300-910 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 300-910 certification? Our 300-910 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 300-910 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 300-910 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
To make logging searches more efficient and useful in Kibana, an Administrator wants to implement index patterns around the hostname of some software systems. Where should this be configured?
A. Configure a new JSON object in Kibana.
B. Create a search index in Logstash.
C. Create an index pattern in Kibana.
D. Create a time filter on Kibana to look at time only.
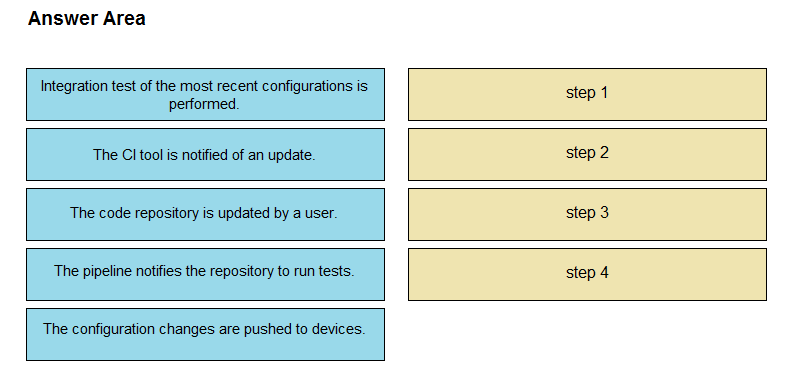
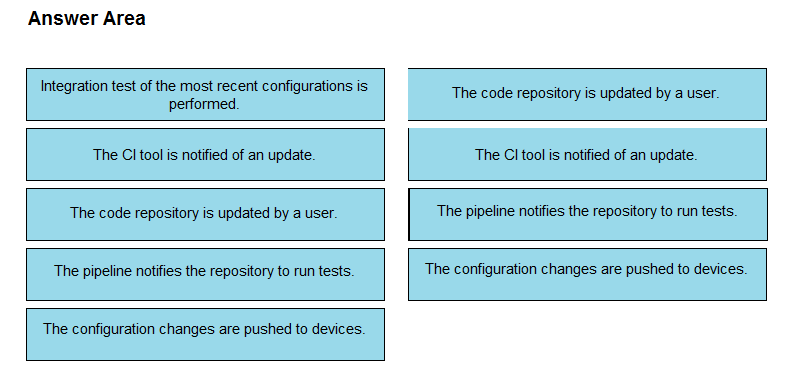
DRAG DROP - The IaC configuration for an application is being deployed using a CI/CD pipeline. Drag and drop the steps for this pipeline from the left into the correct order that they would be executed on the right. Not all options are used. Select and Place:
An application for storing and categorizing has been developed. The application uses dual-factor authentication for user access. After authentication, users can upload sensitive data. The application has been hacked through system exploits and most of the saved data has been lost. Which action prevents new security threats in the environment?
A. Use self-developed algorithms for encryption
B. Install virtual firewalls
C. Actively change the ISP provider
D. Apply all the latest patches and updates
An organization is developing an application using Git. Each team member is assigned to work on specific parts of the application. At the end of each task, individual code parts are merged in the main build. Which two requirements should be implemented to increase the likelihood of continuous integration? (Choose two.)
A. Changes must be scheduled to deploy at a specific time that has minimal traffic
B. Changes must include automated tests
C. Changes must be validated during deployment to the production environment
D. Smaller, individually testable changes must be merged first
E. Team members must be responsible for the code committed by any team member
What is the impact of using the Drone.io CI/CD tool on the local installation step?
A. slows down the development
B. delays the deployment of components
C. speeds up the procedure
D. complicates the application process
DRAG DROP -Refer to the exhibit. A containerized application that leverages a container host VM must be deployed. Drag and drop the events on the left onto their related steps on the right in order to describe the sequence behind the process.
What are two testing scenarios of the chaos engineering principle? (Choose two.)
A. maxing out CPU cores on an Elasticsearch duster
B. removing all users from a version control system
C. executing routine in driver code to emulate I/O errors
D. blocking developers’ building access
E. unplugging a core switch device
The E-commerce application is being monitored using AppDynamics. AppDynamics has noticed that the application response has degraded and has identified some thread contention that might be the cause of the delays. Where in the interface does AppDynamics bring this to your attention?
A. Potential Issues section of an individual transaction
B. Transaction Score graph of a business transaction
C. Code Deadlock section of the Event List
D. Slow Calls and Errors tab of the application
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
A. It runs unit tests against code that is committed.
B. It builds your software on the production environment.
C. It builds your software when changes are committed.
D. It builds your software every 500 milliseconds.
E. It must have a plug-in for Puppet and Maven.
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?
A. recreate
B. blue/green
C. rolling
D. canary
Configuration changes to the production network devices are performed by a CI/CD pipeline. The code repository and the CI tool are running on separate servers. Some configuration changes are pushed to the code repository, but the pipeline did not start. Why did the pipeline fail to start?
A. The CI server was not configured as a Git remote for the repository.
B. The webhook call from the code repository did not reach the CI server.
C. Configuration changes must be sent to the pipeline, which then updates the repository.
D. The pipeline must be started manually after the code repository is updated.
What is the effective way to manage computing costs in a public cloud?
A. Monitor data transfers to minimize cost.
B. Use dedicated hardware for all instances.
C. Select the largest instance option available in order to pay for only one instance.
D. Make use of elastic services and scale on demand.
Which Dockerfile yields the most predictable builds?
A.

B.

C.

D.

Refer to the exhibit. A distributed application contains data services that connect to databases via JDBC and to other remote services via HTTP. The overall response time is too long, and AppDynamics is used to investigate the root cause. From the application flow map, a specific data service running on Docker has been identified whose response time is over 10 seconds. Which action resolves the issue?
A. Change from a JDBC call to a HTTP call to retrieve data faster
B. Run the AccountProfileMySQL service in Kubernetes
C. Explore the JDBC queries looking for optimization opportunities
D. Verify if the Docker container running MySQL is limiting CPU utilization
Which two elements help to secure your API keys? (Choose two.)
A. ramdomness
B. SHA1
C. triple AES
D. rotation
E. dictionary
Refer to the exhibit. The IT team is creating a new design for a logging system. The system must be able to collect logs from different components of the infrastructure using the SNMP protocol. When the data is collected it will need to be presented in a graphical UI to the NOC team. What is the architectural component that needs to be placed in the unlabeled box to complete this design?
A. message queue
B. web server
C. log parser
D. time-series database
A DevOps engineer is supporting a containerized application with multiple components running across the Kubernetes cluster. Metrics from the container (CPU and memory) and application (requests per second and heap size) are being collected by Prometheus and displayed with Grafana. Users report transaction timeout problems with the application, but the metric graphs all look within normal levels. Which type of failure would prevent the engineer from seeing the problem using the captured metrics?
A. Grafana has lost connectivity to Prometheus, which causes graphs to display only the cached data.
B. CPU and memory metrics from Kubernetes nodes are not accurate due to the way that containers share resources.
C. Some containers are crashing regularly and being restarted automatically by Kubernetes.
D. The metricbeat agent has crashed and is no longer sending new data to Prometheus, so the metrics are not updating.
Refer to the exhibit. An organization has issues with code-based failures after implementing a CI/CD pipeline to automate the builds and deployment phases of an application. Which action must be added to the pipeline, after the application is deployed in the staging environment to minimize failures and to ensure a successful continuous deployment?
A. Restructuring and monitoring tests must be run after it is promoted to production
B. Restructuring and monitoring tests must be run before it is promoted to production
C. Functional and nonfunctional tests must be run after it is promoted to production
D. Functional and nonfunctional tests must be run before it is promoted to production
Refer to the exhibit. How does the architecture respond to a usage spike?
A. The monitoring software instructs the Orchestrator to increase the count of containers and to configure the load balancer accordingly
B. The database prioritizes quick and immediate queries over complicated ones to reduce the request queue
C. The Orchestrator increases the resources assigned to containers to increase performance
D. The load balancer interacts with the Orchestrator to optimize the balancing algorithm to match the incoming flow of requests
A user wants to deploy a new service to a Kubernetes cluster. Which two commands accomplish this goal? (Choose two.)
A. Apply
B. Install
C. Deploy
D. Create
E. Expose
FILL BLANK - Fill in the blanks to complete the statement. When creating multiple containers, in order to allow communication with each other, you must create a __________ of type _________ .
Which type of testing should be integrated into a CI/CD pipeline to ensure the correct behavior of all of the modules in the source code that were developed using TDD?
A. soak testing
B. unit testing
C. load testing
D. volume testing
A precheck validation is being designed for the network state in a Cl/CD pipeline This design requires: • the CI/CD pipeline to spin up test instances. • instances must be used to validate changes. • changes must be validated prior to a continuous deployment workflow, and • then push the changes to production How should the pipeline target the required environment?
A. Use separate CI servers for each environment
B. Use different pipelines for each environment
C. Use separate Git repositories for each environment
D. Use different inventory files for each environment
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?
A. Add a step to run the debug ip routing command before the change, and add a step after the change to issue the no debug ip routing command.
B. Add a step to capture the routing table before the change, and add a step after the change to capture it again. Calculate the difference between the two for review.
C. Add a step to ping a host on each of the static routes before the change, and a step after to repeat the same check. Calculate the difference between the two checks for review.
D. Add a step to run the same playbook again with the debug option enabled and use grep on the log output to ensure that the commands are not applied again.
A DevOps engineer must build a Docker image to containerize an application. Then the image must be pushed to a repository on Docker Hub in a CI/CD pipeline using GitHub Actions. Which approach securely encrypts the Docker Hub access token as an environment variable within the CI/CD pipeline?
A. Store the access token with GitHub environment variables
B. Store the access token with GitHub encrypted secrets
C. Store the access token in an environment file in the repository
D. Hard code the access token in the repository with Base64 encoding
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
A. EXPOSE 8080
B. FIREWALL ADD-PORT 8080
C. PORT 8080
D. OPEN PORT 8080
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
A. node
B. app
C. agent
D. tier
E. event
How does eliminating hardcoded or default passwords help to secure an environment?
A. helps by enforcing your password in a repository and storing it in a secure vault
B. helps to manage passwords centrally
C. helps penetration testing team to focus on other issues more efficiently
D. helps by removing back doors in your environments
A DevOps engineer must validate the working state of the network before implementing a CI/CD pipeline model. Which configuration management tool is designed to accomplish this?
A. Jenkins
B. Genie CLI
C. Travis CI
D. Python YAML data libraries
Which Docker command is used to start an interactive Bash shell in a running container named "test"?
A. docker attach -it test /bin/bash
B. docker run -it test /bin/bash
C. docker exec -it test /bin/bash
D. docker run test /bin/bash
Refer to the exhibit. What is the user doing with Drone in this automated test?
A. testing Alpine Linux versus Ubuntu Linux
B. testing a PostgreSQL DB against multiple architectures
C. testing only the amd64 architecture
D. testing PostgreSQL deployment in an Alpine Linux VM
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to create a Terraform configuration that builds the network environment for a multitier software application. More EPG, Contract, and Filter definitions have been removed from the code.
Refer to the exhibit. A Python script implements a logger server. The log receives a message from Base that contains this text: TextMessage. How is the log formatted?
A. Base Alter: TextMessage
B. Undefined: TextMessageBase
C. TextMessage -> Base
D. TextMessage -> Alter Base
An IT team plans to deploy a new service built on top of an existing service. The capacity needed for the new service is difficult to estimate because the demand for the new service is undetermined. The team has these deployment requirements: • A subset of the users of the original service must be migrated to the new service based on their profile • The new service must be rolled back easily if capacity exceeds estimates Which deployment strategy must be used?
A. rolling
B. blue/green
C. geolocation
D. canary
Which Kubernetes object ensures that each node is limited to running no more than one pod?
A. UniCast
B. Deployment
C. DaemonSet
D. ReplicaSet
Which Dockerfile produces an efficient image rebuild when the exposed port Python dependency, or MyApp source code is modified?
A.

B.

C.

D.

Which two actions help limit the attack surface of your Docker container? (Choose two.)
A. Run only a single service in each container.
B. Run all services in a single image.
C. Use version tags for base images and dependencies.
D. Use Kali Linux as a base image.
E. Download images over HTTPS supporting sites.
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
A. encode the value with base64 in a secure DNS CTEXT entry
B. as an environment variable in the Dockerfile
C. Docker environment variable
D. Docker secrets
An interface on a router as a Layer 3 link has been configured to another device by updating an Ansible playbook that is executed via a CI/CD pipeline. The Ansible playbook was written to push the configuration change using the ios_config module. Which automated test validates that the interface is functioning as it should?
A. Add a pipeline step that runs the playbook a second type. If it does not modify the device on the second run, then the interface is correctly configured.
B. Automated testing is already built in because the playbook execution is successful only after Ansible validates that it applied the change.
C. Add a pipeline step that captures and parses the packet flow for the interface.
D. Add a pipeline step that captures and parses the show ip interface output so that the operational state can be referenced.
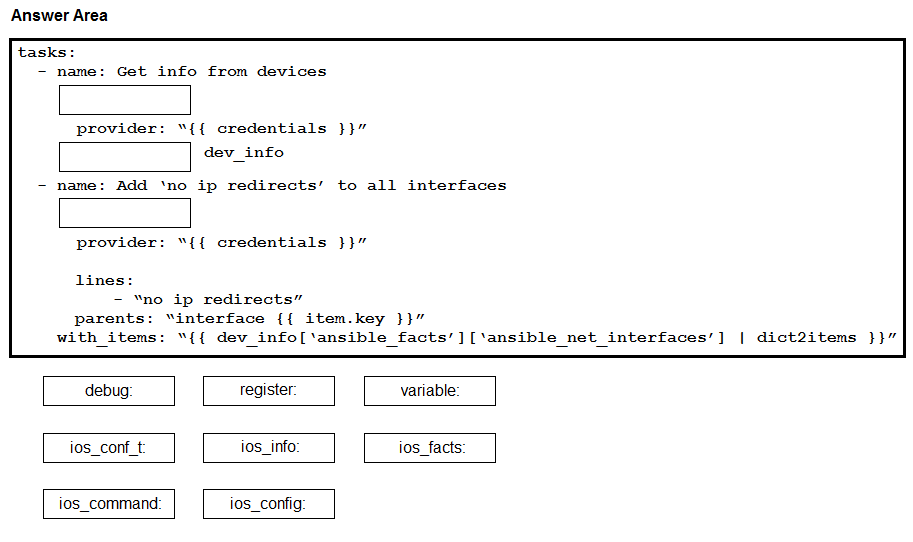
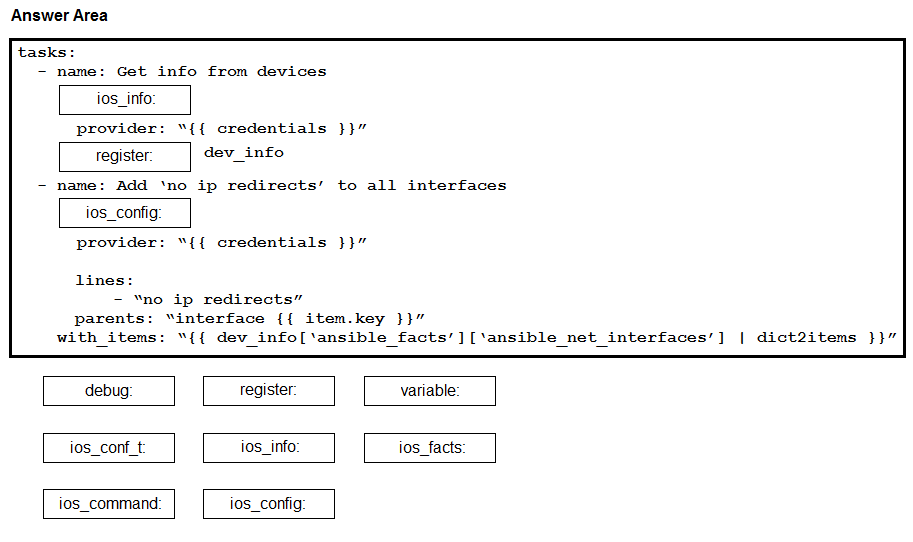
DRAG DROP - Construct an Ansible script to gather information about target routers and then use it to apply no ip redirects to every interface on each device. Drag and drop the code from the bottom onto the correct location in the exhibit to complete the tasks section of the Ansible playbook so that it accomplishes your goal. Select and Place:
Refer to the exhibit. The text represents a syslog message sent from a Linux server to a centralized log system. Based on the format of the log message, how must the functionality of the log parser be extended to improve search capabilities?
A. Reverse lookup the IP address to add a hostname field
B. Convert the date to the time zone of the system
C. Configure the Linux machine to add a UID field to messages
D. Filter out the text of the message to speed up searches
Which step must be taken to enable centralized logging in a Kubernetes environment?
A. No steps need to be taken. The master node automatically aggregates logs from all worker nodes and stores them on the specified persistent volume.
B. Create a CustomResourceDefinition in each deployment that specifies the IP or names the log collector.
C. Deploy a sidecar node that aggregates logs from the entire cluster.
D. Create a DaemonSet that deploys a container with a logging agent on every node in the cluster.
Which two practices help make the security of an application a more integral part of the software development lifecycle? (Choose two.)
A. Add a step to the CI/CD pipeline that runs a dynamic code analysis tool during the pipeline execution.
B. Add a step to the CI/CD pipeline that runs a static code analysis tool during the pipeline execution.
C. Use only software modules that are written by the internal team.
D. Add a step to the CI/CD pipeline to modify the release plan so that updated versions of the software are made available more often.
E. Ensure that the code repository server has enabled drive encryption and stores the keys on a Trusted Platform Module or Hardware Security Module.
Refer to the exhibit. Which CI solution uses this file?
A. Drone
B. GitLab CI
C. Travis CI
D. Jenkins
DRAG DROP - Drag and drop the code from the bottom onto the box where the code is missing to post a message to a Cisco Webex space. Not all options are used.
An IT department needs to deploy a new application named ‘Entfin434772390’ across the entire enterprise. The deployment must gradually transfer user traffic from an on older and nearly identical version of the application named ‘Entfin02754932l’. Both versions of the application are running in the production environment. Which release strategy should be used by the IT department?
A. agile
B. canary
C. rollbacks
D. blue/green
DRAG DROP -Refer to the exhibit. A developer is creating a health check monitoring script that queries information from the Cisco DNA Center platform. The script must trigger an alert if a site health statistic named accessGoodCount drops below 80 and if a network statistic named latestHealthScore is 95 or less. Drag and drop the code snippets from the bottom onto the blanks in the code to monitor the site and network health on a Cisco DNA Center platform instance. Options may be used more than once. Not all options are used.
DRAG DROP - Drag and drop the steps in Gartner's public cloud cost management framework from the left into the order on the right.
What is the purpose of using sysprep when developing a Microsoft Windows-based golden image process?
A. prepares a new host to accept a hard drive image built on another machine
B. removes all host-specific information and components from the local machine
C. installs all the latest security patches and OS updates to the local machine
D. writes the local hard drive image to an ISO file that can be deployed to another machine
Refer to the exhibit. A docker-compose.yml file implements a postgres database container. Which .gitlab-ci.yml code block checks the health status of the container and stops the pipeline if the container is unhealthy?
A.

B.

C.

D.

Access Full 300-910 Dump Free
Looking for even more practice questions? Click here to access the complete 300-910 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 300-910 dump free questions — and get one step closer to exam success!