300-710 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 300-710 certification? Our 300-710 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 300-710 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 300-710 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which action should be taken after editing an object that is used inside an access control policy?
A. Delete the existing object in use.
B. Refresh the Cisco FMC GUI for the access control policy.
C. Redeploy the updated configuration.
D. Create another rule using a different object name.
An engineer configures an access control rule that deploys file policy configurations to security zone or tunnel zones, and it causes the device to restart. What is the reason for the restart?
A. Source or destination security zones in the access control rule matches the security zones that are associated with interfaces on the target devices.
B. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the destination policy.
C. Source or destination security zones in the source tunnel zone do not match the security zones that are associated with interfaces on the target devices.
D. The source tunnel zone in the rule does not match a tunnel zone that is assigned to a tunnel rule in the source policy.
A company is deploying intrusion protection on multiple Cisco FTD appliances managed by Cisco FMC. Which system-provided policy must be selected if speed and detection are priorities?
A. Maximum Detection
B. Connectivity Over Security
C. Security Over Connectivity
D. Balanced Security and Connectivity
What is the role of realms in the Cisco ISE and Cisco FMC integration?
A. Cisco Secure Firewall VDC
B. Cisco ISE context
C. TACACS+ database
D. AD definition
A hospital network needs to upgrade their Cisco FMC managed devices and needs to ensure that a disaster recovery process is in place. What must be done in order to minimize downtime on the network?
A. Configure a second circuit to an ISP for added redundancy.
B. Keep a copy of the current configuration to use as backup.
C. Configure the Cisco FMCs for failover.
D. Configure the Cisco FMC managed devices for clustering.
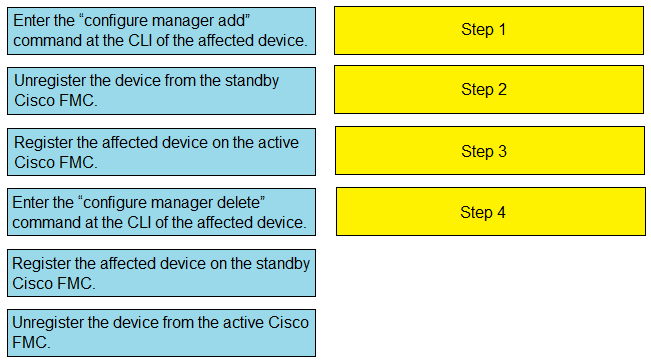
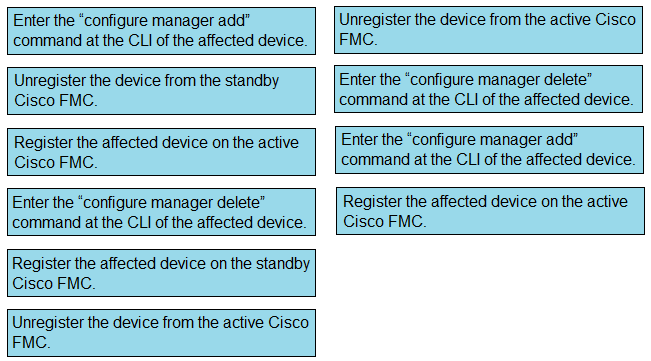
DRAG DROP - Drag and drop the steps to restore an automatic device registration failure on the standby Cisco FMC from the left into the correct order on the right. Not all options are used. Select and Place:
An engineer wants to perform a packet capture on the Cisco FTD to confirm that the host using IP address 192.168.100.100 has the MAC address of 1234.5678.901 to help troubleshoot a connectivity issue. What is the correct tcpdump command syntax to ensure that the MAC address appears in the packet capture output?
A. -w capture.pcap -s 1518 host 192.168.100.100 ether
B. -w capture.pcap -s 1518 host 192.168.100.100 mac
C. -nm src 192.168.100.100
D. -ne src 192.168.100.100
A network administrator has converted a Cisco FTD from using LDAP to LDAPS for VPN authentication. The Cisco FMC can connect to the LDAPS server, but the Cisco FTD is not connecting. Which configuration must be enabled on the Cisco FTD?
A. The LDAPS must be allowed through the access control policy.
B. The RADIUS server must be defined.
C. SSL must be set to a use TLSv1.2 or lower.
D. DNS servers must be defined for name resolution.
An engineer is using the configure manager add
A. DONOTRESOLVE must be added to the command
B. The IP address used should be that of the Cisco FTD, not the Cisco FMC
C. The registration key is missing from the command
D. The NAT ID is required since the Cisco FMC is behind a NAT device
An organization has noticed that malware was downloaded from a website that does not currently have a known bad reputation. How will this issue be addressed globally in the quickest way possible and with the least amount of impact?
A. by creating a URL object in the policy to block the website.
B. Cisco Talos will automatically update the policies.
C. by denying outbound web access
D. by isolating the endpoint
Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
A. rate-limiting
B. suspending
C. correlation
D. thresholding
An engineer configures a network discovery policy on Cisco FMC. Upon configuration, it is noticed that excessive and misleading events are filling the database and overloading the Cisco FMC. A monitored NAT device is executing multiple updates of its operating system in a short period of time. What configuration change must be made to alleviate this issue?
A. Exclude load balancers and NAT devices.
B. Leave default networks.
C. Increase the number of entries on the NAT device.
D. Change the method to TCP/SYN.
A network administrator is configuring a BVI interface on a routed FTD. The administrator wants to isolate traffic on the interfaces connected to the bridge group and not have the FTD route this traffic using the routing table. What must be configured?
A. A new VRF must be created for the BVI interface
B. An IP address must be configured on the BVI
C. IP routing must be removed from the physical interfaces connected to the BVI
D. The BVI interface must be configured for transparent mode
Which Firepower feature allows users to configure bridges in routed mode and enables devices to perform Layer 2 switching between interfaces?
A. FlexConfig
B. BDI
C. SGT
D. IRB
An engineer is troubleshooting an intermittent connectivity issue on a Cisco Secure Firewall Threat Defense appliance and must collect 24 hours' worth of data. The engineer started a packet capture, however it stops prematurely during this time period. The engineer notices that the packet capture buffer size is set to the default of 32 MB. Which buffer size is the maximum that the engineer must set to enable the packet capture to run successfully?
A. 64 MB
B. 1 GB
C. 10 GB
D. 100 GB
An engineer is setting up a remote access VPN on a Cisco FTD device and wants to define which traffic gets sent over the VPN tunnel. Which named object type in Cisco FMC must be used to accomplish this task?
A. crypto map
B. split tunnel
C. access list
D. route map
A network administrator wants to configure a Cisco Secure Firewall Threat Defense instance managed by Cisco Secure Firewall Management Center to block traffic to known cryptomining networks. Which system settings must the administrator configure in Secure Firewall Management Center to meet the requirement?
A. Intrusion Policy, Security Intelligence
B. Access Policy, Security Intelligence
C. Malware Policy, Rules
D. Access Policy, Rules
When deploying a Cisco ASA Firepower module, an organization wants to evaluate the contents of the traffic without affecting the network. It is currently configured to have more than one instance of the same device on the physical appliance. Which deployment mode meets the needs of the organization?
A. inline tap monitor-only mode
B. passive monitor-only mode
C. passive tap monitor-only mode
D. inline mode
An engineer is configuring URL filtering for a Cisco FTD device in Cisco FMC. Users must receive a warning when they access http://www.badadultsite.com with the option of continuing to the website if they choose to. No other websites should be blocked. Which two actions must the engineer take to meet these requirements? (Choose two.)
A. On the HTTP Responses tab of the access control policy editor, set the Interactive Block Response Page to System-provided.
B. Configure the default action for the access control policy to Interactive Block.
C. Configure an access control rule that matches an URL object for http://www.badadultsite.com/ and set the action to Interactive Block.
D. Configure an access control rule that matches the Adult URL category and set the action to Interactive Block.
E. On the HTTP Responses tab of the access control policy editor, set the Block Response Page to Custom.
A network administrator is deploying a new Cisco Secure Firewall Threat Defense (FTD) firewall. After Cisco Secure FTD is deployed, inside clients have intermittent connectivity to each other. When reviewing the packet capture on the Secure FTD firewall, the administrator sees that Secure FTD is responding to all the ARP requests on the inside network. Which action must the network administrator take to resolve the issue?
A. Review the access policy and verify that ARP is allowed from inside to inside.
B. Review NAT policy and disable incorrect proxy ARP configuration.
C. Convert the FTD to transparent mode to allow ARP requests.
D. Hardcode the MAC address of the FTD to IP mapping on client machines.
Network traffic coming from an organization's CEO must never be denied. Which access control policy configuration option should be used if the deployment engineer is not permitted to create a rule to allow all traffic?
A. Change the intrusion policy from security to balance.
B. Configure a trust policy for the CEO.
C. Configure firewall bypass.
D. Create a NAT policy just for the CEO.
The security engineer reviews the syslog server events of an organization and sees many outbound connections to malicious sites initiated from hosts running Cisco Secure Endpoint. The hosts are on a separate network from the Cisco FTD device. Which action blocks the connections?
A. Modify the policy on Cisco Secure Endpoint to enable DFC.
B. Modify the access control policy on the Cisco FMC to block malicious outbound connections
C. Add the IP addresses of the malicious sites to the access control policy on the Cisco FMC
D. Add a Cisco Secure Endpoint policy with the Tetra and Spero engines enabled
An engineer is restoring a Cisco FTD configuration from a remote backup using the command restore remote-manager-backup location 1.1.1.1 admin / Volume/home/admin BACKUP_Cisc394602314.zip on a Cisco FMC. After connecting to the repository, an error occurred that prevents the FTD device from accepting the backup file. What is the problem?
A. The backup file is not in .cfg format
B. The backup file is too large for the Cisco FTD device
C. The backup file extension was changed from .tar to .zip
D. The backup file was not enabled prior to being applied
Which command is run on an FTD unit to associate the unit to an FMC manager that is at IP address 10.0.0.10, and that has the registration key Cisco123?
A. configure manager local 10.0.0.10 Cisco123
B. configure manager add Cisco123 10.0.0.10
C. configure manager local Cisco123 10.0.0.10
D. configure manager add 10.0.0.10 Cisco123
An administrator is attempting to remotely log into a switch in the data center using SSH and is unable to connect. How does the administrator confirm that traffic is reaching the firewall?
A. by performing a packet capture on the firewall
B. by attempting to access it from a different workstation
C. by running Wireshark on the administrator’s PC
D. by running a packet tracer on the firewall
A network engineer is planning on deploying a Cisco Secure Firewall Threat Defense Virtual appliance in transparent mode. Which two virtual environments support this configuration? (Choose two.)
A. OSI
B. AWS
C. GCP
D. KVM
E. ESXi
An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
A. routed
B. passive
C. transparent
D. inline tap
What is a limitation to consider when running a dynamic routing protocol on a Cisco Secure Firewall Threat Defense device in IRB mode?
A. Only link-state routing protocols are supported.
B. Only nonbridge interfaces are supported.
C. Only EtherChannel interfaces are supported.
D. Only distance vector routing protocols are supported.
A network administrator notices that SI events are not being updated. The Cisco FTD device is unable to load all of the SI event entries and traffic is not being blocked as expected. What must be done to correct this issue?
A. Restart the affected devices in order to reset the configurations.
B. Redeploy configurations to affected devices so that additional memory is allocated to the SI module.
C. Replace the affected devices with devices that provide more memory.
D. Manually update the SI event entries to that the appropriate traffic is blocked.
A consultant is working on a project where the customer is upgrading from a single Cisco Firepower 2130 managed by FDM to a pair of Cisco Firepower 2130s managed by FMC for high availability. The customer wants the configuration of the existing device being managed by FDM to be carried over to FMC and then replicated to the additional device being added to create the high availability pair. Which action must the consultant take to meet this requirement?
A. The current FDM configuration must be configured by hand into FMC before the devices are registered.
B. The current FDM configuration must be migrated to FMC using the Secure Firewall Migration Tool.
C. The FTD configuration must be converted to ASA command format, which can then be migrated to FMC.
D. The current FDM configuration will be converted automatically into FMC when the device registers.
An engineer is configuring a custom intrusion rule on Cisco FMC. The engineer needs the rule to search the payload or stream for the string "|44 78 97 13 2 0A|". Which keyword must the engineer use with this string to create an argument for packet inspection?
A. protected_content
B. content
C. data
D. metadata
An engineer is monitoring network traffic from their sales and product development departments, which are on two separate networks. What must be configured in order to maintain data privacy for both departments?
A. Use passive IDS ports for both departments.
B. Use a dedicated IPS inline set for each department to maintain traffic separation.
C. Use 802.1Q inline set Trunk interfaces with VLANs to maintain logical traffic separation.
D. Use one pair of inline set in TAP mode for both departments.
An engineer wants to add an additional Cisco FTD Version 6.2.3 device to their current 6.2.3 deployment to create a high availability pair. The currently deployed Cisco FTD device is using local management and identical hardware including the available port density to enable the failover and stateful links required in a proper high availability deployment. Which action ensures that the environment is ready to pair the new Cisco FTD with the old one?
A. Change from Cisco FDM management to Cisco FMC management on both devices and register them to FMC.
B. Ensure that the two devices are assigned IP addresses from the 169.254.0.0/16 range for failover interfaces.
C. Factory reset the current Cisco FTD so that it can synchronize configurations with the new Cisco FTD device.
D. Ensure that the configured DNS servers match on the two devices for name resolution.
An engineer defines a new rule while configuring an Access Control Policy. After deploying the policy, the rule is not working as expected and the hit counters associated with the rule are showing zero. What is causing this error?
A. An incorrect application signature was used in the rule.
B. The wrong source interface for Snort was selected in the rule.
C. The rule was not enabled after being created.
D. Logging is not enabled for the rule.
Which protocol is needed to exchange threat details in rapid threat containment on Cisco FMC?
A. SGT
B. SNMP v3
C. BFD
D. pxGrid
When is the file-size command needed while troubleshooting with packet capture?
A. when capture packets are less than 16 MB
B. when capture packets are restricted from the secondary memory
C. when capture packets exceed 10 GB
D. when capture packets exceed 32 MB
Remote users who connect via Cisco AnyConnect to the corporate network behind a Cisco FTD device report that they get no audio when calling between remote users using their softphones. These same users can call internal users on the corporate network without any issues. What is the cause of this issue?
A. FTD has no NAT policy that allows outside to outside communication.
B. Split tunneling is enabled for the Remote Access VPN on FTD.
C. The hairpinning feature is not available on FTD.
D. The Enable Spoke to Spoke Connectivity through Hub option is not selected on FTD.
What must be implemented on Cisco Firepower to allow multiple logical devices on a single physical device to have access to external hosts?
A. Add at least two container instances from the same module.
B. Set up a cluster control link between all logical devices.
C. Define VLAN subinterfaces for each logical device.
D. Add one shared management interface on all logical devices.
Refer to the exhibit. An administrator is looking at some of the reporting capabilities for Cisco Firepower and noticed this section of the Network Risk Report showing a lot of SSL activity that could be used for evasion. Which action will mitigate this risk?
A. Use SSL decryption to analyze the packets.
B. Use Cisco Tetration to track SSL connections to servers.
C. Use encrypted traffic analytics to detect attacks.
D. Use Cisco AMP for Endpoints to block all SSL connection.
When using Cisco Threat Response, which phase of the Intelligence Cycle publishes the results of the investigation?
A. processing
B. direction
C. dissemination
D. analysis
An administrator configures new threat intelligence sources and must validate that the feeds are being downloaded and that the intelligence is being used within the Cisco Secure Firewall system. Which action accomplishes the task?
A. Look at the connection security intelligence events
B. Use the source status indicator to validate the usage
C. View the threat intelligence observables to see the downloaded data
D. Look at the access control policy to validate that the intelligence is being used
An organization is migrating their Cisco ASA devices running in multicontext mode to Cisco FTD devices. Which action must be taken to ensure that each context on the Cisco ASA is logically separated in the Cisco FTD devices?
A. Configure a container instance in the Cisco FTD for each context in the Cisco ASA.
B. Add the Cisco FTD device to the Cisco ASA port channels.
C. Configure the Cisco FTD to use port channels spanning multiple networks.
D. Add a native instance to distribute traffic to each Cisco FTD context.
Which two statements are valid regarding the licensing model used on Cisco Secure Firewall Threat Defense Virtual appliances? (Choose two.)
A. All licenses support a maximum of 250 VPN peers
B. All licenses support up to 16 vCPUs
C. All licenses require 500G of available storage for the VM
D. Licenses can be used on both physical and virtual appliances
E. Licenses can be used on any supported cloud platform
An administrator needs to configure Cisco FMC to send a notification email when a data transfer larger than 10 MB is initiated from an internal host outside of standard business hours. Which Cisco FMC feature must be configured to accomplish this task?
A. file and malware policy
B. application detector
C. correlation policy
D. intrusion policy
A network administrator reviews the file report for the last month and notices that all file types, except exe, show a disposition of unknown. What is the cause of this issue?
A. Only Spero file analysis is enabled.
B. The Cisco FMC cannot reach the Internet to analyze files.
C. A file policy has not been applied to the access policy.
D. The malware license has not been applied to the Cisco FTD.
What is the advantage of having Cisco Firepower devices send events to Cisco Threat Response via the security services exchange portal directly as opposed to using syslog?
A. Firepower devices do not need to be connected to the Internet.
B. An on-premises proxy server does not need to set up and maintained.
C. All types of Firepower devices are supported.
D. Supports all devices that are running supported versions of Firepower
With Cisco FTD software, which interface mode must be configured to passively receive traffic that passes through the appliance?
A. ERSPAN
B. firewall
C. tap
D. IPS-only
An engineer has been tasked with performing an audit of network objects to determine which objects are duplicated across the various firewall models (Cisco Secure Firewall Threat Defense, Cisco Secure Firewall ASA, and Meraki MX Series) deployed throughout the company. Which tool will assist the engineer in performing that audit?
A. Cisco Firepower Device Manager
B. Cisco Defense Orchestrator
C. Cisco Secure Firewall Management Center
D. Cisco SecureX
An administrator is setting up a Cisco FMC and must provide expert mode access for a security engineer. The engineer is permitted to use only a secured out-of-band network workstation with a static IP address to access the Cisco FMC. What must be configured to enable this access?
A. Enable SSH and define an access list.
B. Enable HTTPS and SNMP under the Access List section.
C. Enable SCP under the Access List section.
D. Enable HTTP and define an access list.
A connectivity issue is occurring between a client and a server which are communicating through a Cisco Firepower device. While troubleshooting, a network administrator sees that traffic is reaching the server, but the client is not getting a response. Which step must be taken to resolve this issue without initiating traffic from the client?
A. Use packet-tracer to ensure that traffic is not being blocked by an access list
B. Use packet capture to ensure that traffic is not being blocked by an access list
C. Use packet capture to validate that the packet passes through the firewall and is NATed to the corrected IP address
D. Use packet-tracer to validate that the packet passes through the firewall and is NATed to the corrected IP address
Access Full 300-710 Dump Free
Looking for even more practice questions? Click here to access the complete 300-710 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 300-710 dump free questions — and get one step closer to exam success!