300-410 Exam Prep Free – 50 Practice Questions to Get You Ready for Exam Day
Getting ready for the 300-410 certification? Our 300-410 Exam Prep Free resource includes 50 exam-style questions designed to help you practice effectively and feel confident on test day
Effective 300-410 exam prep free is the key to success. With our free practice questions, you can:
- Get familiar with exam format and question style
- Identify which topics you’ve mastered—and which need more review
- Boost your confidence and reduce exam anxiety
Below, you will find 50 realistic 300-410 Exam Prep Free questions that cover key exam topics. These questions are designed to reflect the structure and challenge level of the actual exam, making them perfect for your study routine.
Which of the following are commonly used ports when implementing RADIUS based authentication and accounting? (Choose two.)
A. UDP port 1644 for authentication
B. UDP port 1812 for authentication
C. TCP port 1812 for authentication
D. UDP port 1813 for accounting
E. TCP port 1813 for accounting
F. UDP port 1644 for accounting
Refer to the exhibit. An administrator must upload the packages.conf file to an FTP server. However, the FTP server rejected anonymous service and required users to authenticate. What are the two ways to resolve the issue? (Choose two.)
A. Use the copy flash:packages.conf scp: command instead, and enter the FTP server credentials when prompted.
B. Use the copy flash:packages.conf ftp: command instead, and enter the FTP server credentials when prompted.
C. Enter the FTP server credentials directly in the FTP URL using the ftp://username:password@192.0.2.40/ syntax.
D. Create a user on the router matching the username and password on the FTP server and log in before attempting the copy.
E. Use ip ftp username and ip ftp password configuration commands to specify valid FTP server credentials.
Which routing protocol is used by the PE router to advertise routes to a CE router without redistribution or static after removing the RD tag from the P router?
A. OSPF
B. BGP IPv4
C. IS-IS
D. MP-BGP
Refer to the exhibit. The network administrator configured BGP as the backup route for 10.0.0.0/8 and it should work only when EIGRP 10.0.0.0/8 failed to install for site S4248T5E130F6. Which configuration resolves the issue?
A. configure terminal
router eigrp 1
distance eigrp 90 170
B. configure terminal
router eigrp 1
redistribute bgp metric 10000 1 255 1 1500
C. configure terminal
ip route 10.0.0.0 255.0.0.0 192.168.90.2
D. configure terminal
router eigrp 1
distance eigrp 10 170
The network administrator configured CoPP so that all HTTP and HTTPS traffic from the administrator device located at 172.16 1.99 toward the router CPU is limited to 500 kbps. Any traffic that exceeds this limit must be dropped. access-list 100 permit ip host 172.16.1.99 any ! class-map CM-ADMIN match access-group 100 policy-map PM-COPP class CM-ADMIN police 500000 conform-action transmit interface E0/0 service-policy input PM-COPP CoPP failed to capture the desired traffic and the CPU load is getting higher. Which two configurations resolve the issue? (Choose two.)
A. interface E0/0 no service-policy input PM-COPP ! control-plane service-policy input PM-COPP
B. policy-map PM-COPP class CM-ADMIN no police 500000 conform-action transmit police 500 conform-action transmit ! control-plane service-policy input PM-COPP
C. no access-list 100 access-list 100 permit tcp host 172.16.1.99 any eq 80
D. no access-list 100 access-list 100 permit tcp host 172.16.1.99 any eq 80 access-list 100 permit tcp host 172.16.1.99 any eq 443
E. policy-map PM-COPP class CM-ADMIN no police 500000 conform-action transmit police 500 conform-action transmit A
Which configuration feature should be used to block rogue router advertisements instead of using the IPv6 Router Advertisement Guard feature?
A. VACL blocking broadcast frames from nonauthorized hosts
B. PVLANs with promiscuous ports associated to route advertisements and isolated ports for nodes
C. PVLANs with community ports associated to route advertisements and isolated ports for nodes
D. IPv4 ACL blocking route advertisements from nonauthorized hosts
Refer to the exhibit. A network engineer notices that R1 and R2 cannot establish an eBGP peering. The following messages appear in the log:
Which configuration must the engineer apply to R1 to restore the eBGP peering?
A. 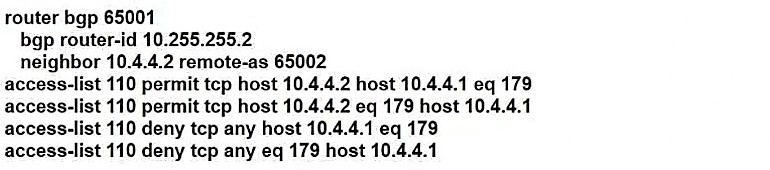
B. 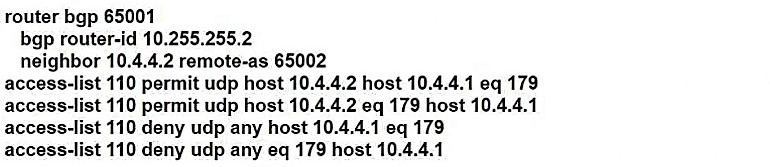
C. 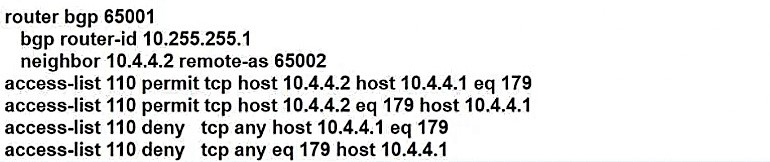
D. D
Refer to the exhibit. An engineer must advertise LAN network 192.168.1.0 of router A to router B through OSPF. The engineer notices that router B was configured, but the LAN network of router A is not in the routing table of router B. Which configuration on router A resolves the problem?
A.

B.

C.

D.

Refer to the exhibit. Which control plane policy limits BGP traffic that is destined to the CPU to 1 Mbps and ignores BGP traffic that is sent at higher rate?
A. policy-map SHAPE_BGP
B. policy-map LIMIT_BGP
C. policy-map POLICE_BGP
D. policy-map COPP
Refer to the exhibit. R1 is configured with IP SLA to check the availability of the server behind R6 but it kept failing. Which configuration resolves the issue?
A. R6(config)#ip sla responder udp-echo ip address 10.10.10.1 port 5000
B. R6(config)#ip access-list extended DDOS R6(config-ext-nacl)#5 permit icmp host 10.10.10.1 host 10.66.66.66
C. R6(config)#ip sla responder
D. R6(config)#ip access-list extended DDOS R6(config-ext-nacl)#5 permit icmp host 10.66.66.66 host 10.10.10.1 B
Which Layer 3 VPN attribute allows different customers to connect to the same MPLS network with overlapping IP ranges?
A. RT
B. RD
C. VRF
D. MP-BGP
Refer to the exhibit. An administrator configured a Cisco router for TACACS authentication, but the router is using the local enable password instead. Which action resolves the issue?
A. configure the aaa authentication login default group admin local if-authenticated command instead.
B. configure the aaa authentication login admin group tacacs+ local enable none command instead.
C. configure the aaa authentication login admin group tacacs+ local if-authenticated command instead.
D. configure the aaa authentication login admin group admin local enable command instead.
How do devices operate in MPLS L3VPN topology?
A. P routers provide connectivity between PE devices with MPLS switching.
B. P and associated PE routers with IGP populate the VRF table in different VPNs.
C. CE routers connect to the provider network and perform LSP functionality.
D. P routers support PE to PE VPN tunnel without LSP functionality.

Refer to the exhibit. Which configuration resolves the route filtering issue on R1 to redistribute all the routes except 172.16.2.48/28?
A.

B.

C.

D.

Refer to the exhibit. The network engineer configured the summarization of the RIP routes into the OSPF domain on R5 but still sees four different 172.16.0.0/24 networks on R4. Which action resolves the issue?
A. R5(config)#router ospf 99 –
R5(config-router)#network 172.16.0.0 0.255.255.255 area 56
R5(config-router)#area 56 range 172.16.0.0 255.255.255.0
B. R5(config)#router ospf 1 –
R5(config-router)#no area –
R5(config-router)#summary-address 172.16.0.0 255.255.252.0
C. R4(config)#router ospf 1 –
R4(config-router)#no area –
R4(config-router)#summary-address 172.16.0.0 255.255.252.0
D. R4(config)#router ospf 99 –
R4(config-router)#network 172.16.0.0 0.255.255.255 area 56
R4(config-router)#area 56 range 172.16.0.0 255.255.255.0
Refer to the exhibit. A user has set up an IP SLA probe to test if a non SLA host web server on IP address 10.1.1.1 accepts HTTP sessions prior to deployment. The probe is failing. Which action should the network administrator recommend for the probe to succeed?
A. Re-issue the ip sla schedule command.
B. Add the control disable option to the tcp connect.
C. Modify the ip sla schedule frequency to forever.
D. Add icmp-echo command for the host.
Refer to the exhibit. An IP SLA was configured on router R1 that allows the default route to be modified in the event that Fa0/0 loses reachability with the router R3 Fa0/0 interface. The route has changed to flow through router R2. Which debug command is used to troubleshoot this issue?
A. debug ip flow
B. debug ip sla error
C. debug ip routing
D. debug ip packet
Refer to the exhibit. A network administrator is trying to switch to the privileged EXEC level on R1 but failed. Which configuration resolves the issue?
A. enable password Cisco@123
B. tacacs-server enable-password Cisco@123
C. tacacs server enable-password Cisco@123
D. enable-password Cisco@123
Refer to the exhibit. Which action resolves the issue?
A. configure host IP address in access-list 16.
B. configure SNMPv3 on the router.
C. configure SNMP authentication on the router.
D. configure a valid SNMP community string.
Refer to the exhibit. The 130.130.130.0/24 route shows in the R2 routing table but is getting filtering toward R3. Which action resolves the issue?
A. Automatic route summarization must be enabled on R2.
B. The outgoing filter list for all interfaces must be set on R2.
C. The incoming filter list for all interfaces must be set on R2.
D. IGP synchronization must be disabled on R2.
Which statement about MPLS LDP router ID is true?
A. If not configured, the operational physical interface is chosen as the router ID even if a loopback is configured.
B. The loopback with the highest IP address is selected as the router I
C. The MPLS LDP router ID must match the IGP router I
D. The force keyword changes the router ID to the speci ed address without causing any impact.
Which technique removes the outermost label of an MPLS-tagged packet before the packet is forwarded to an adjacent LER?
A. explicit-null
B. PHP
C. label swap
D. label imposition
Refer to the exhibit. An engineer implemented CoPP to limit Telnet traffic to protect the router CPU. It was noticed that the Telnet traffic did not pass through CoPP. Which configuration resolves the issue?
A. ip access-list extended TELNET permit tcp host 10.2.2.1 host 10.2.2.4 eq telnet permit tcp host 10.1.1.1 host 10.1.1.3 eq telnet
B. policy-map COPP class TELNET police 8000 conform-action transmit exceed-action transmit
C. ip access-list extended TELNET permit tcp host 10.2.2.4 host 10.2.2.1 eq telnet permit tcp host 10.1.1.3 host 10.1.1.1 eq telnet
D. policy-map COPP class TELNET police 8000 conform-action transmit exceed-action transmit violate-action drop
How does BFD protocol work?
A. When BFD declares a failure on the primary IGP path, the router on the peer router chooses to use the secondary path.
B. BFD operates on the route processor module and impacts the route processor CPU utilization.
C. BFD control packets are sent via UDP port 3784 to the destination router.
D. BFD echo packets are sent to the same source IP and different destination IP with TCP port of 3786.
Which feature minimizes DoS attacks on an IPv6 network?
A. IPv6 Binding Security Table
B. IPv6 Router Advertisement Guard
C. IPv6 prefix Guard
D. IPv6 Destination Guard
Refer to the exhibit. When an FTP client attempts to use passive FTP to connect to the FTP server, the file transfers fail. Which action resolves the issue?
A. Modify traffic filter FTP-SERVER in to the outbound direction.
B. configure active FTP traffic.
C. configure to permit TCP ports higher than 1023.
D. Modify FTP-SERVER access list to remove established at the end.
Which of the following are valid fields in an MPLS header? (Choose four.)
A. Label
B. Sequence Number
C. Experimental (Exp)
D. Bottom of Stack (BoS)
E. Time to Live (TTL)
F. Checksum
, C, D, E
Which transport layer protocol is used to form LDP sessions?
A. UDP
B. SCTP
C. TCP
D. RDP
The network administrator must configure R1 to authenticate Telnet connections based on Cisco ISE using RADIUS. ISE has been configured with an IP address of 192.168.1.5 and with a network device pointing toward R1 (192.168.1.1) with a shared secret password of Cisco123. The administrator has configured this on R1: aaa new-model radius server ISE1 address ipv4 192.168.1.5 key Cisco123 aaa group server tacacs+ RAD-SERV server name ISE1 aaa authentication login default group RAD-SERV The network administrator cannot authenticate to access R1 based on IS
A. Which set of configurations xes the issue?
B. line vty 0 4
login authentication RAD-SERV
C. aaa group server tacacs+ ISE1
server name RAD-SERV
D. aaa group server radius RAD-SERV
server name ISE1
E. line vty 0 4
login authentication default
Refer to the exhibit.An engineer configured SNMP communities on the Core_Sw1, but the SNMP server cannot obtain information from Core_Sw1. Which configuration resolves this issue?
A. access-list 20 permit 10.221.10.11
B. snmp-server group NETADMIN v3 priv read NETVIEW write NETADMIN access 22
C. snmp-server group NETVIEW v2c priv read NETVIEW access 20
D. access-list 20 permit 10.221.10.12
The SNMP server configuration ties ACL 20 to the list of allowed SNMP servers that can pull data from the switch. The IP address of the NMS server needs to be added to this ACL.
Refer to the Exhibit. The access-lists are configured on the network device. There is a server behind the network device. User are trying to access the server securely however they are not able to access it. What changes would you recommend to the above configuration?
A. Permit tcp port 465
B. Permit tcp port 3389
C. Permit tcp port 443
D. Permit tcp any any
Refer to the exhibit. R1 should receive 10.16.2.0/24 from R2. Which action resolves the issue?
A. Add prefix-list seq 1 on R1 to permit 10.16.0.0/22.
B. Add prefix-list seq 1 on R1 to permit 10.16.2.0/24.
C. Modify prefix-list seq 5 on R2 to permit 10.16.0.0/22.
D. Modify prefix-list seq 5 on R2 to permit 10.16.0.0/23.
What is the function of BFD?
A. It creates high CPU utilization on hardware deployments
B. It provides uniform failure detection on the same media type
C. It provides uniform failure detection regardless of media type
D. It negotiates to the highest version if the neighbor version differs
Refer to the exhibit.A network administrator is trying to access a branch router using TACACS+ username and password credentials, but the administrator cannot log in to the router because the WAN connectivity is down. The branch router has following AAA configuration: aaa new-model aaa authorization commands 15 default group tacacs+ aaa accounting commands 1 default stop-only group tacacs+ aaa accounting commands 15 default stop- only group tacacs+ tacacs-server host 10.100.50.99 tacacs-server key Ci$co123 Which command will resolve this problem when WAN connectivity is down?
A. aaa authentication login console group tacacs+ enable
B. aaa authentication login default group tacacs+ local
C. aaa authentication login default group tacacs+ enable
D. aaa authentication login default group tacacs+ console
Refer to the exhibit. The client received the IPv6 address from the IPv6 DHCP server but the show command does not show the IPv6 DHCP bindings on the server. Which action resolves the issue?
A. Extend the DHCP lease time because R1 removed the IPv6 address earlier after the lease expired.
B. configure H1 as the DHCP client that manually assigns the IPv6 address on interface e0/0.
C. configure authorized DHCP servers to avoid IPv6 addresses from a rogue DHCP server.
D. Use the 2001:DBB:BAD:CODE::/64 prefix for the DHCP pool on R1.
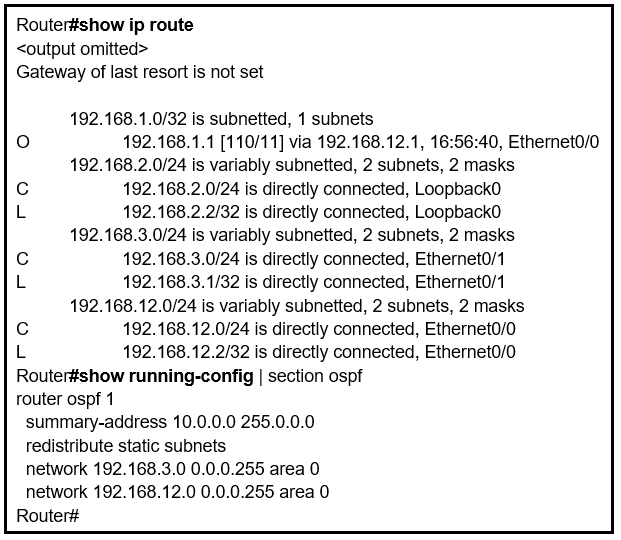
Refer to the exhibit. An engineer is trying to generate a summary route in OSPF for network 10.0.0.0/8, but the summary route does not show up in the routing table. Why is the summary route missing?
A. The summary-address command is used only for summarizing prefixes between areas.
B. The summary route is visible only in the OSPF database, not in the routing table.
C. There is no route for a subnet inside 10.0.0.0/8, so the summary route is not generated.
D. The summary route is not visible on this router, but it is visible on other OSPF routers in the same area.
A network administrator is troubleshooting a high utilization issue on the route processor of a router that was reported by NMS. The administrator logged into the router to check the control plane policing and observed that the BGP process is dropping a high number of routing packets and causing thousands of routes to recalculate frequently. Which solution resolves this issue?
A. Shape the pir for BGP, conform-action set-prec-transmit, and exceed action set-frde-transmit.
B. Police the pir for BGP, conform-action set-prec-transmit, and exceed action set-clp-transmit.
C. Shape the cir for BGP, conform-action transmit, and exceed action transmit.
D. Police the cir for BGP, conform-action transmit, and exceed action transmit.
Refer to the exhibit. After recovering from a power failure, Ethernet0/1 stayed down while Ethernet0/0 returned to the up/up state. The default route through ISP1 was not reinstated in the routing table until Ethernet0/1 also came up. Which action resolves the issue?
A. Add a static route to the 8.8.8.8/32 destination through the next hop 203.0.113.1.
B. Remove the references to the interface names from both static default routes.
C. Reference the track object 1 in both static default routes.
D. configure the default route through ISP1 with a higher administrative distance than 2.
Refer to the exhibit.BGP and EIGRP are mutually redistributed on R3, and EIGRP and OSPF are mutually redistributed on R1. Users report packet loss and interruption of service to applications hosted on the 10.1.1.0/24 prefix. An engineer tested the link from R3 to R4 with no packet loss present but has noticed frequent routing changes on R3 when running the debug ip route command. Which action stabilizes the service?
A. Reduce frequent OSPF SPF calculations on R3 that cause a high CPU and packet loss on traffic traversing R3.
B. Tag the 10.1.1.0/24 prefix and deny the prefix from being redistributed into OSPF on R1.
C. Place an OSPF distribute-list outbound on R3 to block the 10.1.1.0/24 prefix from being advertised back to R3.
D. Repeat the test from R4 using ICMP ping on the local 10.1.1.0/24 prefix, and x any Layer 2 errors on the host or switch side of the subnet.
Refer to the exhibit. Which two actions restrict access to router R1 by SSH? (Choose two.)
A. Remove class-map ANY from service-policy CoPP.
B. configure transport output ssh on line vty and remove sequence 20 from access list 100.
C. configure transport input ssh on line vty and remove sequence 30 from access list 100.
D. Remove sequence 10 from access list 100 and add sequence 20 deny tcp any any eq telnet to access list 199.
E. configure transport output ssh on line vty and remove sequence 10 from access list 199.
Refer to the exhibit. Spoke routers do not learn about each other's routes in the DMVPN Phase2 network. Which action resolves the issue?
A. Disable EIGRP split horizon on the Tunnel0 interface of the hub router.
B. Rectify incorrect wildcard mask configured on the hub router network command.
C. Configure a static route in each spoke to establish a spoke-to-spoke tunnel.
D. Remove default route from spoke routers to establish a spoke-to-spoke tunnel.
Refer to the exhibit. A network administrator wants to block all traffic toward the Internet after business hours and on weekends. When the administrator applies an access list on interface Gi0/1, all traffic is blocked and there is no access to the Internet at any time. Which action resolves the issue?
A. Add the permit ip any any time-range no-conn statement after the deny udp any any time-range no-conn command in the access list.
B. Add the permit ip any any statement after the deny icmp any any time-range no-conn command in the access list.
C. Add the permit allowed time-range no-conn statement after the deny icmp any any time-range no-conn command in the access list.
D. Add the permit ip any any time-range no-conn statement after the deny icmp any any time-range no-conn command in the access list.
Refer to the exhibit. A client is concerned that passwords are visible when running this show archive log config all. Which router configuration is needed to resolve this issue?
A. MASS-RTR(config)#aaa authentication arap
B. MASS-RTR(config-archive-log-cfg)#password encryption aes
C. MASS-RTR(config)#service password-encryption
D. MASS-RTR(config-archive-log-cfg)#hidekeys
A customer requested a GRE tunnel through the provider network between two customer sites using loopback to hide internal networks. Which configuration on R2 establishes the tunnel with R1?
A. R2(config)#interface Tunnel1 R2(config-if)#ip address 172.20.1.2 255.255.255.0 R2(config-if)#ip mtu 1400 R2(config-if)#ip tcp adjust-mss 1360 R2(config-if)#tunnel source 192.168.20.1 R2(config-if)#tunnel destination 192.168.10.1
B. R2(config)#interface Tunnel1 R2(config-if#ip address 172.20.1.2 255.255.255.0 R2(config-if)#ip mtu 1400 R2(config-if)#ip tcp adjust-mss 1360 R2(config-if)#tunnel source 10.10.2.2 R2(config-if)#tunnel destination 10.10.1.1
C. R2(config)#interface Tunnel1 R2(config-if)#ip address 172.20.1.2 255.255.255.0 R2(config-if)#ip mtu 1500 R2(config-if)#ip tcp adjust-mss 1360 R2(config-if)#tunnel source 10.10.2.2 R2(config-if)#tunnel destination 10.10.1.1
D. R2(config)#interface Tunnel1 R2(config-if)#ip address 172.20.1.2 255.255.255.0 R2(config-if)#ip mtu 1500 R2(config-if)#ip tcp adjust-mss 1360 R2(config-if)#tunnel source 192.168.20.1 R2(config-if)#tunnel destination 10.10.1.1 B
Refer to the exhibit. An engineer must configure PBR on R1 to reach to 10.2.2.0/24 via R3 AS64513 as the primary path and a backup route through default route via R2 AS64513. All BGP routes are in the routing table of R1, but a static default route overrides BGP routes. Which PBR configuration achieves the objective?
A. access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255 ! route-map PBR permit 10 match ip address 100 set ip next-hop recursive 10.3.3.1
B. access-list 100 permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0 ! route-map PBR permit 10 match ip address 100 set ip next-hop recursive 10.3.3.1
C. access-list 100 permit ip 10.1.1.0 0.0.0.255 10.2.2.0 0.0.0.255 ! route-map PBR permit 10 match ip address 100 set ip next-hop 10.3.3.1
D. access-list 100 permit ip 10.1.1.0 255.255.255.0 10.2.2.0 255.255.255.0 ! route-map PBR permit 10 match ip address 100 set ip next-hop 10.3.3.1
Refer to the exhibit. An engineer applied an IPv6 traffic filter on R1. The interface apped between R1 and R2 and clearing the BGP session did not restore the BGP session and failed. Which action must the engineer take to restore the BGP session from R2 to R1?
A. ICMPv6 must be permitted by the IPv6 traffic filter.
B. Swap the source and destination IP addresses in the IPv6 traffic filter.
C. Enable the BGP session, which went down when the session was cleared.
D. Apply the IPv6 traffic filter in the outbound direction on the interface.
Refer to the exhibits. London must reach Rome using a faster path via EIGRP if all the links are up, but it failed to take this path. Which action resolves the issue?
A. Change the administrative distance of RIP to 150.
B. Increase the bandwidth of the link between London and Barcelona.
C. Use the network statement on London to inject the 172.16.X.0/24 networks into EIGRP.
D. Use the network statement on Rome to inject the 172.16.X.0/24 networks into EIGRP.
Which of the following are used to validate the source of IPv6 traffic and are considered IPv6 layer 2 snooping features? (Choose two.)
A. DHCPv6 Guard
B. DHCPv6 Root Guard
C. IPv6 Source Guard
D. IPv6 prefix Guard
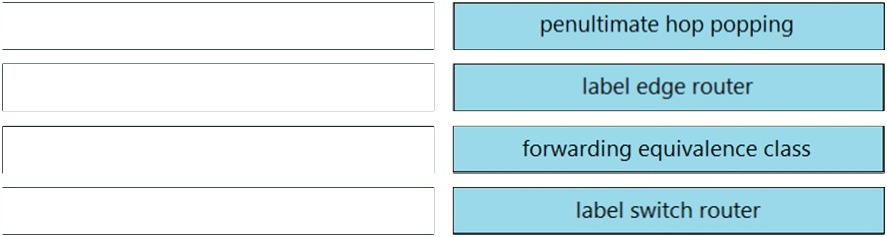
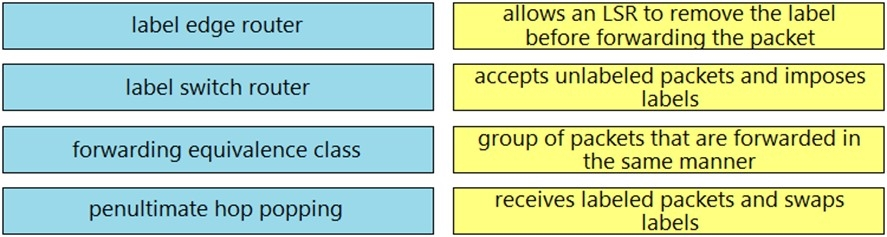
Drag and drop the MPLS concepts from the left onto the descriptions on the right.
Select and Place:
Refer to the exhibit. Users report that IP addresses cannot be acquired from the DHCP server. The DHCP server is configured as shown. About 300 total nonconcurrent users are using this DHCP server, but none of them are active for more than two hours per day. Which action xes the issue within the current resources?
A. Modify the subnet mask to the network 192.168.1.0 255.255.254.0 command in the DHCP pool
B. configure the DHCP lease time to a smaller value
C. configure the DHCP lease time to a bigger value
D. Add the network 192.168.2.0 255.255.255.0 command to the DHCP pool
Access Full 300-410 Exam Prep Free
Want to go beyond these 50 questions? Click here to unlock a full set of 300-410 exam prep free questions covering every domain tested on the exam.
We continuously update our content to ensure you have the most current and effective prep materials.
Good luck with your 300-410 certification journey!