312-38 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 312-38 certification exam? Start your preparation the smart way with our 312-38 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 312-38 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 312-38 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which of the following protocols is used for inter-domain multicast routing?
A. BGP
B. RPC
C. VoIP
D. RADIUS
Which of the following steps OPSEC process examines every aspect of the proposed operation to identify the OPSEC indicators that can reveal important information and then compare them with indicators of the opponent's intelligence collection capabilities identified in the previous activity?
A. Identification of Critical Information
B. analysis weakness
C. risk assessment
D. Appropriate OPSEC measures
E. analysis of threats
Which of the following can be used to disallow a system/user from accessing all applications except a specific folder on a system?
A. Hash rule
B. Path rule
C. Internet zone rule
D. Certificate rule
A newly joined network administrator wants to assess the organization against possible risk. He notices the organization doesn't have a __________ identified which helps measure how risky an activity is.
A. Risk Severity
B. Risk Matrix
C. Risk levels
D. Key Risk Indicator
Which of the following representatives of the incident response team takes forensic backups of systems that are the focus of an incident?
A. Technical representative
B. Lead investigator
C. Information security representative
D. Legal representative
Chris is a senior network administrator. Chris wants to measure the Key Risk Indicator (KRI) to assess the organization. Why is Chris calculating the KRI for his organization? It helps Chris to:
A. Identifies adverse events
B. Facilitates backward viewing
C. Notifies when risk has reached threshold levels
D. Facilitates post incident management
Which phase of incident response process involves collection of incident evidence and sending them to forensic department for further investigation?
A. Incident containment
B. Incident recording and assignment
C. Eradication
D. Preparation for incident response
Which of the following statement holds true in terms of containers?
A. Container requires more memory space
B. Each container runs in its own OS
C. Container is fully isolated; hence, more secure
D. Process-level isolation happens; a container in hence less secure
Which of the following is a term to describe the use of inert gases and chemical agents to extinguish a fire?
A. Gaseous fire suppression
B. Fire alarm system
C. Fire sprinkler
D. Fire suppression system
John, the network administrator and he wants to enable the NetFlow feature in Cisco routers to collect and monitor the IP network traffic passing through the router. Which command will John use to enable NetFlow on an interface?
A. Router IP route
B. Router(Config-if) # IP route cache flow
C. Router# Netmon enable
D. Router# netflow enable
Which among the following is used by anti-malware systems and threat intelligence platforms to spot and stop malicious activities at an initial stage?
A. Indicators of attack
B. Key risk indicators
C. Indicators of compromise
D. Indicators of exposure
Which of the following IEEE standards provides specifications for wireless ATM systems?
A. 802.1
B. 802.5
C. 802.3
D. 802.11a
Which of the following connects the SDN controller and SDN networking devices and relays information from network services to network devices such as switches and routers?
A. Southbound API
B. Eastbound API
C. Westbound API
D. Northbound API
Steven's company has recently grown from 5 employees to over 50. Every workstation has a public IP address and navigated to the Internet with little to no protection. Steven wants to use a firewall. He also wants IP addresses to be private addresses, to prevent public Internet devices direct access to them. What should Steven implement on the firewall to ensure this happens?
A. Steven should use Open Shortest Path First (OSPF).
B. Steven should enable Network Address Translation (NAT).
C. Steven should use a Demilitarized Zone (DMZ).
D. Steven should use IPsec.
The Circuit-level gateway firewall technology functions at which of the following OSI layer?
A. Transport layer
B. Data-link layer
C. Session layer
D. Network layer
Management wants to bring their organization into compliance with the ISO standard for information security risk management. Which ISO standard will management decide to implement?
A. ISO/IEC 27005
B. ISO/IEC 27006
C. ISO/IEC 27002
D. ISO/IEC 27004
Which of the following intrusion detection techniques observes the network for abnormal usage patterns by determining the performance parameters for regular activities and monitoring for actions beyond the normal parameters?
A. Statistical anomaly detection
B. Signature/Pattern matching
C. None of these
D. Stateful protocol analysis
Which of the following interfaces uses hot plugging technique to replace computer components without the need to shut down the system?
A. SATA
B. SCSI
C. IDE
D. SDRAM
Andrew would like to configure IPsec in a manner that provides confidentiality for the content of packets. What component of IPsec provides this capability?
A. IKE
B. ESP
C. AH
D. ISAKMP
Which type of modulation technique is used in local area wireless networks (LAWNs)?
A. FHSS
B. DSSS
C. MIMO-OFDM
D. OFDM
Cindy is the network security administrator for her company. She just got back from a security conference in Las Vegas where they talked about all kinds of old and new security threats; many of which she did not know of. She is worried about the current security state of her company's network so she decides to start scanning the network from an external IP address. To see how some of the hosts on her network react, she sends out SYN packets to an IP range. A number of IPs respond with a SYN/ACK response. Before the connection is established, she sends RST packets to those hosts to stop the session. She has done this to see how her intrusion detection system will log the traffic. What type of scan is Cindy attempting here?
A. The type of scan she is using is called a NULL scan.
B. Cindy is attempting to find live hosts on her company’s network by using a XMAS scan.
C. Cindy is using a half-open scan to find live hosts on her network.
D. She is utilizing a RST scan to find live hosts that are listening on her network.
Which of the following is NOT an AWS Shared Responsibility Model devised by AWS?
A. Shared Responsibility Model for Container Services
B. Shared Responsibility Model for Infrastructure Services
C. Shared Responsibility Model for Abstract Services
D. Shared Responsibility Model for Storage Services
Which of the following is not part of the recommended first response steps for network defenders?
A. Restrict yourself from doing the investigation
B. Extract relevant data from the suspected devices as early as possible
C. Disable virus protection
D. Do not change the state of the suspected device
Michelle is a network security administrator working at a multinational company. She wants to provide secure access to corporate data (documents, spreadsheets, email, schedules, presentations, and other enterprise data) on mobile devices across organizations networks without being slowed down and also wants to enable easy and secure sharing of information between devices within an enterprise. Based on the above-mentioned requirements, which among the following solution should Michelle implement?
A. MDM
B. MAM
C. MCM
D. MEM
Byron, a new network administrator at FBI, would like to ensure that Windows PCs there are up-to-date and have less internal security flaws. What can he do?
A. Centrally assign Windows PC group policies
B. Dedicate a partition on HDD and format the disk using NTFS
C. Download and install latest patches and enable Windows Automatic Updates
D. Install antivirus software and turn off unnecessary services
Sam wants to implement a network-based IDS and finalizes an IDS solution that works based on pattern matching. Which type of network-based IDS is Sam implementing?
A. Behavior-based IDS
B. Anomaly-based IDS
C. Signature-based IDS
D. Stateful protocol analysis
Ryan works as a network security engineer at an organization the recently suffered an attack. As a countermeasure, Ryan would like to obtain more information about the attacker and chooses to deploy a honeypot into the organizations production environment called Kojoney. Using this honeypot, he would like to emulate the network vulnerability that was attacked previously. Which type of honeypot is he trying to implement?
A. High interaction honeypots
B. Research honeypot
C. Low interaction honeypots
D. Pure honeypots
You have just set up a wireless network for customers at a coffee shop. Which of the following are good security measures to implement? Each correct answer represents a complete solution. (Choose two.)
A. Using WPA encryption
B. Not broadcasting SSID
C. Using WEP encryption
D. MAC filtering the router
Which protocol could choose the network administrator for the wireless network design, if he need to satisfied the minimum requirement of 2.4 GHz, 22 MHz of bandwidth, 2 Mbits/s stream for data rate and use DSSS for modulation.
A. 802.11n
B. 802.11g
C. 802.11b
D. 802.11a
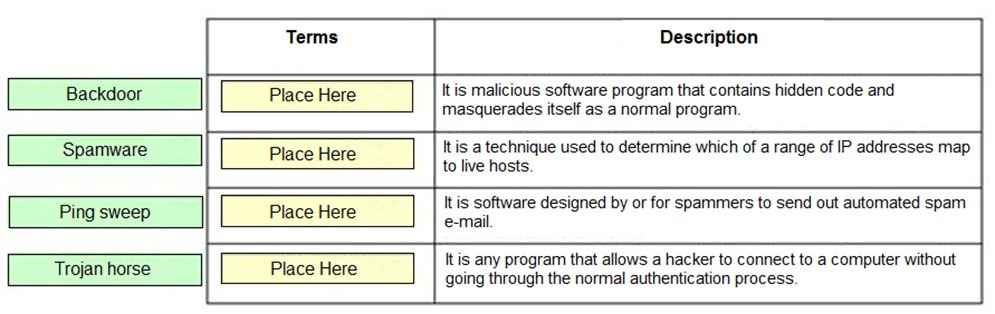
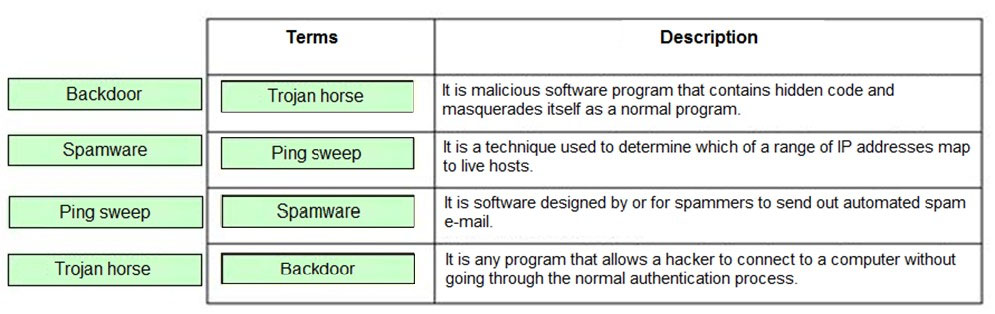
DRAG DROP - Drag and drop the terms to match with their descriptions. Select and Place:
Ross manages 30 employees and only 25 computers in the organization. The network the company uses is a peer-to-peer. Ross configures access control measures allowing the employees to set their own control measures for their files and folders. Which access control did Ross implement?
A. Mandatory access control
B. Non-discretionary access control
C. Discretionary access control
D. Role-based access control
How is an “attack” represented?
A. Motive (goal) + method
B. Motive (goal) + method + vulnerability
C. Asset + Threat + Vulnerability
D. Asset + Threat
Which of the following TCP/IP state transitions represents no connection state at all?
A. Closed
B. Closing
C. Close-wait
D. Fin-wait-1
If an organization has decided to consume PaaS Cloud service model, then identify the organization's responsibility that they need to look after based on shared responsibility model.
A. Data, interfaces, application, etc.
B. Data, interfaces, application, middleware, OS, VM, virtual network, etc.
C. Data, interfaces, application, middleware, OS, VM, virtual network, hypervisors, processing and memory, data storage, network interfaces, facilities and data centers, etc.
D. Data, interfaces, etc.
Which among the following tools can help in identifying IoEs to evaluate human attack surface?
A. securiCAD
B. Amass
C. Skybox
D. SET
Which of the following is a centralized collection of honeypots and analysis tools?
A. Production honeypot
B. Honeynet
C. Research honeypot
D. Honeyfarm
Which of the following is a process of transformation where the old system can no longer be maintained?
A. Disaster
B. Risk
C. Threat
D. Crisis
Docker provides Platform-as-a-Service (PaaS) through ________ and delivers containerized software packages.
A. Server-level virtualization
B. Network-level virtualization
C. OS-level virtualization
D. Storage-level virtualization
Management asked their network administrator to suggest an appropriate backup medium for their backup plan that best suits their organization's need. Which of the following factors will the administrator consider when deciding on the appropriate backup medium? (Choose all that apply.)
A. Reliability
B. Capability
C. Accountability
D. Extensibility
Which BC/DR activity works on the assumption that the most critical processes are brought back from a remote location first, followed by the less critical functions?
A. Recovery
B. Restoration
C. Response
D. Resumption
Adam works as a Professional Penetration Tester. A project has been assigned to him to test the vulnerabilities of the CISCO Router of Umbrella Inc. Adam finds out that HTTP Configuration Arbitrary Administrative Access Vulnerability exists in the router. By applying different password cracking tools, Adam gains access to the router. He analyzes the router config file and notices the following lines: logging buffered errors logging history critical logging trap warnings logging 10.0.1.103 By analyzing the above lines, Adam concludes that this router is logging at log level 4 to the syslog server 10.0.1.103. He decides to change the log level from 4 to 0. Which of the following is the most likely reason of changing the log level?
A. Changing the log level from 4 to 0 will result in the logging of only emergencies. This way the modification in the router is not sent to the syslog server.
B. By changing the log level, Adam can easily perform a SQL injection attack.
C. Changing the log level grants access to the router as an Administrator.
D. Changing the log level from 4 to 0 will result in the termination of logging. This way the modification in the router is not sent to the syslog server.
Justine has been tasked by her supervisor to ensure that the company's physical security is on the same level as their logical security measures. She installs video cameras at all entrances and exits and installs badge access points for all doors. The last item she wants to install is a method to prevent unauthorized people piggybacking employees. What should she install to prevent piggybacking?
A. Justine needs to install a biometrics station at each entrance.
B. She should install a mantrap.
C. She should install a Thompson Trapdoor.
D. Justine will need to install a revolving security door.
Which of the following is a Cisco product that performs VPN and firewall functions?
A. Circuit-Level Gateway
B. PIX Firewall
C. IP Packet Filtering Firewall
D. Application Level Firewall
Which of the following types of RAID offers no protection for the parity disk?
A. RAID 2
B. RAID 1
C. RAID 5
D. RAID 3
Which of the following helps in viewing account activity and events for supported services made by AWS?
A. AWS CloudFormation
B. AWS Certificate Manager
C. AWS CloudHSM
D. AWS CloudTrial
In ______ method, event logs are arranged in the form of a circular buffer.
A. Non-wrapping method
B. LIFO method
C. Wrapping method
D. FIFO method
To provide optimum security while enabling safe/necessary services, blocking known dangerous services, and making employees accountable for their online activity, what Internet Access policy would Brian, the network administrator, have to choose?
A. Prudent policy
B. Paranoid policy
C. Promiscuous policy
D. Permissive policy
Which type of firewall consists of three interfaces and allows further subdivision of the systems based on specific security objectives of the organization?
A. Screened subnet
B. Bastion host
C. Unscreened subnet
D. Multi-homed firewall
Which of the following layers provides communication session management between host computers?
A. Application layer
B. Internet layer
C. Transport layer
D. Link layer
John works as a C programmer. He develops the following C program:His program is vulnerable to a __________ attack.
A. SQL injection
B. Denial-of-Service
C. Buffer overflow
D. Cross site scripting
Access Full 312-38 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 312-38 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 312-38 mock test free today—and take a major step toward exam success!