312-50V10 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 312-50V10 certification? Take your preparation to the next level with our 312-50V10 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 312-50V10 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 312-50V10 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A security analyst is performing an audit on the network to determine if there are any deviations from the security policies in place. The analyst discovers that a user from the IT department had a dial-out modem installed. Which security policy must the security analyst check to see if dial-out modems are allowed?
A. Firewall-management policy
B. Acceptable-use policy
C. Remote-access policy
D. Permissive policy
Which of the following programs is usually targeted at Microsoft Office products?
A. Polymorphic virus
B. Multipart virus
C. Macro virus
D. Stealth virus
Which results will be returned with the following Google search query? site:target.com site:Marketing.target.com accounting
A. Results from matches on the site marketing.target.com that are in the domain target.com but do not include the word accounting.
B. Results matching all words in the query.
C. Results for matches on target.com and Marketing.target.com that include the word “accounting”
D. Results matching “accounting” in domain target.com but not on the site Marketing.target.com
In IPv6 what is the major difference concerning application layer vulnerabilities compared to IPv4?
A. Implementing IPv4 security in a dual-stack network offers protection from IPv6 attacks too.
B. Vulnerabilities in the application layer are independent of the network layer. Attacks and mitigation techniques are almost identical.
C. Due to the extensive security measures built in IPv6, application layer vulnerabilities need not be addresses.
D. Vulnerabilities in the application layer are greatly different from IPv4.
The collection of potentially actionable, overt, and publicly available information is known as
A. Open-source intelligence
B. Human intelligence
C. Social intelligence
D. Real intelligence
_________ is a set of extensions to DNS that provide the origin authentication of DNS data to DNS clients (resolvers) so as to reduce the threat of DNS poisoning, spoofing, and similar types of attacks.
A. DNSSEC
B. Resource records
C. Resource transfer
D. Zone transfer
If an attacker uses the command SELECT*FROM user WHERE name = "˜x' AND userid IS NULL; --"˜; which type of SQL injection attack is the attacker performing?
A. End of Line Comment
B. UNION SQL Injection
C. Illegal/Logically Incorrect Query
D. Tautology
A company's Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application. What kind of Web application vulnerability likely exists in their software?
A. Cross-site scripting vulnerability
B. Session management vulnerability
C. SQL injection vulnerability
D. Cross-site Request Forgery vulnerability
You are performing a penetration test. You achieved access via a buffer overflow exploit and you proceed to find interesting data, such as files with usernames and passwords. You find a hidden folder that has the administrator's bank account password and login information for the administrator's bitcoin account. What should you do?
A. Do not report it and continue the penetration test.
B. Transfer money from the administrator’s account to another account.
C. Do not transfer the money but steal the bitcoins.
D. Report immediately to the administrator.
A Security Engineer at a medium-sized accounting firm has been tasked with discovering how much information can be obtained from the firm's public facing web servers. The engineer decides to start by using netcat to port 80. The engineer receives this output: HTTP/1.1 200 OK - Server: Microsoft-IIS/6 - Expires: Tue, 17 Jan 2011 01:41:33 GMT Date: Mon, 16 Jan 2011 01:41:33 GMT Content-Type: text/html - Accept-Ranges: bytes - Last-Modified: Wed, 28 Dec 2010 15:32:21 GMT ETag: "b0aac0542e25c31:89d" Content-Length: 7369 - Which of the following is an example of what the engineer performed?
A. Cross-site scripting
B. Banner grabbing
C. SQL injection
D. Who is database query
What is the known plaintext attack used against DES which gives the result that encrypting plaintext with one DES key followed by encrypting it with a second DES key is no more secure than using a single key?
A. Man-in-the-middle attack
B. Meet-in-the-middle attack
C. Replay attack
D. Traffic analysis attack
There are several ways to gain insight on how a cryptosystem works with the goal of reverse engineering the process. A term describes when two pieces of data result in the value is?
A. Polymorphism
B. Escrow
C. Collusion
D. Collision
Which Metasploit Framework tool can help penetration tester for evading Anti-virus Systems?
A. msfencode
B. msfpayload
C. msfcli
D. msfd
You are the Network Admin, and you get a complaint that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL. What may be the problem?
A. Traffic is Blocked on UDP Port 53
B. Traffic is Blocked on TCP Port 80
C. Traffic is Blocked on TCP Port 54
D. Traffic is Blocked on UDP Port 80
In Wireshark, the packet bytes panes show the data of the current packet in which format?
A. Decimal
B. ASCII only
C. Binary
D. Hexadecimal
>NMAP ""sn 192.168.11.200-215 The NMAP command above performs which of the following?
A. A port scan
B. A ping scan
C. An operating system detect
D. A trace sweep
You need a tool that can do network intrusion prevention and intrusion detection, function as a network sniffer, and record network activity. What tool would you most likely select?
A. Snort
B. Nmap
C. Cain & Abel
D. Nessus
What is the purpose of DNS AAAA record?
A. Address prefix record
B. Address database record
C. Authorization, Authentication and Auditing record
D. IPv6 address resolution record
What is the purpose of a demilitarized zone on a network?
A. To scan all traffic coming through the DMZ to the internal network
B. To only provide direct access to the nodes within the DMZ and protect the network behind it
C. To provide a place to put the honeypot
D. To contain the network devices you wish to protect
While performing online banking using a Web browser, a user receives an email that contains a link to an interesting Web site. When the user clicks on the link, another Web browser session starts and displays a video of cats playing a piano. The next business day, the user receives what looks like an email from his bank, indicating that his bank account has been accessed from a foreign country. The email asks the user to call his bank and verify the authorization of a funds transfer that took place. What Web browser-based security vulnerability was exploited to compromise the user?
A. Clickjacking
B. Cross-Site Scripting
C. Cross-Site Request Forgery
D. Web form input validation
What is the most common method to exploit the "Bash Bug" or "ShellShock" vulnerability?
A. Manipulate format strings in text fields
B. SSH
C. SYN Flood
D. Through Web servers utilizing CGI (Common Gateway Interface) to send a malformed environment variable to a vulnerable Web server
You have gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your toolkit, you have an Ubuntu 9.10 Linux LiveCD. Which Linux-based tool can change any user's password or activate disabled Windows accounts?
A. John the Ripper
B. SET
C. CHNTPW
D. Cain & Abel
You have successfully gained access to your client's internal network and successfully comprised a Linux server which is part of the internal IP network. You want to know which Microsoft Windows workstations have file sharing enabled. Which port would you see listening on these Windows machines in the network?
A. 161
B. 3389
C. 445
D. 1433
Firewalls are the software or hardware systems that are able to control and monitor the traffic coming in and out the target network based on pre-defined set of rules. Which of the following types of firewalls can protect against SQL injection attacks?
A. Data-driven firewall
B. Stateful firewall
C. Packet firewall
D. Web application firewall
Which of the following Linux commands will resolve a domain name into IP address?
A. >host-t a hackeddomain.com
B. >host-t ns hackeddomain.com
C. >host -t soa hackeddomain.com
D. >host -t AXFR hackeddomain.com
On performing a risk assessment, you need to determine the potential impacts when some of the critical business process of the company interrupt its service. What is the name of the process by which you can determine those critical business?
A. Risk Mitigation
B. Emergency Plan Response (EPR)
C. Disaster Recovery Planning (DRP)
D. Business Impact Analysis (BIA)
It has been reported to you that someone has caused an information spillage on their computer. You go to the computer, disconnect it from the network, remove the keyboard and mouse, and power it down. What step in incident handling did you just complete?
A. Discovery
B. Recovery
C. Containment
D. Eradication
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient's consent, similar to email spamming?
A. Bluesmacking
B. Bluesniffing
C. Bluesnarfing
D. Bluejacking
If there is an Intrusion Detection System (IDS) in intranet, which port scanning technique cannot be used?
A. Spoof Scan
B. TCP SYN
C. TCP Connect scan
D. Idle scan
You are analyzing a traffic on the network with Wireshark. You want to routinely run a cron job which will run the capture against a specific set of IPs. "" 192.168.8.0/24. What command you would use?
A. tshark “”net 192.255.255.255 mask 192.168.8.0
B. wireshark “”capture “”local “”masked 192.168.8.0 “”range 24
C. sudo tshark “”f “net 192.168.8.0/24”
D. wireshark “”fetch “192.168.8/*”
Analyst is investigating proxy logs and found out that one of the internal user visited website storing suspicious java scripts. After opening one of them, he noticed that it is very hard to understand the code and that all codes differ from the typical java script. What is the name of this technique to hide the code and extend analysis time?
A. Steganography
B. Code encoding
C. Obfuscation
D. Encryption
You have several plain-text firewall logs that you must review to evaluate network traffic. You know that in order to do fast, efficient searches of the logs you must use regular expressions. Which command-line utility are you most likely to use?
A. Relational Database
B. MS Excel
C. Notepad
D. Grep
During the process of encryption and decryption, what keys are shared?
A. Private keys
B. User passwords
C. Public keys
D. Public and private keys
Which of the following cryptography attack is an understatement for the extraction of cryptographic secrets (e.g. the password to an encrypted file) from a person by a coercion or torture?
A. Chosen-Cipher text Attack
B. Ciphertext-only Attack
C. Timing Attack
D. Rubber Hose Attack
This tool is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools. Which of the following tools is being described?
A. wificracker
B. Airguard
C. WLAN-crack
D. Aircrack-ng
Which of the following statements is TRUE?
A. Sniffers operate on Layer 2 of the OSI model
B. Sniffers operate on Layer 3 of the OSI model
C. Sniffers operate on both Layer 2 & Layer 3 of the OSI model.
D. Sniffers operate on the Layer 1 of the OSI model.
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing. What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
A. Service Level Agreement
B. Project Scope
C. Rules of Engagement
D. Non-Disclosure Agreement
You want to do an ICMP scan on a remote computer using hping2. What is the proper syntax?
A. hping2 -1 host.domain.com
B. hping2-i host.domain.com
C. hping2 “”set-ICMP host.domain.com
D. hping2 host.domain.com
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124. An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is: nmap 192.168.1.64/28 Why he cannot see the servers?
A. He needs to change the address to 192.168.1.0 with the same mask
B. He needs to add the command “”ip address”” just before the IP address.
C. He is scanning from 192.168.1.64 to 192.168.1.78 because of the mask /28 and the servers are not in that range.
D. The network must be down and the nmap command and IP address are ok
Which of the following is one of the most effective ways to prevent Cross-site Scripting (XSS) flaws in software applications?
A. Use security policies and procedures to define and implement proper security settings.
B. Use digital certificates to authenticate a server prior to sending data.
C. Validate and escape all information sent to a server.
D. Verify access right before allowing access to protected information and UI controls.
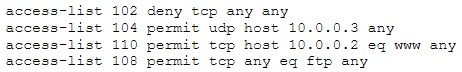
The security administrator of ABC needs to permit Internet traffic in the host 10.0.0.2 and UDP traffic in the host 10.0.0.3. He also needs to permit all FTP traffic to the rest of the network and deny all other traffic. After he applied his ACL configuration in the router, nobody can access to the ftp, and the permitted hosts cannot access the Internet. According to the next configuration, what is happening in the network?
A. The ACL 104 needs to be first because is UDP
B. The ACL 110 needs to be changed to port 80
C. The ACL for FTP must be before the ACL 110
D. The first ACL is denying all TCP traffic and the other ACLs are being ignored by the router
Cross-site request forgery involves:
A. A request sent by a malicious user from a browser to a server
B. Modification of a request by a proxy between client and server
C. A browser making a request to a server without the user’s knowledge
D. A server making a request to another server without the user’s knowledge
Elliot is in the process of exploiting a web application that uses SQL as a back-end database. He is determined that the application is vulnerable to SQL injection and has introduced conditional timing delays into injected queries to determine whether they are successful. What type of SQL injection is Elliot most likely performing?
A. NoSQL injection
B. Blind SQL injection
C. Union-based SQL injection
D. Error-based SQL injection
A virus that attempts to install itself inside the file it is infecting is called?
A. Tunneling virus
B. Cavity virus
C. Polymorphic virus
D. Stealth virus
The configuration allows a wired or wireless network interface controller to pass all traffic it receives to the Central Processing Unit (CPU), rather than passing only the frames that the controller is intended to receive. Which of the following is being described?
A. Multi-cast mode
B. Promiscuous mode
C. WEM
D. Port forwarding
Which of the following is the BEST way to defend against network sniffing?
A. Restrict Physical Access to Server Rooms hosting Critical Servers
B. Use Static IP Address
C. Using encryption protocols to secure network communications
D. Register all machines MAC Address in a Centralized Database
Which of the following describes the characteristics of a Boot Sector Virus?
A. Modifies directory table entries so that directory entries point to the virus code instead of the actual program.
B. Moves the MBR to another location on the RAM and copies itself to the original location of the MBR.
C. Moves the MBR to another location on the hard disk and copies itself to the original location of the MBR.
D. Overwrites the original MBR and only executes the new virus code.
What does a firewall check to prevent particular ports and applications from getting packets into an organization?
A. Transport layer port numbers and application layer headers
B. Presentation layer headers and the session layer port numbers
C. Network layer headers and the session layer port numbers
D. Application layer port numbers and the transport layer headers
When you are collecting information to perform a data analysis, Google commands are very useful to find sensitive information and files. These files may contain information about passwords, system functions, or documentation. What command will help you to search files using Google as a search engine?
A. site: target.com filetype:xls username password email
B. domain: target.com archieve:xls username password email
C. inurl: target.com filename:xls username password email
D. site: target.com file:xls username password email
Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). More generally, it is about constructing and analyzing protocols that overcome the influence of adversaries and that are related to various aspects in information security such as data confidentially, data integrity, authentication, and non-repudiation. Modern cryptography intersects the disciplines of mathematics, computer science, and electrical engineering. Applications of cryptography include ATM cards, computer passwords, and electronic commerce. Basic example to understand how cryptography works is given below:Which of the following choices true about cryptography?
A. Algorithm is not the secret; key is the secret.
B. Public-key cryptography, also known as asymmetric cryptography, public key is for decrypt, private key is for encrypt.
C. Secure Sockets Layer (SSL) use the asymmetric encryption both (public/private key pair) to deliver the shared session key and to achieve a communication way.
D. Symmetric-key algorithms are a class of algorithms for cryptography that use the different cryptographic keys for both encryption of plaintext and decryption of ciphertext.
Free Access Full 312-50V10 Practice Exam Free
Looking for additional practice? Click here to access a full set of 312-50V10 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 312-50V10 certification journey!