300-715 Mock Test Free – 50 Realistic Questions to Prepare with Confidence.
Getting ready for your 300-715 certification exam? Start your preparation the smart way with our 300-715 Mock Test Free – a carefully crafted set of 50 realistic, exam-style questions to help you practice effectively and boost your confidence.
Using a mock test free for 300-715 exam is one of the best ways to:
- Familiarize yourself with the actual exam format and question style
- Identify areas where you need more review
- Strengthen your time management and test-taking strategy
Below, you will find 50 free questions from our 300-715 Mock Test Free resource. These questions are structured to reflect the real exam’s difficulty and content areas, helping you assess your readiness accurately.
Which two fields are available when creating an endpoint on the context visibility page of Cisco ISE? (Choose two.)
A. Security Group Tag
B. Endpoint Family
C. Policy Assignment
D. Identity Group Assignment
E. IP Address
What are two differences of TACACS+ compared to RADIUS? (Choose two.)
A. TACACS+ uses a connectionless transport protocol, whereas RADIUS uses a connection-oriented transport protocol.
B. TACACS+ encrypts the full packet payload, whereas RADIUS only encrypts the password.
C. TACACS+ only encrypts the password, whereas RADIUS encrypts the full packet payload.
D. TACACS+ uses a connection-oriented transport protocol, whereas RADIUS uses a connectionless transport protocol.
E. TACACS+ supports multiple sessions per user, whereas RADIUS supports one session per user.
What is the deployment mode when two Cisco ISE nodes are configured in an environment?
A. standalone
B. distributed
C. standard
D. active
What is a valid status of an endpoint attribute during the device registration process?
A. block listed
B. pending
C. unknown
D. DenyAccess
An administrator is configuring endpoint profiling and needs to enable CoA for devices that change profiles. Which two actions must be taken to accomplish this goal? (Choose two.)
A. Ensure that the firewall is not blocking port 1700
B. Define “reauth” in the default CoA action to be used
C. Use an API to detect when profile changes occur and send instructions to ISE to provide a CoA
D. Modify the RADIUS endpoint attribute filters to send CoA actions as the profiles change
E. Enable the CoA policy and create rules for each type
An engineer is using Cisco ISE and configuring guest services to allow wireless devices to access the network. Which action accomplishes this task?
A. Create the redirect ACL on Cisco ISE and add it to the Cisco ISE Policy.
B. Create the redirect ACL on the WLC and add it to the WLC policy.
C. Create the redirect ACL on Cisco ISE and add it to the WLC policy.
D. Create the redirect ACL on the WLC and add it to the Cisco ISE policy.
An administrator needs to add a new third party network device to be used with Cisco ISE for Guest and BYOD authorizations. Which two features must be configured under Network Device Profile to achieve this? (Choose two.)
A. TACACS
B. SNMP community
C. CoA Type
D. dACL
E. URL Redirect
Which two ports must be open between Cisco ISE and the client when you configure posture on Cisco ISE? (Choose two.)
A. TCP 80
B. TCP 8905
C. TCP 8443
D. TCP 8906
E. TCP 443
Which Cisco ISE deployment model provides redundancy by having every node in the deployment configured with the Administration, Policy Service, and Monitoring personas to protect from a complete node failure?
A. dispersed
B. distributed
C. two-node
D. hybrid
What is needed to configure wireless guest access on the network?
A. endpoint already profiled in ISE
B. WEBAUTH ACL for redirection
C. Captive Portal Bypass turned on
D. valid user account in Active Directory
A user recently had their laptop stolen. IT has ordered a replacement device for the user and was able to obtain the MAC address of the device 04.57:47:34 35 0A from the vendor before it shipped. Which statement regarding adding MAC addresses to Cisco ISE is correct?
A. MAC addresses can only be manually imported using a .csv file and the import option.
B. MAC addresses can only be manually imported using the REST API.
C. MAC addresses can only be allowed after the device has connected to the network.
D. MAC addresses can be manually added using the + sign under Context Visibility > Endpoints.
An employee must access the internet through the corporate network from a new mobile device that does not support native supplicant provisioning provided by Cisco ISE. Which portal must the employee use to provision to the device?
A. My Devices
B. BYOD
C. Personal Device
D. Client Provisioning
When configuring Active Directory groups, what does the Cisco ISE use to resolve ambiguous group names?
A. MIB
B. SID
C. MAB
D. TGT
When configuring an authorization policy, an administrator cannot see specific Active Directory groups present in their domain to be used as a policy condition. However, other groups that are in the same domain are seen. What is causing this issue?
A. Cisco ISE’s connection to the AD join point is failing.
B. Cisco ISE only sees the built-in groups, not user created ones.
C. The groups are not added to Cisco ISE under the AD join point.
D. The groups are present but need to be manually typed as conditions.
What are two components of the posture requirement when configuring Cisco ISE posture? (Choose two.)
A. Client Provisioning portal
B. remediation actions
C. updates
D. access policy
E. conditions
An engineer must configure web redirection for guests to a portal where no authentication is required and an Acceptable Use Policy must be accepted by the guest before network access is allowed. Which type of guest portal must be configured in Cisco ISE to meet the requirement?
A. Sponsored
B. Self Registered
C. Hotspot
D. Custom
In which two ways can users and endpoints be classified for TrustSec? (Choose two.)
A. VLAN
B. dynamic
C. QoS
D. SGACL
E. SXP
An engineer is configuring Cisco ISE to reprofile endpoints based only on new requests of INIT-REBOOT and SELECTING message types. Which probe should be used to accomplish this task?
A. DHCP
B. DNS
C. NMAP
D. RADIUS
A network administrator is configuring authorization policies in Cisco ISE. There is a requirement to use AD group assignments to control access to network resources. After a recent power failure and Cisco ISE rebooting itself, the AD group assignments no longer work. What is the cause of this issue?
A. The AD join point is no longer connected.
B. The certificate checks are not being conducted.
C. The network devices ports are shut down.
D. The AD DNS response time is slow.
An administrator is configuring a Cisco WLC for web authentication. Which two client profiling methods are enabled by default if the Apply Cisco ISE Default Settings check box has been selected? (Choose two.)
A. LLDP
B. CDP
C. DHCP
D. SNMP
E. HTTP
Which use case validates a change of authorization?
A. An endpoint that is disconnected from the network is discovered.
B. Endpoints are created through device registration for the guests.
C. An endpoint profiling policy is changed for authorization policy.
D. An authenticated, wired EAP-capable endpoint is discovered.
A network administrator notices that after a company-wide shut down, many users cannot connect their laptops to the corporate SSID. What must be done to permit access in a timely manner?
A. Connect this system as a guest user and then redirect the web auth protocol to log in to the network.
B. Allow authentication for expired certificates within the EAP-TLS section under the allowed protocols.
C. Add a certificate issue from the CA server, revoke the expired certificate, and add the new certificate in system.
D. Authenticate the user’s system to the secondary Cisco ISE node and move this user to the primary with the renewed certificate.
Which two external identity stores support EAP-TLS and PEAP-TLS? (Choose two.)
A. RSA SecurID
B. RADIUS Token
C. Active Directory
D. Internal Database
E. LDAP
A network engineer is configuring Cisco TrustSec and needs to ensure that the Security Group Tag is being transmitted between two devices. Where in the Layer 2 frame should this be verified?
A. payload
B. 802.1 AE header
C. CMD field
D. 802.1Q field
An administrator enables the profiling service for Cisco ISE to use for authorization policies while in closed mode. When the endpoints connect, they receive limited access so that the profiling probes can gather information and Cisco ISE can assign the correct profiles. They are using the default values within Cisco ISE, but the devices do not change their access due to the new profile. What is the problem?
A. The default profiler configuration is set to No CoA for the reauthentication setting.
B. In closed mode, profiling does not work unless CDP is enabled.
C. The profiler feed is not downloading new information, so the profiler is inactive.
D. The profiling probes are not able to collect enough information to change the device profile.
A Cisco ISE administrator must restrict specific endpoints from accessing the network while in closed mode. The requirement is to have Cisco ISE centrally store the endpoints to restrict access from. What must be done to accomplish this task?
A. Create a profiling policy for each endpoint with the cdpCacheDeviceId attribute.
B. Create a logical profile for each device’s profile policy and block that via authorization policies.
C. Add each MAC address manually to a blocklist identity group and create a policy denying access.
D. Add each IP address to a policy denying access.
A network engineer is configuring guest access and notices that when a guest user registers a second device for access, the first device loses access. What must be done to ensure that both devices for a particular user are able to access the guest network simultaneously?
A. Use a custom portal to increase the number of logins.
B. Create an Adaptive Network Control policy to increase the number of devices.
C. Modify the guest type to increase the number of maximum devices.
D. Configure the sponsor group to increase the number of logins.
During BYOD flow, where does a Microsoft Windows PC download the Network Setup Assistant?
A. Microsoft App Store
B. Cisco App Store
C. Cisco ISE directly
D. Native OTA functionality
An engineer is designing a BYOD environment utilizing Cisco ISE for devices that do not support native supplicants. Which portal must the security engineer configure to accomplish this task?
A. BYOD
B. Client Provisioning
C. My Devices
D. MDM
An engineer configured posture assessment for their network access control with the goal of using an agent that supports using service conditions for the assessment. The agent should run as a background process to avoid user interruption, but the user can see it when it is run. What is the problem?
A. The selected posture agent does not support the engineer’s goal.
B. The posture module was deployed using the headend instead of installing it with SCCM.
C. The proper permissions were not given to the temporal agent to conduct the assessment.
D. The user required remediation so the agent appeared in the notifications.
An engineer has been tasked with using Cisco ISE to restrict network access at the switchport level using 802.1X authentication. Users who fail 802.1X authentication should e redirected via web redirection and have their access restricted via an ACL. What must be configured in Cisco ISE to accomplish this task?
A. an authorization profile
B. an authorization rule
C. an authentication policy
D. an authentication profile
A network engineer must configure a centralized Cisco ISE solution for wireless guest access with users in different time zones. The guest account activation time must be independent of the user time zone, and the guest account must be enabled automatically when the user self-registers on the guest portal. Which option in the time profile settings must be selected to meet the requirement?
A. Select FromFirstLogin from the Account Type dropdown.
B. Select FromCreation from the Account Type dropdown.
C. Set the Maximum Account Duration to 1 Day.
D. Set the Duration field to 24:00:00.
A network administrator must use Cisco ISE to check whether endpoints have the correct version of antivirus installed. Which action must be taken to allow this capability?
A. Create a Cisco AnyConnect Network Visibility Module configuration profile to send the antivirus information of the endpoints to Cisco ISE.
B. Configure Cisco ISE to push the HostScan package to the endpoints to check for the antivirus version.
C. Configure a native supplicant profile to be used for checking the antivirus version.
D. Create a Cisco AnyConnect configuration within Cisco ISE for the Compliance Module and associated configuration files.
Which supplicant(s) and server(s) are capable of supporting EAP-CHAINING?
A. Cisco Secure Services Client and Cisco Access Control Server
B. Cisco AnyConnect NAM and Cisco Identity Service Engine
C. Cisco AnyConnect NAM and Cisco Access Control Server
D. Windows Native Supplicant and Cisco Identity Service Engine
A network engineer received alerts from the monitoring platform that a switch port exists with multiple sessions. RADIUS CoA using Cisco ISE must be used to address the issue. Which RADIUS CoA configuration must be used?
A. port bounce
B. no CoA
C. exception
D. reauth
An engineer is starting to implement a wired 802.1X project throughout the campus. The task is to ensure that the authentication procedure is disabled on the ports but still allows all endpoints to connect to the network. Which port-control option must the engineer configure?
A. pae-disabled
B. auto
C. force-authorized
D. force-unauthorized
A network administrator is configuring client provisioning resource policies for client machines and must ensure that an agent pop-up is presented to the client when attempting to connect to the network. Which configuration item needs to be added to allow for this?
A. a temporal agent that gets installed onto the system
B. a remote posture agent proxying the network connection
C. the client provisioning URL in the authorization policy
D. an API connection back to the client
An organization has a fully distributed Cisco ISE deployment. When implementing probes, an administrator must scan for unknown endpoints to learn the IP-to- MAC address bindings. The scan is complete on one PSN, but the information is not available on the others. What must be done to make the information available?
A. Cisco ISE must be configured to learn the IP-MAC binding of unknown endpoints via RADIUS authentication, not via scanning.
B. Cisco ISE must learn the IP-MAC binding of unknown endpoints via DHCP profiling, not via scanning.
C. Scanning must be initiated from the MnT node to centrally gather the information.
D. Scanning must be initiated from the PSN that last authenticated the endpoint.
When configuring Active Directory groups, an administrator is attempting to retrieve a group that has a name that is ambiguous with another group. What must be done so that the correct group is returned?
A. Use the SID as the identifier for the group.
B. Configure MAB to utilize one group, and 802 1xto utilize the conflicting group.
C. Select both groups, and use a TCT pointer to identity the appropriate one.
D. Utilize MIB entries to identify the desired group.
A customer wants to set up the Sponsor portal and delegate the authentication flow to a third party for added security while using Kerberos. Which database should be used to accomplish this goal?
A. local database
B. LDAP
C. RSA Token Server
D. Active Directory
An organization wants to standardize the 802.1X configuration on their switches and remove static ACLs on the switch ports while allowing Cisco ISE to communicate to the switch what access to provide. What must be configured to accomplish this task?
A. dynamic access list within the authorization profile
B. extended access-list on the switch for the client
C. security group tag within the authorization policy
D. port security on the switch based on the client’s information
An engineer is configuring 802.1X and is testing out their policy sets. After authentication, some endpoints are given an access-reject message but are still allowed onto the network. What is causing this issue to occur?
A. The authorization results for the endpoints include the Trusted security group tag.
B. The authorization results for the endpoints include a dACL allowing access.
C. The switch port is configured with authentication event server dead action authorize vlan.
D. The switch port is configured with authentication open.
An engineer is deploying Cisco ISE to use 802.1X authentication for controlling access to the company's wired network. The request from company management is to minimize the impact on users during the rollout of 802.1X on the company switches. Which mode must be used first in a phased 802.1X deployment to fulfill this request?
A. Monitor
B. Open
C. Low-impact
D. Closed
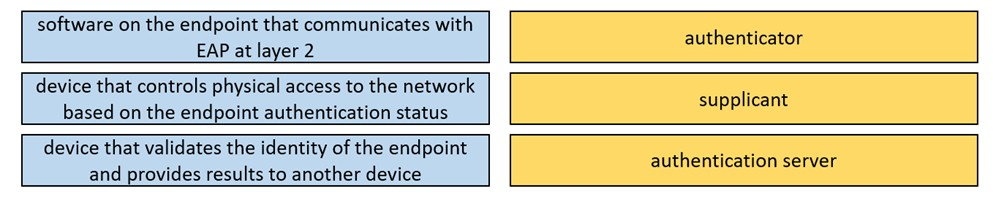
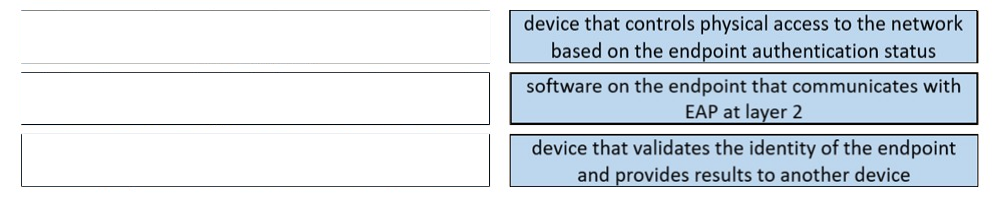
DRAG DROP - Drag the descriptions on the left onto the components of 802.1X on the right. Select and Place:
An administrator is adding network devices for a new medical building into Cisco ISE. These devices must be in a network device group that is identifying them as `Medical Switch` so that the policies can be made separately for the endpoints connecting through them. Which configuration item must be changed in the network device within Cisco ISE to accomplish this goal?
A. Change the device profile to Medical Switch.
B. Change the device type to Medical Switch.
C. Change the device location to Medical Switch.
D. Change the model name to Medical Switch.
When creating a policy within Cisco ISE for network access control, the administrator wants to allow different access restrictions based upon the wireless SSID to which the device is connecting. Which policy condition must be used in order to accomplish this?
A. Network Access NetworkDeviceName CONTAINS
B. DEVICE Device Type CONTAINS
C. Airespace Airespace-Wlan-Id CONTAINS
D. Radius Called-Station-ID CONTAINS
What should be configured on the Cisco ISE authentication policy for unknown MAC addresses/identities for successful authentication?
A. continue
B. pass
C. drop
D. reject
The security engineer for a company has recently deployed Cisco ISE to perform centralized authentication of all network device logins using TACACSs+ against the local AD domain. Some of the other network engineers are having a hard time remembering to enter their AD account password instead of the local admin password that they have used for years. The security engineer wants to change the password prompt to “Use Local AD Password:” as a way of providing a hint to the network engineers when logging in. Under which page in Cisco ISE would this change be made?
A. Work Centers> Device Administration Ext Id Sources>Advanced Settings
B. The password prompt cannot be changed on a Cisco IOS device
C. Work Centers> Device Administration> Network Resources> Network Devices
D. Work Centers> Device Administration> Settings> Connection Settings
The 300 GB OVA templates for VMs are sufficient for which two dedicated Cisco ISE node types? (Choose two.)
A. Administration
B. Log Collector
C. pxGrid
D. Policy Service
E. Monitoring
A network engineer needs to deploy 802.1x using Cisco ISE in a wired network environment where thin clients download their system image upon bootup using PXE. For which mode must the switch ports be configured?
A. closed
B. restricted
C. monitor
D. low-impact
Access Full 300-715 Mock Test Free
Want a full-length mock test experience? Click here to unlock the complete 300-715 Mock Test Free set and get access to hundreds of additional practice questions covering all key topics.
We regularly update our question sets to stay aligned with the latest exam objectives—so check back often for fresh content!
Start practicing with our 300-715 mock test free today—and take a major step toward exam success!