300-910 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 300-910 certification exam? Start your preparation the smart way with our 300-910 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 300-910 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 300-910 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Refer to the exhibit. What is the user doing with Drone in this automated test?
A. testing Alpine Linux versus Ubuntu Linux
B. testing a PostgreSQL DB against multiple architectures
C. testing only the amd64 architecture
D. testing PostgreSQL deployment in an Alpine Linux VM
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
A. It runs unit tests against code that is committed.
B. It builds your software on the production environment.
C. It builds your software when changes are committed.
D. It builds your software every 500 milliseconds.
E. It must have a plug-in for Puppet and Maven.
DRAG DROP -Refer to the exhibit. A development team is designing an application that will include multiple components and services. To streamline the process, CO/CD must be implemented. Drag and drop the CI/CD pipeline stages from the left onto the targets on the right.
Refer to the exhibit. What is causing the requests code to fail?
A. Rython3 is not compatible with requests.
B. The requests library is not imported.
C. The requests library is not installed.
D. The requests coming into stdin fail because device_ip cannot be parsed.
Which Dockerfile yields the most predictable builds?
A.

B.

C.

D.

A developer is creating an application based on microservices. The application will be used as a central repository for all company's documents. One of the microservices in the application will perform image processing. This microservice must autoscale to meet the current load and avoid down time. Which metric must be used to trigger autoscaling events?
A. network
B. CPU/GPU
C. disk I/O
D. memory
Which two elements help to secure your API keys? (Choose two.)
A. ramdomness
B. SHA1
C. triple AES
D. rotation
E. dictionary
What is the impact of using the Drone.io CI/CD tool on the local installation step?
A. slows down the development
B. delays the deployment of components
C. speeds up the procedure
D. complicates the application process
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to create a Terraform configuration that builds the network environment for a multitier software application. More EPG, Contract, and Filter definitions have been removed from the code.
What is chaos engineering?
A. designing an application with fuzzy logic that makes it hard to predict
B. a product engineering approach that lacks a formal methodology
C. splitting a project between teams that do not communicate with each other
D. introducing problems into a system to study behavior and improve reliability
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
A. Jenkins
B. Genie CLI
C. Travis CI
D. Python YAML data libraries
Refer to the exhibit. What is the reason for this error message?
A. The required dependencies for the urllib3 module are not installed.
B. The requests module is not installed.
C. The required dependencies for the requests module are not installed.
D. The site-packages directory has been corrupted.
What is a benefit of monitoring the CI/CD pipeline?
A. troubleshoots distributed systems performance
B. proactively deploys new servers if needed
C. analyzes network outages that affect the network and server infrastructure
D. provides insight into how efficiently the development team is operating
Which step must be taken to enable centralized logging in a Kubernetes environment?
A. No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B. Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C. Deploy a sidecar node that aggregates logs from the entire cluster.
D. Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.
Which description of a canary deployment is true?
A. deployment by accident
B. deployment that is rolled back automatically after a configurable amount of minutes
C. deployment relating to data mining development
D. deployment to a limited set of servers or users
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
A. performing code reviews
B. requirement gathering
C. change management process
D. new code scanning
E. rollback plans
Refer to the exhibit. A distributed application contains data services that connect to databases via JDBC and to other remote services via HTTP. The overall response time is too long, and AppDynamics is used to investigate the root cause. From the application flow map, a specific data service running on Docker has been identified whose response time is over 10 seconds. Which action resolves the issue?
A. Change from a JDBC call to a HTTP call to retrieve data faster
B. Run the AccountProfileMySQL service in Kubernetes
C. Explore the JDBC queries looking for optimization opportunities
D. Verify if the Docker container running MySQL is limiting CPU utilization
FILL BLANK - Fill in the blanks to complete the line of Python code that sends a message to a Webex Teams room or person.
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network. If an attacker gains access to the scripts, what is the risk exposure?
A. The Automation server is at risk of being compromised.
B. The Ansible scripts run through encrypted SSH connections.
C. The internal network is at risk of being compromised.
D. The entire CI/CD-related infrastructure is at risk.
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?
A. Ansible
B. pyATS
C. Genie CLI
D. Travis CI
A precheck validation is being designed for the network state in a Cl/CD pipeline This design requires: • the CI/CD pipeline to spin up test instances. • instances must be used to validate changes. • changes must be validated prior to a continuous deployment workflow, and • then push the changes to production How should the pipeline target the required environment?
A. Use separate CI servers for each environment
B. Use different pipelines for each environment
C. Use separate Git repositories for each environment
D. Use different inventory files for each environment
FILL BLANK - Fill in the blanks to describe the concepts of extending DevOps practices to the network for NetDevOps. NetDevOps builds and manages networks as a system that enables network services to be consumed in a DevOps approach. Organizations practicing NetDevOps see changes in the _________ as routine and expected activities, with a well-defined and practiced process for _________ , testing, and __________ network changes. By making them routine, network changes can be small and simple.
Refer to the exhibit. A developer needs to scale the existing pods within the worked nodes. Which object should be edited to achieve this goal?
A. ReplicaSet
B. PriorityClass
C. Deployment
D. Pod
How long analysis systems such as Elasticsearch, Logstash, and Kibana Stack handle ingesting unstructured logs from different devices in various formats?
A. All devices that generate syslogs must use agents that process the local logs and transmit them in a specific format to the ELK Stack.
B. All logs are stored in their unstructured text format, and the ELK Stack performs data analysis by intelligently parsing the logs using machine learning algorithms.
C. All different message formats are parsed separately using custom filters, and the resulting structured data is stored for later analysis.
D. A single, comprehensive log format is defined on the ELK Stack. All incoming logs, regardless of format, are transformed to match the comprehensive format, and only applicable fields are populated.
How does eliminating hardcoded or default passwords help to secure an environment?
A. helps by enforcing your password in a repository and storing it in a secure vault
B. helps to manage passwords centrally
C. helps penetration testing team to focus on other issues more efficiently
D. helps by removing back doors in your environments
Which Dockerfile produces an efficient image rebuild when the exposed port Python dependency, or MyApp source code is modified?
A.

B.

C.

D.

Which two actions help limit the attack surface of your Docker container? (Choose two.)
A. Run only a single service in each container.
B. Run all services in a single image.
C. Use version tags for base images and dependencies.
D. Use Kali Linux as a base image.
E. Download images over HTTPS supporting sites.
Which Kubernetes object is used to create a ClusterIP or NodePort?
A. service
B. pod
C. deployment
D. loadbalancer
DRAG DROP -Refer to the exhibit. A developer is creating a health check monitoring script that queries information from the Cisco DNA Center platform. The script must trigger an alert if a site health statistic named accessGoodCount drops below 80 and if a network statistic named latestHealthScore is 95 or less. Drag and drop the code snippets from the bottom onto the blanks in the code to monitor the site and network health on a Cisco DNA Center platform instance. Options may be used more than once. Not all options are used.
DRAG DROP - Drag and drop the steps in Gartner's public cloud cost management framework from the left into the order on the right.
Refer to the exhibit. The text represents a syslog message sent from a Linux server to a centralized log system. Based on the format of the log message, how must the functionality of the log parser be extended to improve search capabilities?
A. Reverse lookup the IP address to add a hostname field
B. Convert the date to the time zone of the system
C. Configure the Linux machine to add a UID field to messages
D. Filter out the text of the message to speed up searches
Refer to the exhibit. An organization has issues with code-based failures after implementing a CI/CD pipeline to automate the builds and deployment phases of an application. Which action must be added to the pipeline, after the application is deployed in the staging environment to minimize failures and to ensure a successful continuous deployment?
A. Restructuring and monitoring tests must be run after it is promoted to production
B. Restructuring and monitoring tests must be run before it is promoted to production
C. Functional and nonfunctional tests must be run after it is promoted to production
D. Functional and nonfunctional tests must be run before it is promoted to production
Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability. In which two ways are these services packaged and deployed? (Choose two.)
A. Service instances must be isolated from one another.
B. Service must be independently deployable and scalable.
C. Service are written using the same languages, frameworks, and framework versions.
D. Service must be dependent, deployable, and scalable.
E. Service instances do not need to be isolated from one another.
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.
Refer to the exhibit. The push_configs.yml playbook returns the error shown. Which action resolves the error?
A. Install the Paramiko library on the host that runs Ansible
B. Generate a new SSH key pair and add the public key to the target machine
C. Export the ANSIBLE_HOST_KEY_CHECKING=False variable
D. Comment out the StrictHostKeyChecking=yes line from ansible.cfg
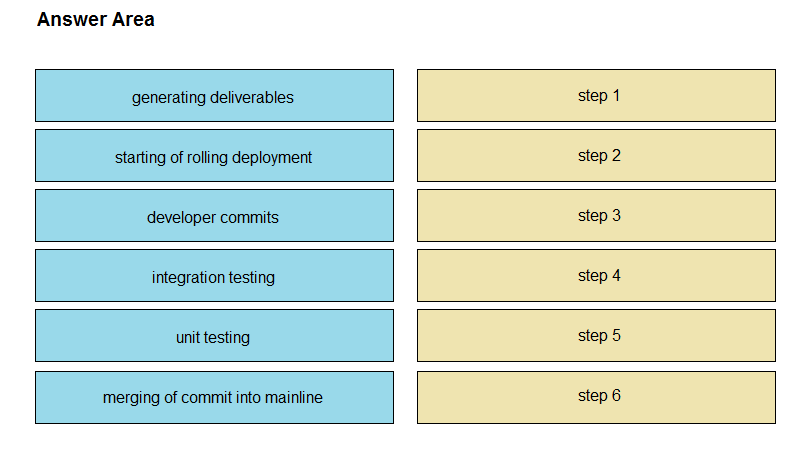
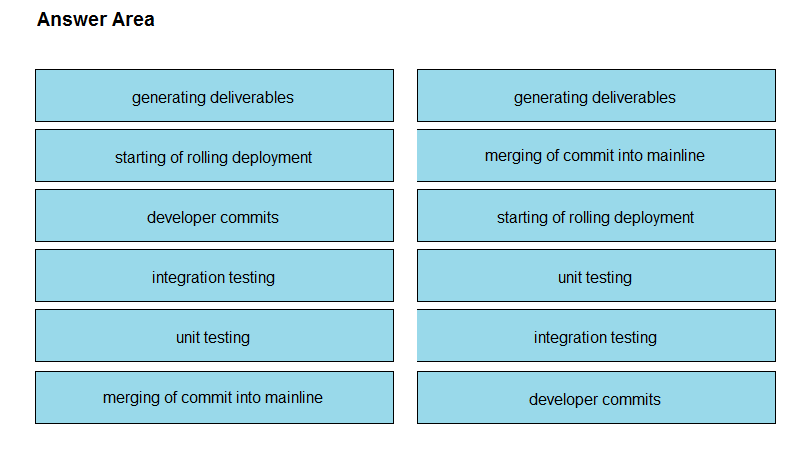
DRAG DROP - Drag and drop the operations from the left into the correct order on the right when using CI/CD, assuming that there are no failures or conflicts. Select and Place:
What is a capability of node-level logging in Kubernetes?
A. Using the Kubernetes JSON logging driver enables log persistence
B. Output that is written to stdin is retrieved by using kubectl
C. Output that is written to stderr is not logged or retrievable by using kubectl
D. Using the local logging driver of Docker enables log persistence
A DevOps engineer is supporting a containerized application with multiple components running across the Kubernetes cluster. Metrics from the container (CPU and memory) and application (requests per second and heap size) are being collected by Prometheus and displayed with Grafana. Users report transaction timeout problems with the application, but the metric graphs all look within normal levels. Which type of failure would prevent the engineer from seeing the problem using the captured metrics?
A. Grafana has lost connectivity to Prometheus, which causes graphs to display only the cached data.
B. CPU and memory metrics from Kubernetes nodes are not accurate due to the way that containers share resources.
C. Some containers are crashing regularly and being restarted automatically by Kubernetes.
D. The metricbeat agent has crashed and is no longer sending new data to Prometheus, so the metrics are not updating.
Which approach must be used to integrate DevOps practices into the team structure in an existing organization?
A. Create a team that can deliver all the stages with active cooperation between the team members
B. Create a team that can deliver all the stages with well-defined roles and a communication structure between team members
C. Create a team for each stage with structured communication channels
D. Create a team for each stage with active cooperation between the teams
DRAG DROP -Refer to the exhibit. A containerized application that leverages a container host VM must be deployed. Drag and drop the events on the left onto their related steps on the right in order to describe the sequence behind the process.
Refer to the exhibit. An application has been developed as a fileserver. To create this application as a fileserver. the class is used to store data in an SQL database. Which two steps help minimize the risk of attack and compromise of the application? (Choose two.)
A. Reject string values that are greater than maximum size
B. Use floating point instead of integer for rating to avoid overflow
C. Validate the content of the name and address parameters
D. Run the application in a Docker container
E. Compile the application using Java HotSpot
Which Docker command is used to start an interactive Bash shell in a running container named "test"?
A. docker attach -it test /bin/bash
B. docker run -it test /bin/bash
C. docker exec -it test /bin/bash
D. docker run test /bin/bash
What is the purpose of using a build tool in software development?
A. It complies source code into binaries and executables.
B. It provides a way to edit source code using a graphical interface.
C. It is a manual process that is followed to build software.
D. It tracks bugs and incidents in a built application.
A DevOps engineer must build a Docker image to containerize an application. Then the image must be pushed to a repository on Docker Hub in a CI/CD pipeline using GitHub Actions. Which approach securely encrypts the Docker Hub access token as an environment variable within the CI/CD pipeline?
A. Store the access token with GitHub environment variables
B. Store the access token with GitHub encrypted secrets
C. Store the access token in an environment file in the repository
D. Hard code the access token in the repository with Base64 encoding
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
A. Apply
B. Install
C. Deploy
D. Create
E. Expose
Refer to the exhibit. Which CI solution uses this file?
A. Drone
B. GitLab CI
C. Travis CI
D. Jenkins
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
A. encode the value with base64 in a secure DNS CTEXT entry
B. as an environment variable in the Dockerfile
C. Docker environment variable
D. Docker secrets
What are two benefits of Infrastructure as Code? (Choose two.)
A. It enables continuous integration.
B. It allows for management control.
C. It ensures consistency.
D. It improves application monitoring.
E. It reduces risk.
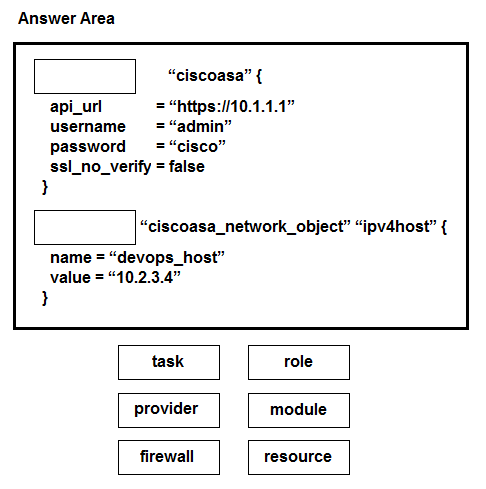
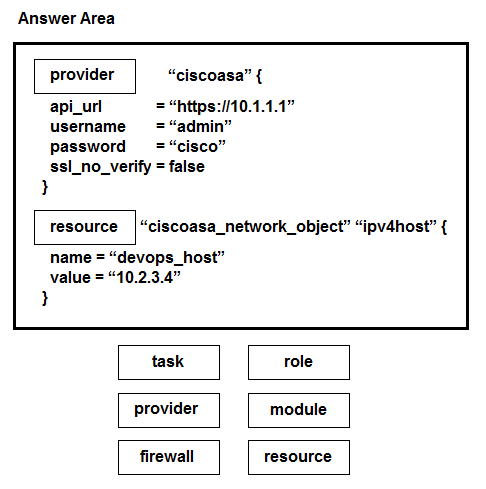
DRAG DROP - Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device. Select and Place:
DRAG DROP - A developer is creating an application where each service uses a different operating system. The application components need to be isolated but must have the ability to communicate with each other. Drag and drop the entries from the left into the order on the right to create a Dockerfile that will accomplish this goal.
Access Full 300-910 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 300-910 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 300-910 mock test free today—and take a major step toward exam success!