312-49V10 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 312-49V10 certification? Our 312-49V10 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 312-49V10 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 312-49V10 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which Linux command when executed displays kernel ring buffers or information about device drivers loaded into the kernel?
A. pgrep
B. dmesg
C. fsck
D. grep
After an unexpected shutdown of a company's database server, the IT forensics team is tasked with collecting data from the Database Plan Cache to investigate potential issues. What query should they use to retrieve the SQL text of all cached entries and acquire additional aggregate performance statistics?
A. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_plan_attributes(plan_handle) followed by: select * from sys.dm_exec_query_stats
B. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_sql_text(plan_handle) followed by: select * from sys.dm_exec_plan_attributes(plan_handle)
C. Use: select * from sys.dm_exec_sql_text(plan_handle) cross apply sys.dm_exec_cached_plans followed by: select * from sys.dm_exec_query_stats
D. Use: select * from sys.dm_exec_cached_plans cross apply sys.dm_exec_sql_text(plan_handle) followed by: select * from sys.dm_exec_query_stats
In an ongoing investigation, a computer forensics investigator encounters a suspicious file believed to be packed using a password-protected program packer. The investigator possesses both the knowledge of the packing tool used and the necessary unpacking tool. What critical step should the investigator consider before analyzing the packed file?
A. Conduct static analysis on the packed file immediately
B. Reverse engineer the packed file to understand the hidden attack tools
C. Attempt to decrypt the password prior to unpacking the file
D. Run the packed file in a controlled environment for dynamic analysis
A cybersecurity investigator is conducting a search and seizure operation involving a large data breach. She needs a witness’s signature for the agreement to proceed. She is considering one of her team members as a witness but is unsure whether this would comply with standard procedures. According to best practices in obtaining witness signatures during such operations, what actions should she take?
A. She should not involve any of her team members as a witness to avoid potential bias in court
B. If one witness is needed, she may consider her team member, given that they understand the relevance and can testify voluntarily
C. She should choose anyone present during the seizure as a witness regardless of their understanding of the case
D. She should choose a member from her team as a witness as it saves time and resources
You are an information security analyst at a large pharmaceutical company. While performing a routine review of audit logs, you have noticed a significant amount of egress traffic to various IP addresses on destination port 22 during off-peak hours. You researched some of the IP addresses and found that many of them are in Eastern Europe. What is the most likely cause of this traffic?
A. The organization’s primary internal DNS server has been compromised and is performing DNS zone transfers to malicious external entities
B. Data is being exfiltrated by an advanced persistent threat (APT)
C. Malicious software on internal system is downloading research data from partner SFTP servers in Eastern Europe
D. Internal systems are downloading automatic Windows updates
An Expert witness give an opinion if:
A. The Opinion, inferences or conclusions depend on special knowledge, skill or training not within the ordinary experience of lay jurors
B. To define the issues of the case for determination by the finder of fact
C. To stimulate discussion between the consulting expert and the expert witness
D. To deter the witness form expanding the scope of his or her investigation beyond the requirements of the case
In a Filesystem Hierarchy Standard (FHS), which of the following directories contains the binary files required for working?
A. /mnt
B. /sbin
C. /media
D. /proc
What is the framework used for application development for iOS-based mobile devices?
A. Cocoa Touch
B. Dalvik
C. Zygote
D. AirPlay
When examining a file with a Hex Editor, what space does the file header occupy?
A. the last several bytes of the file
B. the first several bytes of the file
C. none, file headers are contained in the FAT
D. one byte at the beginning of the file
Files stored in the Recycle Bin in its physical location are renamed as Dxy.ext, where `x` represents the ___________________.
A. Drive name
B. Original file name’s extension
C. Sequential number
D. Original file name
A forensic investigator encounters a suspicious executable on a compromised system, believed to be packed using a known program packer, and is password-protected. The investigator has knowledge of the tool used for packing and has the corresponding unpacking tool. What should be the next best course of action to examine the executable?
A. Use the unpacking tool to decompress the executable, without dealing with the password
B. Run a dynamic analysis on the packed executable in a controlled environment
C. Decrypt the password to unpack the executable before analyzing
D. Use reverse engineering to understand the attack tool hidden inside
Under which Federal Statutes does FBI investigate for computer crimes involving e-mail scams and mail fraud?
A. 18 U.S.C. 1029 Possession of Access Devices
B. 18 U.S.C. 1030 Fraud and related activity in connection with computers
C. 18 U.S.C. 1343 Fraud by wire, radio or television
D. 18 U.S.C. 1361 Injury to Government Property
E. 18 U.S.C. 1362 Government communication systems
F. 18 U.S.C. 1831 Economic Espionage Act
G. 18 U.S.C. 1832 Trade Secrets Act
A breach resulted from a malware attack that evaded detection and compromised the machine memory without installing any software or accessing the hard drive. What technique did the adversaries use to deliver the attack?
A. Trojan
B. JavaScript
C. Spyware
D. Fileless
Which ISO Standard enables laboratories to demonstrate that they comply with quality assurance and provide valid results?
A. ISO/IEC 16025
B. ISO/IEC 18025
C. ISO/IEC 19025
D. ISO/IEC 17025
When obtaining a warrant, it is important to:
A. particularlydescribe the place to be searched and particularly describe the items to be seized
B. generallydescribe the place to be searched and particularly describe the items to be seized
C. generallydescribe the place to be searched and generally describe the items to be seized
D. particularlydescribe the place to be searched and generally describe the items to be seized
Bob has encountered a system crash and has lost vital data stored on the hard drive of his Windows computer. He has no cloud storage or backup hard drives. he wants to recover all those data, which includes his personal photos, music, documents, videos, official email, etc. Which of the following tools shall resolve Bob's purpose?
A. Colasoft’s Capsa
B. Recuva
C. Cain & Abel
D. Xplico
Which of the following acts as a network intrusion detection system as well as network intrusion prevention system?
A. Accunetix
B. Nikto
C. Snort
D. Kismet
You work as an IT security auditor hired by a law firm in Boston to test whether you can gain access to sensitive information about the company clients. You have rummaged through their trash and found very little information. You do not want to set off any alarms on their network, so you plan on performing passive foot printing against their Web servers. What tool should you use?
A. Ping sweep
B. Nmap
C. Netcraft
D. Dig
A forensic investigator has collected a compromised Amazon Echo Dot and a smartphone from a crime scene. The Alexa app on the smartphone is synced with the Echo Dot. To begin investigating these devices, the investigator needs to obtain certain artifacts. In this scenario, which of the following sequence of steps should the investigator follow to acquire the necessary artifacts for a client-based analysis?
A. Retrieve database files using the adb pull command -> Generate an image of the firmware -> Parse database files -> Conduct data analysis
B. Parse database files -> Retrieve database files using the adb pull command -> Generate an image of the firmware -> Conduct data analysis
C. Generate an image of the firmware -> Retrieve database files using the adb pull command -> Parse database files -> Conduct data analysis
D. Retrieve database files using the adb pull command -> Parse database files -> Generate an image of the firmware -> Conduct data analysis
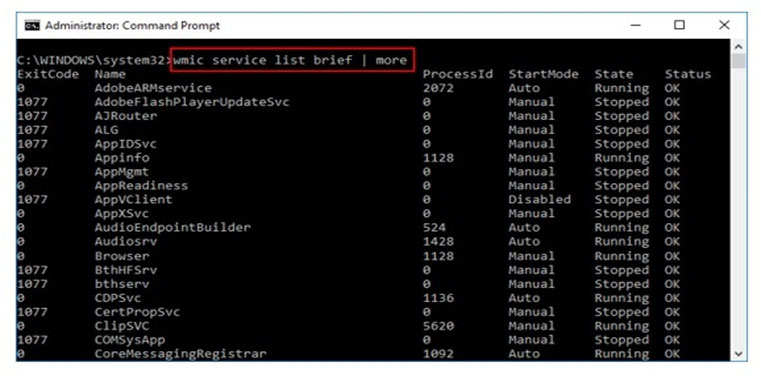
What is the investigator trying to view by issuing the command displayed in the following screenshot?
A. List of services stopped
B. List of services closed recently
C. List of services recently started
D. List of services installed
Which of the following files gives information about the client sync sessions in Google Drive on Windows?
A. sync_log.log
B. Sync_log.log
C. sync.log
D. Sync.log
Which of the following files stores information about local Dropbox installation and account, email IDs linked with the account, current version/build for the local application, the host_id, and local path information?
A. host.db
B. sigstore.db
C. config.db
D. filecache.db
Study the log given below and answer the following question: Apr 24 14:46:46 [4663]: spp_portscan: portscan detected from 194.222.156.169 Apr 24 14:46:46 [4663]: IDS27/FIN Scan: 194.222.156.169:56693 -> 172.16.1.107:482 Apr 24 18:01:05 [4663]: IDS/DNS-version-query: 212.244.97.121:3485 -> 172.16.1.107:53 Apr 24 19:04:01 [4663]: IDS213/ftp-passwd-retrieval: 194.222.156.169:1425 -> 172.16.1.107:21 Apr 25 08:02:41 [5875]: spp_portscan: PORTSCAN DETECTED from 24.9.255.53 Apr 25 02:08:07 [5875]: IDS277/DNS-version-query: 63.226.81.13:4499 -> 172.16.1.107:53 Apr 25 02:08:07 [5875]: IDS277/DNS-version-query: 63.226.81.13:4630 -> 172.16.1.101:53 Apr 25 02:38:17 [5875]: IDS/RPC-rpcinfo-query: 212.251.1.94:642 -> 172.16.1.107:111 Apr 25 19:37:32 [5875]: IDS230/web-cgi-space-wildcard: 198.173.35.164:4221 -> 172.16.1.107:80 Apr 26 05:45:12 [6283]: IDS212/dns-zone-transfer: 38.31.107.87:2291 -> 172.16.1.101:53 Apr 26 06:43:05 [6283]: IDS181/nops-x86: 63.226.81.13:1351 -> 172.16.1.107:53 Apr 26 06:44:25 victim7 PAM_pwdb[12509]: (login) session opened for user simple by (uid=0) Apr 26 06:44:36 victim7 PAM_pwdb[12521]: (su) session opened for user simon by simple(uid=506) Apr 26 06:45:34 [6283]: IDS175/socks-probe: 24.112.167.35:20 -> 172.16.1.107:1080 Apr 26 06:52:10 [6283]: IDS127/telnet-login-incorrect: 172.16.1.107:23 -> 213.28.22.189:4558 Precautionary measures to prevent this attack would include writing firewall rules. Of these firewall rules, which among the following would be appropriate?
A. Disallow UDP53 in from outside to DNS server
B. Allow UDP53 in from DNS server to outside
C. Disallow TCP53 in from secondaries or ISP server to DNS server
D. Block all UDP traffic
During a computer hacking forensic investigation, an investigator is tasked with acquiring volatile data from a live Linux system with limited physical access. Which methodology would be the most suitable for this scenario?
A. Using Belkasoft Live RAM Capturer to extract the entire contents of the computer’s volatile memory
B. Performing remote acquisition of volatile data from a Linux machine using dd and netcat
C. Using the fmem module and dd command locally to access the RAM and acquire its content directly
D. Performing local acquisition of RAM using the LiME tool
Which of the following protocols allows non-ASCII files, such as video, graphics, and audio, to be sent through the email messages?
A. MIME
B. BINHEX
C. UT-16
D. UUCODE
Choose the layer in iOS architecture that provides frameworks for iOS app development?
A. Core OS
B. Core services
C. Media services
D. Cocoa Touch
What is the name of the first reserved sector in File allocation table?
A. Volume Boot Record
B. Partition Boot Sector
C. Master Boot Record
D. BIOS Parameter Block
The Recycle Bin exists as a metaphor for throwing files away, but it also allows a user to retrieve and restore files. Once the file is moved to the recycle bin, a record is added to the log file that exists in the Recycle Bin. Which of the following files contains records that correspond to each deleted file in the Recycle Bin?
A. INFO2
B. INFO1
C. LOGINFO1
D. LOGINFO2
Simon is a former employee of Trinitron XML Inc. He feels he was wrongly terminated and wants to hack into his former company's network. Since Simon remembers some of the server names, he attempts to run the axfr and ixfr commands using DIG. What is Simon trying to accomplish here?
A. Send DOS commands to crash the DNS servers
B. Perform DNS poisoning
C. Perform a zone transfer
D. Enumerate all the users in the domain
Gary is checking for the devices connected to USB ports of a suspect system during an investigation. Select the appropriate tool that will help him document all the connected devices.
A. DevScan
B. Devcon
C. fsutil
D. Reg.exe
Hackers can gain access to Windows Registry and manipulate user passwords, DNS settings, access rights or others features that they may need in order to accomplish their objectives. One simple method for loading an application at startup is to add an entry (Key) to the following Registry Hive:
A. HKEY_LOCAL_MACHINEhardwarewindowsstart
B. HKEY_LOCAL_USERSSoftwareMicrosoftoldVersionLoad
C. HKEY_CURRENT_USERMicrosoftDefault
D. HKEY_LOCAL_MACHINESoftwareMicrosoftCurrentVersionRun
A forensic investigator discovers an Android smartwatch at the crime scene during an investigation. The investigator realizes the smartwatch was potentially involved in the crime, but the device associated with it was not found at the scene. What is the most suitable initial step for the investigator to retrieve meaningful data from the smartwatch?
A. The investigator should first physically dismantle the smartwatch to access its internal storage
B. The investigator should immediately turn off the smartwatch to prevent data manipulation
C. The investigator should start by understanding the smartwatch’s basic framework, including its APIs
D. The investigator should directly analyze data stored on the smartwatch using IoT forensics tools
Which type of attack is possible when attackers know some credible information about the victim's password, such as the password length, algorithms involved, or the strings and characters used in its creation?
A. Rule-Based Attack
B. Brute-Forcing Attack
C. Dictionary Attack
D. Hybrid Password Guessing Attack
To preserve digital evidence, an investigator should ____________________.
A. Make two copies of each evidence item using a single imaging tool
B. Make a single copy of each evidence item using an approved imaging tool
C. Make two copies of each evidence item using different imaging tools
D. Only store the original evidence item
What operating system would respond to the following command? c:> nmap -sW 10.10.145.65
A. Windows 95
B. FreeBSD
C. Windows XP
D. Mac OS X
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
A. It contains the times and dates of when the system was last patched
B. It is not necessary to scan the virtual memory of a computer
C. It contains the times and dates of all the system files
D. Hidden running processes
Mark works for a government agency as a cyber-forensic investigator. He has been given the task of restoring data from a hard drive. The partition of the hard drive was deleted by a disgruntled employee in order to hide their nefarious actions. What tool should Mark use to restore the data?
A. R-Studio
B. EFSDump
C. Diskview
D. Diskmon
Consider the scenario where a large multinational corporation suspects an internal security breach, with significant data possibly compromised. The corporate forensic team initiates the process of conducting a comprehensive forensic investigation following the search and seizure protocols. During this process, they want to ensure they capture all the required information and minimize disruption to the company's ongoing business operations. Which among the following activities should NOT be a part of their plan for this search and seizure operation?
A. Generating a comprehensive list of all potentially involved devices along with their specifications, status, and locations
B. Obtaining formal written consent from the company’s owner before beginning the investigation process
C. Requesting a warrant for search and seizure detailing the exact locations and types of evidence expected to be found
D. Carrying out all search and seizure activities without seeking witness signatures for the activities performed
Where does Encase search to recover NTFS files and folders?
A. MBR
B. MFT
C. Slack space
D. HAL
Harold is a computer forensics investigator working for a consulting firm out of Atlanta Georgia. Harold is called upon to help with a corporate espionage case in Miami Florida. Harold assists in the investigation by pulling all the data from the computers allegedly used in the illegal activities. He finds that two suspects in the company where stealing sensitive corporate information and selling it to competing companies. From the email and instant messenger logs recovered, Harold has discovered that the two employees notified the buyers by writing symbols on the back of specific stop signs. This way, the buyers knew when and where to meet with the alleged suspects to buy the stolen material. What type of steganography did these two suspects use?
A. Text semagram
B. Visual semagram
C. Grill cipher
D. Visual cipher
Rusty, a computer forensics apprentice, uses the command nbtstat `"c while analyzing the network information in a suspect system. What information is he looking for?
A. Contents of the network routing table
B. Status of the network carrier
C. Contents of the NetBIOS name cache
D. Network connections
You are working as Computer Forensics investigator and are called by the owner of an accounting firm to investigate possible computer abuse by one of the firm's employees. You meet with the owner of the firm and discover that the company has never published a policy stating that they reserve the right to inspect their computing assets at will. What do you do?
A. Inform the owner that conducting an investigation without a policy is not a problem because the company is privately owned
B. Inform the owner that conducting an investigation without a policy is a violation of the 4th amendment
C. Inform the owner that conducting an investigation without a policy is a violation of the employee’s expectation of privacy
D. Inform the owner that conducting an investigation without a policy is not a problem because a policy is only necessary for government agencies
Adam, a forensic investigator, is investigating an attack on Microsoft Exchange Server of a large organization. As the first step of the investigation, he examined the PRIV.EDB file and found the source from where the mail originated and the name of the file that disappeared upon execution. Now, he wants to examine the MIME stream content. Which of the following files is he going to examine?
A. PRIV.STM
B. gwcheck.db
C. PRIV.EDB
D. PUB.EDB
A cybercrime investigator is evaluating a data breach in a company's AWS infrastructure. The breached service was categorized as an AWS container service. What primary security aspects were likely managed by the company and not by AWS, which the investigator should first focus on?
A. Physical infrastructure and foundational services
B. Network configuration of the container services
C. Data management and firewall configuration
D. Application platform and Operating System (OS) security
A Computer Hacking Forensic Investigator is acquiring volatile data from a Linux-based suspect machine that they cannot physically access. They need to obtain a dump of the system's RAM remotely. Which of the following sequences of commands and tools should be utilized for a forensically sound extraction?
A. On the forensic workstation: insmod lime-.ko “path= format=lime”; on the suspect machine: nc : > filename.mem
B. On the suspect machine: insmod lime-.ko “path=tcp: format=lime”: on the forensics workstation: nc : > filename.mem
C. On the forensic workstation: nc -l > filename.dd; on the suspect machine: dd if=/dev/fmem bs=l024 | nc
D. On the suspect machine: dd if=/dev/fmem of= bs=lMB; on the forensic workstation: nc -l > filename.dd
Which of the following Windows event logs record events related to device drives and hardware changes?
A. Application log
B. Security log
C. Forwarded events log
D. System log
In a complex forensic investigation, a CHFI investigator has been given a 2 TB suspect drive from which they must acquire relevant data as quickly as possible. The investigator uses a verified and tested data acquisition tool to accomplish this task. Given that the suspect drive cannot be retained, and considering the mandatory requirements of the selected tool, which of the following steps is the most critical for the investigator to ensure a forensically sound acquisition?
A. Prioritizing and acquiring only those data that are of evidentiary value
B. Testing lossless compression by applying an MD5, SHA-2, or SHA-3 hash on a file before and after compression
C. Using Microsoft disk compressions tools like DriveSpace and DoubleSpace to exclude slack disk space between the files
D. Compress files by using archiving tools like PKZip, WinZip, and WinRAR
Preparing an image drive to copy files to is the first step in Linux forensics. For this purpose, what would the following command accomplish? dcfldd if=/dev/zero of=/dev/hda bs=4096 conv=noerror, sync
A. Fill the disk with zeros
B. Low-level format
C. Fill the disk with 4096 zeros
D. Copy files from the master disk to the slave disk on the secondary IDE controller
After passing her CEH exam, Carol wants to ensure that her network is completely secure. She implements a DMZ, stateful firewall, NAT, IPSEC, and a packet filtering firewall. Since all security measures were taken, none of the hosts on her network can reach the Internet. Why is that?
A. Stateful firewalls do not work with packet filtering firewalls
B. NAT does not work with stateful firewalls
C. IPSEC does not work with packet filtering firewalls
D. NAT does not work with IPSEC
Data is striped at a byte level across multiple drives, and parity information is distributed among all member drives.What RAID level is represented here?
A. RAID Level 0
B. RAID Level 5
C. RAID Level 3
D. RAID Level 1
Access Full 312-49V10 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 312-49V10 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 312-49V10 certification journey!