300-910 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 300-910 certification? Our 300-910 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 300-910 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 300-910 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
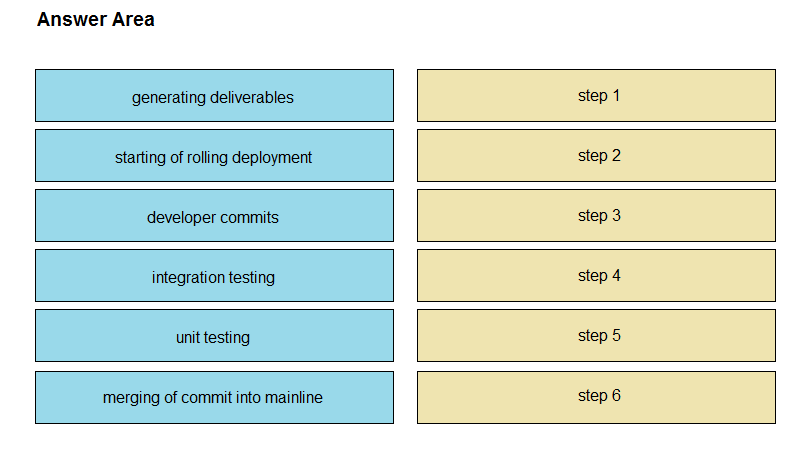
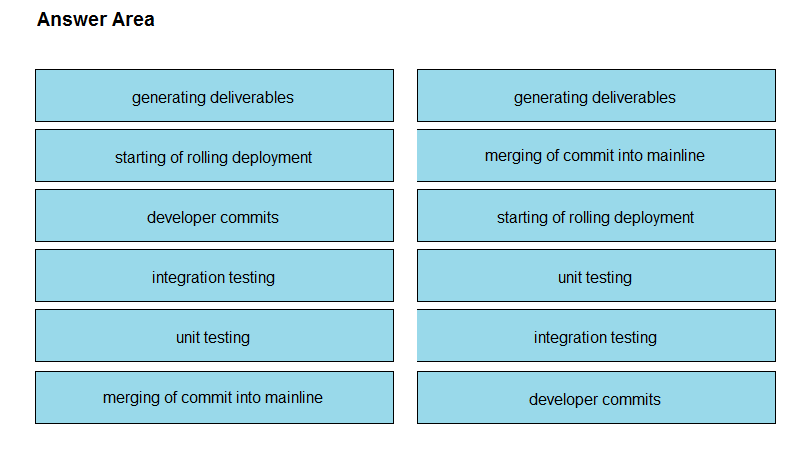
DRAG DROP - Drag and drop the operations from the left into the correct order on the right when using CI/CD, assuming that there are no failures or conflicts. Select and Place:
Which type of security testing should be performed as a part of a CI/CD pipeline by analyzing the source code itself without compiling the code into a running executable?
A. Dynamic Application Security Testing
B. Runtime Application Health-Protection
C. Continuous Application Security Testing
D. Static Analysis Security Testing
FILL BLANK - Fill in the blanks to describe the concepts of extending DevOps practices to the network for NetDevOps. NetDevOps builds and manages networks as a system that enables network services to be consumed in a DevOps approach. Organizations practicing NetDevOps see changes in the _________ as routine and expected activities, with a well-defined and practiced process for _________ , testing, and __________ network changes. By making them routine, network changes can be small and simple.
What is the impact of using the Drone.io CI/CD tool on the local installation step?
A. slows down the development
B. delays the deployment of components
C. speeds up the procedure
D. complicates the application process
Which two actions help limit the attack surface of your Docker container? (Choose two.)
A. Run only a single service in each container.
B. Run all services in a single image.
C. Use version tags for base images and dependencies.
D. Use Kali Linux as a base image.
E. Download images over HTTPS supporting sites.
A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network. If an attacker gains access to the scripts, what is the risk exposure?
A. The Automation server is at risk of being compromised.
B. The Ansible scripts run through encrypted SSH connections.
C. The internal network is at risk of being compromised.
D. The entire CI/CD-related infrastructure is at risk.
A company has experienced serious growth and the hosted applications are getting more and more hits. Based on the increased work load, applications have started to show signs of reduced performance, which is affecting the user experience. Which two server metrics should be tracked to ensure that the customer experience remains within acceptable limits? (Choose two.)
A. application feature sprawl
B. CPU peak usage
C. CPU average usage
D. microservices count
E. CPU frequency
Refer to the exhibit. How does the architecture respond to a usage spike?
A. The monitoring software instructs the Orchestrator to increase the count of containers and to configure the load balancer accordingly
B. The database prioritizes quick and immediate queries over complicated ones to reduce the request queue
C. The Orchestrator increases the resources assigned to containers to increase performance
D. The load balancer interacts with the Orchestrator to optimize the balancing algorithm to match the incoming flow of requests
DRAG DROP -Refer to the exhibit. A developer is creating a health check monitoring script that queries information from the Cisco DNA Center platform. The script must trigger an alert if a site health statistic named accessGoodCount drops below 80 and if a network statistic named latestHealthScore is 95 or less. Drag and drop the code snippets from the bottom onto the blanks in the code to monitor the site and network health on a Cisco DNA Center platform instance. Options may be used more than once. Not all options are used.
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
A. node
B. app
C. agent
D. tier
E. event
Refer to the exhibit. The exhibit shows the output of an Ansible task that prints the contents of the show_ip_int_brief variable that was registered in a different task in the playbook. Which expression is used to print the output of the command without its header row?
A. show_ip_int_brief[“˜stdout_lines’][0]
B. show_ip_int_brief[“˜stdout_lines’][1:]
C. show_ip_int_brief[“˜stdout_lines’][0][1:]
D. show_ip_int_brief[“˜stdout_lines’]
Refer to the exhibit. The push_configs.yml playbook returns the error shown. Which action resolves the error?
A. Install the Paramiko library on the host that runs Ansible
B. Generate a new SSH key pair and add the public key to the target machine
C. Export the ANSIBLE_HOST_KEY_CHECKING=False variable
D. Comment out the StrictHostKeyChecking=yes line from ansible.cfg
An organization is developing an application using Git. Each team member is assigned to work on specific parts of the application. At the end of each task, individual code parts are merged in the main build. Which two requirements should be implemented to increase the likelihood of continuous integration? (Choose two.)
A. Changes must be scheduled to deploy at a specific time that has minimal traffic
B. Changes must include automated tests
C. Changes must be validated during deployment to the production environment
D. Smaller, individually testable changes must be merged first
E. Team members must be responsible for the code committed by any team member
Refer to the exhibit. A docker-compose.yml file implements a postgres database container. Which .gitlab-ci.yml code block checks the health status of the container and stops the pipeline if the container is unhealthy?
A.

B.

C.

D.

FILL BLANK - Fill in the blanks to complete the line of Python code that sends a message to a Webex Teams room or person.
Which Kubernetes object is used to create a ClusterIP or NodePort?
A. service
B. pod
C. deployment
D. loadbalancer
A new banking application is being developed as the main currency exchange resource for all the customers on a global scale. The application must comply with the security based on the deployed region. Therefore, the CI/CD pipeline must be created with the highest security possible. Which approach accomplishes this goal?
A. Give the accounts used in the CI/CD pipeline full administrative rights to all applications
B. Use the same passwords across the entire CI/CD pipeline
C. Ensure that secrets are not inadvertently passed on during builds for pull requests via CI/CD pipeline
D. Never use one-time passwords in CI/CD pipeline
Which step must be taken to enable centralized logging in a Kubernetes environment?
A. No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B. Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C. Deploy a sidecar node that aggregates logs from the entire cluster.
D. Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.
Refer to the exhibit. Which action allows the development team to reach the deployed application?
A. Create an init container to initialize routes for the containers in the pod
B. Create a service to expose the logic running in the pod
C. Delete the deployment and redeploy by using a ReplicaSet.
D. Delete the deployment and redeploy by using the latest tag for the container image
A team must roll out updates on the production instance of an application. To avoid any service down time, the new version must be released alongside the old version. After the team ensures that the new version operates as it should, traffic will be redirected to the new version. Then the old version will be shut down. Which deployment strategy must be used?
A. rolling
B. blue/green
C. shadow
D. canary
DRAG DROP - Drag and drop the steps in Gartner's public cloud cost management framework from the left into the order on the right.
What is the purpose of using a build tool in software development?
A. It complies source code into binaries and executables.
B. It provides a way to edit source code using a graphical interface.
C. It is a manual process that is followed to build software.
D. It tracks bugs and incidents in a built application.
Which two elements help to secure your API keys? (Choose two.)
A. ramdomness
B. SHA1
C. triple AES
D. rotation
E. dictionary
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?
A. Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command.
B. Add a step to capture the routing table before the change, and add a step after the change to capture it again. Calculate the difference between the two for review.
C. Add a step to ping a host on each of the static routes before the change, and a step after to repeat the same check. Calculate the difference between the two checks for review.
D. Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again.
A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
A. performing code reviews
B. requirement gathering
C. change management process
D. new code scanning
E. rollback plans
Which Dockerfile produces an efficient image rebuild when the exposed port Python dependency, or MyApp source code is modified?
A.

B.

C.

D.

A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?
A. recreate
B. blue/green
C. rolling
D. canary
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
A. encode the value with base64 in a secure DNS CTEXT entry
B. as an environment variable in the Dockerfile
C. Docker environment variable
D. Docker secrets
Which description of a canary deployment is true?
A. deployment by accident
B. deployment that is rolled back automatically after a configurable amount of minutes
C. deployment relating to data mining development
D. deployment to a limited set of servers or users
An IT team plans to deploy a new service built on top of an existing service. The capacity needed for the new service is difficult to estimate because the demand for the new service is undetermined. The team has these deployment requirements: • A subset of the users of the original service must be migrated to the new service based on their profile • The new service must be rolled back easily if capacity exceeds estimates Which deployment strategy must be used?
A. rolling
B. blue/green
C. geolocation
D. canary
A DevOps engineering wants to build an application implementation based on the CI/CD pipeline model. Which service should be used to provide hosted continuous service for open and private projects?
A. Ansible
B. pyATS
C. Genie CLI
D. Travis CI
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to create a Terraform configuration that builds the network environment for a multitier software application. More EPG, Contract, and Filter definitions have been removed from the code.
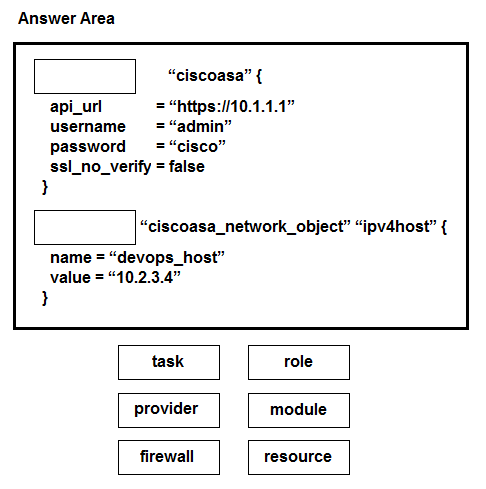
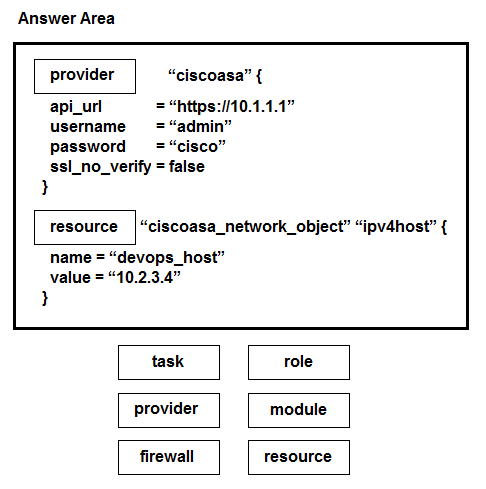
DRAG DROP - Drag and drop the commands from the bottom onto the correct Terraform code in the exhibit to push a network object to a Cisco ASA Firewall device. Select and Place:
Which Kubernetes object ensures that each node is limited to running no more than one pod?
A. UniCast
B. Deployment
C. DaemonSet
D. ReplicaSet
Refer to the exhibit. What are the properties of the load balancer in a Kubernetes environment?
A. Has exposed ports 80 and 8080 to a private IP address and directs outgoing connections to the port named http-port1
B. Has exposed ports 80 and 8080 to a public IP address and directs incoming connections to the port named nginx-port
C. Forwards incoming traffic from the port named nginx-port to ports 80 and 8080 of nginxapp
D. Forwards any outgoing traffic from the port named nginx-port to exposed ports http-port1 and http-port2 of nginxapp
What is a capability of node-level logging in Kubernetes?
A. Using the Kubernetes JSON logging driver enables log persistence
B. Output that is written to stdin is retrieved by using kubectl
C. Output that is written to stderr is not logged or retrievable by using kubectl
D. Using the local logging driver of Docker enables log persistence
Refer to the exhibit. What is the reason for this error message?
A. The required dependencies for the urllib3 module are not installed.
B. The requests module is not installed.
C. The required dependencies for the requests module are not installed.
D. The site-packages directory has been corrupted.
DRAG DROP - A developer is creating an application where each service uses a different operating system. The application components need to be isolated but must have the ability to communicate with each other. Drag and drop the entries from the left into the order on the right to create a Dockerfile that will accomplish this goal.
What is an advantage of using configuration management tools to automate infrastructure services?
A. eliminates the need to run integration tests within the CI/CD pipeline
B. provides high native monitoring of services
C. eliminates the need for CI/CD tools
D. integrates with container orchestration
A company has a CI/CD pipeline implemented to automate application deployment. An urgent change is required in the production environment. A developer produces and tests the required change in the company's environment, but the pipeline fails when pushed. Which action conforms to the rules of a CI/CD pipeline and enables the pipeline to pass?
A. Remove the failing test.
B. Manually deploy the change into the production environment
C. Use a backup pipeline
D. Replicate the production environment in the pipeline before applying
What are two reasons a Docker golden image should be updated? (Choose two.)
A. when there is a change to a username or password in the Docker secrets
B. when the application has a new release
C. when a fix for a security vulnerability is released
D. when a change is needed to an environment variable in the Dockerfile
E. when the base image is nearing the end of life
An IT department needs to deploy a new application named ‘Entfin434772390’ across the entire enterprise. The deployment must gradually transfer user traffic from an on older and nearly identical version of the application named ‘Entfin02754932l’. Both versions of the application are running in the production environment. Which release strategy should be used by the IT department?
A. agile
B. canary
C. rollbacks
D. blue/green
Which two statements about Infrastructure as Code are true? (Choose two.)
A. Test-driven development practices make use of Infrastructure as Code.
B. Infrastructure as Code refers to automated testing libraries.
C. DevOps builds upon Infrastructure as Code.
D. Infrastructure as Code is based on practices from software development.
E. Infrastructure as Code must use the same programming language as the application.
What is a practice of infrastructure as code?
A. Use multiple version control systems
B. Document as much as possible
C. Configure the deployment consistently
D. Test, integrate, and deploy once a day
What is chaos engineering?
A. designing an application with fuzzy logic that makes it hard to predict
B. a product engineering approach that lacks a formal methodology
C. splitting a project between teams that do not communicate with each other
D. introducing problems into a system to study behavior and improve reliability
Refer to the exhibit. Which CI solution uses this file?
A. Drone
B. GitLab CI
C. Travis CI
D. Jenkins
Configuration changes to the production network devices are performed by a CI/CD pipeline. The code repository and the CI tool are running on separate servers. Some configuration changes are pushed to the code repository, but the pipeline did not start. Why did the pipeline fail to start?
A. The CI server was not configured as a Git remote for the repository.
B. The webhook call from the code repository did not reach the CI server.
C. Configuration changes must be sent to the pipeline, which then updates the repository.
D. The pipeline must be started manually after the code repository is updated.
What is the effective way to manage computing costs in a public cloud?
A. Monitor data transfers to minimize cost.
B. Use dedicated hardware for all instances.
C. Select the largest instance option available in order to pay for only one instance.
D. Make use of elastic services and scale on demand.
Which two practices help make the security of an application a more integral part of the software development lifecycle? (Choose two.)
A. Add a step to the CI/CD pipeline that runs a dynamic code analysis tool during the pipeline execution.
B. Add a step to the CI/CD pipeline that runs a static code analysis tool during the pipeline execution.
C. Use only software modules that are written by the internal team.
D. Add a step to the CI/CD pipeline to modify the release plan so that updated versions of the software are made available more often.
E. Ensure that the code repository server has enabled drive encryption and stores the keys on a Trusted Platform Module or Hardware Security Module.
An application is being developed to be used by the HR department of a company on a global scale. The application will be used as a central repository for employee contracts. For user access, a RADIUS server will be used with authorized user groups. Which action must be used to prevent developers from accidentally committing secrets in the code?
A. Add a unit test to block the secrets
B. Add a precommit Git hook to block the secrets
C. Add dast to the repository to block the secrets
D. Add a job in the CI build to block the secrets
Access Full 300-910 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 300-910 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 300-910 certification journey!