300-735 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 300-735 exam? Start with our 300-735 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 300-735 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 300-735 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
Refer to the exhibit. A security engineer created a script and successfully executed it to retrieve all currently open alerts. Which print command shows the first returned alert?
A. print(response[data][0])
B. print(response[results][0])
C. print(response.json()[data][0])
D. print(response.json()[results][0])
What are two benefits of Ansible when managing security platforms? (Choose two.)
A. End users can be identified and tracked across a network.
B. Network performance issues can be identified and automatically remediated.
C. Policies can be updated on multiple devices concurrently, which reduces outage windows.
D. Anomalous network traffic can be detected and correlated.
E. The time that is needed to deploy a change is reduced, compared to manually applying the change.
Which description of synchronous calls to an API is true?
A. They can be used only within single-threaded processes.
B. They pause execution and wait for the response.
C. They always successfully return within a fixed time.
D. They can be used only for small requests.
Which two URI parameters are needed for the Cisco Stealthwatch Top Alarm Host v1 API? (Choose two.)
A. startAbsolute
B. externalGeos
C. tenantId
D. intervalLength
E. tagID
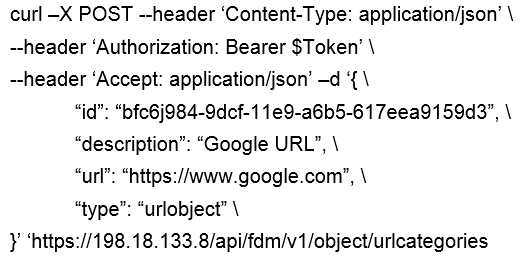
Refer to the exhibit. What is the purpose of the API represented by this URL?
A. Getting or setting intrusion policies in FMC
B. Creating an intrusion policy in FDM
C. Updating access policies
D. Getting the list of intrusion policies configured in FDM
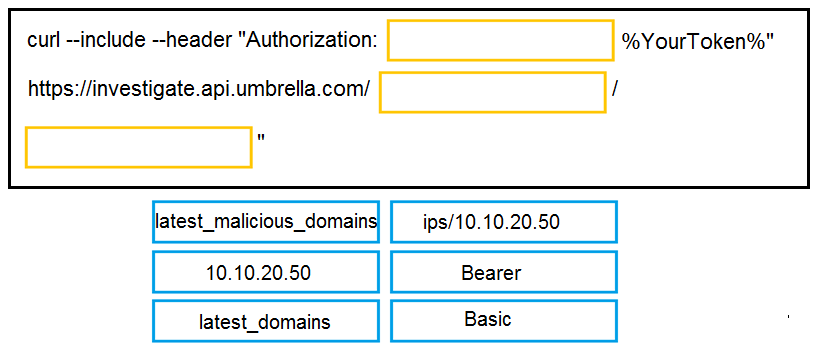
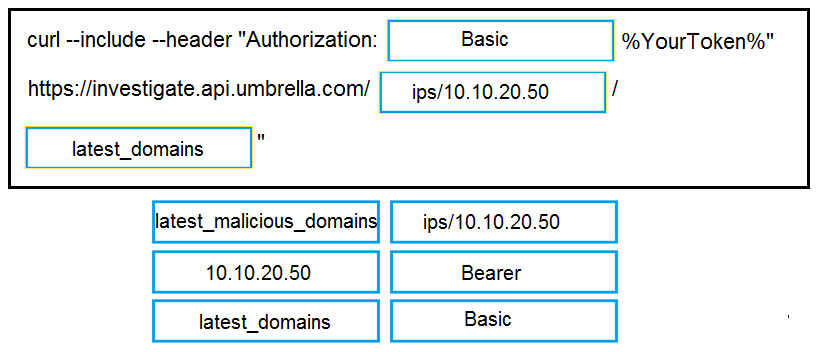
DRAG DROP - Drag and drop the code to complete the curl query to the Cisco Umbrella Investigate API for the Latest Malicious Domains for the IP address 10.10.20.50. Not all options are used. Select and Place:
Which two statements describe the characteristics of API styles for REST and RPC? (Choose two.)
A. REST-based APIs function in a similar way to procedures.
B. REST-based APIs are used primarily for CRUD operations.
C. REST and RPC API styles are the same.
D. RPC-based APIs function in a similar way to procedures.
E. RPC-based APIs are used primarily for CRUD operations.
What are two capabilities of Cisco Firepower Management Center eStreamer? (Choose two.)
A. eStreamer is used to get sources for intelligence services.
B. eStreamer is used to send malware event data.
C. eStreamer is used to get a list of access control policies.
D. eStreamer is used to send policy data.
E. eStreamer is used to send intrusion event data.
Refer to the exhibit. A network operator wrote a Python script to retrieve events from Cisco AMP.Against which API gateway must the operator make the request?
A. BASE_URL = “https://api.amp.cisco.com”
B. BASE_URL = “https://amp.cisco.com/api”
C. BASE_URL = “https://amp.cisco.com/api/”
D. BASE_URL = “https://api.amp.cisco.com/”
For which two programming languages does Cisco offer an SDK for Cisco pxGrid 1.0? (Choose two.)
A. Python
B. Perl
C. Java
D. C
E. JavaScript
Which curl command lists all tags (host groups) that are associated with a tenant using the Cisco Stealthwatch Enterprise API?
A. curl -X PUT”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/{tenant_id}/tags
B. curl -X POST -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/tags
C. curl -X GET -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/{tenant_id}/tags
D. curl -X GET -H”Cookie:{Cookie Data}”https://{stealthwatch_host}/smc-configuration/rest/v1/tenants/tags
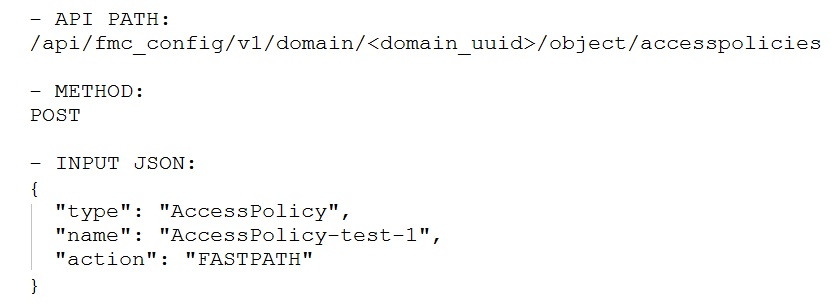
When the URI "/api/fmc_config/v1/domain/e276abec-e0f2-11e3-8169-6d9ed49b625f/policy/accesspolicies" is used to make a POST request, what does "e276abec-e0f2-11e3-8169-6d9ed49b625f" represent?
A. API token
B. domain UUID
C. access policy UUID
D. object UUID
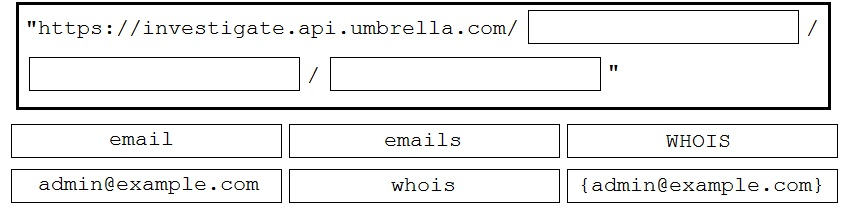
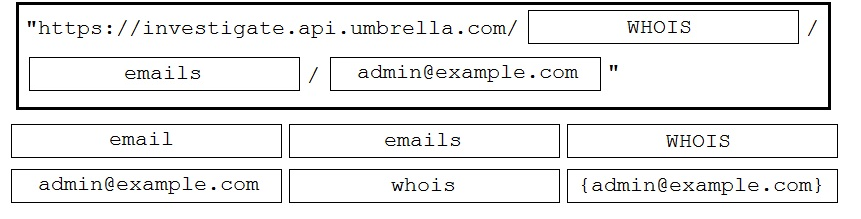
DRAG DROP - Drag and drop the code to complete the Cisco Umbrella Investigate WHOIS query that returns a list of domains that are associated with the email address " admin@example.com ". Not all options are used. Select and Place:
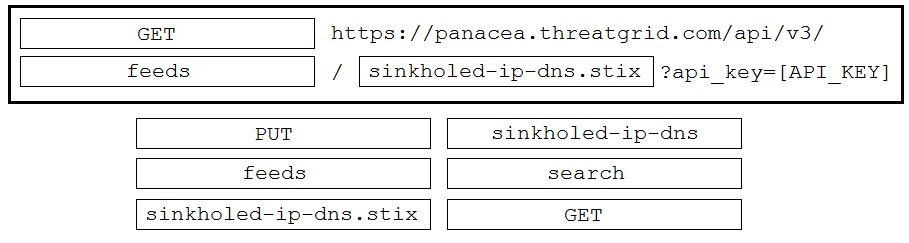
DRAG DROP - Drag and drop the items to complete the ThreatGRID API call to return a curated feed of sinkholed-ip-dns in stix format. Not all options are used. Select and Place:
Which API capability is available on Cisco Firepower devices?
A. Firepower Management Center – Sockets API
B. Firepower Management Center – eStreamer API
C. Firepower Management Center – Camera API
D. Firepower Management Center – Host Output API
Which header set should be sent with all API calls to the Cisco Stealthwatch Cloud API? A.B.
C.
D.
Refer to the exhibit. A Python function named "query" has been developed and the goal is to use it to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs. How is the function called, if the goal is to identify the sessions that are associated with the IP address 10.0.0.50?
A. query(config, secret, “getSessionByIpAddress/10.0.0.50”, “ipAddress”)
B. query(config, “10.0.0.50”, url, payload)
C. query(config, secret, url, “10.0.0.50”)
D. query(config, secret, url, ‘{“ipAddress”: “10.0.0.50”}’)
What is the purpose of the snapshot APIs exposed by Cisco Stealthwatch Cloud?
A. Report on flow data during a customizable time period.
B. Operate and return alerts discovered from infrastructure observations.
C. Return current configuration data of Cisco Stealthwatch Cloud infrastructure.
D. Create snapshots of supported Cisco Stealthwatch Cloud infrastructure.
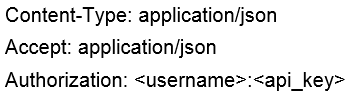
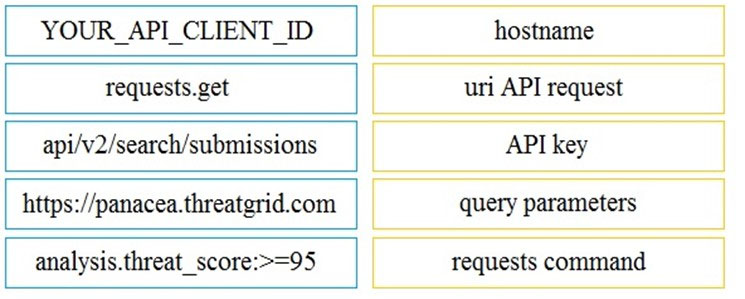
DRAG DROP - Drag and drop the code to complete the script to search Cisco ThreatGRID and return all public submission records associated with cisco.com. Not all options are used. Select and Place:
Refer to the exhibit. The security administrator must temporarily disallow traffic that goes to a production web server using the Cisco FDM REST API. The administrator sends an API query as shown in the exhibit. What is the outcome of that action?
A. The given code does not execute because the mandatory parameters, source, destination, and services are missing.
B. The given code does not execute because it uses the HTTP method “PUT”. It should use the HTTP method “POST”.
C. The appropriate rule is updated with the source, destination, services, and other fields set to “Any” and the action set to “DENY”. Traffic to the production web server is disallowed, as expected.
D. A new rule is created with the source, destination, services, and other fields set to “Any” and the action set to “DENY”. Traffic to the production web server is disallowed, as expected.
Refer to the exhibit. A network operator wants to add a certain IP to a DMZ tag. Which code segment completes the script and achieves the goal? A.
B.
C.
D.
Which request searches for a process window in Cisco ThreatGRID that contains the word "secret"?
A. /api/v2/search/submissions?term=processwindow&title=secret
B. /api/v2/search/submissions?term=processwindow&q=secret
C. /api/v2/search/submissions?term=window&title=secret
D. /api/v2/search/submissions?term=process&q=secret
Refer to the exhibit. Which expression prints the text "802.1x"?
A. print(quiz[0][‘choices’][‘b’])
B. print(quiz[‘choices’][‘b’])
C. print(quiz[0][‘choices’][‘b’][‘802.1x’])
D. print(quiz[0][‘question’][‘choices’][‘b’])
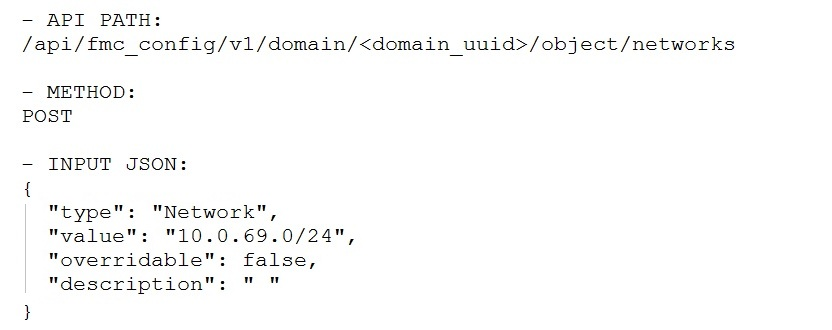
Which snippet is used to create an object for network 10.0.69.0/24 using Cisco Firepower Management Center REST APIs? A.B.
C.
D.
Which two API capabilities are available on Cisco Identity Services Engine? (Choose two.)
A. Platform Configuration APIs
B. Monitoring REST APIs
C. Performance Management REST APIs
D. External RESTful Services APIs
E. Internal RESTful Services APIs
Which two APIs are available from Cisco ThreatGRID? (Choose two.)
A. Access
B. User Scope
C. Data
D. Domains
E. Curated Feeds
Which snippet describes the way to create an URL object in Cisco FDM using FDM REST APIs with curl? A.B.
C.
D.
Which URI string is used to create a policy that takes precedence over other applicable policies that are configured on Cisco Stealthwatch?
A. /tenants/{tenantId}/policy/system/host-policy
B. /tenants/{tenantId}/policy/system/role-policy
C. /tenants/{tenantId}/policy/system
D. /tenants/{tenantId}/policy/system/{policyId}
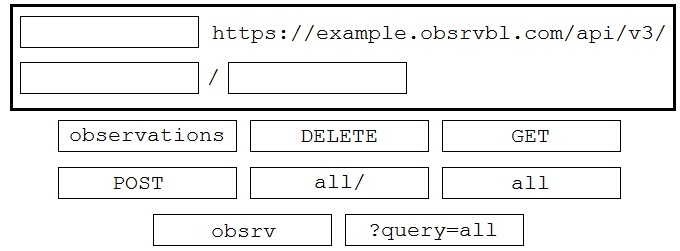
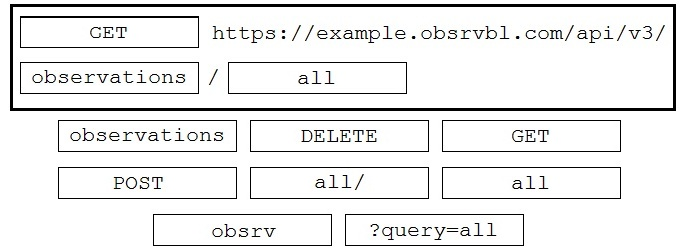
DRAG DROP - Drag and drop the code to complete the API call to query all Cisco Stealthwatch Cloud observations. Not all options are used. Select and Place:
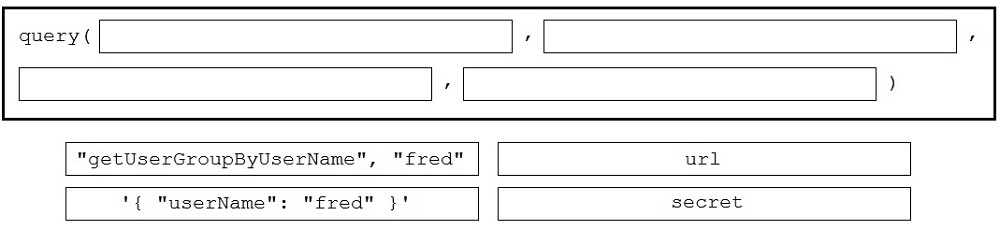
DRAG DROP -Refer to the exhibit. A Python function named "query" has been developed, and will be used to query the service "com.cisco.ise.session" via Cisco pxGrid 2.0 APIs. Drag and drop the code to construct a Python call to the "query" function to identify the user groups that are associated with the user "fred". Not all options are used. Select and Place:
Which step is required by Cisco pxGrid providers to expose functionality to consumer applications that are written in Python?
A. Look up the existing service using the /pxgrid/control/ServiceLookup endpoint.
B. Register the service using the /pxgrid/control/ServiceRegister endpoint.
C. Configure the service using the /pxgrid/ise/config/profiler endpoint.
D. Expose the service using the /pxgrid/ise/pubsub endpoint.
Which two commands create a new local source code branch? (Choose two.)
A. git checkout -b new_branch
B. git branch -b new_branch
C. git checkout -f new_branch
D. git branch new_branch
E. git branch -m new_branch
Refer to the exhibit. What must be present in a Cisco Web Security Appliance before the script is run?
A. reporting group with the name web_malware_category_malware_name_user_detail
B. data for specified dates
C. reporting group with the name blocked_malware
D. data in the queried category
The Cisco Security Management Appliance API is used to make a GET call using the URI /sma/api/v2.0/reporting/mail_incoming_traffic_summary/ detected_amp?startDate=2016-09-10T19:00:00.000Z&endDate=2018-09-24T23:00:00.000Z&device_type=esa&device_name=esa01. What does this GET call return?
A. values of all counters of a counter group, with the device group name and device type for web
B. value of a specific counter from a counter group, with the device name and type for email
C. value of a specific counter from a counter group, with the device name and type for web
D. values of all counters of a counter group, with the device group name and device type for email
Refer to the exhibit. A network operator must generate a daily flow report and learn how to act on or manipulate returned data. When the operator runs the script, it returns an enormous amount of information. Which two actions enable the operator to limit returned data? (Choose two.)
A. Add recordLimit. followed by an integer (key:value) to the flow_data.
B. Add a for loop at the end of the script, and print each key value pair separately.
C. Add flowLimit, followed by an integer (key:value) to the flow_data.
D. Change the startDateTime and endDateTime values to include smaller time intervals.
E. Change the startDate and endDate values to include smaller date intervals.
Refer to the exhibit. A network operator must create a Python script that makes an API request to Cisco Umbrella to do a pattern search and return all matched URLs with category information. Which code completes the script?
A. URL = BASE_URL + “/find/exa[a-z]ple.com” PARAMS = { “categoryinclude” : “true”}
B. URL = BASE_URL + “/find/exa[a-z]ple.com” PARAMS = { “returncategory” : “true”}
C. URL = BASE_URL + “/find/exa[a-z]ple.com” PARAMS = { “includeCategory” : “true”}
D. URL = BASE_URL + “/find/exa[a-z]ple.com” PARAMS = { “returnCategory” : “true”}
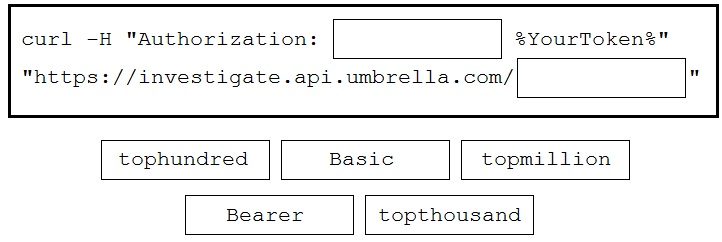
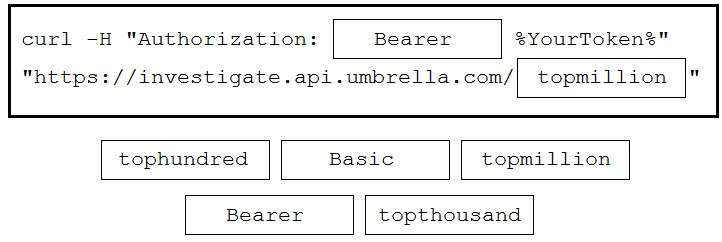
DRAG DROP - Drag and drop the code to complete the curl command to query the Cisco Umbrella Investigate API for the umbrella popularity list. Not all options are used. Select and Place:
What are two advantages of Python virtual environments? (Choose two.)
A. Virtual environments can move compiled modules between different platforms.
B. Virtual environments permit non-administrative users to install packages.
C. The application code is run in an environment that is destroyed upon exit.
D. Virtual environments allow for stateful high availability.
E. Virtual environments prevent packaging conflicts between multiple Python projects.
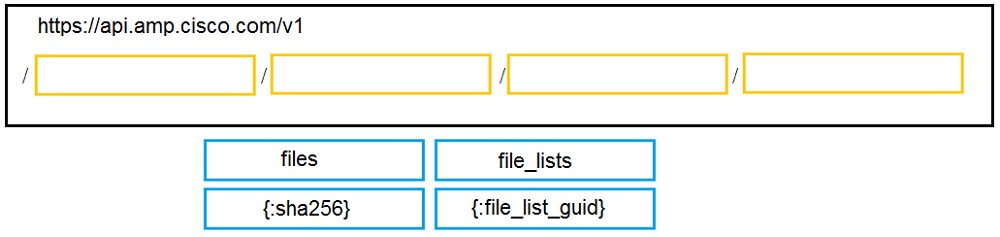
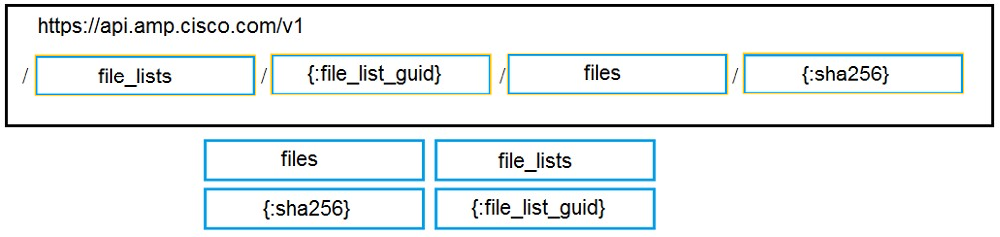
DRAG DROP - Drag and drop the code to complete the URL for the Cisco AMP for Endpoints API POST request so that it will add a sha256 to a given file_list using file_list_guid. Select and Place:
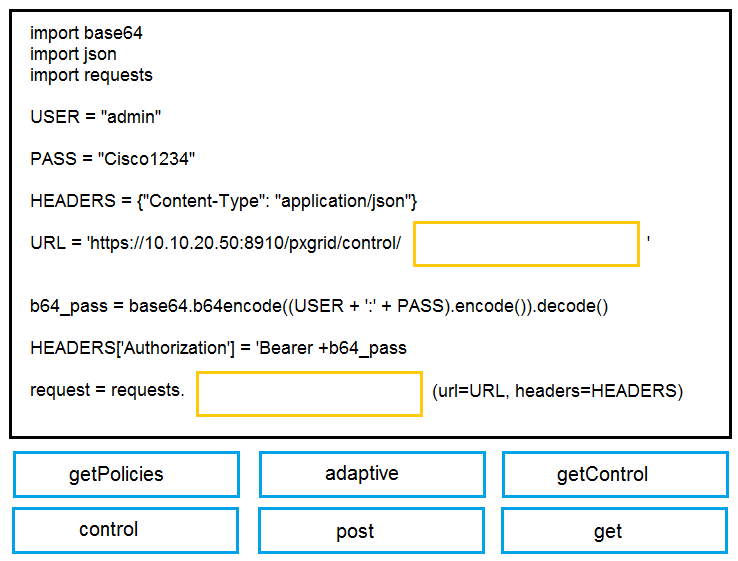
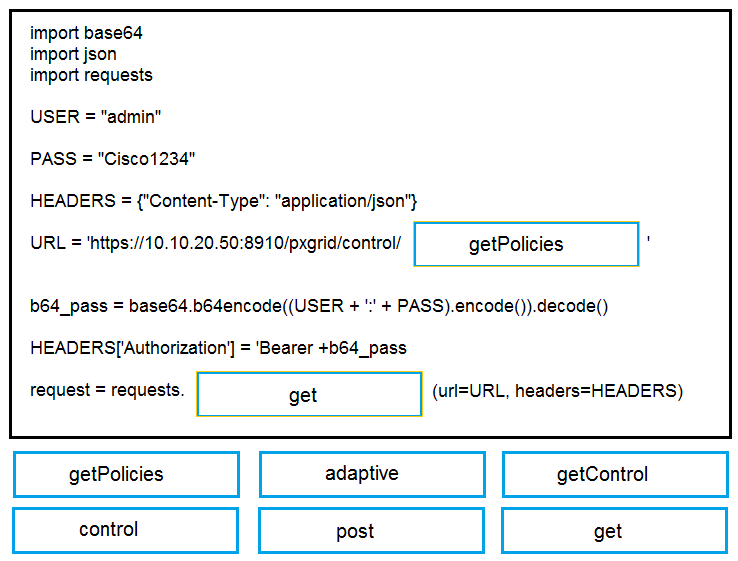
DRAG DROP - Drag and drop the items to complete the pxGrid script to retrieve all Adaptive Network Control policies. Assume that username, password, and base URL are correct. Not all options are used. Select and Place:
Refer to the exhibit. Which URL returned the data?
A. https://api.amp.cisco.com/v1/computers
B. https://api.amp.cisco.com/v0/computers
C. https://amp.cisco.com/api/v0/computers
D. https://amp.cisco.com/api/v1/computers
Refer to the exhibit. A security engineer attempts to query the Cisco Security Management appliance to retrieve details of a specific message. What must be added to the script to achieve the desired result?
A. Add message ID information to the URL string as a URI.
B. Run the script and parse through the returned data to find the desired message.
C. Add message ID information to the URL string as a parameter.
D. Add message ID information to the headers.
If the goal is to create an access policy with the default action of blocking traffic, using Cisco Firepower Management Center REST APIs, which snippet is used? A.B.
C.
D.
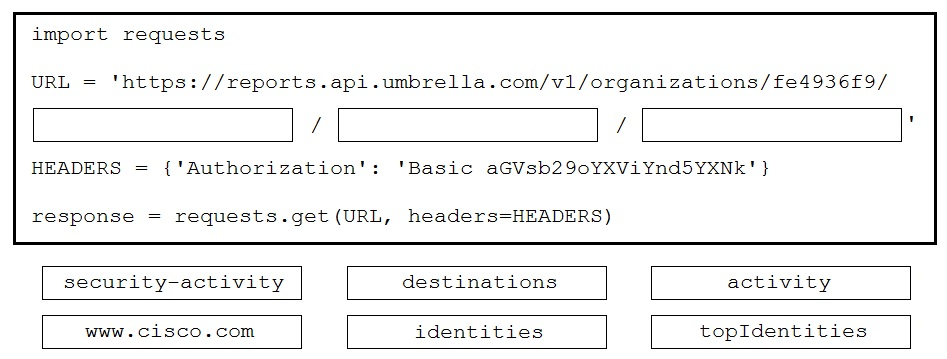
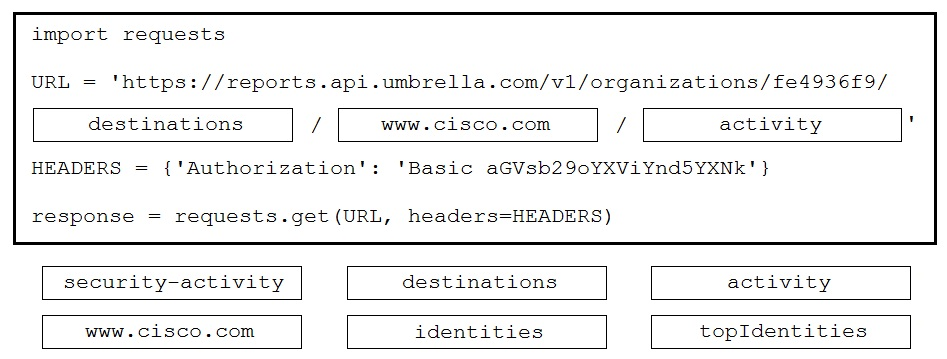
DRAG DROP - A Python script is being developed to return the top 10 identities in an organization that have made a DNS request to "www.cisco.com". Drag and drop the code to complete the Cisco Umbrella Reporting API query to return the top identities. Not all options are used. Select and Place:
Which query parameter is required when using the reporting API of Cisco Security Management Appliances?
A. device_type
B. query_type
C. filterValue
D. startDate + endDate
Refer to the exhibit. What does the response from the API contain when this code is executed?
A. error message and status code of 403
B. newly created domains in Cisco Umbrella Investigate
C. updated domains in Cisco Umbrella Investigate
D. status and security details for the domains
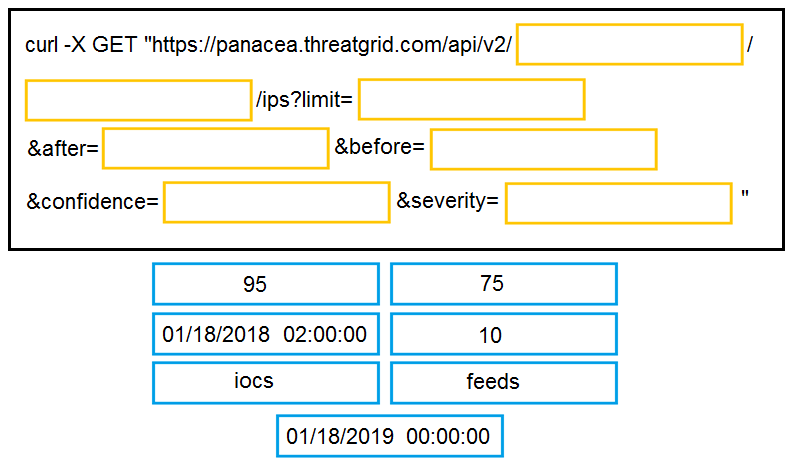
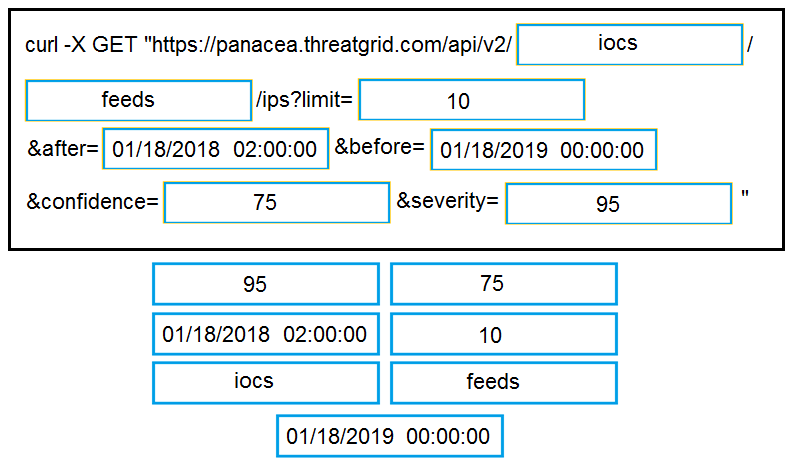
DRAG DROP - Drag and drop the items to complete the curl request to the ThreatGRID API. The API call should request the first 10 IP addresses that ThreatGRID saw samples communicate with during analysis, in the first two hours of January 18 (UTC time), where those communications triggered a Behavior Indicator that had a th confidence equal to or higher than 75 and a severity equal to or higher than 95. Select and Place:
After changes are made to the Cisco Firepower Threat Defense configuration using the Cisco Firepower Device Manager API, what must be done to ensure that the new policy is activated?
A. Submit a POST to the /api/fdm/latest/operational/deploy URI.
B. Submit a GET to the /api/fdm/latest/operational/deploy URI.
C. Submit a PUT to the /api/fdm/latest/devicesettings/pushpolicy URI.
D. Submit a POST to the /api/fdm/latest/devicesettings/pushpolicy URI.
Which API is used to query if the domain "example.com" has been flagged as malicious by the Cisco Security Labs team?
A. https://s-platform.api.opendns.com/1.0/events?example.com
B. https://investigate.api.umbrella.com/domains/categorization/example.com
C. https://investigate.api.umbrella.com/domains/volume/example.com
D. https://s-platform.api.opendns.com/1.0/domains?example.com
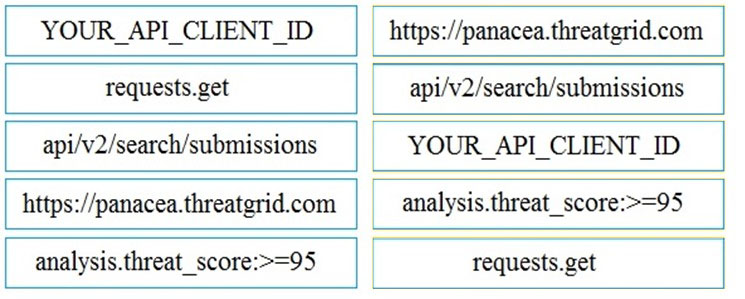
DRAG DROP -Refer to the exhibit. Drag and drop the elements from the left onto the script on the right that queries Cisco ThreatGRID for indications of compromise. Select and Place:
Free Access Full 300-735 Practice Test Free Questions
If you’re looking for more 300-735 practice test free questions, click here to access the full 300-735 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-735 certification journey!