTTP/1.1Host: westbank.com”
B. “GET/restricted/accounts/?name=Ned HTTP/1.1 Host: westbank.com”
C. “GET/restricted/bank.getaccount(“˜Ned’) HTTP/1.1 Host: westbank.com”
D. “GET/restricted/rn%00account%00Ned%00access HTTP/1.1 Host: westbank.com”
Why containers are less secure than virtual machines?
A. Host OS on containers has a larger surface attack.
B. Containers are attached to the same virtual network.
C. Containers may fulfill disk space of the host.
D. A compromise container may cause a CPU starvation of the host.
What does the option * indicate?
A. s
B. t
C. n
D. a
In which of the following password protection technique, random strings of characters are added to the password before calculating their hashes?
A. Keyed Hashing
B. Key Stretching
C. Salting
D. Double Hashing
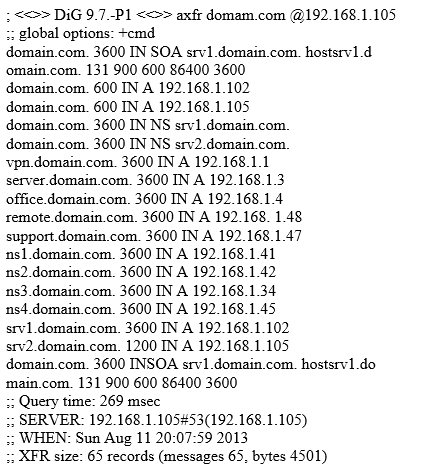
Look at the following output. What did the hacker accomplish?
A. The hacker used who is to gather publicly available records for the domain.
B. The hacker used the “fierce” tool to brute force the list of available domains.
C. The hacker listed DNS records on his own domain.
D. The hacker successfully transferred the zone and enumerated the hosts.
In IPv6 what is the major difference concerning application layer vulnerabilities compared to IPv4?
A. Implementing IPv4 security in a dual-stack network offers protection from IPv6 attacks too.
B. Vulnerabilities in the application layer are independent of the network layer. Attacks and mitigation techniques are almost identical.
C. Due to the extensive security measures built in IPv6, application layer vulnerabilities need not be addresses.
D. Vulnerabilities in the application layer are greatly different from IPv4.
An attacker has installed a RAT on a host. The attacker wants to ensure that when a user attempts to go to "www.MyPersonalBank.com", that the user is directed to a phishing site. Which file does the attacker need to modify?
A. Boot.ini
B. Sudoers
C. Networks
D. Hosts
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?
A. Spoof Scan
B. TCP SYN
C. TCP Connect scan
D. Idle scan
Which of the following tools is used to analyze the files produced by several packet-capture programs such as tcpdump, WinDump, Wireshark, and EtherPeek?
A. tcptrace
B. Nessus
C. OpenVAS
D. tcptraceroute
What type of vulnerability/attack is it when the malicious person forces the user's browser to send an authenticated request to a server?
A. Cross-site request forgery
B. Cross-site scripting
C. Session hijacking
D. Server side request forgery
This asymmetry cipher is based on factoring the product of two large prime numbers. What cipher is described above?
A. SHA
B. RSA
C. MD5
D. RC5
In which of the following cryptography attack methods, the attacker makes a series of interactive queries, choosing subsequent plaintexts based on the information from the previous encryptions?
A. Chosen-plaintext attack
B. Ciphertext-only attack
C. Adaptive chosen-plaintext attack
D. Known-plaintext attack
Free Access Full 312-50V10 Practice Test Free Questions
If you’re looking for more 312-50V10 practice test free questions, click here to access the full 312-50V10 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 312-50V10 certification journey!