312-38 Practice Questions Free – 50 Exam-Style Questions to Sharpen Your Skills
Are you preparing for the 312-38 certification exam? Kickstart your success with our 312-38 Practice Questions Free – a carefully selected set of 50 real exam-style questions to help you test your knowledge and identify areas for improvement.
Practicing with 312-38 practice questions free gives you a powerful edge by allowing you to:
- Understand the exam structure and question formats
- Discover your strong and weak areas
- Build the confidence you need for test day success
Below, you will find 50 free 312-38 practice questions designed to match the real exam in both difficulty and topic coverage. They’re ideal for self-assessment or final review. You can click on each Question to explore the details.
Which of the following helps prevent executing untrusted or untested programs or code from untrusted or unverified third-parties?
A. Application sandboxing
B. Deployment of WAFS
C. Application whitelisting
D. Application blacklisting
Katie has implemented the RAID level that splits data into blocks and evenly writes the data to multiple hard drives but does not provide data redundancy. This type of RAID level requires a minimum of __________ in order to setup.
A. Two drives
B. Three drives
C. Six drives
D. Four drives
If an organization has decided to consume PaaS Cloud service model, then identify the organization's responsibility that they need to look after based on shared responsibility model.
A. Data, interfaces, application, etc.
B. Data, interfaces, application, middleware, OS, VM, virtual network, etc.
C. Data, interfaces, application, middleware, OS, VM, virtual network, hypervisors, processing and memory, data storage, network interfaces, facilities and data centers, etc.
D. Data, interfaces, etc.
Which of the following connects the SDN controller and SDN networking devices and relays information from network services to network devices such as switches and routers?
A. Southbound API
B. Eastbound API
C. Westbound API
D. Northbound API
How is an “attack” represented?
A. Motive (goal) + method
B. Motive (goal) + method + vulnerability
C. Asset + Threat + Vulnerability
D. Asset + Threat
Which of the following protocols is used for inter-domain multicast routing?
A. BGP
B. RPC
C. VoIP
D. RADIUS
Which of the following layers of the OSI model provides physical addressing?
A. Application layer
B. Network layer
C. Physical layer
D. Data link layer
Which of the following systems includes an independent NAS Head and multiple storage arrays?
A. FreeNAS
B. None of these
C. Gateway NAS System
D. Integrated NAS System
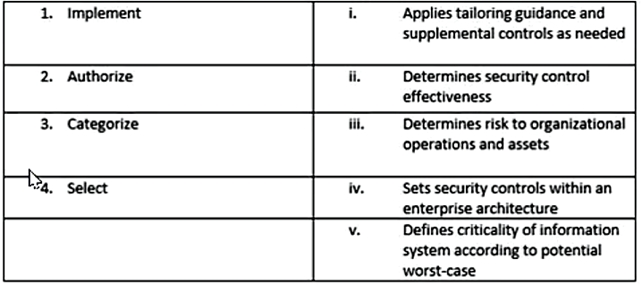
Match the following NIST security life cycle components with their activities:
A. 1-iv, 2- iii,3-v,4-i
B. 1-ii,2-i,3-v,4-iv
C. 1-i,2-v,3-iii,4-ii
D. 1-iii,2-iv,3-v,4-i
Which of the following intrusion detection techniques observes the network for abnormal usage patterns by determining the performance parameters for regular activities and monitoring for actions beyond the normal parameters?
A. Statistical anomaly detection
B. Signature/Pattern matching
C. None of these
D. Stateful protocol analysis
Which of the following incident handling stage removes the root cause of the incident?
A. Eradication
B. Recovery
C. Detection
D. Containment
Which of the following TCP/IP state transitions represents no connection state at all?
A. Closed
B. Closing
C. Close-wait
D. Fin-wait-1
Which among the following filter is used to detect a SYN/FIN attack?
A. tcp.flags==0x002
B. tcp.flags==0x004
C. tcp.flags==0x003
D. tcp.flags==0x001
Which of the following statements are true about a wireless network? Each correct answer represents a complete solution. Choose all that apply.
A. Data can be shared easily between wireless devices.
B. It provides mobility to users to access a network.
C. Data can be transmitted in different ways by using Cellular Networks, Mobitex, DataTAC, etc.
D. It is easy to connect.
Which of the following firewalls are used to monitor the status of active connections, and configure the network packets to pass through the firewall? Each correct answer represents a complete solution. Choose all that apply.
A. Farm owner
B. Proxy server
C. Dynamic packet filtering
D. The circuit gateway
Sam wants to implement a network-based IDS and finalizes an IDS solution that works based on pattern matching. Which type of network-based IDS is Sam implementing?
A. Behavior-based IDS
B. Anomaly-based IDS
C. Signature-based IDS
D. Stateful protocol analysis
Which of the following is a free security-auditing tool for Linux?
A. SAINT
B. SATAN
C. Nessus
D. HPing
Which of the following is a presentation layer protocol?
A. TCP
B. RPC
C. BGP
D. LWAPP
Which of the following helps in viewing account activity and events for supported services made by AWS?
A. AWS CloudFormation
B. AWS Certificate Manager
C. AWS CloudHSM
D. AWS CloudTrial
Assume that you are a network administrator and the company has asked you to draft an Acceptable Use Policy (AUP) for employees. Under which category of an information security policy does AUP fall into?
A. Incident Response Policy (IRP)
B. Issue Specific Security Policy (ISSP)
C. Enterprise Information Security Policy (EISP)
D. System Specific Security Policy (SSSP)
In which of the following conditions does the system enter ROM monitor mode? Each correct answer represents a complete solution. Choose all that apply.
A. The router does not have a configuration file.
B. There is a need to set operating parameters.
C. The user interrupts the boot sequence.
D. The router does not find a valid operating system image.
The CEO of Max Rager wants to send a confidential message regarding the new formula for its coveted soft drink, SuperMax, to its manufacturer in Texas. However, he fears the message could be altered in transit. How can he prevent this incident from happening and what element of the message ensures the success of this method?
A. Hashing; hash code
B. Symmetric encryption; secret key
C. Hashing; public key
D. Asymmetric encryption; public key
Ross manages 30 employees and only 25 computers in the organization. The network the company uses is a peer-to-peer. Ross configures access control measures allowing the employees to set their own control measures for their files and folders. Which access control did Ross implement?
A. Mandatory access control
B. Non-discretionary access control
C. Discretionary access control
D. Role-based access control
Docker provides Platform-as-a-Service (PaaS) through ________ and delivers containerized software packages.
A. Server-level virtualization
B. Network-level virtualization
C. OS-level virtualization
D. Storage-level virtualization
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep attack. Which of the following Wireshark filters will he use?
A. Icmp.type==8 or icmp.type==16
B. icmp.type==8 or icmp.type==0
C. icmp.type==8 and icmp.type==0
D. Icmp.type==0 and icmp.type==16
Identify the virtualization level that creates a massive pool of storage areas for different virtual machines running on the hardware.
A. Fabric virtualization
B. Storage device virtualization
C. Server virtualization
D. File system virtualization
Which of the following creates passwords for individual administrator accounts and stores them in Windows AD?
A. LSASS
B. SRM
C. SAM
D. LAPS
Which Event Correlation Approach checks and compares all the fields systematically and intentionally for positive and negative correlation with each other to determine the correlation across one or multiple fields?
A. Rule-Based Approach
B. Graph-Based Approach
C. Field-Based Approach
D. Automated Field Correlation
Which of the following is not part of the recommended first response steps for network defenders?
A. Restrict yourself from doing the investigation
B. Extract relevant data from the suspected devices as early as possible
C. Disable virus protection
D. Do not change the state of the suspected device
Justine has been tasked by her supervisor to ensure that the company's physical security is on the same level as their logical security measures. She installs video cameras at all entrances and exits and installs badge access points for all doors. The last item she wants to install is a method to prevent unauthorized people piggybacking employees. What should she install to prevent piggybacking?
A. Justine needs to install a biometrics station at each entrance.
B. She should install a mantrap.
C. She should install a Thompson Trapdoor.
D. Justine will need to install a revolving security door.
Which of the following interfaces uses hot plugging technique to replace computer components without the need to shut down the system?
A. SATA
B. SCSI
C. IDE
D. SDRAM
Which of the following refers to a potential occurrence of an undesired event that can eventually damage and interrupt the operational and functional activities of an organization?
A. Attack
B. Risk
C. Threat
D. Vulnerability
Maximus Tech is a multinational company that uses Cisco ASA Firewalls for their systems. Jason is the one of the members of the team that checks the logs at Maximus Tech. As a part of his job, he is going through the logs and he came across a firewall log that looks like this: May 06 2018 21:27:27 asa 1: % ASA -5 – 11008: User ‘enable_15’ executed the ‘configure term’ command Based on the security level mentioned in the log, what did Jason understand about the description of this message?
A. Warning condition message
B. Critical condition message
C. Normal but significant message
D. Informational message
Individuals in the organization using system resources in a way that violates acceptable usage policies indicates which of the following security incident(s):
A. Unauthorized Access
B. Improper Usage
C. Denial-of-Service (DoS)
D. Malicious Code
Simran is a network administrator at a start-up called Revolution. To ensure that neither party in the company can deny getting email notifications or any other communication, she mandates authentication before a connection establishment or message transfer occurs. What fundamental attribute of network defense is she enforcing?
A. Integrity
B. Non-repudiation
C. Confidentiality
D. Authentication
Which of the following can be used to disallow a system/user from accessing all applications except a specific folder on a system?
A. Hash rule
B. Path rule
C. Internet zone rule
D. Certificate rule
Which type of modulation technique is used in local area wireless networks (LAWNs)?
A. FHSS
B. DSSS
C. MIMO-OFDM
D. OFDM
You just set up a wireless network to customers in the cafe. Which of the following are good security measures implemented? Each correct answer represents a complete solution. Choose all that apply.
A. WEP encryption
B. WPA encryption
C. Not broadcasting the SSID
D. The MAC-filtering router
Which of the following steps OPSEC process examines every aspect of the proposed operation to identify the OPSEC indicators that can reveal important information and then compare them with indicators of the opponent's intelligence collection capabilities identified in the previous activity?
A. Identification of Critical Information
B. analysis weakness
C. risk assessment
D. Appropriate OPSEC measures
E. analysis of threats
Which of the following IP class addresses are not allotted to hosts? Each correct answer represents a complete solution. Choose all that apply.
A. Class C
B. Class D
C. Class A
D. Class B
E. Class E
Which of the following statements are true about an IPv6 network? Each correct answer represents a complete solution. Choose all that apply.
A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresses.
B. It increases the number of available IP addresses.
C. It uses longer subnet masks than those used in IPv4.
D. It provides improved authentication and security.
E. It uses 128-bit addresses.
Which of the following is a mechanism that helps to ensure that only the intended and authorized recipients are able to read the data?
A. access to information
B. none
C. integrity
D. authentication
E. confidence
Which BC/DR activity includes action taken toward resuming all services that are dependent on business-critical applications?
A. Response
B. Recovery
C. Resumption
D. Restoration
Which of the following IP addresses is not reserved for the hosts? Each correct answer represents a complete solution. Choose all that apply.
A. E-Class
B. class D
C. class A
D. B-
Which of the following types of RAID offers no protection for the parity disk?
A. RAID 2
B. RAID 1
C. RAID 5
D. RAID 3
Which of the following is an example of MAC model?
A. Chinese Waterfall model
B. Clark-Beason integrity model
C. Access control matrix model
D. Bell-LaPadula model
Which of the following is a distance vector routing protocols? Each correct answer represents a complete solution. Choose all that apply.
A. OSPF
B. IGRP
C. IS-IS
D. REST IN PEACE
Heather has been tasked with setting up and implementing VPN tunnels to remote offices. She will most likely be implementing IPsec VPN tunnels to connect the offices. At what layer of the OSI model does an IPsec tunnel function on?
A. They function on the data link layer.
B. They work on the network layer.
C. They function on either the application or the physical layer.
D. They work on the session layer.
How many layers are present in the OSI layer model?
A. 5
B. 4
C. 7
D. 9
Management wants to bring their organization into compliance with the ISO standard for information security risk management. Which ISO standard will management decide to implement?
A. ISO/IEC 27005
B. ISO/IEC 27006
C. ISO/IEC 27002
D. ISO/IEC 27004
Free Access Full 312-38 Practice Questions Free
Want more hands-on practice? Click here to access the full bank of 312-38 practice questions free and reinforce your understanding of all exam objectives.
We update our question sets regularly, so check back often for new and relevant content.
Good luck with your 312-38 certification journey!