312-49V10 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 312-49V10 certification? Our 312-49V10 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 312-49V10 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 312-49V10 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which of the following is the most effective tool for acquiring volatile data from a Windows-based system?
A. Helix
B. Datagrab
C. Coreography
D. Ethereal
Harold wants to set up a firewall on his network but is not sure which one would be the most appropriate. He knows he needs to allow FTP traffic to one of the servers on his network, but he wants to only allow FTP-PUT. Which firewall would be most appropriate for Harold? needs?
A. Circuit-level proxy firewall
B. Packet filtering firewall
C. Application-level proxy firewall
D. Data link layer firewall
You are a security analyst performing a penetration tests for a company in the Midwest. After some initial reconnaissance, you discover the IP addresses of some Cisco routers used by the company. You type in the following URL that includes the IP address of one of the routers: http://172.168.4.131/level/99/exec/show/config After typing in this URL, you are presented with the entire configuration file for that router. What have you discovered?
A. HTTP Configuration Arbitrary Administrative Access Vulnerability
B. HTML Configuration Arbitrary Administrative Access Vulnerability
C. Cisco IOS Arbitrary Administrative Access Online Vulnerability
D. URL Obfuscation Arbitrary Administrative Access Vulnerability
In a recent cybercrime investigation, a forensic analyst found that the suspect had used anti-forensic techniques to complicate the investigation process. The criminal had been working to erase data, manipulate metadata, and employ encryption, which made the investigation significantly more complex. Which of the following scenarios would indicate that the suspect had overwritten data and metadata in an attempt to evade investigation?
A. The investigator detects that the suspect used VeraCrypt for full-volume encryption to protect critical files
B. AnalyzeMFT tool reveals inconsistencies between $STANDARD_INFORMATION and $FILE_NAME attributes in the NTFS file system
C. The investigator finds the disk has been completely formatted, wiping its address tables and unlinking all files in the file system
D. The investigator finds the majority of the hard drive’s sectors contain the null character, indicating usage of disk wiping utilities
You are working for a large clothing manufacturer as a computer forensics investigator and are called in to investigate an unusual case of an employee possibly stealing clothing designs from the company and selling them under a different brand name for a different company. What you discover during the course of the investigation is that the clothing designs are actually original products of the employee and the company has no policy against an employee selling his own designs on his own time. The only thing that you can find that the employee is doing wrong is that his clothing design incorporates the same graphic symbol as that of the company with only the wording in the graphic being different. What area of the law is the employee violating?
A. trademark law
B. copyright law
C. printright law
D. brandmark law
Which is a standard procedure to perform during all computer forensics investigations?
A. with the hard drive removed from the suspect PC, check the date and time in the system’s CMOS
B. with the hard drive in the suspect PC, check the date and time in the File Allocation Table
C. with the hard drive removed from the suspect PC, check the date and time in the system’s RAM
D. with the hard drive in the suspect PC, check the date and time in the system’s CMOS
Annie is searching for certain deleted files on a system running Windows XP OS. Where will she find the files if they were not completely deleted from the system?
A. C: $Recycled.Bin
B. C: $Recycle.Bin
C. C:RECYCLER
D. C:$RECYCLER
An organization has suffered a significant data breach and called in a Computer Hacking Forensics Investigator (CHFI) to gather evidence. The investigator has decided to use the dead acquisition technique to gather nonvolatile data from the compromised system. Which of the following would NOT typically be acquired during this type of forensic data acquisition process?
A. Web browser cache
B. Unallocated drive space
C. Active network connections
D. Boot sectors
Bob has encountered a system crash and has lost vital data stored on the hard drive of his Windows computer. He has no cloud storage or backup hard drives. he wants to recover all those data, which includes his personal photos, music, documents, videos, official email, etc. Which of the following tools shall resolve Bob's purpose?
A. Colasoft’s Capsa
B. Recuva
C. Cain & Abel
D. Xplico
In handling computer-related incidents, which IT role should be responsible for recovery, containment, and prevention to constituents?
A. Security Administrator
B. Network Administrator
C. Director of Information Technology
D. Director of Administration
Which of the following does Microsoft Exchange E-mail Server use for collaboration of various e-mail applications?
A. Simple Mail Transfer Protocol (SMTP)
B. Messaging Application Programming Interface (MAPI)
C. Internet Message Access Protocol (IMAP)
D. Post Office Protocol version 3 (POP3)
A picture file is recovered from a computer under investigation. During the investigation process, the file is enlarged 500% to get a better view of its contents. The picture quality is not degraded at all from this process. What kind of picture is this file?
A. Raster image
B. Vector image
C. Metafile image
D. Catalog image
Robert needs to copy an OS disk snapshot of a compromised VM to a storage account in different region for further investigation. Which of the following should he use in this scenario?
A. Azure Active Directory
B. Azure Portal
C. Azure CLI
D. Azure Monitor
What is the location of a Protective MBR in a GPT disk layout?
A. Logical Block Address (LBA) 2
B. Logical Block Address (LBA) 0
C. Logical Block Address (LBA) 1
D. Logical Block Address (LBA) 3
In Steganalysis, which of the following describes a Known-stego attack?
A. The hidden message and the corresponding stego-image are known
B. During the communication process, active attackers can change cover
C. Original and stego-object are available and the steganography algorithm is known
D. Only the steganography medium is available for analysis
A cybersecurity forensics investigator is tasked with acquiring data from a suspect's drive for a civil litigation case. The suspect drive is 1TB, and due to time constraints, the investigator decides to prioritize and acquire only data of evidentiary value. The original drive cannot be retained. In this context, which of the following steps should the investigator prioritize?
A. Opt for disk-to-image copying for the large suspect drive
B. Execute logical acquisition considering the one-time opportunity to capture data
C. Utilize DriveSpace or DoubleSpace to reduce the data size
D. Use a reliable data acquisition tool to make a copy of the original drive
When carrying out a forensics investigation, why should you never delete a partition on a dynamic disk?
A. All virtual memory will be deleted
B. The wrong partition may be set to active
C. This action can corrupt the disk
D. The computer will be set in a constant reboot state
A breach resulted from a malware attack that evaded detection and compromised the machine memory without installing any software or accessing the hard drive. What technique did the adversaries use to deliver the attack?
A. Trojan
B. JavaScript
C. Spyware
D. Fileless
What type of analysis helps to identify the time and sequence of events in an investigation?
A. Time-based
B. Functional
C. Relational
D. Temporal
In a computer forensics investigation, what describes the route that evidence takes from the time you find it until the case is closed or goes to court?
A. rules of evidence
B. law of probability
C. chain of custody
D. policy of separation
Jason has set up a honeypot environment by creating a DMZ that has no physical or logical access to his production network. In this honeypot, he has placed a server running Windows Active Directory. He has also placed a Web server in the DMZ that services a number of web pages that offer visitors a chance to download sensitive information by clicking on a button. A week later, Jason finds in his network logs how an intruder accessed the honeypot and downloaded sensitive information. Jason uses the logs to try and prosecute the intruder for stealing sensitive corporate information. Why will this not be viable?
A. Entrapment
B. Enticement
C. Intruding into a honeypot is not illegal
D. Intruding into a DMZ is not illegal
Given the drive dimensions as follows and assuming a sector has 512 bytes, what is the capacity of the described hard drive? 22,164 cylinders/disk 80 heads/cylinder 63 sectors/track
A. 53.26 GB
B. 57.19 GB
C. 11.17 GB
D. 10 GB
What will the following Linux command accomplish? dd if=/dev/mem of=/home/sam/mem.bin bs=1024
A. Copy the master boot record to a file
B. Copy the contents of the system folder to a file
C. Copy the running memory to a file
D. Copy the memory dump file to an image file
When reviewing web logs, you see an entry for resource not found in the HTTP status code field. What is the actual error code that you would see in the log for resource not found?
A. 202
B. 404
C. 606
D. 999
"To ensure that the digital evidence is collected, preserved, examined, or transferred in a manner safeguarding the accuracy and reliability of the evidence, law enforcement, and forensics organizations must establish and maintain an effective quality system" is a principle established by:
A. SWGDE
B. EC-Council
C. NIST
D. NCIS
What is the following command trying to accomplish? C:> nmap `"sU `"p445 192.168.0.0/24
A. Verify that UDP port 445 is open for the 192.168.0.0 network
B. Verify that TCP port 445 is open for the 192.168.0.0 network
C. Verify that NETBIOS is running for the 192.168.0.0 network
D. Verify that UDP port 445 is closed for the 192.168.0.0 network
An investigator is searching through the firewall logs of a company and notices ICMP packets that are larger than 65,536 bytes. What type of activity is the investigator seeing?
A. Smurf
B. Ping of death
C. Fraggle
D. Nmap scan
A sophisticated cyber-attack has targeted an organization, and the forensic team is called upon for incident response. Their assets are largely hosted on AWS, particularly using S3 and EC2 instances. As a forensic investigator, your first step to retaining valuable evidence in the EC2 instances is:
A. Retrieve and analyze log data from the affected EC2 instances
B. Encrypt all the data present in the EC2 instances to avoid further unauthorized access
C. Immediately isolate the affected EC2 instances from the network to avoid data corruption
D. Create a snapshot of the EBS volume in the affected EC2 instance and share it with the forensic team for analysis
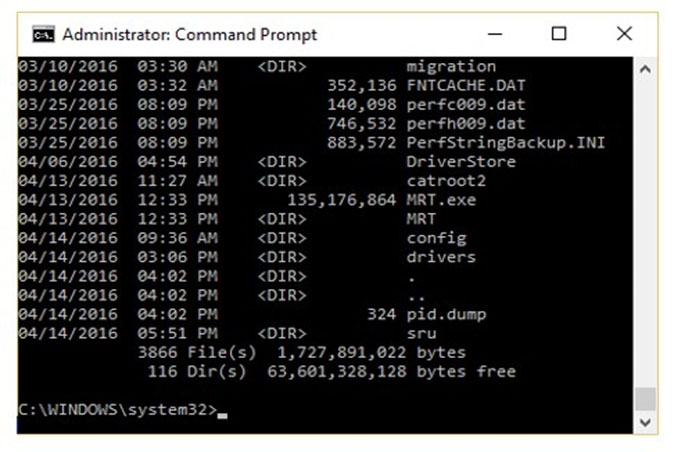
The given image displays information about date and time of installation of the OS along with service packs, patches, and sub-directories. What command or tool did the investigator use to view this output?
A. dir /o:d
B. dir /o:s
C. dir /o:e
D. dir /o:n
What file is processed at the end of a Windows XP boot to initialize the logon dialog box?
A. NTOSKRNL.EXE
B. NTLDR
C. LSASS.EXE
D. NTDETECT.COM
A cybersecurity investigator is working on a case involving a malicious executable suspected of being packed using a popular program packer. The investigator realizes that the packer used is password-protected. In such a scenario, what should be the investigator's first course of action to analyze the packed file?
A. Mount compound files
B. Perform static analysis on the packed file
C. Decrypt the password to unpack the file
D. Run the packed file in a controlled environment for dynamic analysis
During an incident response to a data breach in a company's AWS environment, a forensic investigator is tasked to analyze and extract data from different storage types for further examination. What would be the most appropriate and effective course of action given that Amazon S3, EBS, and EFS were used?
A. Implement ACL permissions for S3 buckets, and attach the affected EFS to a Linux instance for data extraction
B. Create IAM policies to restrict access, and proceed with data extraction from EBS and EFS storage types
C. Extract all data directly from Amazon S3 and EBS, and attach the EFS to a Linux instance for data extraction
D. Snapshot the affected EBS volumes and S3 buckets, and mount EFS to a Linux instance for analysis
A forensic investigator is examining a potential intrusion involving an Amazon Echo. The investigator has acquired an affected Echo and the smartphone synced to it. For further data analysis, he needs to retrieve relevant database files from the smartphone. Which files will the investigator primarily focus on to retrieve essential information?
A. /data/data/com.amazon.dee.app/databases/map_data_storage_v2.db and/data/data/com.amazon.dee.app/databases/DataStore.db
B. /data/data/com.amazon.dee.app/databases/DataStore.db and/data/data/com.amazon.dee.app/databases/map_data_storage_v3.db
C. /data/data/com.amazon.dee.app/databases/map_data_storage_v1.db and/data/data/com.amazon.dee.app/databases/DataStore.db
D. /data/data/com.amazon.dee.app/databases/map_data_storage_v2.db and/data/data/com.amazon.dee.app/databases/DeviceInfo.db
If you are concerned about a high level of compression but not concerned about any possible data loss, what type of compression would you use?
A. Lossful compression
B. Lossy compression
C. Lossless compression
D. Time-loss compression
The Apache server saves diagnostic information and error messages that it encounters while processing requests. The default path of this file is usr/local/apache/ logs/error.log in Linux. Identify the Apache error log from the following logs.
A. http://victim.com/scripts/..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..%c0%af../..% c0%af../..%c0%af../winnt/system32/cmd.exe?/c+dir+C:Winnt system32LogfilesW3SVC1
B. [Wed Oct 11 14:32:52 2000] [error] [client 127.0.0.1] client denied by server configuration: /export/home/live/ap/htdocs/test
C. 127.0.0.1 – frank [10/Oct/2000:13:55:36 -0700]”GET /apache_pb.gif HTTP/1.0″ 200 2326
D. 127.0.0.1 – – [10/Apr/2007:10:39:11 +0300] ] [error] “GET /apache_pb.gif HTTP/1.0” 200 2326
Raw data acquisition format creates _________ of a data set or suspect drive.
A. Segmented image files
B. Simple sequential flat files
C. Compressed image files
D. Segmented files
In a complex forensic investigation, a CHFI investigator has been given a 2 TB suspect drive from which they must acquire relevant data as quickly as possible. The investigator uses a verified and tested data acquisition tool to accomplish this task. Given that the suspect drive cannot be retained, and considering the mandatory requirements of the selected tool, which of the following steps is the most critical for the investigator to ensure a forensically sound acquisition?
A. Prioritizing and acquiring only those data that are of evidentiary value
B. Testing lossless compression by applying an MD5, SHA-2, or SHA-3 hash on a file before and after compression
C. Using Microsoft disk compressions tools like DriveSpace and DoubleSpace to exclude slack disk space between the files
D. Compress files by using archiving tools like PKZip, WinZip, and WinRAR
Centralized binary logging is a process in which many websites write binary and unformatted log data to a single log file. What extension should the investigator look to find its log file?
A. .cbl
B. .log
C. .ibl
D. .txt
Select the data that a virtual memory would store in a Windows-based system.
A. Information or metadata of the files
B. Documents and other files
C. Application data
D. Running processes
In which implementation of RAID will the image of a Hardware RAID volume be different from the image taken separately from the disks?
A. RAID 1
B. The images will always be identical because data is mirrored for redundancy
C. RAID 0
D. It will always be different
A CHFI has been asked to recover browser history from a seized Microsoft Edge browser on a Windows system. This is important to pinpoint the suspect's online activities. The suspect was known to clear their browser history frequently. Which tool and path would most efficiently recover the required data?
A. MZCacheView tool; Path: C:UsersWAppDataLocalMozillaFirefoxProfilesXXXXXXXX.defaultcache2
B. MZHistoryView tool; Path:C:UsersWAppDataRoamingMozillaFirefoxProfilesXXXXXXXX.defaultplaces.sqlite
C. Browsing HistoryView tool; Path: C:UsersAdminAppDataLocalMicrosoftWindowsHistory
D. Browsing HistoryView tool; Path: C:UsersAdminAppDataLocalMicrosoftWindowsWebCache
An investigator needs to perform data acquisition from a storage media without altering its contents to maintain the integrity of the content. The approach adopted by the investigator relies upon the capacity of enabling read-only access to the storage media. Which tool should the investigator integrate into his/her procedures to accomplish this task?
A. Data duplication tool
B. BitLocker
C. Write blocker
D. Backup tool
What are the security risks of running a "repair" installation for Windows XP?
A. Pressing Shift+F10gives the user administrative rights
B. Pressing Shift+F1gives the user administrative rights
C. Pressing Ctrl+F10 gives the user administrative rights
D. There are no security risks when running the “repair” installation for Windows XP
You are a Computer Hacking Forensic Investigator working on a high-profile case involving an Android device. You discovered an SQLite database during your investigation. However, this database has an unusual extension type and does not display content using your current tools. You recall that you have the following tools at your disposal: Oxygen Forensics SQLite Viewer, DB Browser for SQLite, X-plore, SQLitePlus Database Explorer, and SQLite Viewer. Given that this particular SQLite database may contain important evidence, what should be your approach?
A. Switch between all the available tools until you find one that works with the unknown database extension
B. Use X-plore, as it offers root access which can provide access to the database
C. Stick to using Oxygen Forensics SQLite Viewer, which can analyze actual and deleted data
D. Use the SQLite “.dump” command to extract the data into a readable format
Data density of a disk drive is calculated by using _________.
A. Track density, areal density, and bit density.
B. Track space, bit area, and slack space.
C. Slack space, bit density, and slack density.
D. Track density, areal density, and slack density.
What is the smallest physical storage unit on a hard drive?
A. Track
B. Cluster
C. Sector
D. Platter
You have completed a forensic investigation case. You would like to destroy the data contained in various disks at the forensics lab due to sensitivity of the case. How would you permanently erase the data on the hard disk?
A. Throw the hard disk into the fire
B. Run the powerful magnets over the hard disk
C. Format the hard disk multiple times using a low level disk utility
D. Overwrite the contents of the hard disk with Junk data
Which response organization tracks hoaxes as well as viruses?
A. NIPC
B. FEDCIRC
C. CERT
D. CIAC
You are running known exploits against your network to test for possible vulnerabilities. To test the strength of your virus software, you load a test network to mimic your production network. Your software successfully blocks some simple macro and encrypted viruses. You decide to really test the software by using virus code where the code rewrites itself entirely and the signatures change from child to child, but the functionality stays the same. What type of virus is this that you are testing?
A. Polymorphic
B. Metamorphic
C. Oligomorhic
D. Transmorphic
You are a forensic investigator who is analyzing a hard drive that was recently collected as evidence. You have been unsuccessful at locating any meaningful evidence within the file system and suspect a drive wiping utility may have been used. You have reviewed the keys within the software hive of the Windows registry and did not find any drive wiping utilities. How can you verify that drive wiping software was used on the hard drive?
A. Check the list of installed programs
B. Look for distinct repeating patterns on the hard drive at the bit level
C. Document in your report that you suspect a drive wiping utility was used, but no evidence was found
D. Load various drive wiping utilities offline, and export previous run reports
Access Full 312-49V10 Dump Free
Looking for even more practice questions? Click here to access the complete 312-49V10 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 312-49V10 dump free questions — and get one step closer to exam success!