312-38 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 312-38 certification? Our 312-38 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 312-38 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 312-38 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
To provide optimum security while enabling safe/necessary services, blocking known dangerous services, and making employees accountable for their online activity, what Internet Access policy would Brian, the network administrator, have to choose?
A. Prudent policy
B. Paranoid policy
C. Promiscuous policy
D. Permissive policy
Which of the following is a free security-auditing tool for Linux?
A. SAINT
B. SATAN
C. Nessus
D. HPing
Heather has been tasked with setting up and implementing VPN tunnels to remote offices. She will most likely be implementing IPsec VPN tunnels to connect the offices. At what layer of the OSI model does an IPsec tunnel function on?
A. They function on the data link layer.
B. They work on the network layer.
C. They function on either the application or the physical layer.
D. They work on the session layer.
Which of the following is the full form of SAINT?
A. System Automated Integrated Network Tool
B. Security Admin Integrated Network Tool
C. System Admin Integrated Network Tool
D. System Administrators Integrated Network Tool
Which of the following is a worldwide organization whose mission is to create, refine and promote internet safety standards?
A. None
B. SPROUT
C. ANSI
D. IEEE
E. WASC
Which of the following creates passwords for individual administrator accounts and stores them in Windows AD?
A. LSASS
B. SRM
C. SAM
D. LAPS
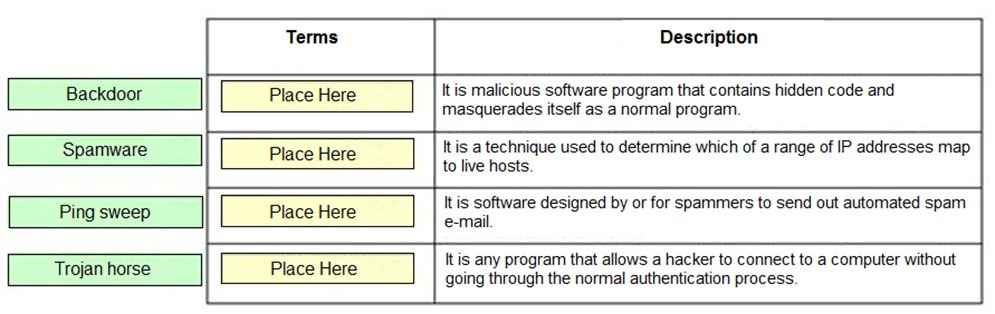
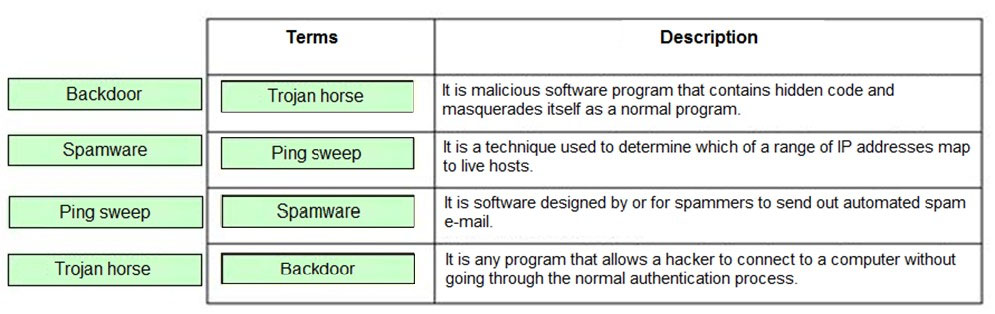
DRAG DROP - Drag and drop the terms to match with their descriptions. Select and Place:
In ______ method, event logs are arranged in the form of a circular buffer.
A. Non-wrapping method
B. LIFO method
C. Wrapping method
D. FIFO method
James is a network administrator working at a student loan company in Minnesota. This company processes over 20,000 student loans a year from colleges all over the state. Most communication between the company, schools, and lenders is carried out through emails. Much of the email communication used at his company contains sensitive information such as social security numbers. For this reason, James wants to utilize email encryption. Since a server-based PKI is not an option for him, he is looking for a low/no cost solution to encrypt emails. What should James use?
A. James should utilize the free OTP software package.
B. James can enforce mandatory HTTPS in the email clients to encrypt emails.
C. James could use PGP as a free option for encrypting the company’s emails.
D. James can use MD5 algorithm to encrypt all the emails.
Which among the following is used by anti-malware systems and threat intelligence platforms to spot and stop malicious activities at an initial stage?
A. Indicators of attack
B. Key risk indicators
C. Indicators of compromise
D. Indicators of exposure
Which BC/DR activity works on the assumption that the most critical processes are brought back from a remote location first, followed by the less critical functions?
A. Recovery
B. Restoration
C. Response
D. Resumption
Which of the following UTP cables supports transmission up to 20MHz?
A. Category 2
B. Category 5e
C. Category 4
D. Category 1
Which of the following layers provides communication session management between host computers?
A. Application layer
B. Internet layer
C. Transport layer
D. Link layer
Which of the following conditions cannot enter the system ROM monitor mode? Each correct answer represents a complete solution. Choose all that apply.
A. The router does not find a valid operating system image.
B. The router does not have the configuration file.
C. The user interrupts the boot sequence.
D. It is necessary to set the operating parameters.
Which of the following systems includes an independent NAS Head and multiple storage arrays?
A. FreeNAS
B. None of these
C. Gateway NAS System
D. Integrated NAS System
Which type of modulation technique is used in local area wireless networks (LAWNs)?
A. FHSS
B. DSSS
C. MIMO-OFDM
D. OFDM
The GMT enterprise is working on their internet and web usage policies. GMT would like to control internet bandwidth consumption by employees. Which group of policies would this belong to?
A. Enterprise Information Security Policy
B. Network Services Specific Security Policy
C. Issue Specific Security Policy
D. System Specific Security Policy
Which of the following types of RAID offers no protection for the parity disk?
A. RAID 2
B. RAID 1
C. RAID 5
D. RAID 3
You want to increase your network security implementing a technology that only allows certain MAC addresses in specific ports in the switches; which one of the above is the best choice?
A. Port Security
B. Port Authorization
C. Port Detection
D. Port Knocking
Which of the following steps of the OPSEC process examines each aspect of the planned operation to identify OPSEC indicators that could reveal critical information and then compare those indicators with the adversary's intelligence collection capabilities identified in the previous action?
A. Analysis of Threats
B. Application of Appropriate OPSEC Measures
C. Identification of Critical Information
D. Analysis of Vulnerabilities
E. Assessment of Risk
The Circuit-level gateway firewall technology functions at which of the following OSI layer?
A. Transport layer
B. Data-link layer
C. Session layer
D. Network layer
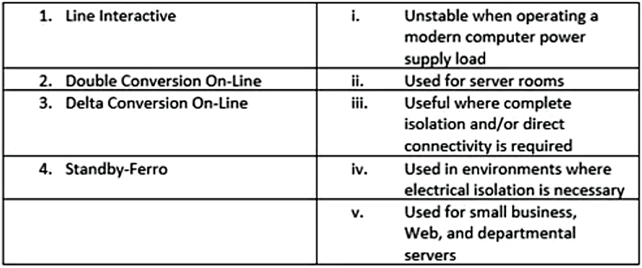
Your company is planning to use an uninterruptible power supply (UPS) to avoid damage from power fluctuations. As a network administrator, you need to suggest an appropriate UPS solution suitable for specific resources or conditions. Match the type of UPS with the use and advantage:
A. 1-i,2-iv,3-ii,4-v
B. 1-v,2-iii,3-i,4-ii
C. 1-ii,2-iv,3-iii,4-i
D. 1-iii,2-iv,3-v,4-iv
Which phase of incident response process involves collection of incident evidence and sending them to forensic department for further investigation?
A. Incident containment
B. Incident recording and assignment
C. Eradication
D. Preparation for incident response
Which of the following statements are true about an IPv6 network? Each correct answer represents a complete solution. Choose all that apply.
A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresses.
B. It increases the number of available IP addresses.
C. It uses longer subnet masks than those used in IPv4.
D. It provides improved authentication and security.
E. It uses 128-bit addresses.
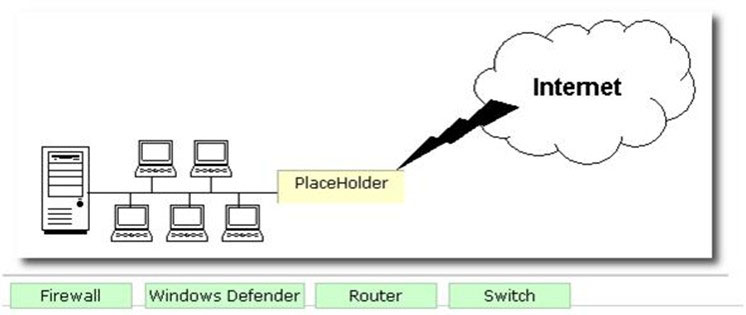
DRAG DROP - George works as a Network Administrator for Blue Soft Inc. The company uses Windows Vista operating system. The network of the company is continuously connected to the Internet. What will George use to protect the network of the company from intrusion? Select and Place:
Physical access controls help organizations monitor, record, and control access to the information assets and facility. Identify the category of physical security controls which includes security labels and warning signs.
A. Technical control
B. Environmental control
C. Physical control
D. Administrative control
Which protocol could choose the network administrator for the wireless network design, if he need to satisfied the minimum requirement of 2.4 GHz, 22 MHz of bandwidth, 2 Mbits/s stream for data rate and use DSSS for modulation.
A. 802.11n
B. 802.11g
C. 802.11b
D. 802.11a
What defines the maximum time period an organization is willing to lose data during a major IT outage event?
A. RPO
B. BC
C. RTO
D. DR
Which of the following is a process of transformation where the old system can no longer be maintained?
A. Disaster
B. Risk
C. Threat
D. Crisis
Which of the following is a tool that runs on the Windows OS and analyzes iptables log messages to detect port scans and other suspicious traffic?
A. PSAD
B. Hping
C. NetRanger
D. Nmap
Which of the following encryption techniques do digital signatures use?
A. MD5
B. RSA
C. Blowfish
D. IDEA
Which of the following steps will NOT make a server fault tolerant? Each correct answer represents a complete solution. (Choose two.)
A. Adding a second power supply unit
B. Performing regular backup of the server
C. Adding one more same sized disk as mirror on the server
D. Implementing cluster servers’ facility
E. Encrypting confidential data stored on the server
Which of the following tools is used to ping a given range of IP addresses and resolve the host name of the remote system?
A. SuperScan
B. Netscan
C. Hping
D. Nmap
The agency Jacob works for stores and transmits vast amounts of sensitive government data that cannot be compromised. Jacob has implemented Encapsulating Security Payload (ESP) to encrypt IP traffic. Jacob wants to encrypt the IP traffic by inserting the ESP header in the IP datagram before the transport layer protocol header. What mode of ESP does Jacob need to use to encrypt the IP traffic?
A. Jacob should use ESP in pass-through mode.
B. Jacob should utilize ESP in tunnel mode.
C. He should use ESP in gateway mode.
D. He should use ESP in transport mode.
Justine has been tasked by her supervisor to ensure that the company's physical security is on the same level as their logical security measures. She installs video cameras at all entrances and exits and installs badge access points for all doors. The last item she wants to install is a method to prevent unauthorized people piggybacking employees. What should she install to prevent piggybacking?
A. Justine needs to install a biometrics station at each entrance.
B. She should install a mantrap.
C. She should install a Thompson Trapdoor.
D. Justine will need to install a revolving security door.
As a network administrator, you have implemented WPA2 encryption in your corporate wireless network. The WPA2's __________ integrity check mechanism provides security against a replay attack.
A. CBC-MAC
B. CRC-MAC
C. CBC-32
D. CRC-32
Which of the following incident handling stage removes the root cause of the incident?
A. Eradication
B. Recovery
C. Detection
D. Containment
Leslie, the network administrator of Livewire Technologies, has been recommending multilayer inspection firewalls to deploy the company’s infrastructure. What layers of the TCP/IP model can it protect?
A. IP, application, and network interface
B. Network interface, TCP, and IP
C. Application, TCP, and IP
D. Application, IP, and network interface
Which of the following steps OPSEC process examines every aspect of the proposed operation to identify the OPSEC indicators that can reveal important information and then compare them with indicators of the opponent's intelligence collection capabilities identified in the previous activity?
A. Identification of Critical Information
B. analysis weakness
C. risk assessment
D. Appropriate OPSEC measures
E. analysis of threats
James is working as a Network Administrator in a reputed company situated in California. He is monitoring his network traffic with the help of Wireshark. He wants to check and analyze the traffic against a PING sweep attack. Which of the following Wireshark filters will he use?
A. Icmp.type==8 or icmp.type==16
B. icmp.type==8 or icmp.type==0
C. icmp.type==8 and icmp.type==0
D. Icmp.type==0 and icmp.type==16
Which firewall technology can be implemented in all (application, session, transport, network, and presentation) layers of the OSI model?
A. Circuit-level gateway
B. Packet filtering
C. VPN
D. Network address translation
Kelly is taking backups of the organization's data. Currently, she is taking backups of only those files that are created or modified after the last backup. What type of backup is Kelly using?
A. Full backup
B. Incremental backup
C. Normal backup
D. Differential backup
Which of the following can be used to suppress fire from Class K sources?
A. Water
B. Carbon dioxide
C. Foam
D. Dry Chemical
Adam works as a Professional Penetration Tester. A project has been assigned to him to test the vulnerabilities of the CISCO Router of Umbrella Inc. Adam finds out that HTTP Configuration Arbitrary Administrative Access Vulnerability exists in the router. By applying different password cracking tools, Adam gains access to the router. He analyzes the router config file and notices the following lines: logging buffered errors logging history critical logging trap warnings logging 10.0.1.103 By analyzing the above lines, Adam concludes that this router is logging at log level 4 to the syslog server 10.0.1.103. He decides to change the log level from 4 to 0. Which of the following is the most likely reason of changing the log level?
A. Changing the log level from 4 to 0 will result in the logging of only emergencies. This way the modification in the router is not sent to the syslog server.
B. By changing the log level, Adam can easily perform a SQL injection attack.
C. Changing the log level grants access to the router as an Administrator.
D. Changing the log level from 4 to 0 will result in the termination of logging. This way the modification in the router is not sent to the syslog server.
Simran is a network administrator at a start-up called Revolution. To ensure that neither party in the company can deny getting email notifications or any other communication, she mandates authentication before a connection establishment or message transfer occurs. What fundamental attribute of network defense is she enforcing?
A. Integrity
B. Non-repudiation
C. Confidentiality
D. Authentication
John has successfully remediated the vulnerability of an internal application that could have caused a threat to the network. He is scanning the application for the existence of a remediated vulnerability, this process is called a __________ and it has to adhere to the __________.
A. Mitigation, Security policies
B. Verification, Security Policies
C. Vulnerability scanning, Risk Analysis
D. Risk analysis, Risk matrix
Which of the following types of information can be obtained through network sniffing? (Choose all that apply.)
A. DNS traffic
B. Telnet passwords
C. Programming errors
D. Syslog traffic
John is the Vice-President of a BPO. He wants to implement a policy allowing employees to use and manage devices purchased by the organization but restrict the use of the device for business use only. Which among the following policies does John want to implement?
A. COPE policy
B. CYOD policy
C. BYOD policy
D. COBO policy
Which BC/DR activity includes action taken toward resuming all services that are dependent on business-critical applications?
A. Response
B. Recovery
C. Resumption
D. Restoration
Byron, a new network administrator at FBI, would like to ensure that Windows PCs there are up-to-date and have less internal security flaws. What can he do?
A. Centrally assign Windows PC group policies
B. Dedicate a partition on HDD and format the disk using NTFS
C. Download and install latest patches and enable Windows Automatic Updates
D. Install antivirus software and turn off unnecessary services
Access Full 312-38 Dump Free
Looking for even more practice questions? Click here to access the complete 312-38 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 312-38 dump free questions — and get one step closer to exam success!