312-49V10 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 312-49V10 certification exam? Start your preparation the smart way with our 312-49V10 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 312-49V10 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 312-49V10 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
To make sure the evidence you recover and analyze with computer forensics software can be admitted in court, you must test and validate the software. What group is actively providing tools and creating procedures for testing and validating computer forensics software?
A. Computer Forensics Tools and Validation Committee (CFTVC)
B. Association of Computer Forensics Software Manufactures (ACFSM)
C. National Institute of Standards and Technology (NIST)
D. Society for Valid Forensics Tools and Testing (SVFTT)
Lance wants to place a honeypot on his network. Which of the following would be your recommendations?
A. Use a system that has a dynamic addressing on the network
B. Use a system that is not directly interacting with the router
C. Use it on a system in an external DMZ in front of the firewall
D. It doesn’t matter as all replies are faked
Where is the default location for Apache access logs on a Linux computer?
A. usr/local/apache/logs/access_log
B. bin/local/home/apache/logs/access_log
C. usr/logs/access_log
D. logs/usr/apache/access_log
Investigator Janet comes across a suspicious Windows registry key during a computer hacking forensic investigation. She believes modifying this key is associated with the recent cyberattack on the company's servers. In order to confirm this, Janet needs to reference a timestamp embedded inside the registry key. What is the correct name of this timestamp?
A. Last Write Time
B. User Activity Time
C. System Modification Time
D. Current System Time
During an incident response to a data breach in a company's AWS environment, a forensic investigator is tasked to analyze and extract data from different storage types for further examination. What would be the most appropriate and effective course of action given that Amazon S3, EBS, and EFS were used?
A. Implement ACL permissions for S3 buckets, and attach the affected EFS to a Linux instance for data extraction
B. Create IAM policies to restrict access, and proceed with data extraction from EBS and EFS storage types
C. Extract all data directly from Amazon S3 and EBS, and attach the EFS to a Linux instance for data extraction
D. Snapshot the affected EBS volumes and S3 buckets, and mount EFS to a Linux instance for analysis
When investigating a computer forensics case where Microsoft Exchange and Blackberry Enterprise server are used, where would investigator need to search to find email sent from a Blackberry device?
A. RIM Messaging center
B. Blackberry Enterprise server
C. Microsoft Exchange server
D. Blackberry desktop redirector
Amber, a black hat hacker, has embedded a malware into a small enticing advertisement and posted it on a popular ad-network that displays across various websites. What is she doing?
A. Click-jacking
B. Compromising a legitimate site
C. Spearphishing
D. Malvertising
Which of the following data structures stores attributes of a process, as well as pointers to other attributes and data structures?
A. Lsproc
B. DumpChk
C. RegEdit
D. EProcess
Which of the following Event Correlation Approach is an advanced correlation method that assumes and predicts what an attacker can do next after the attack by studying the statistics and probability and uses only two variables?
A. Bayesian Correlation
B. Vulnerability-Based Approach
C. Rule-Based Approach
D. Route Correlation
The surface of a hard disk consists of several concentric rings known as tracks; each of these tracks has smaller partitions called disk blocks. What is the size of each block?
A. 512 bits
B. 512 bytes
C. 256 bits
D. 256 bytes
Matthew has been assigned the task of analyzing a suspicious MS Office document via static analysis over an Ubuntu-based forensic machine. He wants to see what type of document it is, whether it is encrypted, or contains any flash objects/VBA macros. Which of the following python-based script should he run to get relevant information?
A. oleid.py
B. oleform.py
C. oledir.py
D. pdfid.py
John is using Firewalk to test the security of his Cisco PIX firewall. He is also utilizing a sniffer located on a subnet that resides deep inside his network. After analyzing the sniffer log files, he does not see any of the traffic produced by Firewalk. Why is that?
A. Firewalk cannot pass through Cisco firewalls
B. Firewalk sets all packets with a TTL of zero
C. Firewalk cannot be detected by network sniffers
D. Firewalk sets all packets with a TTL of one
Harold wants to set up a firewall on his network but is not sure which one would be the most appropriate. He knows he needs to allow FTP traffic to one of the servers on his network, but he wants to only allow FTP-PUT. Which firewall would be most appropriate for Harold? needs?
A. Circuit-level proxy firewall
B. Packet filtering firewall
C. Application-level proxy firewall
D. Data link layer firewall
What does ICMP Type 3/Code 13 mean?
A. Host Unreachable
B. Administratively Blocked
C. Port Unreachable
D. Protocol Unreachable
You have been given the task to investigate web attacks on a Windows-based server. Which of the following commands will you use to look at the sessions the machine has opened with other systems?
A. Net sessions
B. Net config
C. Net share
D. Net use
Which of the following technique creates a replica of an evidence media?
A. Data Extraction
B. Backup
C. Bit Stream Imaging
D. Data Deduplication
Which of the following files gives information about the client sync sessions in Google Drive on Windows?
A. sync_log.log
B. Sync_log.log
C. sync.log
D. Sync.log
Frank, a cloud administrator in his company, needs to take backup of the OS disks of two Azure VMs that store business-critical data. Which type of Azure blob storage can he use for this purpose?
A. Append blob
B. Medium blob
C. Block blob
D. Page blob
Fill in the missing Master Boot Record component. 1. Master boot code 2. Partition table 3. ____________
A. Signature word
B. Volume boot record
C. Boot loader
D. Disk signature
A cybersecurity investigator is working on a case involving a malicious executable suspected of being packed using a popular program packer. The investigator realizes that the packer used is password-protected. In such a scenario, what should be the investigator's first course of action to analyze the packed file?
A. Mount compound files
B. Perform static analysis on the packed file
C. Decrypt the password to unpack the file
D. Run the packed file in a controlled environment for dynamic analysis
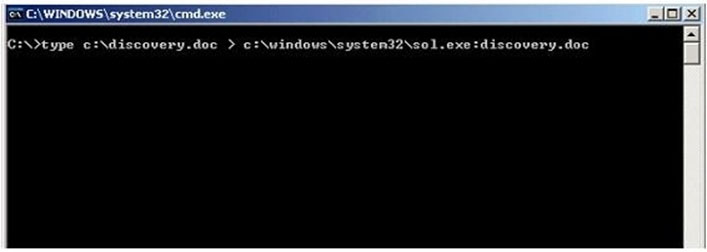
What feature of Windows is the following command trying to utilize?
A. White space
B. AFS
C. ADS
D. Slack file
A forensic investigator is examining an attack on a MySQL database. The investigator has been given access to a server, but the physical MySQL data files are encrypted, and the database is currently inaccessible. The attacker seems to have tampered with the data. Which MySQL utility program would most likely assist the investigator in determining the changes that occurred during the attack?
A. Mysqlbinlog, because it reads the binary log files directly and displays them in text format
B. Myisamchk, because it views the status of the MylSAM table or checks, repairs, and optimizes them
C. Mysqldump, because it allows dumping a database for backup purposes
D. Mysqlaccess, because it checks the access privileges defined for a hostname or username
An international corporation is targeted by a severe data breach, resulting in massive corruption in its MySQL database. The forensic investigator is responsible for recovering the corrupted data and tracing the perpetrators. During the investigation, the team detected a high number of unauthorized access attempts from several hostnames and usernames that coincided with the attack. Which MySQL utility program would most suitably validate these access attempts in this scenario?
A. Mysqlaccess, due to its ability to check and validate the access privileges defined for a hostname or username
B. Myisamlog, for its functionality to process the contents of the MyISAM log file and perform recovery operations
C. Mysqlbinlog, due to its ability to read and display binary log files in text format
D. Mysqldump, for its capacity to dump a database or a collection of databases for backup and restore purposes
Which of the following is an iOS Jailbreaking tool?
A. Kingo Android ROOT
B. Towelroot
C. One Click Root
D. Redsn0w
Forensic Investigator Alex has to collect data from a suspect's large drive in a time-bound investigation. The court would allow him to retain the original drive. Considering these factors, what should be Alex's primary considerations to ensure a forensically sound data acquisition?
A. Using Microsoft disk compression tools and validating the data acquisition process
B. Sanitizing the target media using the (German) VSITR method and acquiring volatile data
C. Enabling write protection on the evidence media and prioritizing data acquisition based on evidentiary value
D. Utilizing lossless compression tools and creating a bit-stream copy using a reliable acquisition tool
Which code does the FAT file system use to mark the file as deleted?
A. ESH
B. 5EH
C. H5E
D. E5H
What type of analysis helps to identify the time and sequence of events in an investigation?
A. Time-based
B. Functional
C. Relational
D. Temporal
Jeff is a forensics investigator for a government agency's cyber security office. Jeff is tasked with acquiring a memory dump of a Windows 10 computer that was involved in a DDoS attack on the government agency's web application. Jeff is onsite to collect the memory. What tool could Jeff use?
A. Memcheck
B. RAMMapper
C. Autopsy
D. Volatility
Who is responsible for the following tasks? ✑ Secure the scene and ensure that is maintained in a secure state until the Forensic Team advises ✑ Make notes about the scene that will eventually be handed over to the Forensic Team
A. Non-forensics staff
B. Lawyers
C. System administrators
D. Local managers or other non-forensic staff
Which type of attack is possible when attackers know some credible information about the victim's password, such as the password length, algorithms involved, or the strings and characters used in its creation?
A. Rule-Based Attack
B. Brute-Forcing Attack
C. Dictionary Attack
D. Hybrid Password Guessing Attack
If you plan to startup a suspect's computer, you must modify the ___________ to ensure that you do not contaminate or alter data on the suspect's hard drive by booting to the hard drive.
A. deltree command
B. CMOS
C. Boot.sys
D. Scandisk utility
Which of the following is NOT a graphics file?
A. Picture1.tga
B. Picture2.bmp
C. Picture3.nfo
D. Picture4.psd
Which federal computer crime law specifically refers to fraud and related activity in connection with access devices like routers?
A. 18 U.S.C. 1029
B. 18 U.S.C. 1362
C. 18 U.S.C. 2511
D. 18 U.S.C. 2703
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
A. All virtual memory will be deleted
B. The wrong partition may be set to active
C. This action can corrupt the disk
D. The computer will be set in a constant reboot state
Hard disk data addressing is a method of allotting addresses to each _______ of data on a hard disk.
A. Physical block
B. Operating system block
C. Hard disk block
D. Logical block
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
A. Text semagram
B. Visual semagram
C. Grill cipher
D. Visual cipher
Which program uses different techniques to conceal a malware's code, thereby making it difficult for security mechanisms to detect or remove it?
A. Dropper
B. Packer
C. Injector
D. Obfuscator
An investigator is studying a suspicious Windows service discovered on a corporate system that seems to be associated with malware. The service has a name similar to a genuine Windows service, runs as a SYSTEM account, and exhibits potentially harmful behavior. Which tool and method should the investigator use to study the service's behavior without allowing it to inflict more damage?
A. Deploy Autoruns for Windows to check if the suspicious service is configured to run at system bootup
B. Inspect the startup folder for the presence of the suspicious service using command prompt commands
C. Use SrvMan to stop the suspicious service and analyze its impact on the system
D. Utilize the Windows Service Manager to create an identical service and study its behavior
While looking through the IIS log file of a web server, you find the following entries:What is evident from this log file?
A. Web bugs
B. Cross site scripting
C. Hidden fields
D. SQL injection is possible
During an investigation, a forensics analyst discovers an unusual increase in outbound network traffic, network traffic traversing on non-standard ports, and multiple failed login attempts on a host system. The analyst also found that certain programs were using these unusual ports, appearing to be legitimate. If these are the primary Indicators of Compromise, what should be the next immediate step in the investigation to contain the intrusion effectively?
A. Enforcing stringent password policies and re-authenticating all users to prevent further login anomalies
B. Examining the logs for repeated requests for the same file, indicating a possible exploit attempt
C. Analyzing Uniform Resource Locators for any signs of phishing or spamming activities
D. Conducting a deep dive into user-agent strings to determine if there is any spoofing of device OS and browser information
A Computer Hacking Forensics Investigator (CHFI) has been asked to retrieve specific email files from a large RAID server after a data breach. Additionally, fragments of unallocated (deleted) data are also required. However, there is a severe constraint on time and resources. Considering these requirements, which type of data acquisition should the investigator primarily focus on?
A. Logical acquisition
B. Bit-stream disk-to-disk
C. Sparse acquisition
D. Bit-stream disk-to-image-file
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
A. Shortcut Files
B. Virtual files
C. Prefetch Files
D. Image Files
An investigator has acquired packed software and needed to analyze it for the presence of malice. Which of the following tools can help in finding the packaging software used?
A. SysAnalyzer
B. PEiD
C. Comodo Programs Manager
D. Dependency Walker
During an investigation, Noel found a SIM card from the suspect's mobile. The ICCID on the card is 8944245252001451548. What does the first four digits (89 and 44) in the ICCID represent?
A. TAC and industry identifier
B. Industry identifier and country code
C. Country code and industry identifier
D. Issuer identifier number and TAC
You are working as Computer Forensics investigator and are called by the owner of an accounting firm to investigate possible computer abuse by one of the firm's employees. You meet with the owner of the firm and discover that the company has never published a policy stating that they reserve the right to inspect their computing assets at will. What do you do?
A. Inform the owner that conducting an investigation without a policy is not a problem because the company is privately owned
B. Inform the owner that conducting an investigation without a policy is a violation of the 4th amendment
C. Inform the owner that conducting an investigation without a policy is a violation of the employee’s expectation of privacy
D. Inform the owner that conducting an investigation without a policy is not a problem because a policy is only necessary for government agencies
An attacker successfully gained access to a remote Windows system and plans to install persistent backdoors on it. Before that, to avoid getting detected in future, he wants to cover his tracks by disabling the last-accessed timestamps of the machine. What would he do to achieve this?
A. Set the registry value of HKLMSYSTEMCurrentControlSetControlFileSystemNtfsDisableLastAccessUpdate to 0
B. Run the command fsutil behavior set disablelastaccess 0
C. Set the registry value of HKLMSYSTEMCurrentControlSetControlFileSystemNtfsDisableLastAccessUpdate to 1
D. Run the command fsutil behavior set enablelastaccess 0
During an international cybercrime investigation, your team discovers an intercepted email with a sequence of special characters. Believing that the Unicode standard might have been used in encoding the message, which of the following elements could serve as the strongest indicator of this suspicion?
A. The presence of characters from multiple modern and historic scripts
B. The presence of over 128.000 different characters in the intercepted email
C. The presence of a unique number for each character, irrespective of the platform, program, and language
D. The presence of characters from a single non-English script
If a suspect computer is located in an area that may have toxic chemicals, you must:
A. coordinate with the HAZMAT team
B. determine a way to obtain the suspect computer
C. assume the suspect machine is contaminated
D. do not enter alone
Which file is a sequence of bytes organized into blocks understandable by the system's linker?
A. executable file
B. source file
C. Object file
D. None of these
UEFI is a specification that defines a software interface between an OS and platform firmware. Where does this interface store information about files present on a disk?
A. BIOS-MBR
B. GUID Partition Table (GPT)
C. Master Boot Record (MBR)
D. BIOS Parameter Block
Access Full 312-49V10 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 312-49V10 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 312-49V10 mock test free today—and take a major step toward exam success!