300-820 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 300-820 certification? Take your preparation to the next level with our 300-820 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 300-820 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 300-820 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
A remote financial institution is implementing email encryption. It is required that all inbound emails use SMTP over TLS. What must be done to accomplish this?A. Disable TLS certificates.
B. Utilize Cisco Registered Envelope Service.
C. Leverage Cisco Talos Threat Intelligence Group.
D. Enable Application Inspection and Control for SMTP.
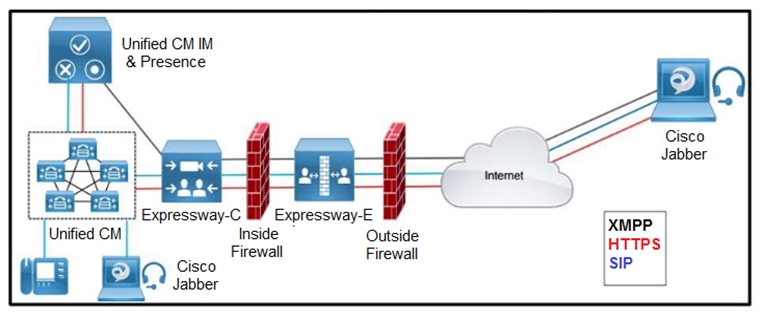
Refer to the exhibit. Which inbound connection should an administrator configure on the outside firewall?A. Media: UDP 36000 to 36011
B. XMPP: TCP 5222
C. SIP: TCP 5061
D. HTTPS (tunneled over SSH between C and E): TCP 2222
Which action must be taken before a custom quarantine that is being used can be deleted?A. Delete the quarantine that is assigned to a filter.
B. Delete the quarantine that is not assigned to a filter.
C. Delete only the unused quarantine.
D. Remove the quarantine from the message action of a filter.
Refer to the exhibit. For improved security, an administrator wants to warn users about opening any links or attachments within an email. How must the administrator configure an HTML-coded message at the top of an email body to create this warning?A. Create a text resource type of Notification Template, change to code view to paste the HTML code into the text box, then use this text resource inside a content filter.
B. Create a text resource type of Disclaimer Template, change to code view to paste the HTML code into the text box, then use this text resource inside a content filter.
C. Create a text resource type of Disclaimer Template, past the HTML code into the text box, then use this text resource inside a content filter.
D. Create a text resource type of Notification Template, past the HTML code into the text box, then use this text resource inside a content filter.
A Webex engineer is configuring SSO in Control Hub with Active Directory Federation Services. The engineer wants to authenticate users for all the applications that they are given rights to. The engineer also wants to eliminate further prompts when users switch applications during a particular session. Which action tells ADFS the fields to map to Webex to identify a user?A. Send LDAP attributes as claims.
B. Create claim rules for Webex authentication
C. Add a relying party trust to the ADFS.
D. Map the E-mail-addresses LDAP attribute to the uid outgoing claim type.
A network administrator notices that there are a high number of queries to the LDAP server. The mail logs show an entry “550 Too many invalid recipients | Connection closed by foreign host.”
Which feature must be used to address this?A. DHAP
B. SBRS
C. LDAP
D. SMTP
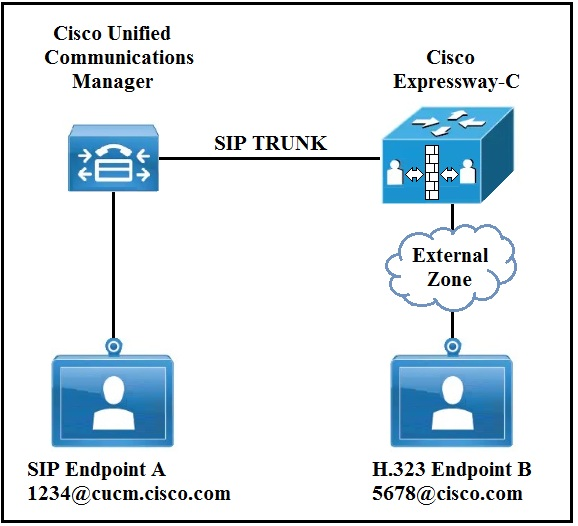
Refer to the exhibit. In an environment SIP devices are registered to CUCM and H.323 devices to VCS.
What would be required to enable these calls to setup correctly?A. Create a presearch transform.
B. Change the domain of SIP endpoint A to cisco.com.
C. Disable SIP in the external zone.
D. Change the interworking mode to On.
Which setting affects the aggressiveness of spam detection?A. protection level
B. spam threshold
C. spam timeout
D. maximum depth of recursion scan
Which type of attack is prevented by configuring file reputation filtering and file analysis features?A. denial of service
B. zero-day
C. backscatter
D. phishing
What is the last step for domain management in Cisco Webex Control Hub if an engineer adds users already signed in with the company domain?A. Publish a domain.
B. Add a domain.
C. Verify a domain.
D. Claim a domain.
Which zone is required between Expressway-E and Expressway-C in Mobile and Remote Access deployments?A. Unified Communications traversal zone
B. neighbor zone
C. DNS zone
D. traversal zone
What is the purpose of a transform in the Expressway server?A. A transform has the function as a neighbor zone in the Expressway. It creates a connection with another server.
B. A transform changes the audio codec when the call goes through the Expressway.
C. A transform is used to route calls to a destination.
D. A transform changes an alias that matches certain criteria into another alias.
Which complication does a NAT introduce in SDP for a SIP call?A. Additional headers due to NAT encapsulation can cause the packet size to exceed the MTU.
B. When the client is behind a NAT they may be unable to determine the appropriate offset due to time zones.
C. The IP address specified in the connection data field may be an unrouteable internal address.
D. The encryption keys advertised in the SDP are only valid for clients not behind a NAT.
Which commands disable SIP Inspection on the Cisco ASA FirePOWER firewall?A. hostname#no inspect sip
B. hostname(config)#policy-map global_policyhostname(config-pmap)#class-map inspection defaulthostname(config-pmap)#no inspect_sip
C. hostname(config)#no inspect_sip
D. hostname(config)#policy-map global_policyhostname(config-pmap)#class-map inspection_defaulthostname(config-pmap)#no inspect sip
Refer to the exhibit. When Expressway-E routes a call with URI
4040@uclab.local
to a DNS zone, which DNS server does the Expressway query for the SIP SRV records?A. 10.20.20.20
B. 10.10.10.10
C. 10.40.40.40
D. 10.30.30.30
An Expressway pairs deployed for Mobile and Remote Access. An administrator installs a new server certificate on the Expressway-E. After installing the new certificate, the UC Traversal zone between Expressway-C and Expressway-E is active. Still, Jabber Mobile and Remote Access clients cannot log in over the Expressway. The certificate Common Name is the FQDN of Expressway-E, “expe01 example.com”, and the certificate contains no additional names. Which Subject Alternate Name must be added to the certificate to allow Jabber Mobile and Remote Access clients to log in successfully?A. FQDN of the Expressway-C, “expc01.example.local”
B. registration domain, “example.com” or “collab-edge.example.com”
C. Cisco UCM cluster FQDN, “cucmcluster.example.local”
D. FQDN of the Expressway-E, “expe01.example.com”
When the network requirements are configured for a new Video Mesh deployment, which firewall ports are required so that Video Mesh cascade signaling succeeds?A. TCP 443 and 444
B. TCP 443 and 8443
C. UDP 5004 and 5005
D. UDP 33432 through 33433
Which two steps are needed to disable local spam quarantine before external quarantine is enabled? (Choose two.)A. Uncheck the Enable Spam Quarantine check box.
B. Select Monitor and click Spam Quarantine.
C. Check the External Safelist/Blocklist check box.
D. Select External Spam Quarantine and click on Configure.
E. Select Security Services and click Spam Quarantine.
Which antispam feature is utilized to give end users control to allow emails that are spam to be delivered to their inbox, overriding any spam verdict and action on the Cisco ESA?A. end user allow list
B. end user spam quarantine access
C. end user passthrough list
D. end user safelist
Jabber cannot log in via Mobile and Remote Access. You inspect Expressway-C logs and see this error message:
XCP_JABBERD Detail="Unable to connect to host '%IP%', port 7400:(111) Connection refused"
Which is the cause of this issue?A. Rich Media Session licenses are not activated on Expressway-E.
B. Expressway-E is listening on the wrong IP interface.
C. The destination port for Expressway-E is set to 7400 instead of 8443 on the Expressway-C.
D. The XCP Service is not activated on Expressway-E.
Refer to the exhibit. Which configuration allows the Cisco ESA to scan for executables inside the zip and apply the action as per the content filter?A. Modify the content filter to look for .exe filename instead of executable filetype.
B. Configure the recursion depth to a higher value.
C. Configure the maximum attachment size to a higher value.
D. Modify the content filter to look for attachment filetype of compressed.
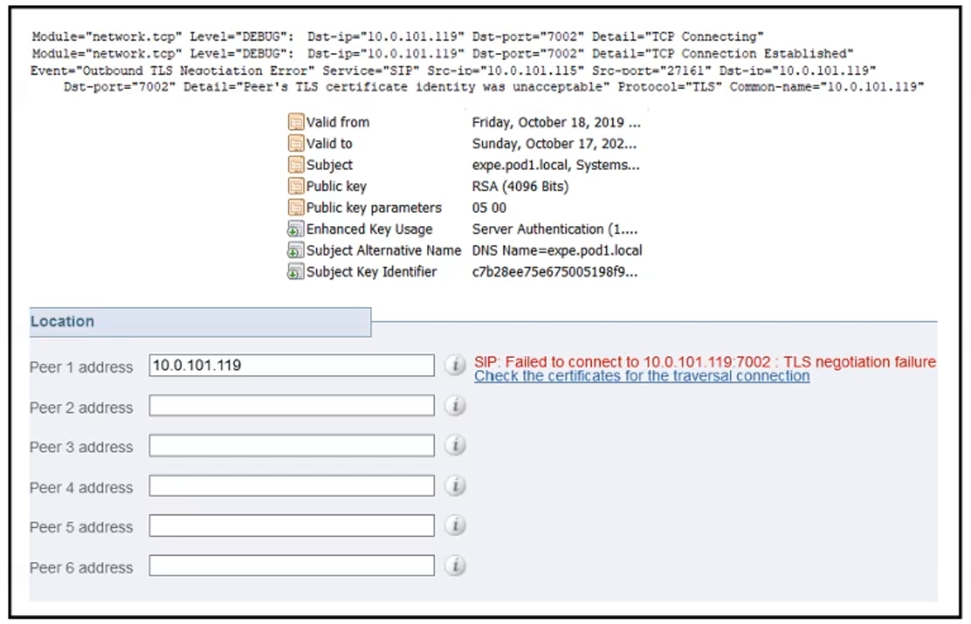
Refer to the exhibit showing logs from the Expressway-C, a copy of the Expressway-E certificate, and the UC traversal zone configuration for the Expressway-C.
An office administrator is deploying mobile and remote access and sees an issue with the UC traversal zone. The zone is showing `TLS negotiation failure`. What is causing this issue?A. The Expressway-E certificate includes the Expressway-C FQDN as a SAN entry
B. The Expressway-C is missing the FQDN of Cisco UCM in the Common Name of its certificate
C. In the UC Traversal Zone on the Expressway-C, the peer address is set to the IP of the Expressway-E, which is not a SAN entry in the Expressway-E certificate
D. The Expressway-E does not have the FQDN of Cisco UCM listed as a SAN in its certificate
Between which two DTMF relay methods does the Expressway support interworking? (Choose two.)A. unsolicited notify
B. RFC 2833
C. KPML
D. passthrough
E. H.245 user input indication
Cisco Collaboration endpoints are exchanging encrypted signaling messages.
What is one major complication in implementing NAT ALG for voice and video devices?A. Internal endpoints cannot use addresses from the private address space.
B. The NAT ALG cannot inspect the contents of encrypted signaling messages.
C. NAT ALG introduces jitter in the voice path.
D. Source addresses cannot provide the destination addresses that remote endpoints should use for return packets.
An administrator notices that the Cisco ESA delivery queue is consistently full. After further investigation, it is determined that the IP addresses currently in use by the Cisco ESA are being rate-limited by some destinations. The administrator creates a new interface with an additional IP address using virtual gateway technology, but the issue is not solved. Which configuration change resolves the issue?A. Use the CLI command alt-src-host to set the new interface as a possible delivery candidate.
B. Use the CLI command loadbalance auto to enable mail delivery over all interfaces.
C. Use the CLI command deliveryconfig to set the new interface as the primary interface for mail delivery.
D. Use the CLI command altsrchost to set the new interface as the source IP address for all mail.
What is a requirement when configuring the Cisco Webex Hybrid Message account for accessing the API of the Cisco UCM IM and Presence Service?A. Add a new end-user with the ג€Standard AXL API Accessג€ role
B. Use an application user with only the ג€Standard CTI Allow Control of All Devicesג€ role
C. Use an application user not the main administrator account with the ג€Standard AXL API Accessג€ role
D. Use the main administrator account if it includes the ג€Standard AXL API Accessג€ role
Spammers routinely try to send emails with the recipient field filled with a list of all possible combinations of letters and numbers. These combinations, appended with a company’s domain name are malicious attempts at learning all possible valid email addresses. Which action must be taken on a Cisco ESA to prevent this from occurring?A. Quarantine external authentication queries.
B. Enable end user safelist features.
C. Perform LDAP acceptance validation.
D. Select the SMTP Authentication Query checkbox.
How do the Cisco Expressway-C and Expressway-E servers transmit media to each other?A. RTP and RTCP are multiplexed for all internal and external video endpoints across the traversal link using UDP.
B. When the Expressway-C receives RTP and RTCP media, it establishes a new UDP socket with the Expressway-E.
C. RTP and RTCP are multiplexed for all internal and external video endpoints across the traversal link using TLS.
D. When the Expressway-E receives RTP and RTCP media, it establishes a new UDP socket with the Expressway-C.
An analyst creates a new content dictionary to use with Forged Email Detection.
Which entry will be added into the dictionary?A. mycompany.com
B. Alpha Beta
C. ^Alpha Beta$
D. Alpha.Beta@mycompany.com
Which step is required when configuring cloud and hybrid deployments for Cisco Jabber?A. Add the Jabber user to Cisco Unity Connection.
B. Add the Jabber user to Expressway-E.
C. Add the Jabber user to Expressway-C.
D. Add Jabber Users to the Cisco Webex Administration Tool.
To comply with a recent audit, an engineer must configure anti-virus message handling options on the incoming mail policies to attach warnings to the subject of an email.
What should be configured to meet this requirement for known viral emails?A. Virus Infected Messages
B. Unscannable Messages
C. Encrypted Messages
D. Positively Identified Messages
Which two are configured in the DMARC verification profile? (Choose two.)A. name of the verification profile
B. minimum number of signatures to verify
C. ESA listeners to use the verification profile
D. message action into an incoming or outgoing content filter
E. message action to take when the policy is reject/quarantine
Within which cache timeline do the Webex App endpoints perform a STUN test to calculate round-trip delay time to available media node clusters?A. 1 hour
B. 2 hours
C. 4 hours
D. 6 hours
Which statement about scheduling Expressway backups is true?A. It is not supported on the application.
B. It is allowed from the application CLI of the Expressway only.
C. It is allowed from the application CLI and GUI of the Expressway.
D. It is allowed from the application GUI of the Expressway only.
DRAG DROP
-
Drag and drop the services from the left onto their descriptions on the right. Some services are used more than once.

Which suboption must be selected when LDAP is configured for Spam Quarantine End-User Authentication?A. Designate as the active query
B. Update Frequency
C. Server Priority
D. Entity ID
An engineer is configuring Cisco Expressway-E and needs to implement toll fraud prevention. Which configuration meets this requirement?A. Enable SIP ALG inspection on the network address translation firewall.
B. Enable and configure local call policy.
C. Enable and configure the Expressway-E firewall.
D. Configure the external firewall to block specific IPs.
What is a benefit of deploying Cisco SMA?A. centralized management of logs for Cisco ESA appliances
B. centralized management of botnet directories
C. centralized management of software updates for Cisco ESA appliances
D. centralized management of quarantined email
A network administrator is modifying an outgoing mail policy to enable domain protection for the organization. A DNS entry is created that has the public key.
Which two headers will be used as matching criteria in the outgoing mail policy? (Choose two.)A. message-ID
B. sender
C. URL reputation
D. from
E. mail-from
An engineer is deploying Mobile and Remote Access to allow external Cisco Jabber users to sign into a Cisco UCM cluster via Cisco Expressways. The users will sign-in in the format
username@cisco.com
. Contact photos for Jabber are hosted on a webserver with the FQDN of phonebook cisco.com. Which configuration must be completed to allow external Jabber users to see contact photos?A. An HTTP allow list entry must be made on the Expressway-E for phonebook cisco.com.
B. A SIP allow list entry must be made on the Expressway-E for .*@cisco.com.
C. An HTTP allow list entry must be made on the Expressway-C for phonebook cisco.com.
D. A SIP allow list entry must be made on the Expressway-C for .*@cisco.com.
DRAG DROP
-
Drag and drop the required SAN field items from the left onto the features within the server categories on the right.

Cisco Collaboration deployment has video endpoints that can do B2B calls over the internet, but they also can make audio calls through a gateway. This ability means that someone from the internet can make fraud calls through the system. Which action must an engineer take to set up the search rules for calls that are being headed to the PSTN gateway?A. Ensure that only requests that are authenticated are allowed to make a PSTN call.
B. Avoid using any wild card in the source settings in the search rules.
C. Add registered devices only in the search rule for the PSTN gateway.
D. Add registered devices only in the zone for the PSTN gateway.
When email authentication is configured on Cisco ESA, which two key types should be selected on the signing profile? (Choose two.)A. DKIM
B. Public Keys
C. Domain Keys
D. Symmetric Keys
E. Private Keys
Which connection does the traversal zone configuration define?A. Expressway-E and Collaboration Endpoints
B. Cisco UCS E-Series and Cisco UCM
C. Cisco UC and Cisco Unified Presence Server
D. Cisco Expressway-C and Cisco Expressway-E platforms
What must be configured to allow the Cisco ESA to encrypt an email using the Cisco Registered Envelope Service?A. provisioned email encryption profile
B. message encryption from a content filter that select "Message Encryption" over TLS
C. message encryption from the mail flow policies with "CRES" selected
D. content filter to forward the email to the Cisco Registered Envelope server
Which action is required when using Cisco Jabber for Cloud with Cisco Webex Messenger?A. Configure, extend, and connect.
B. Configure policies.
C. Configure service discovery for remote access.
D. Configure desk phone control.
Which two statements about Expressway media traversal are true? (Choose two.)A. Expressway Control is the traversal server installed in the DMZ.
B. The Expressway Edge must be put in a firewall DMZ segment.
C. Cisco Unified Communications Manager zone can be either traversal server or client.
D. The Unified Communications traversal zone can be used for Mobile and Remote Access.
E. Both Expressway Edge interfaces can be NATed.
Which feature must be configured before an administrator can use the outbreak filter for nonviral threats?A. quarantine threat level
B. antispam
C. data loss prevention
D. antivirus
When deploying an Expressway Core and Expressway Edge cluster for mobile and remote access, which TLS verity subject name must be configured on the
Expressway-E UC traversal zone?A. Webex CUSP Cluster Name
B. Expressway-E Cluster Name
C. Cisco Unified Communications Manager Publisher FQDN
D. Expressway-C Cluster Name
An administrator is configuring a new Cisco Webex Hybrid Message Service deployment, and the Expressway-C Message Connector is successfully registered in the Control Hub. After the server information of the IM and Presence server is added to the Expressway-C, an error “Connectivity to IM and Presence AXL Service could not be established” is displayed in the Control Hub. The Cisco AXL Web Service is enabled on the IM and Presence Service publisher, and the main administrator account enabled for AXL API permission is being used. Which configuration change must be made to resolve this error?A. Enable the Cisco AXL Web Service on the Control Hub
B. Enable the Cisco AXL Web Service on the Expressway-C Message Connector
C. Enable an End User account for AXL.API permissions on the IM and Presence Service publisher
D. Enable a second administrator account for AXL API permissions on the IM and Presence Service publisher
Free Access Full 300-820 Practice Exam Free
Looking for additional practice? Click here to access a full set of 300-820 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 300-820 certification journey!