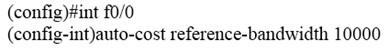300-101 Dump Free – 50 Practice Questions to Sharpen Your Exam Readiness.
Looking for a reliable way to prepare for your 300-101 certification? Our 300-101 Dump Free includes 50 exam-style practice questions designed to reflect real test scenarios—helping you study smarter and pass with confidence.
Using an 300-101 dump free set of questions can give you an edge in your exam prep by helping you:
- Understand the format and types of questions you’ll face
- Pinpoint weak areas and focus your study efforts
- Boost your confidence with realistic question practice
Below, you will find 50 free questions from our 300-101 Dump Free collection. These cover key topics and are structured to simulate the difficulty level of the real exam, making them a valuable tool for review or final prep.
Which technology was originally developed for routers to handle fragmentation in the path between end points?
A. PMTUD
B. MSS
C. windowing
D. TCP
E. global synchronization
Which two causes of latency are true? (Choose two.)
A. split horizon
B. propagation delay
C. serialization delay
D. high bandwidth on a link
E. under-utilization of a link
Which three items can you track when you use two time stamps with IP SLAs? (Choose three.)
A. delay
B. jitter
C. packet loss
D. load
E. throughput
F. path
Which protocol can you use to remotely install an IOS on a Cisco switch?
A. SFTP
B. NetFlow
C. FTP
D. SNMP
Which option is the best for protecting CPU utilization on a device?
A. fragmentation
B. COPP
C. ICMP redirects
D. ICMP unreachable messages
Which configuration command is used to enable EIGRP unequal-cost path load balancing?
A. maximum-paths
B. distance
C. metric
D. variance
E. default-metric
OSPF chooses routes in which order, regardless of route's administrative distance and metric?
A. Intra-Area (O) – Inter-Area (O IA) – External Type 1 (E1) – External Type 2 (E2) – NSSA Type 1 (N1) – NSSA Type 2 (N2)
B. Intra-Area (O) – Inter-Area (O IA) – NSSA Type 1 (N1) – NSSA Type 2 (N2) – External Type 1 (E1) – External Type 2 (E2)
C. Intra-Area (O) – Inter-Area (O IA) – NSSA Type 1 (N1) – External Type 1 (E1) – NSSA Type 2 (N2) – External Type 2 (E2)
D. Intra-Area (O) – NSSA Type 1 (N1) – External Type 1 (E1) – Inter-Area (O IA) – NSSA Type 2 (N2) – External Type 2 (E2)
E. Intra-Area (O) – Inter-Area (O IA) – NSSA Type 1 (N1) – External Type 1 (E1) – NSSA Type 2 (N2) – External Type 2 (E2)
F. NSSA Type 1 (N1) – NSSA Type 2 (N2) – Intra-Area (O) – Inter-Area (O IA) – External Type 1 (E1) – External Type 2 (E2) A
Prior to enabling PPPoE in a virtual private dialup network group, which task must be completed?
A. Disable CDP on the interface.
B. Execute the vpdn enable command.
C. Execute the no switchport command.
D. Enable QoS FIFO for PPPoE support.
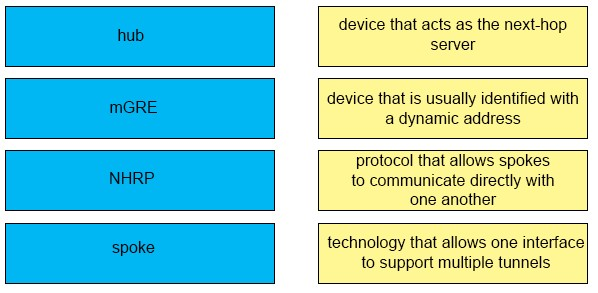
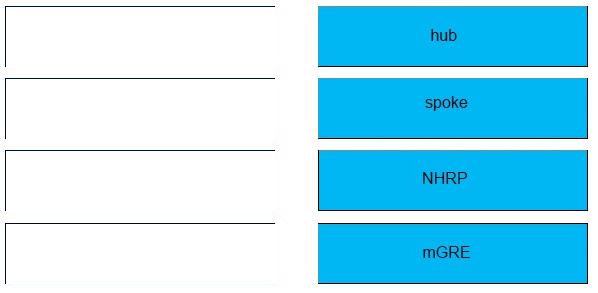
DRAG DROP - Drag and drop the DMVPN components from the left onto the correct descriptions on the right. Select and Place:
In EIGRP, when the IP default-network command is configured on a router, what is generated in the router`s configuration?
A. A static route
B. A directly connected route
C. An EIGRP route
A network engineer is configuring SNMP on network devices to utilize one-way SNMP notifications. However, the engineer is not concerned with authentication or encryption. Which command satisfies the requirements of this scenario?
A. router(config)#snmp-server host 172.16.201.28 traps version 2c CISCORO
B. router(config)#snmp-server host 172.16.201.28 informs version 2c CISCORO
C. router(config)#snmp-server host 172.16.201.28 traps version 3 auth CISCORO
If you want to migrate an IS-IS network to another routing protocol with a lower AD, which two protocols do you consider? (Choose two.)
A. RIP
B. UDP
C. TCP/IP
D. EIGRP
E. OSPF
F. internal BGP
Based on the configuration information shown above, which of the following are true? (Choose two)
A. will redistribute only clasfull routes
B. routes will be redistributed as E2
C. routes will be redistributed as N2
D. will redistribute all eigrp routes
Which feature can automatically assign IP addresses in a PPPoE environment?
A. DHCP
B. BOOTP
C. PPP
D. APIPA
Which ospf area prevent LSA type 4, LSA type 5? (Choose two.)
A. Not so stubby
B. Total stubby
C. Stubby area BC
When an EIGRP topology change is detected, what is the correct order of events when there is a FS?
A. The neighbor adjacency is deleted. The feasible route is used. DUAL is notified. Remove all topology entries learned from that neighbor.
B. DUAL is notified. Remove all topology entries learned from that neighbor. The neighbor adjacency is deleted. Routes enter the Active state and the feasible route is used.
C. The neighbor adjacency is deleted. Routes enter the Active state and the feasible route is used. DUAL is notified. Remove all topology entries learned from that neighbor.
D. DUAL is notified. The neighbor adjacency is deleted. Remove all topology entries learned from that neighbor.
What does the following access list, which is applied on the external interface FastEthernet 1/0 of the perimeter router, accomplish? router(config)#access-list 101 deny ip 10.0.0.0 0.255.255.255 any log router (config)#access-list 101 deny ip 192.168.0.0 0.0.255.255 any log router (config) #access-list 101 deny ip 172.16.0.0 0.15.255.255 any log router (config)#access-list 101 permit ip any any router (config)#interface fastEthernet 1/0 router (config-if)#ip access-group 101 in
A. It prevents incoming traffic from IP address ranges 10.0.0.0-10.0.0.255, 172.16.0.0- 172.31.255.255, 192.168.0.0-192.168.255.255 and logs any intrusion attempts.
B. It prevents the internal network from being used in spoofed denial of service attacks and logs any exit to the Internet.
C. It filters incoming traffic from private addresses in order to prevent spoofing and logs any intrusion attempts.
When an OSPF design is planned, which implementation can help a router not have memory resource issues?
A. Have a backbone area (area 0) with 40 routers and use default routes to reach external destinations.
B. Have a backbone area (area 0) with 4 routers and 30,000 external routes injected into OSPF.
C. Have less OSPF areas to reduce the need for interarea route summarizations.
D. Have multiple OSPF processes on each OSPF router. Example, router ospf 1, router ospf 2.
Which condition must be met before a router can send an ICMP redirect message?
A. The IP address of the sending device must be in the same subnet as the next hop.
B. The ingress and egress interfaces on the device must be different.
C. The datagram must be source-routed.
D. ICMP echo requests must have been disabled globally.
You have been asked to evaluate how EIGRP is functioning in a customer network.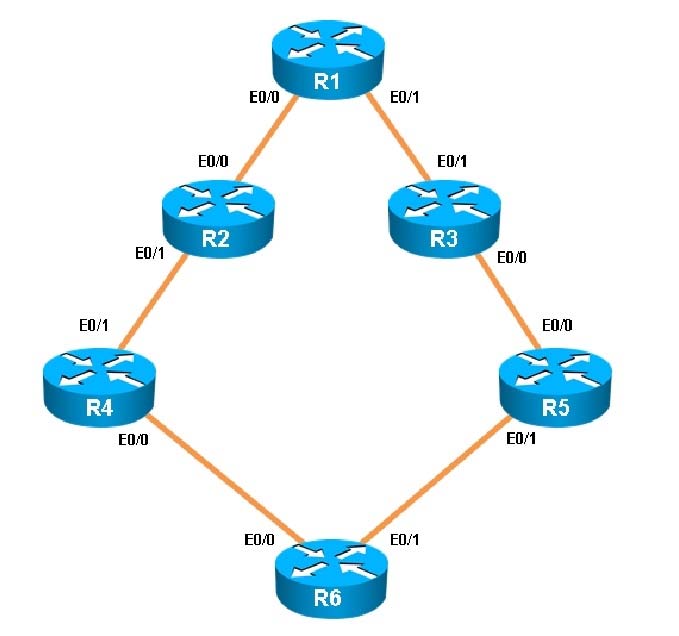
What type of route filtering is occurring on R6
A. Distribute-list using an ACL
B. Distribute-list using a prefix-list
C. Distribute-list using a route-map
D. An ACL using a distance of 255
PPPoE is composed of which two phases?
A. Active Authentication Phase and PPP Session Phase
B. Passive Discovery Phase and PPP Session Phase
C. Active Authorization Phase and PPP Session Phase
D. Active Discovery Phase and PPP Session Phase
You are troubleshooting an OSPF problem where external routes are not showing up in the OSPF database. Which two options are valid checks that should be performed first to verify proper OSPF operation? (Choose two.)
A. Are the ASBRs trying to redistribute the external routes into a totally stubby area?
B. Are the ABRs configured with stubby areas?
C. Is the subnets keyword being used with the redistribution command?
D. Is backbone area (area 0) contiguous?
E. Is the CPU utilization of the routers high?
What following parameters for the EIGRP authentication need to match in order for EIGRP neighbors to establish a neighbor relationship?
A. Autonomous System number.
B. K-Values
C. If authentication is used both: the key number, the password, and the date/time.
D. The neighbors must be on common subnet (all IGPs follow this rule).
Scenario - You have been asked to evaluate an OSPF network setup in a test lab and to answer questions a customer has about its operation. The customer has disabled your access to the show running-config command. Instructions - - Enter IOS commands on the device to verify network operation and answer for multiple-choice questions. - THIS TASK DOES NOT REQUIRE DEVICE CONFIGURATION. - Click on the icon or the lab at the bottom of the screen to gain access to the console for each device. - No console or enable passwords are required. - To access the multiple-choice questions, click on the numbered boxes on the left of the top panel. - There are four multiple-choice questions with this task. Be sure to answer all four questions before selecting the Next button.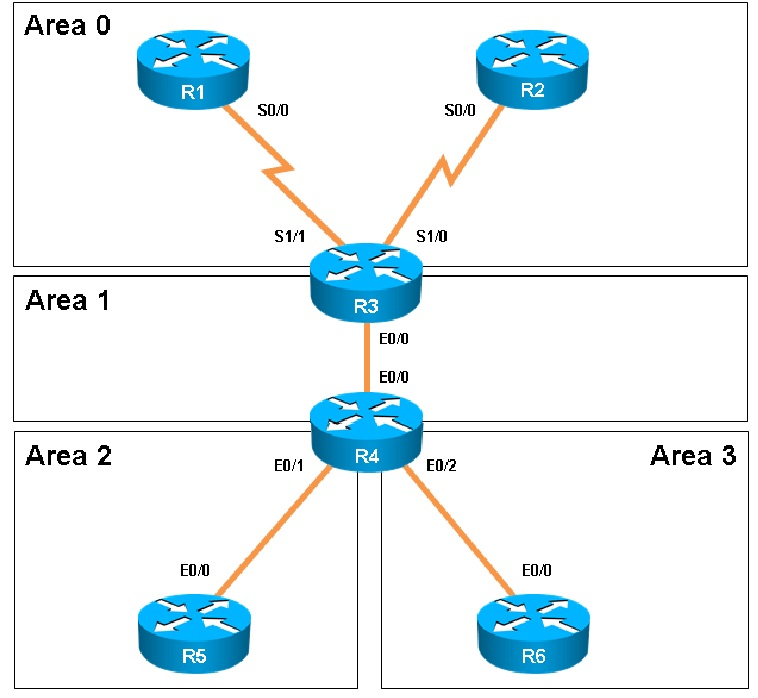

Areas of Router 5 and 6 are not normal areas. Inspect their routing tables and determine which statement is true.
A. R5’s Loopback and R6’s Loopback are both present in R5’s Routing table
B. R5’s Loopback and R6’s Loopback are both present in R6’s Routing table
C. Only R5’s loopback is present in R5’s Routing table
D. Only R6’s loopback is present in R5’s Routing table
E. Only R5’s loopback is present in R6’s Routing table
Which two statements about Frame Relay Point-to-Point connections are true? (Choose two.)
A. Changing a point-to-point sub interface to a different type requires the device to be reloaded.
B. They use two DLCIs to communicate with multiple endpoints over the Frame Relay cloud.
C. The device can establish a point-to-point connection to the cloud without a DLCI.
D. They can operate normally without a DLCI map.
E. Each physical interface that extends to the Frame Relay cloud can support a single SVC.
An engineer is using a network sniffer to troubleshoot DHCPv6 between a router and hosts on the LAN with the following configuration: interface Ethernet0 ipv6 dhcp server DHCPSERVERPOOL rapid-commit ! Which two DHCP messages will appear in the sniffer logs? (Choose two.)
A. reply
B. request
C. advertise
D. Acknowledge
E. solicit
F. accept
You have been asked to evaluate how EIGRP is functioning in a customer network.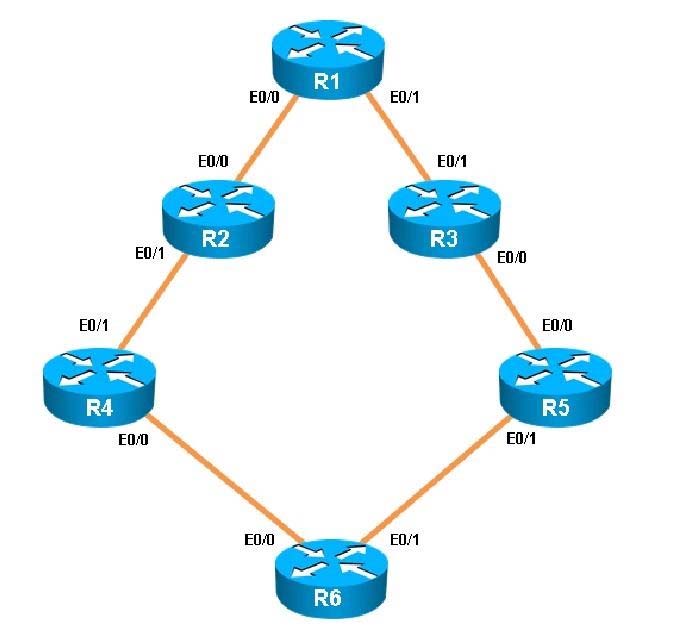

Which key chain is being used for authentication of EIGRP adjacency between R4 and R2?
A. CISCO
B. EIGRP
C. key
Which two statements about VRRP object tracking are true? (Choose two.)
A. VRRP supports only interface tracking.
B. A VRRP group can track only one object at a time.
C. The priority of a VRRP device can change in accordance with the up or down status of a VRRP object.
D. VRRP can track the status of interfaces and routes.
E. The VRRP interface priority must be manually configured by the administrator.
Which command do you enter to display log messages with a timestamp that includes the length of time since the device was last rebooted?
A. Service timestamps log uptime
B. Logging facility 20
C. Service timestamps debugging localtime msec
D. Logging console errors
E. Logging monitor 7
F. Service timestamps log datetime msec
Which two LSA types were introduced to support OSPF for IPv6? (Choose two.)
A. type 9
B. type 5
C. type 10
D. type 8
E. type 7 AD
Which three statements about the EIGRP routing protocol are true? (Choose three)
A. EIGRP sends periodic hello packets to the multicast IP address 224.0.0.10.
B. EIGRP will not form a neighbor relationship with another peer when their AS number and K values, either or both are mismatched.
C. EIGRP will form a neighbor relationship with another peer even when their K values are mismatched.
D. EIGRP supports five generic packet types, including Hello, Update, Query, Reply, and ACK packets.
Which condition must be satisfied before an EIGRP neighbor can be considered a feasible successor?
A. The neighbor’s advertised distance must be less than or equal to the feasible distance of the current successor.
B. The neighbor’s advertised distance must be less than the feasible distance of the current successor.
C. The neighbor’s advertised distance must be greater than the feasible distance of the current successor.
D. The neighbor’s advertised distance must be equal to the feasible distance of the current successor.
How to set up IP SLA to monitor Bandwidth between the certain limits?
A. Timer
B. Frequency
C. Threshold
D. Queue-limit
Which two phases of DMVPN allow to spoke sites to create dynamic tunnels to one another? (Choose two.)
A. Phase1
B. Phase 2
C. Phase 3
D. Phase 4
E. Phase 5
Which two BGP neighbor states are valid? (Choose two.)
A. Established
B. Active
C. Stuck in active
D. 2-WAY
E. Unknown
F. DROTHER
You have a router has some interface configured with 10Gb interface and giga interface. Which command you use to optimize higher BW? A.B.
C.
D.
A network administrator is troubleshooting an EIGRP connection between RouterA, IP address 10.1.2.1, and RouterB, IP address 10.1.2.2.Given the debug output on RouterA, which two statements are true?
A. RouterA received a hello packet with mismatched autonomous system numbers.
B. RouterA received a hello packet with mismatched hello timers.
C. RouterA received a hello packet with mismatched authentication parameters.
D. RouterA received a hello packet with mismatched metric-calculation mechanisms.
E. RouterA will form an adjacency with RouterB.
F. RouterA will not form an adjacency with RouterB.
Refer to the exhibit.Which three commands should be used on router B1 to redistribute the EIGRP AS 10 routes into RIP? (Choose three.)
A. router rip
B. router eigrp 10
C. redistribute eigrp 10
D. redistribute rip
E. default-metric 10000 100 255 1 1500
F. default-metric 5
Which condition can cause unicast reverse path forwarding to fail?
A. PortFast security violation
B. split horizon
C. asymmetric routing
D. STP convergence C
You have been asked to evaluate how EIGRP is functioning in a customer network.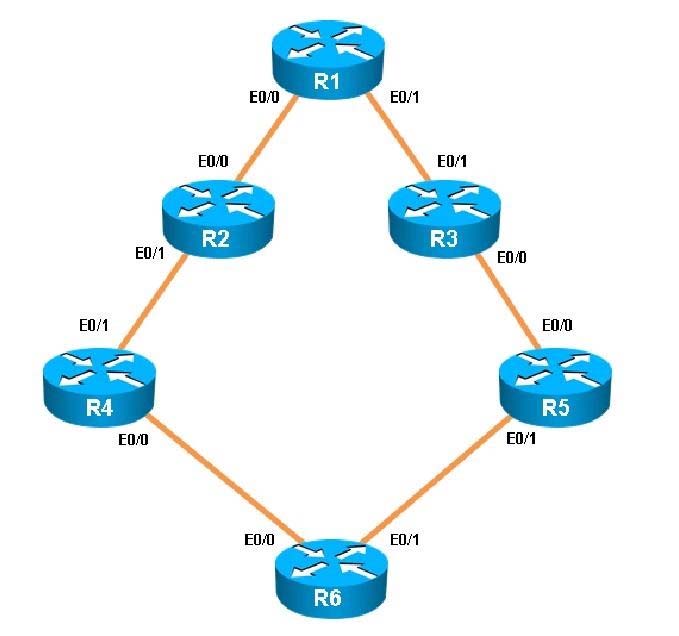

What percent of R1`s interfaces bandwidth is EIGRP allowed to use?
A. 10
B. 20
C. 30
D. 40
Refer to the Exhibit.Routers in the Diagram are configured with EIGRP. If RTB and RTC fail, which action will RTA take with respect to the HQ network?
A. RTA will automatically route packets via RTD to the HQ network.
B. RTA will place the route via RTD into the hold down state.
C. RTA will go into the active state for all routers.
D. RTA will go into the active state for the route to HQ network.
Which of the following are characteristics of TACACS+? (Choose two.)
A. Uses UDP
B. Encrypts an entire packet
C. Offers robust accounting
D. Cisco-proprietary
Which criterion does BGP evaluate first when determining the best path?
A. MED value
B. neighbor address
C. local preference value
D. weight
Refer to the exhibit.BigBids Incorporated is a worldwide auction provider. The network uses EIGRP as its routing protocol throughout the corporation. The network administrator does not understand the convergence of EIGRP. Using the output of the show ip eigrp topology all-links command, answer the administrator's question. Which three networks is the router at 172.17.10.2 directly connected to? (Choose three)
A. 172.17.0.0/30
B. 172.17.1.0/24
C. 172.17.2.0/24
D. 172.17.3.0/25
E. 172.17.3.128/25
An engineer has added the following configuration snippet to an implementation planning document. The configuration will be added to Router R1, whose Fa0/0 interface connects to a LAN to which Routers R2 and R3 also connect. R2 and R3 are already EIGRP neighbors with each other. Assuming the snippet shows all commands on R1 related to EIGRP authentication, which answer lists an appropriate comment to be made during the implementation plan peer review? key chain fred key 3 key-string whehew interface fa0/0 ip authentication key-chain eigrp 9 fred
A. The configuration is missing one authentication-related configuration command.
B. The configuration is missing two authentication-related configuration commands.
C. Authentication type 9 is not supported; type 5 should be used insteaD.
D. The key numbers must begin with key 1, so change the key 3 command to key 1.
What is the international standard for transmitting data over a cable system?
A. PPPoE
B. DOCSIS
C. CMTS
D. AAL5
Refer to the exhibit.Router RTA is the hub router for routers RTB and RTC. The Frame Relay network is configured with EIGRP, and the entire network is in autonomous system 1. However, router RTB and RTC are not receiving each other's routes. What is the solution?
A. Configure the auto summary command under router eigrp 1 on router RTA.
B. Issue the no ip split horizon command on router RTA.
C. Configure subinterfaces on the spoke routers and assign different IP address subnets for each subinterface.
D. Check and change the access lists on router RTA.
E. Issue the no ip split horizon eigrp 1 command on router RTA.
F. Configure a distribute list on router RTA that allows it to advertise all routes to the spoke routers.
Study the exhibit carefully.Router R1 is connected to networks 172.16.1.0 /26 and 172.16.1.64 /27. Based on the partial output in the exhibit, which description is correct?
A. Router R1 should be reconfigured with an ACL instead of an ip prefix-list command.
B. Router R1 will advertise both routes.
C. Router R1 will deny the 172.16.1.0/27 route while permitting the 172.16.1.0/26 route to be advertised.
Redistributing BGP into OSPF what statement is correct? route-map deny 10 match ip address 10 route-map permit 20 access-list 10 permit 172.16.0.0 0.0.0.255
A. 172.16.0.0/24 will NOT be redistributed into OSPF.
B. 172.16.0.0/24 will be redistributed into OSPF.
C. Routes permitted by ACL 10 will be redistributed.
D. All routes will be filtered. A
You have been asked to evaluate how EIGRP is functioning in a customer network.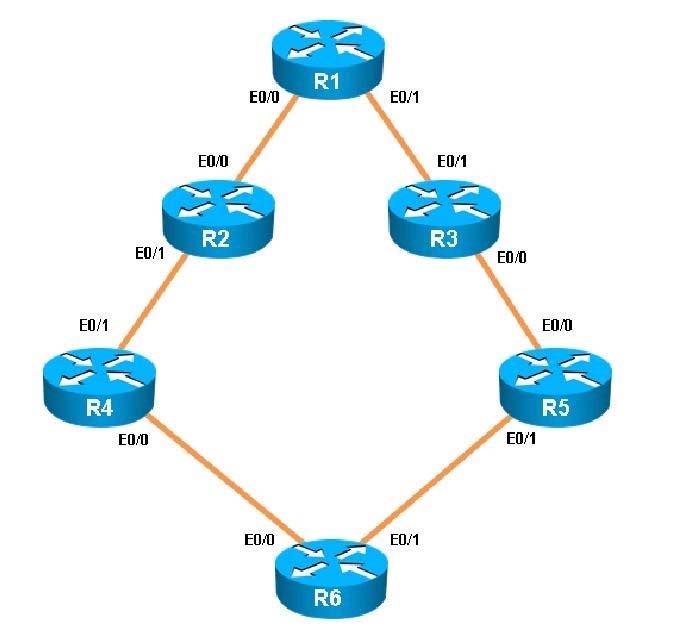

What type of route filtering is occurring on R6
A. Distribute-list using an ACL
B. Distribute-list using a prefix-list
C. Distribute-list using a route-map
D. An ACL using a distance of 255
Access Full 300-101 Dump Free
Looking for even more practice questions? Click here to access the complete 300-101 Dump Free collection, offering hundreds of questions across all exam objectives.
We regularly update our content to ensure accuracy and relevance—so be sure to check back for new material.
Begin your certification journey today with our 300-101 dump free questions — and get one step closer to exam success!