300-430 Practice Test Free – 50 Real Exam Questions to Boost Your Confidence
Preparing for the 300-430 exam? Start with our 300-430 Practice Test Free – a set of 50 high-quality, exam-style questions crafted to help you assess your knowledge and improve your chances of passing on the first try.
Taking a 300-430 practice test free is one of the smartest ways to:
- Get familiar with the real exam format and question types
- Evaluate your strengths and spot knowledge gaps
- Gain the confidence you need to succeed on exam day
Below, you will find 50 free 300-430 practice questions to help you prepare for the exam. These questions are designed to reflect the real exam structure and difficulty level. You can click on each Question to explore the details.
A new MSE with wIPS service has been installed and no alarm information appears to be reaching the MSE from controllers. Which protocol must be allowed to reach the MSE from the controllers?
A. SOAP/XML
B. NMSP
C. CAPWAP
D. SNMP
A customer is concerned that their wireless network is detecting spurious threats from channels that are not being used by their wireless infrastructure. Which two technologies must they deploy? (Choose two.)
A. FlexConnect mode
B. monitor mode
C. sniffer mode with no submode
D. local mode with WIPS submode
E. rogue detector mode
An engineer has implemented 802.1x authentication on the wireless network utilizing the internal database of a RADIUS server. Some clients reported that they are unable to connect. After troubleshooting, it is found that PEAP authentication is failing. A debug showed the server is sending an Access-Reject message. Which action must be taken to resolve authentication?
A. Use the user password that is configured on the server.
B. Disable the server certificate to be validated on the client.
C. Update the client certificate to match the user account.
D. Replace the client certificates from the CA with the server certificate.
A wireless engineer needs to implement client tracking. Which method does the angle of arrival use to determine the location of a wireless device?
A. received signal strength
B. triangulation
C. time distance of arrival
D. angle of incidence
A network engineer observes a spike in controller CPU overhead and overall network utilization after multicast is enabled on a controller with 500 APs. Which feature corrects the issue?
A. controller IGMP snooping
B. multicast AP multicast mode
C. broadcast forwarding
D. unicast AP multicast mode
An administrator receives reports of many interferes in the wireless network and wants to get these interferes' location from the maps in Cisco Prime Infrastructure. When looking at the floor plans/maps, the administrator does not see any interferes but can see all wireless clients located successfully. What must be configured to get the location?
A. Add MSE to Cisco Prime Infrastructure and synchronized.
B. Enable interferer tracking on the MSE.
C. Activate NMSP communication with the WLC.
D. Configure SNMP between Cisco Prime Infrastructure and the WLC.
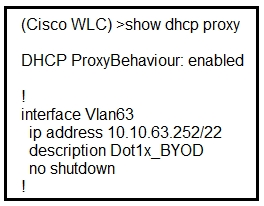
Refer to the exhibit. A network administrator deploys the DHCP profiler service in two ISE servers: 10.3.10.101 and 10.3.10.102. All BYOD devices connecting to WLAN on VLAN63 have been incorrectly profiled and are assigned as unknown profiled endpoints. Which action efficiently rectifies the issue according to Cisco recommendations?
A. Nothing needed to be added on the Cisco WLC or VLAN interface. The ISE configuration must be fixed.
B. Disable DHCP proxy on the Cisco WLC.
C. Disable DHCP proxy on the Cisco WLC and run the ip helper-address command under the VLAN interface to point to DHCP and the two ISE servers.
D. Keep DHCP proxy enabled on the Cisco WLC and define helper-address under the VLAN interface to point to the two ISE servers.
A municipality customer uses a Cisco 5520 Series Wireless Controller for the wireless network. The customer intends to move the depot of its stores from using legacy bespoke voice-over-Wi-Fi handsets to a VoIP software package running on 5 GHz-capable laptops, tablets, and smartphones. Bluetooth headsets will be used for any voice communication on any data device. Assuming that a suitable RF site survey for 5 GHz has already been carried out, which two configuration settings ensure the best possible voice experience? (Choose two.)
A. Configure AVC on the controller to prioritize voice over other applications’ traffic on the same device.
B. Remark all traffic coming from the new voice-capable devices with DSCP 46 (EF) at the AP.
C. Assign the Platinum QoS profile to the SSID carrying the new-style voice traffic.
D. Create mobility groups and include all the APs in the high-density areas.
E. Turn off the 2.4 GHz radios on all APs where the voice application is used.
A company has a Cisco wireless network with Cisco ISE. The company wants to allow employees to use their personal mobile devices on the wireless network. The company wants to allow access to the network only if the devices meet certain criteria. To meet the requirement, the company asked a network engineer to create a native supplicant profile. Which two fields must be configured when the profile is created? (Choose two.)
A. Allowed Protocol (PEAP/TLS)
B. Allowed Protocol (Ms-CHAPv2/ EAP-FAST)
C. SSID Name
D. WLC Name
E. Allowed Protocol (LEAP/ EAP-TTLS)
An engineer set up RADIUS for WLC management to harden the configuration. Read-only access must be provided to a user. Which Service-Type attribute must be configured on the RADIUS server to meet this requirement?
A. NAS Prompt
B. Administrative
C. Call Check
D. Callback Login
An engineer must run a Client Traffic Stream Metrics report in Cisco Prime Infrastructure. Which task must be run before the report?
A. scheduled report
B. radio performance
C. client status
D. software
An engineer is implementing Cisco Identity-Based Networking on a Cisco AireOS controller. The engineer has two ACLs on the controller. The first ACL, named BASE_ACL, is applied to the corporate_clients interface on the WLC, which is used for all corporate clients. The second ACL, named HR_ACL, is referenced by ISE in the Human Resources group policy. What is the resulting ACL when a Human Resources user connects?
A. HR_ACL appended with BASE_ACL
B. HR_ACL only
C. BASE_ACL appended with HR_ACL
D. BASE_ACL only
An engineer must control administrative access to the WLC using their Active Directory without being concerned about RBAC after the admin user is authenticated. Which two features does the engineer configure to accomplish this task? (Choose two.)
A. Device Admin Policy Set
B. User Access Mode: ReadWrite
C. ACL
D. RADIUS server
E. TACACS server
Refer to the exhibit.Which area indicates the greatest impact on the wireless network when viewing the Cisco CleanAir Zone of Impact map of interferers?
A. A
B. B
C. C
D. D
A company has a single WLAN configured for 802.1x authentication with the QoS set to Silver. This WLAN supports all corporate and BYOD access. A decision has been made to allow users to install Cisco Jabber on their personal mobile devices. Users report poor voice quality when using Jabber. QoS is being applied only as best effort. What must be configured to ensure that the WLAN remains on the Silver class and to ensure Platinum class for Jabber?
A. Configure QoS on the mobile devices that have Jabber installed.
B. Enable Cisco Centralized Key Management on the WLAN so that the Jabber-enabled devices will connect.
C. Configure the WLAN to broadcast on 5 GHz radios only and allow Jabber users to connect.
D. Configure an AVC profile for the Jabber traffic and apply it to the WLAN.
An engineer set up identity-based networking with ISE and configured AAA override on the WLAN. Which two attributes must be used to change the client behavior from the default settings? (Choose two.)
A. DHCP timeout
B. DNS server
C. IPv6 ACL
D. DSCP value
E. multicast address
A network engineer created a new wireless network that will be used for guest access. The corporate network must utilize all rates. The guest network must use only lower rates instead of 802.11n data rates. To what must the WMM policy of the WLAN be set to accomplish this task?
A. required
B. allowed
C. disabled
D. mandatory
An engineer must configure a Cisco WLC to support Cisco Aironet 600 Series OfficeExtend APs. Which two Layer 2 security options are supported in this environment? (Choose two.)
A. Static WEP + 802.1X
B. WPA+WPA2
C. Static WEP
D. CKIP
E. 802.1X
Refer to the exhibit. An engineer configured a BYOD policy that allows for printing on the WLAN using Bonjour services. However, the engineer cannot get printing to work. The WLC firmware is 8.x. What must be implemented on the controller?
A. Enable mDNS and IGMP snooping.
B. Activate location-specific services.
C. Configure Secure Web Mode Cipher-Option SSLv2.
D. Increase the IGMP Query Interval value
A request has come in to use dynamic VLAN assignment on an autonomous AP. After the AP is configured, which RADIUS attribute must an engineer use to pass the VLAN ID to the AP?
A. Tunnel-Medium-Type
B. Tunnel-Private-Group-ID
C. Tunnel-Assignment-ID
D. Tunnel-Type
An IT department receives a report of a stolen laptop and has information on the MAC address of the laptop. Which two settings must be set on the wireless infrastructure to determine its location? (Choose two.)
A. Location History for Clients must be enabled on the MSE.
B. Client location tracking must be enabled on the MSE.
C. Location History for Visitors must be enabled on the MSE.
D. Location History for Rogue APs & Rogue Clients must be enabled on the MSE.
E. Tracking optimization must be enabled on the WLC.
An engineer needs to configure the infrastructure for wireless clients to use IEEE 802.1X to the onboarding VLAN. After authentication and profiling, it must be determined if the client is a company device that is up-to-date. After this step, the device must connect to the corporate VLAN and access all resources. What must be implemented to meet these requirements?
A. Change of Authentication
B. Completion of Authentication
C. Change of Authorization
D. Completion of Authorization
An engineer is configuring a new wireless network for guest access. The Facebook page of the company must be viewed by the guest users before they get access to the network. A Cisco MSE is used as a wireless component. Which URL must be used in the configuration as the external redirection URL?
A. http://:8083/visitor/login.do
B. http://:8083/fbwifi/forward
C. http://:8084/visitor/login.do
D. http://:8084/fbwifi/forward
Which command set configures a Cisco Catalyst 9800 Series Wireless Controller so that the client traffic enters the network at the AP switch port? A.B.
C.
D.
An engineer has eight WLCs in a mobility group and must reduce the bandwidth consumed. Which two configuration items achieve this result? (Choose two.)
A. global multicast mode
B. mobility group unicast messaging
C. global unicast messaging
D. mobility group multicast messaging
E. global symmetric mobility messaging
An enterprise started using WebEx as a virtual meeting solution. There is a concern that the existing wireless network will not be able to support the increased amount of traffic as a result of using WebEx. An engineer needs to remark the QoS value for this application to ensure high quality in meetings. What must be implemented to accomplish this task?
A. QoS preferred call index
B. UP to DSCP map
C. AVC profiles
D. WLAN quality of service profile
A customer recently upgraded the network to Cisco SD-Access. Cisco DNA Center manages the wireless network; all SSIDs are Fabric-enabled. Cisco DNA Center must be able to classify “Rogue on Wire" APs. Which action must the customer take?
A. Configure all access switches to be managed by Cisco DNA Center.
B. Allow SNMPv3 between Cisco DNA Center and access switches.
C. Connect APs to the network using a trunk port with native VLAN.
D. Disable all the DCA channels under RRM on the WLC.
An engineer must implement Cisco Identity-Based Networking Services at a remote site using ISE to dynamically assign groups of users to specific IP subnets. If the subnet assigned to a client is available at the remote site, then traffic must be offloaded locally, and subnets are unavailable at the remote site must be tunneled back to the WLC. Which feature meets these requirements?
A. learn client IP address
B. FlexConnect local authentication
C. VLAN-based central switching
D. central DHCP processing
An engineer configures QoS on an AireOS WLC v8.5. The engineer configures a WLAN for voice traffic and must give a higher priority to WMM clients than to non-WMM clients. Which two configurations should be performed? (Choose two.)
A. Implement the Gold QoS profile.
B. Set Multicast Default Priority to Voice.
C. Set Unicast Default Priority to Platinum.
D. Select Video from the Unicast Default Priority drop-down menu.
E. Implement the Platinum QoS profile.
A network engineer performed a new deployment of Cisco DNA Center. The engineer discovered and provisioned all APs and converted them to fabric. The SSIDs were created, and the APs were allocated to the respective floors, but the SSIDs are not being seen on the floors. What must be configured to establish this connectivity?
A. Map the pools to the SSIDs.
B. Configure RADIUS for the SSIDs.
C. Enable all radios on the APs.
D. Add the users in Cisco ISE.
A company is collecting the requirements for an on-premises event. During the event, a wireless client connected to a dedicated WLAN will run a video application that will need on average 391595179 bits per second to function properly. What is the QoS marking that needs to be applied to that WLAN?
A. Platinum
B. Gold
C. Silver
D. Bronze
Which customizable security report on Cisco Prime Infrastructure will show rogue APs detected since a point in time?
A. Network Summary
B. Rogue APs Events
C. New Rogue APs
D. Rogue APs Count Summary
Refer to the exhibit. An administrator notices slower location updates from the controller to Cisco CMX. Which command must be configured to get an update every 5 seconds for rogues?
A. config location notification interval rssi rogues 5
B. config nmsp notification interval rssi rogues 5
C. config subscription notification interval rssi rogues 5
D. config cmx notification interval rssi rogues 5
Refer to the exhibit. A company is implementing Cisco ISE and IBN for their WLAN. The pictured IBN profile is applied to BYOD devices that are not registered to the Mobile Device Manager. Which advanced setting must be enabled on the WLAN to allow the policy to work correctly?
A. static IP tunneling
B. allow AAA override
C. RADIUS profiling
D. Aironet IE
Refer to the exhibit. Which two items must be supported on the VoWLAN phones to take full advantage of this WLAN configuration? (Choose two.)
A. TSPEC
B. SIFS
C. 802.11e
D. WMM
E. APSD
An engineer is performing a Cisco Hyperlocation accuracy test and executes the cmxloc start command on Cisco CMX. Which two parameters are relevant? (Choose two.)
A. X, Y real location
B. client description
C. AP name
D. client MAC address
E. WLC IP address
Which three properties are used for client profiling of wireless clients? (Choose three.)
A. HTTP user agent
B. DHCP
C. MAC OUI
D. hostname
E. OS version
F. IP address
WPA2 Enterprise with 802.1X is being used for clients to authenticate to a wireless network through a Cisco ISE server. For security reasons, the network engineer wants to ensure that only PEAP authentication is used. The engineer sent instructions to clients on how to configure the supplicants, but the ISE logs still show users authenticating using EAP-FAST. Which action ensures that access to the network is restricted for these users unless the correct authentication mechanism is configured?
A. Enable AAA override on the SSID, gather the usernames of these users, and disable the RADIUS accounts until the devices are correctly configured.
B. Enable AAA override on the SSID and configure an ACL on the WLC that allows access to users with IP addresses from a specific subnet.
C. Enable AAA override on the SSID and configure an access policy in Cisco ISE that denies access to the list of MACs that have used EAP-FAST.
D. Enable AAA override on the SSID and configure an access policy in Cisco ISE that allows access only when the EAP authentication method is PEAP.
Refer to the exhibit. An engineer deployed a Cisco WLC using local EAP. Users who are configured for EAP-PEAP cannot connect to the network. Based on the local EAP debug on the controller provided, why is the client unable to connect?
A. The client is failing to accept certificate.
B. The Cisco WLC is configured for the incorrect date.
C. The Cisco WLC local EAP profile is misconfigured.
D. The user is using invalid credentials.
The security policy mandates that only controller web management traffic is allowed from the IT subnet. In testing, an engineer is trying to connect to a WLAN with Web Authentication for guest users, but the page is timing out on the wireless client browser. What is the cause of the issue?
A. The implemented CPU ACL on the controller is blocking HTTP/HTTPS traffic from the guest clients.
B. Web Authentication Redirect is not supported with CPU ACLs.
C. The DNS server that is configured on the controller is incorrect.
D. Web Authentication Redirect is supported only with Internet Explorer, and the client is using Google Chrome.
An engineer is configuring multicast for two WLCs. The controllers are in different physical locations and each handles around 500 wireless clients. How should the CAPWAP multicast group address be assigned during configuration?
A. Each WLC must be assigned a unique multicast group address.
B. Each WLC management address must be in the same multicast group.
C. Both WLCs must be assigned the same multicast group address.
D. Each WLC management address must be in a different multicast group.
When implementing self-registration for guest/BYOD devices, what happens when an employee tries to connect four devices to the network at the same time?
A. The last device is removed and the newly added device is updated as active device.
B. The registration is allowed, but only one device is connected at any given time.
C. All devices are allowed on the network simultaneously.
D. Purge time dictates how long a device is registered to the portal.
An engineer is ensuring that, on the IEEE 802.1X wireless network, clients authenticate using a central repository and local credentials on the Cisco WLC. Which two configuration elements must be completed on the WLAN? (Choose two.)
A. TACACS+
B. MAC authentication
C. local EAP enabled
D. web authentication
E. LDAP server
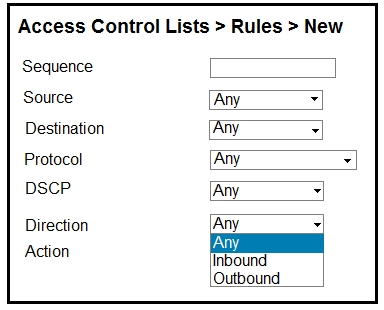
Refer to the exhibit. An engineer is creating an ACL to restrict some traffic to the WLC CPU. Which selection must be made from the direction drop-down list?
A. It must be Inbound because traffic goes to the WLC.
B. Packet direction has no significance; it is always Any.
C. It must be Outbound because it is traffic that is generated from the WLC.
D. To have the complete list of options, the CPU ACL must be created only by the CLI.
An engineer is responsible for a wireless network for an enterprise. The enterprise has distributed offices around the globe, and all APs are configured in FlexConnect mode. The network must be configured to support 802.11r and CCKM. What needs to be implemented to accomplish this goal?
A. Enable VLAN-based central switching.
B. Enable FlexConnect local authentication.
C. Enable FlexConnect local switching.
D. Create FlexConnect groups.
What is configured to use more than one port on the OEAP to extend the wired network?
A. remote LAN ACL
B. AAA override
C. client load balancing
D. remote LAN
A healthcare organization notices many rogue APs and is concerned about a honeypot attack. Which configuration must a wireless network engineer perform in Cisco Prime Infrastructure to prevent these attacks most efficiently upon detection?
A. Set the auto containment level to 0 and select the Using Our SSID containment option.
B. Set the manual containment level to 4 and select the Ad Hoc Rogue AP containment option.
C. Set the auto containment level to 0 and select the Ad Hoc Rogue AP containment option.
D. Set the auto containment level to 4 and select the Using Our SSID containment option.
After looking in the logs, an engineer notices that RRM keeps changing the channels for non-IEEE 802.11 interferers. After surveying the area, it has been decided that RRM should not change the channel. Which feature must be enabled to ignore non-802.11 interference?
A. Avoid Cisco AP Load
B. Avoid Non-802.11 Noise
C. Avoid Persistent Non-WiFi Interference
D. Avoid Foreign AP Interference
Refer to the exhibit. Global multicast has been configured for multicast-multicast, but multicast is not functioning on any of the WLANs in the network. Which action enables multicast?
A. Set the AP to local.
B. Set the radio policy to All on the WLAN.
C. Enable the Multicast VLAN feature.
D. Enable WLAN advanced settings to support multicast-multicast mode.
A customer must use deep-packet inspection on the Cisco Catalyst 9800 Series Wireless Controller. The details must include all wireless client use details. Where must AVC be configured to meet this requirement?
A. AP join tag
B. policy profile
C. RF tag
D. WLAN
Free Access Full 300-430 Practice Test Free Questions
If you’re looking for more 300-430 practice test free questions, click here to access the full 300-430 practice test.
We regularly update this page with new practice questions, so be sure to check back frequently.
Good luck with your 300-430 certification journey!