300-415 Practice Exam Free – 50 Questions to Simulate the Real Exam
Are you getting ready for the 300-415 certification? Take your preparation to the next level with our 300-415 Practice Exam Free – a carefully designed set of 50 realistic exam-style questions to help you evaluate your knowledge and boost your confidence.
Using a 300-415 practice exam free is one of the best ways to:
- Experience the format and difficulty of the real exam
- Identify your strengths and focus on weak areas
- Improve your test-taking speed and accuracy
Below, you will find 50 realistic 300-415 practice exam free questions covering key exam topics. Each question reflects the structure and challenge of the actual exam.
Which two actions must be taken to allow certain department to require firewall protection when interacting with data center networks without including other departments? (Choose two.)
A. Use classification, policing, and marking
B. Advertise to vSmart controllers.
C. The regional hub advertises the availability of the firewall service.
D. Apply data policies at vEdge.
E. Deploy a service-chained firewall service per VPN.
Which website allows access to visualize the geography screen from vManager using the internet?
A. *.globalstreetmaps.org
B. *.fullstreetmaps.org
C. *.callstreetmaps.org
D. *.openstreetmaps.org
An engineer modifies a data policy for DIA in VPN 200 to meet the requirements for traffic destined to these locations: · external networks; must be translated · external networks; must use a public TLOC color · syslog servers, must use a private TLOC color Here is the existing data policy configuration:Which policy configuration sequence set meets the requirements?
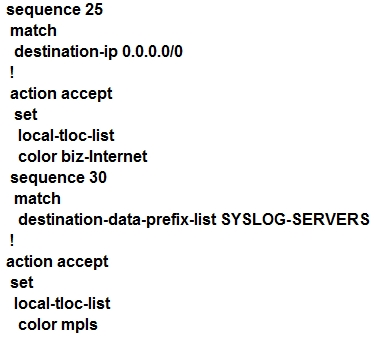

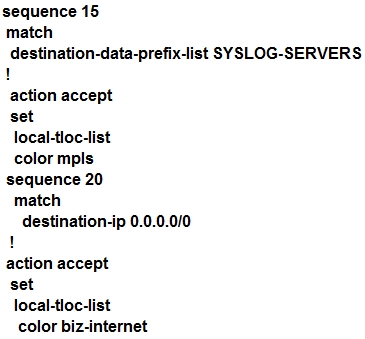
A.
Which component is responsible for routing protocols such as BGP and OSPF in a Cisco SD-WAN solution?
A. vSmart Controller
B. WAN Edge Router
C. vManage
D. vBond Orchestrator
Which component of the Cisco SD-WAN architecture oversees the control plane of overlay network to establish, adjust, and maintain the connections between the WAN Edge devices that form the Cisco SD-WAN fabric?
A. APIC-EM
B. vSmart
C. vManage
D. vBond
An organization wants to discover, monitor, and track the applications running on the WAN Edge device on the LAN. Which configuration achieves the goal?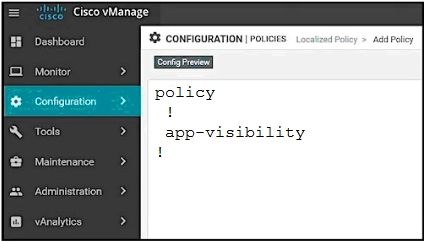

A. C
Refer to the exhibit. Which shaping-rate does the engineer use to shape traffic at 9 Mbps?
A. 9
B. 9000
C. 90000
D. 9000000
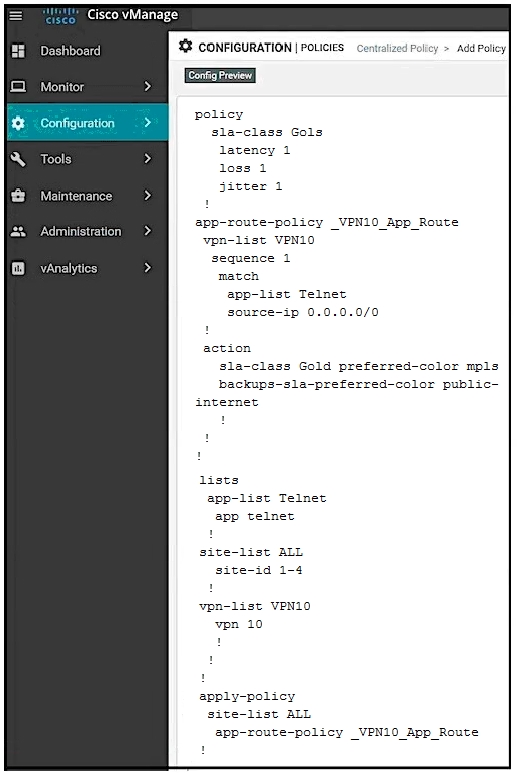
Refer to the exhibit. An organization is testing a Cisco SD-WAN solution and decided to have the control plane established first and not the data plane at the time of migration. Which configuration achieves this goal?

A.
Which routing protocol is used to exchange control plane information between vSmart controllers and WAN Edge routers in the Cisco SD-WAN secure extensible network?
A. BGP
B. OSPF
C. BFD
D. OMP
Refer to the exhibit.A network administrator is configuring OSPF advanced configuration parameters from a template using the vManager GUI for a branch WAN Edge router to calculate the summary routes to an ASBR. Which action achieves this configuration?
A. Enable Originate.
B. Disable RFC 1583 Compatible.
C. Disable Originate.
D. Enable RFC 1583 Compatible.
How is multicast routing enabled on devices in the Cisco SD-WAN overlay network?
A. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as speci ed in the original PIM join message.
B. The WAN Edge routers originate multicast service routes to the vSmart controller via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as speci ed in the original PIM join message.
C. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v1 or v2 toward the source or PIM-RP as speci ed in the original PIM join message.
D. The vSmart controller originates multicast service routes to the WAN Edge routers via OMP, which then forwards joins for requested multicast groups based on IGMP v2 or v3 toward the source or PIM-RP as speci ed in the original PIM join message.
Which protocol does vManage use to provision the WAN Edge device during the onboarding process?
A. RESTCONF
B. NETCONF
C. EPP
D. HTTPS
How is the software managed in Cisco SD-WAN?
A. Software upgrade operation in the group must include vManage, vBond, and vSmart.
B. Software downgrades are unsupported for vManage.
C. Software images must be uploaded to vManage through HTTP or FTP.
D. Software images must be transferred through VPN 512 or VPN 0 of vManage.
Which set of elements are verified by the controller to confirm the identity of edge devices?
A. certificates, organization name, and serial number of the device
B. organization name, serial number, and system IP of the device
C. certificates, organization name, and vBond domain
D. certificates, system IP, and vBond domain
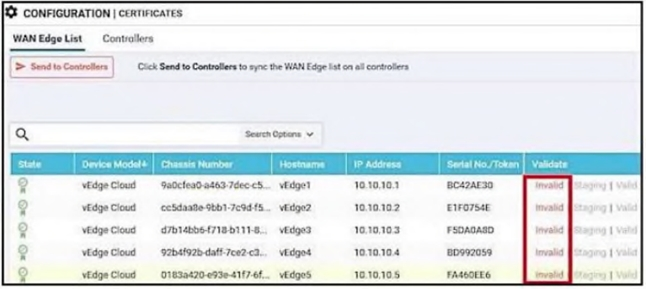
Refer to the exhibit. vManage logs are available for the past few months. A device name change was deployed mistakenly at a critical site. How is the device name change tracked by operations and design teams?



What are the two components of an application-aware firewall? (Choose two.)
A. default action
B. sequence
C. zone pair
D. lists
E. firewall policy
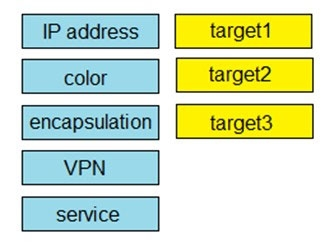
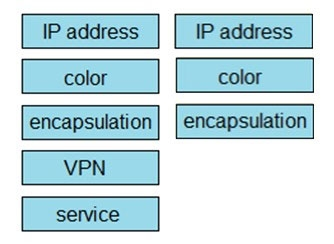
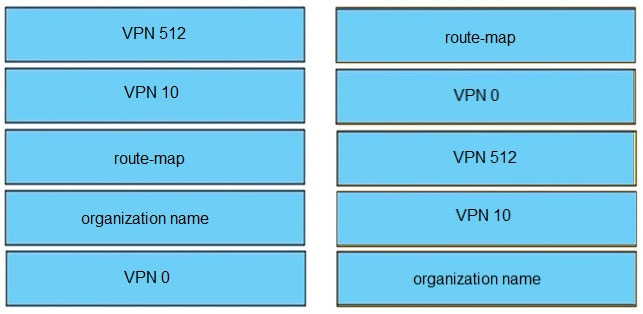
Drag and drop the attributes from the left that make each transport location unique onto the right. Not all options are used.
Select and Place:
Which two types of SGT propagation are supported by Cisco TrustSec? (Choose two.)
A. key chain
B. offline tagging
C. SXP
D. reconciliation
E. inline tagging
How many subnets are necessary in Azure VNet for a WAN Edge device to function in the cloud deployment?
A. CSR is the WAN Edge device that is supported in the Microsoft cloud. The Microsoft underlay cloud fabric performs the management function.
B. There must be three subnets in VNet: management, public, and services.
C. One public subnet is required in VNet. The Microsoft underlay cloud fabric performs all of the routing functions for WAN Edge.
D. Public and services subnets are required in VNet. The Microsoft underlay cloud fabric performs the management function.
Two sites have one WAN Edge each. Each WAN Edge has two public TLOCs with no restrict configured. There is full reachability between the TLOCs. How many data tunnels are formed on each WAN Edge router?
A. 6
B. 2
C. 4
D. 8
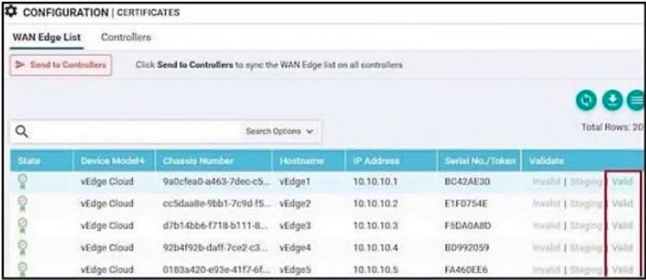
Which two different states of a WAN Edge certificate are shown on vManage? (Choose two.)
A. active
B. inactive
C. staging
D. provisioned
E. invalid
Drag and drop the functions from the left onto the correct templates on the right.
Select and Place:

Which Cisco SD-WAN component centralizes policy configuration?
A. Cisco DNA Center
B. vBond
C. WAN Edge
D. vSmart
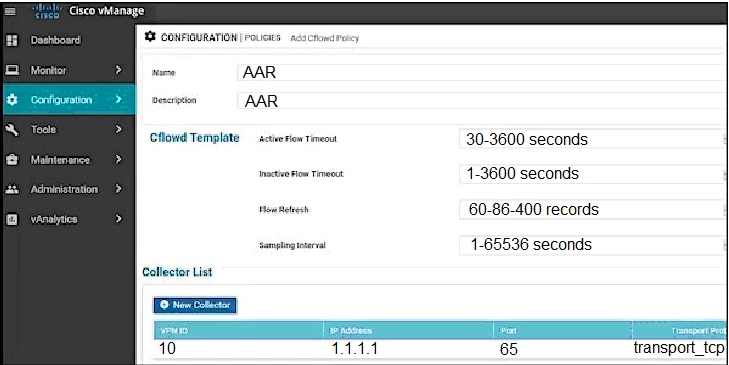
An engineer is configuring a data policy for packets that must be captured through the policy. Which command accomplishes this task?
A. policy > data-policy > vpn-list > sequence > default-action > accept
B. policy > data-policy > vpn-list > sequence > match
C. policy > data-policy > vpn-list > sequence > action
D. policy > data-policy > vpn-list > sequence > default-action > drop
Which component is used for stateful inspection of TCP, UDP, and ICMP ows in Cisco SD-WAN firewall policies?
A. subnets
B. sites
C. interfaces
D. zones
A policy is created to influence routing path in the network using a group of prefixes. Which policy application will achieve this goal when applied to a site list?
A. control-policy
B. vpn-membership policy
C. app-route policy
D. c owd-template
Which value is verified in the certificates to confirm the identity of the physical WAN Edge device?
A. Serial Number
B. OTP
C. System-IP
D. Chassis-ID
Which two mechanisms are used by vManage to ensure that the certificate serial number of the WAN Edge router that is needed to authenticate is listed in the WAN Edge Authorized Serial Number list? (Choose two.)
A. Synchronize to the PnP.
B. The vManage is shipped with the list.
C. Synchronize to the Smart Account.
D. Manually upload it to vManage.
E. The devices register to vManage directly as the devices come online.
Which protocol runs between the vSmart controllers and WAN Edge routers when the vSmart controller acts like a route reflector?
A. IPsec inside the DTLS/TLS control connection
B. BGP inside the DTLS/TLS
C. OMP outside the DTLS/TLS control connection
D. OMP inside the DTLS/TLS control connection
What is the default value for the number of paths advertised per prefix in the OMP feature template?
A. 4
B. 8
C. 12
D. 16
How many concurrent sessions does a vManager REST API have before it invalidates the least recently used session if the maximum concurrent session number is reached?
A. 150
B. 200
C. 250
D. 300
Refer to the exhibit. An administrator is configuring a policy in addition to an existing hub-and-spoke policy for two sites that should directly communicate with each other. How is this policy configured?
A. mesh
B. custom control (route and TLOC)
C. hub-and-spoke
D. import existing topology
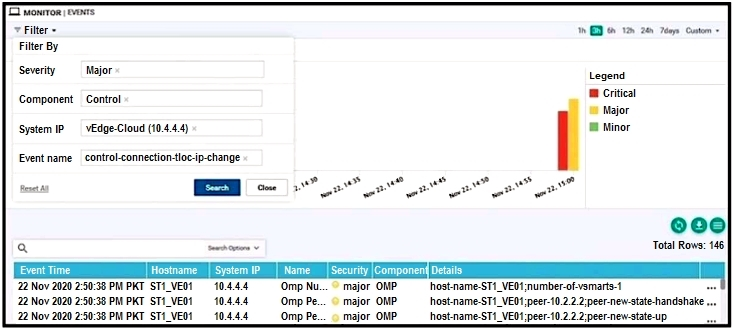
Refer to the exhibit. The control connection is failing. Which action resolves the issue?
A. Validate the certificates authenticity on vSmart
B. Restore the reachability to the vSmart
C. Import vSmart in vManager
D. Upload the WAN Edge list on vManage
When software is upgraded on a vManage NMS, which two image-adding options store images in a local vManage software repository? (Choose two.)
A. To be downloaded over an ICMP connection
B. To be downloaded over a SNMP connection
C. To be downloaded over a control plane connection
D. To be downloaded over an out-of-band connection
E. To be downloaded over a SMTP connection
What prohibits deleting a VNF image from the software repository?
A. if the image is stored by vManage
B. if the image is referenced by a service chain
C. if the image is included in a configured policy
D. if the image is uploaded by a WAN Edge device
Which Cisco SD-WAN component facilitates the initial communication between WAN Edge devices to join the fabric?
A. WAN Edge Router
B. vSmart Controller
C. vManage
D. vBond Orchestrator
Which SD-WAN devices require multicast PIM and IGMP configurations when setting up SD-WAN multicast?
A. datacenter replicator devices
B. datacenter devices with multicast sources
C. branch devices with multicast receivers
D. branch devices with unicast traffic
Which process is continued by Cisco SD-WAN when packet duplication is enabled?
A. Additional headers are added to outgoing packets to perform custom routing policies.
B. Dynamic traffic is compressed and signaled before it is forwarded though the WAN.
C. Copies of packets are sent over multiple WAN circuits to overcome packet loss.
D. Application traffic is analyzed to find patterns and enable custom detection rules.
What is the role of the Session Traversal Utilities for NAT server provided by the vBond orchestrator?
A. It prevents SD-WAN Edge routers from forming sessions with public transports among different service providers.
B. It facilitates SD-WAN Edge routers to stay behind a NAT-enabled firewall while the transport addresses of the SD-WAN controller are unNAT-ed.
C. It allows WAN Edge routers to form sessions among MPLS TLOCs using only public IP addresses.
D. It facilitates SD-WAN routers and controllers to discover their own mapped or translated IP addresses and port numbers.
Refer to the exhibit. An engineer is troubleshooting a control connection issue on a WAN Edge device that shows socket errors. The packet capture shows some ICMP packets dropped between the two devices. Which action resolves the issue?
A. Remove IP duplication in the network and configure a unique IP address.
B. Recover vBond or wait for the controller to reload, which could be caused by a reset.
C. Recover the vManage controller that is down in a high availability cluster.
D. Change the system IP or restart the WAN Edge if the system IP is changed.
Which REST API call is used for real-time monitoring of application-aware routing?
A. history
B. SLA class
C. event
D. alarm
Which two requirements must be met for DNS inspection when integrating with Cisco Umbrella? (Choose two.)
A. Attach security policy to the device template.
B. Create and attach a System feature template with the Umbrella registration credentials.
C. Register and configure the vManage public IP and serial number in the Umbrella portal.
D. Upload the WAN Edge serial allow list to the Umbrella portal.
E. configure the Umbrella token on the vManage.
Which two platforms for the Cisco SD-WAN architecture are deployable in a hypervisor on-premises or in IAAS Cloud? (Choose two.)
A. CSR 1000v
B. ISR 4431
C. vEdge 100c
D. vEdge 2000
E. vEdge Cloud
Which policy tracks path characteristics such as loss, latency, and jitter in vManage?
A. VPN
B. control
C. app-route
D. data
Which policy blocks TLOCs from remotes and allows TLOCs from the data center to form hub-and-spoke peering?
A. centralized data policy
B. localized control policy
C. centralized control policy
D. localized data policy
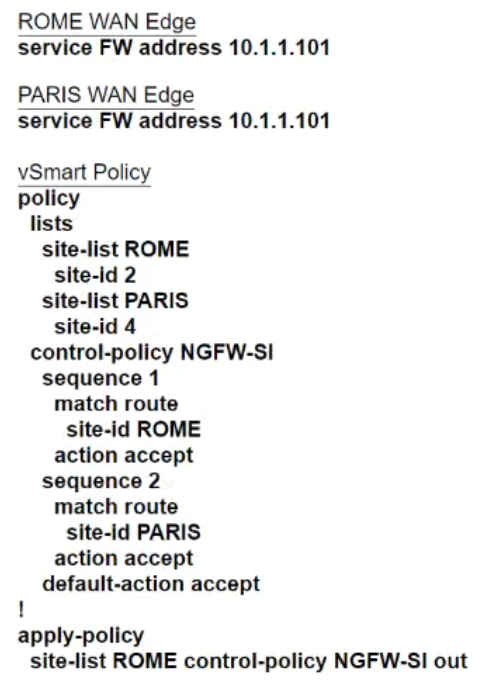
Refer to the exhibit. The Cisco SD-WAN is deployed using the default topology. The engineer wants to configure a service insertion policy such that all data traffic between Rome to Paris is forwarded through the NGFW located in London. Which configuration fulfills this requirement, assuming that the Service VPN ID is 1?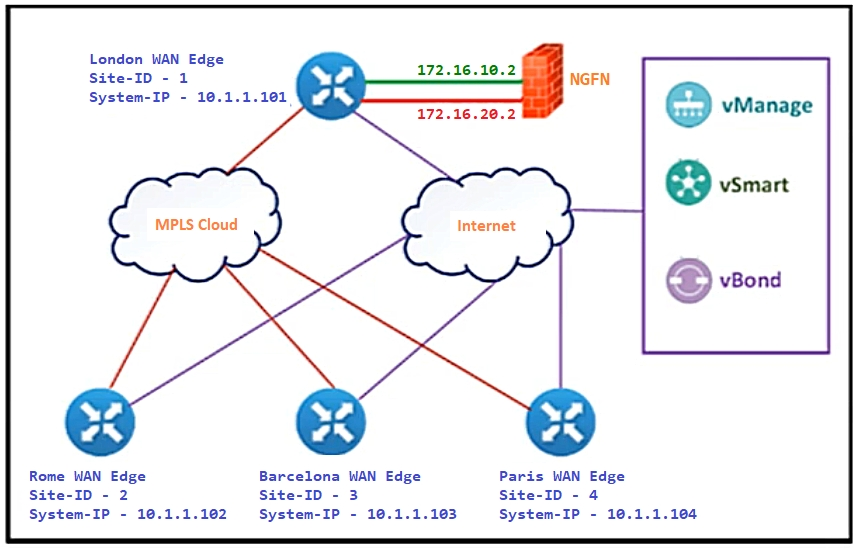
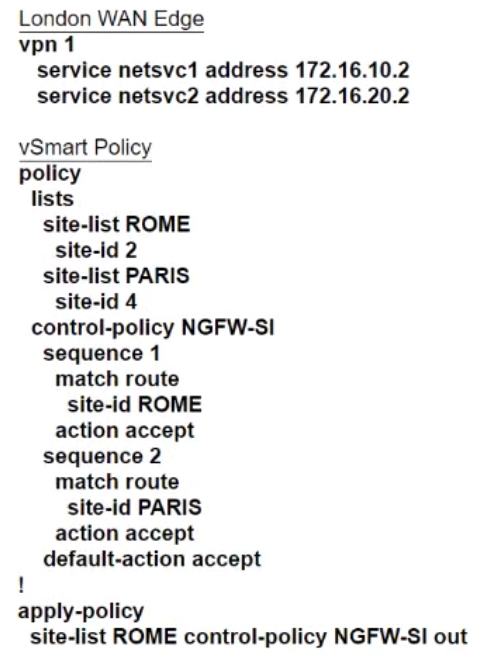


A.
Which action is performed during the onboarding process when a WAN Edge router is connected to ZTP server ztp.viptela.com?
A. The router is connected to WAN Edge Cloud Center.
B. The router receives its vBond Orchestrator information.
C. The router is synced with vSmart Controller via an IPsec tunnel.
D. The router is connected to vSmart Controller via a DTLS/TLS tunnel.
How many vManage NMSs should be installed in each domain to achieve scalability and redundancy?
A. two clusters
B. two instances
C. two or more in a cluster
D. three or more in a cluster
Which protocol is used by the REST API to communicate with network devices in the Cisco SD-WAN network?
A. HTTP
B. SSL
C. IPsec
D. SSH
How is an event monitored and reported for an individual device in the overlay network at site ID:S4300T6E43F36?
A. The device sends event notifications to vManage.
B. The device sends notifications to vSmart that sends them to vManage.
C. The device sends a critical alarm of events to vManage.
D. The device sends a critical alarm to vSmart that sends it to vManage.
Free Access Full 300-415 Practice Exam Free
Looking for additional practice? Click here to access a full set of 300-415 practice exam free questions and continue building your skills across all exam domains.
Our question sets are updated regularly to ensure they stay aligned with the latest exam objectives—so be sure to visit often!
Good luck with your 300-415 certification journey!